In today's modern work environment, the widespread adoption of SaaS apps has brought unprecedented efficiency and agility to organizations. However, this SaaS acceleration has also introduced new challenges, particularly in security and compliance. One effective way to overcome these challenges is to leverage identity governance and administration tools.
As an IT manager, it's crucial to understand the significance of IGA solutions to strengthen your organization’s security posture and maintain compliance.
As organizations embrace SaaS applications, the number of user identities, access permissions, and data flows grows exponentially. Managing these identities and their associated access privileges manually becomes complex and error-prone. IGA solutions are a vital bridge between the increased SaaS adoption and the imperative to maintain security and compliance.
IGA solutions play a pivotal role in fortifying your organization's security posture. It empowers your team to centrally manage user identities, access rights, and entitlements across various SaaS platforms. IGA minimizes the risk of data breaches, insider threats, and unauthorized access by ensuring users access the right resources.
Further, comprehensive user provisioning and deprovisioning, along with role-based access controls, bolster the organization's defenses against potential security breaches. In addition, these solutions provide an audit trail that simplifies compliance reporting by automating access request approvals and monitoring user activities. It also demonstrates accountability and transparency to stakeholders.
Key Features Of An Effective IGA Solution
Below are key features that make an IGA solution suitable for your organization.
- Identity Lifecycle Management: An IGA solution should facilitate efficient onboarding, modification, and offboarding of user identities. This streamlines access management and minimizes the risk associated with orphaned accounts.
- Role-Based Access Controls (RBAC): The ability to assign access permissions based on job roles and responsibilities is paramount. RBAC simplifies access rights management and reduces the likelihood of granting excessive privileges.
- Access Certification and Review: Regular access reviews ensure that permissions align with employees' responsibilities. An effective IGA solution should automate this process, notifying managers to confirm or revoke access.
- Segregation of Duties (SoD): Preventing conflicts of interest minimizes fraud and unauthorized activities. Look for an IGA solution that enforces SoD policies by identifying and mitigating potential conflicts in access rights.
- User Activity Monitoring: Real-time monitoring of user activities provides insights into potential security incidents. A robust IGA solution should alert administrators to suspicious behaviors and facilitate prompt responses.
- Self-Service Access Requests: Empowering users to request access to specific resources streamlines the process while adhering to proper authorization channels.
- Compliance Reporting and Auditing: The IGA solution should generate comprehensive reports demonstrating compliance efforts, simplifying audits and regulatory assessments.
- Integration Capabilities: Seamless integration with your existing IT infrastructure, including SaaS applications, is essential for efficient operation.
This blog post will help you explore the various IGA solutions that will ensure security and compliance in your organization.
Top 11 IGA Solutions
Let’s discuss the list of IGA solutions.
1. Zluri
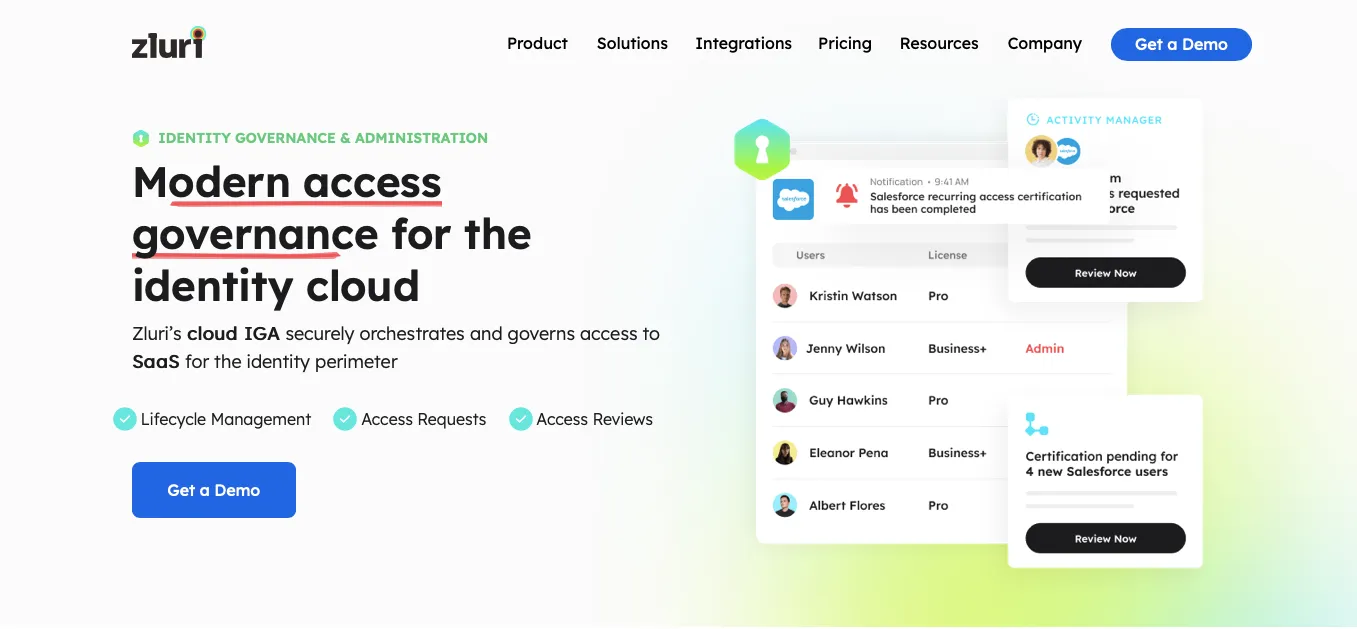
Zluri presents a robust IGA platform for ensuring users have the right access to your SaaS applications. With Zluri's IGA platform, you can effortlessly control and bolster the security of your SaaS apps. You can set up users, review their access automatically, and let them request access independently. This puts you in charge of ensuring everyone has the right access.
Let's dive into what sets Zluri apart from other IGA tools with its distinct and exceptional capabilities.
- Powerful Discovery Engine
Zluri uses 9 discovery methods to gain complete visibility into your organization's SaaS landscape. These methods include browser agents, IDPs & SSO, direct integrations, desktop agents, active directories, HRMS platforms, MDM platforms, finance systems, and CASB platforms. This empowers your team to identify and manage SaaS applications effectively.
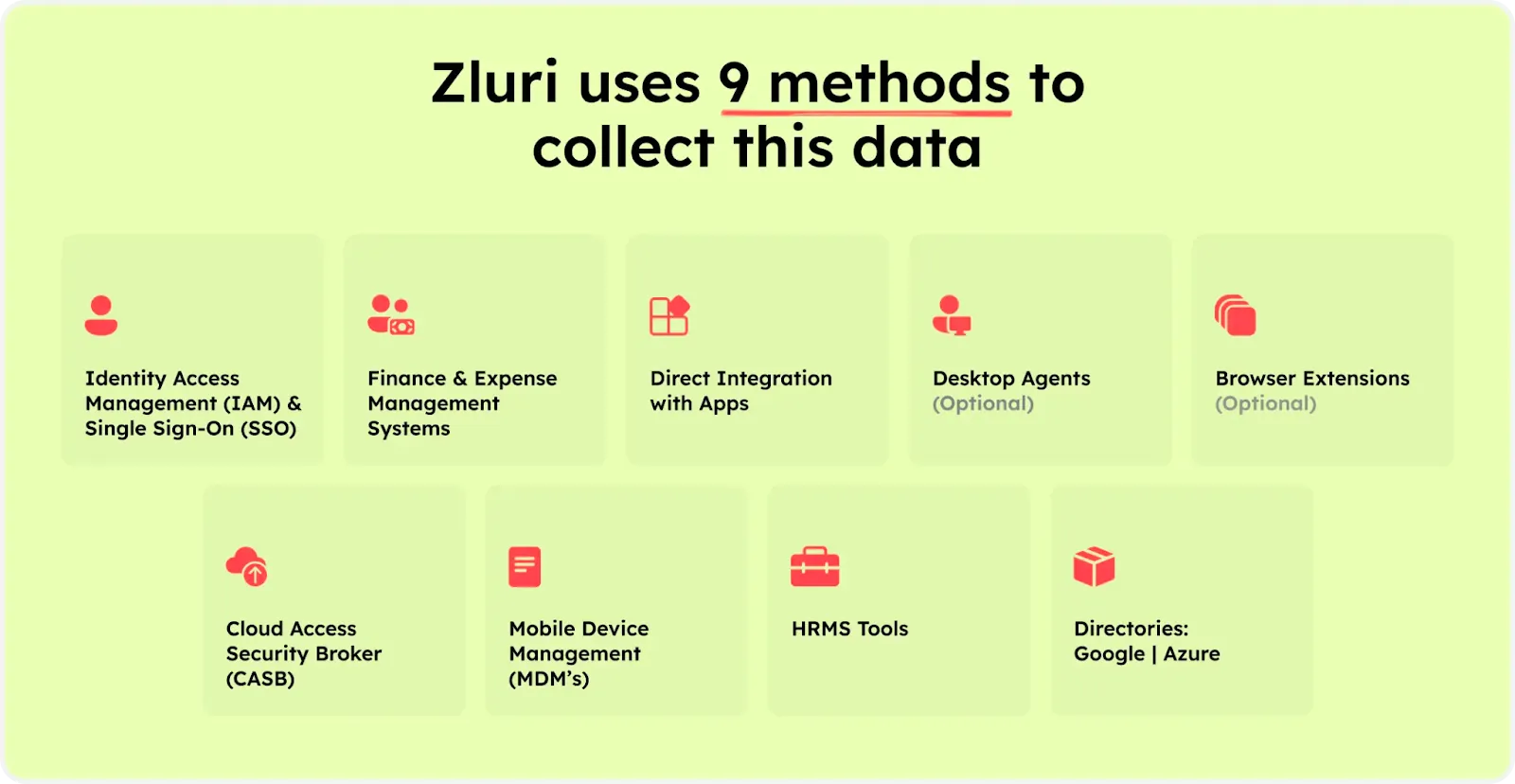
But Zluri does more than just find data. It connects with over 300 SaaS apps that help you to receive live information, useful insights, and AI alerts to stay updated. Through API connections, Zluri ensures you explore every corner of data in all your SaaS apps. You can be sure that Zluri shows you everything about your SaaS setup.
- Robust Automation Engine
Zluri's automation engine functions like an auto-pilot for your organization. It effortlessly handles access processes, guarantees efficient automation through careful checks, and helps you adhere to clear rules and policies.
Simplify your access management with Zluri’s lifecycle management capabilities
Zluri's IGA solution provides you with lifecycle management capabilities. It includes ensuring the required access, adjusting it for role changes, and safely removing access when needed. This way, your IT team can increase employees’ productivity while safeguarding the security of your organization’s sensitive data.
In addition, Zluri offers key unique features that differentiate it from others, ensuring effective access management:
Customizable workflows: Zluri enables you to create workflows that match your organization's needs. This stops the manual work of granting and revoking users’ access. You can easily personalize workflows using the user's job, team, and experience, all through an easy interface. This will strengthen your security posture while users have the required access to perform their job.
Onboarding

Offboarding
Powerful app recommendations & in-app suggestions: Zluri also gives contextual-based recommendations for apps that fit well with each user's role, team, and experience. This helps your team select the right apps easily.

Moreover, it offers suggestions within apps to boost how users work, suggesting actions for better task results.
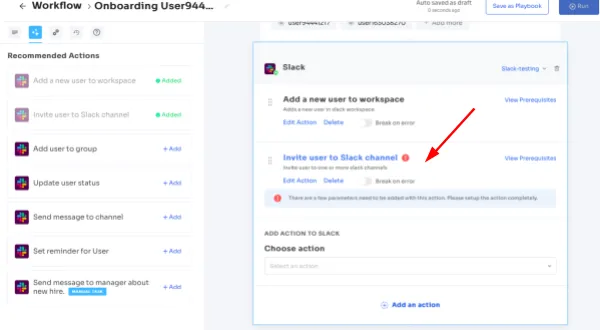
Automation Playbooks: Zluri simplifies employees’ onboarding and offboarding by saving workflows as “playbooks”. This means you don't have to make new workflows every time, which makes the process even smoother and more efficient.
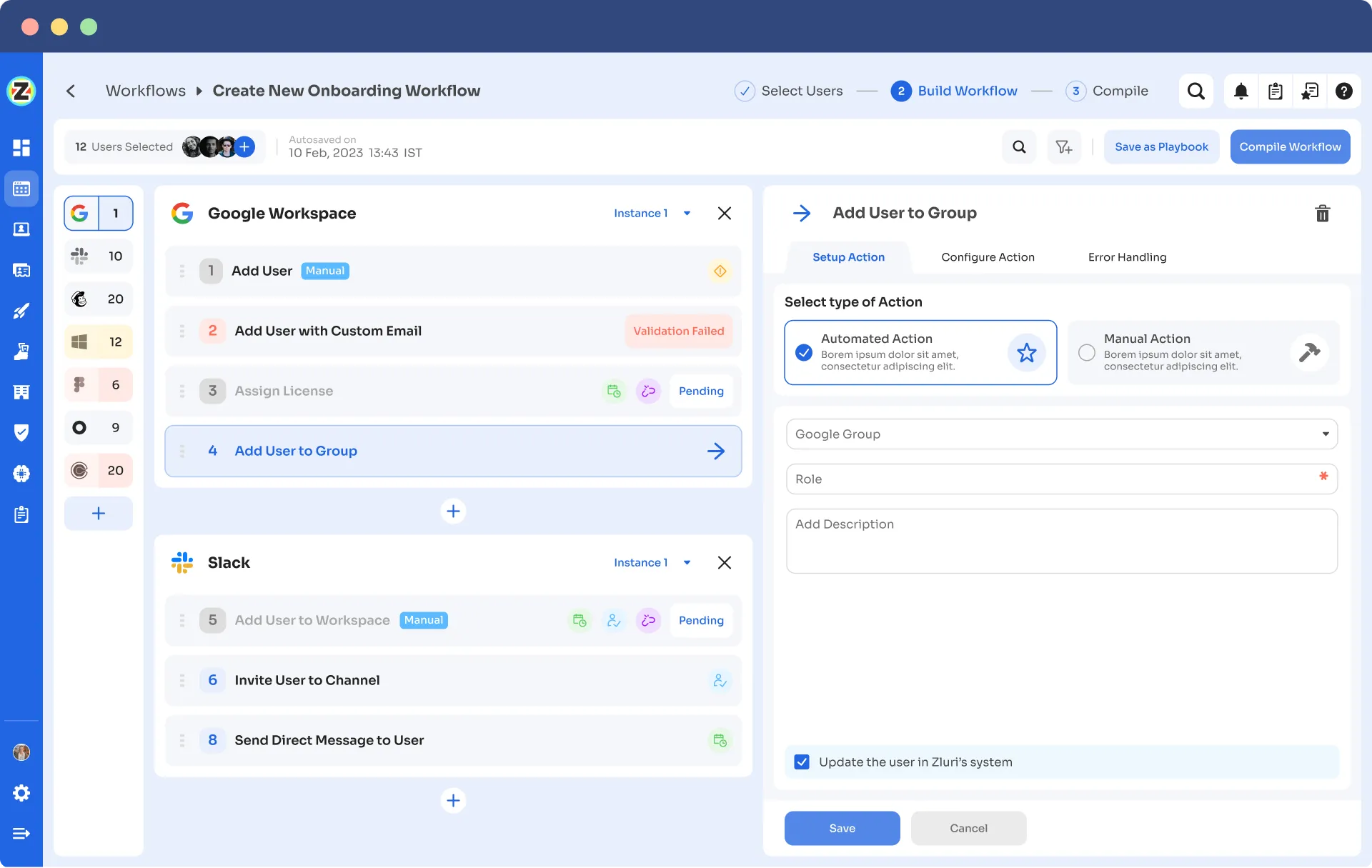
Onboarding Playbooks
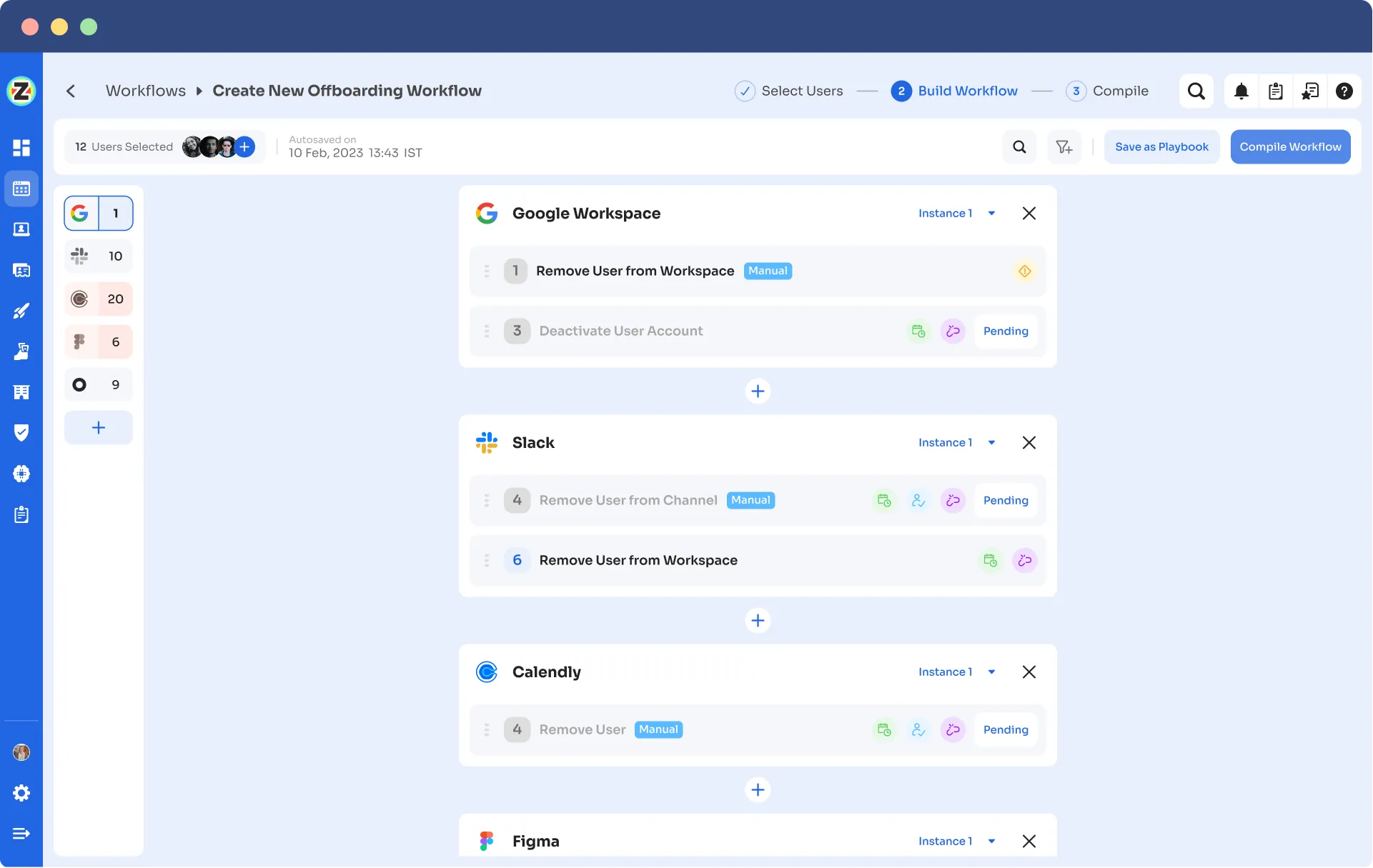
Offboarding Playbooks
Note: These playbooks also make sure your team keeps your data secure and follows the rules, whether they're setting up or taking away user access down the line.
But what happens when a user’s role changes during the mid-lifecycle transitions?
Ad-hoc access request management
Zluri makes it easy to handle user access when their roles change with its Employee App Store (EAS). This feature lets your IT team stay in control of which tools and apps employees can use.

With the EAS, your team or an assigned person can review access requests. They will be able to understand the employee's role and requirements. This ensures that employees can only access what they actually require, enhancing the security of sensitive information.
Example: Let's say you have a company's financial records stored in a computer system. Different employees need access to these records for various tasks. Some employees handle billing, some manage expenses, and others track sales. By using the EAS, the responsible person can see who needs access to what.
So, if an employee in the sales department requests access to the financial records, the EAS will make sure they are only granted access to the sales-related information they require rather than giving them access to the entire financial database. This way, sensitive financial data remains protected from being seen or used by those who don't actually need it for their jobs.
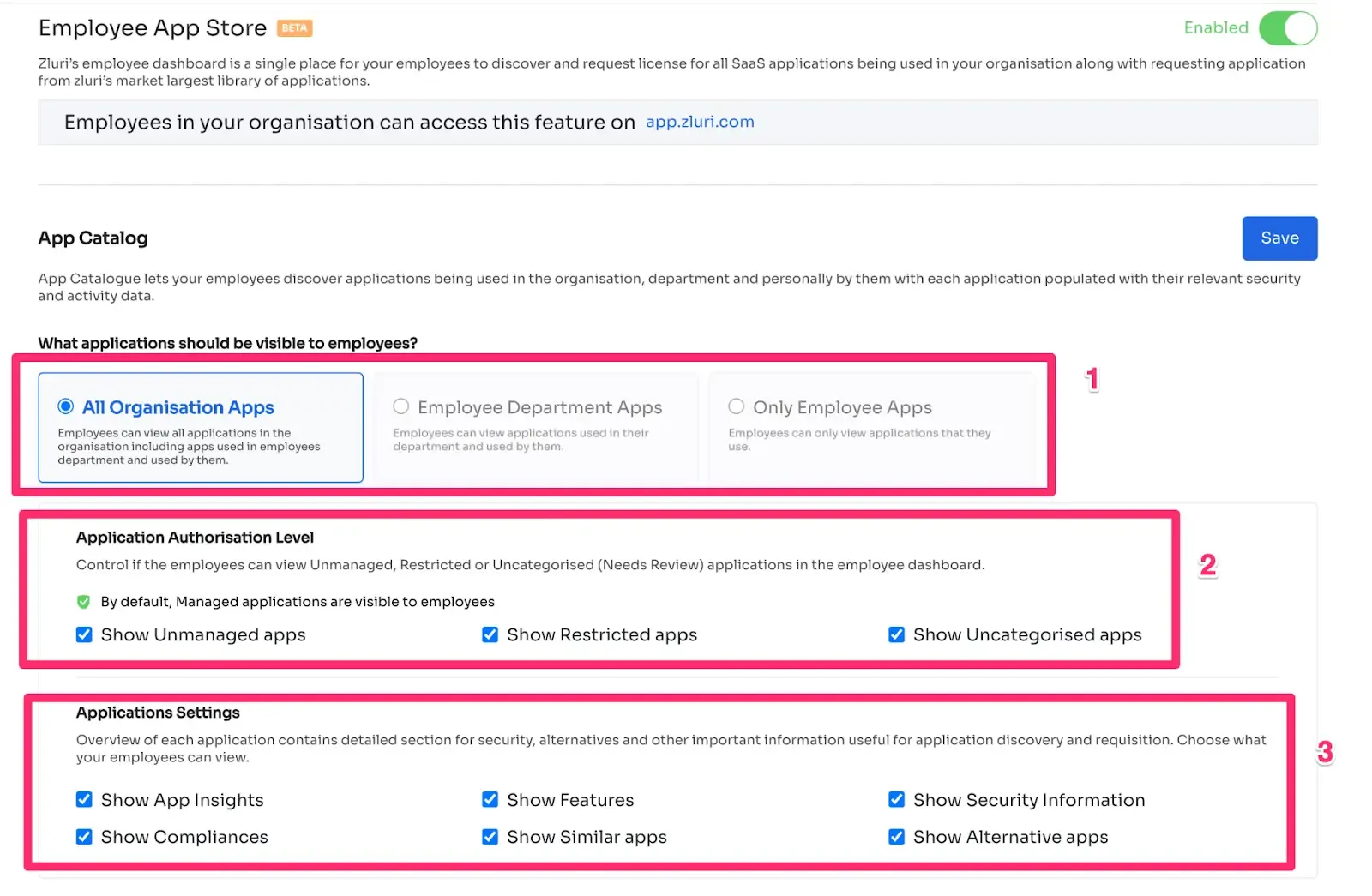
Zluri offers a straightforward approach to approving or declining requests. There are three tiers involved: app owners, managers responsible for overseeing tasks, and IT administrators. Even if opinions differ among them, those higher up can override decisions.
When a request receives “rejected” as a response, the reason behind it can be provided. This promotes understanding among all parties. Moreover, the approver has the option to modify the request if necessary.
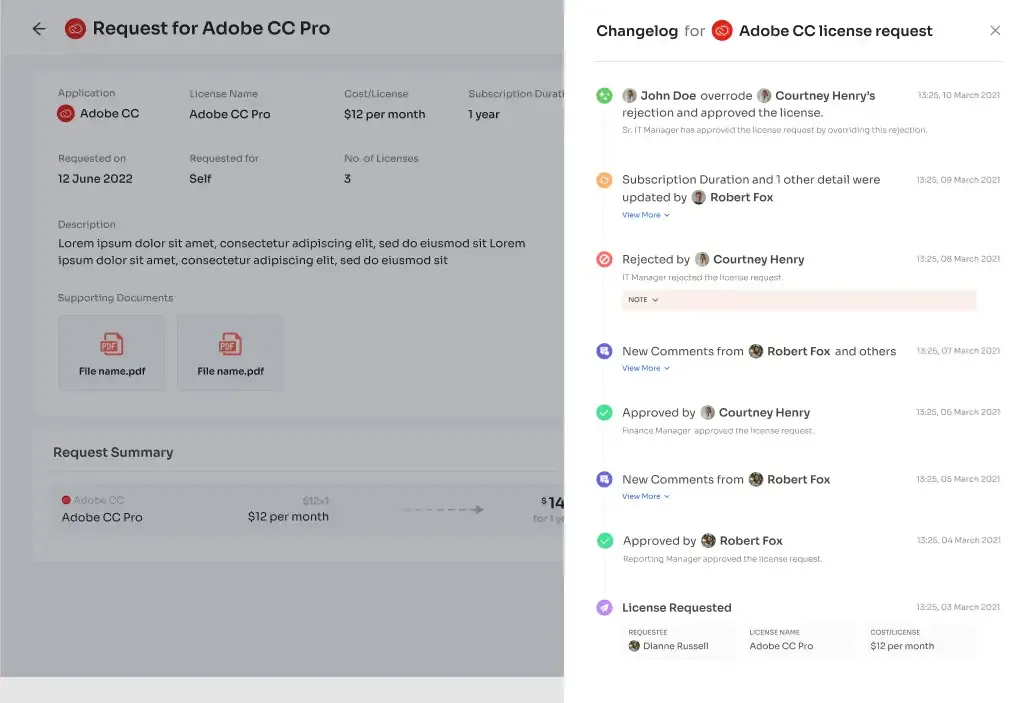
Zluri introduces a fascinating feature known as a 'changelog.' This functions like a list of updates. Whether you make a request or if any changes occur, these are documented there. This ensures everyone stays informed about the ongoing developments.
- Ensure security and compliance with Zluri’s access certification
Zluri's IGA solution makes managing user access review and permissions a breeze for your organization. It's a centralized platform that simplifies security, GRC, and auditing tasks. With Zluri, you can easily define access review criteria, select who reviews, and set up review schedules.
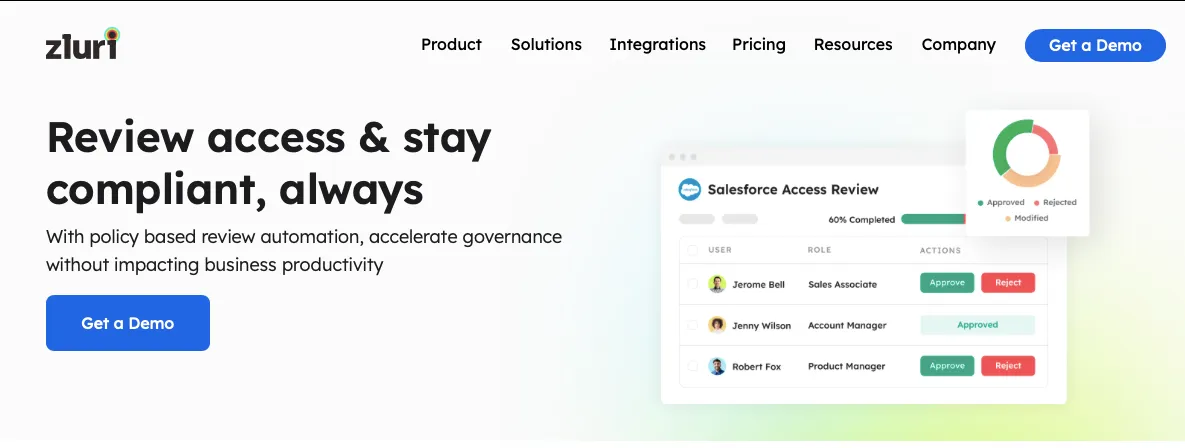
Zluri's intelligent automation checks user access rights using predefined rules, saving time and reducing errors compared to manual reviews using spreadsheets. But Zluri continues beyond reviews.
It also automatically remediates access issues if any violations are found. This boosts your organization's security and ensures you follow all the rules. Zluri helps you remove access for employees who've left or no longer need certain privileges, which helps prevent unauthorized breaches and keeps your data safe.
Zluri also creates detailed reports. These reports give you insights into users’ access, any vulnerabilities, and whether you're meeting compliance standards. These reports are super helpful when you need to show auditors that you're doing things the right way and when you need to make smart choices about managing access.
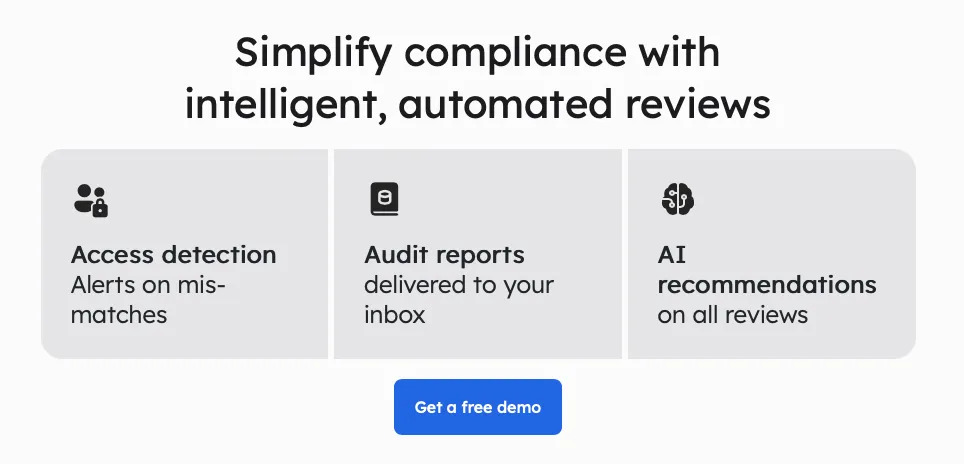
Zluri's unique approach to access reviews sets it apart from other IGA tools. Let’s see how.
Continuous Access Reviews: With Zluri's IGA solution, you're in charge of who gets access to what. You can closely monitor access rights by doing regular checks and planned reviews.
Regular certifications make sure that access permissions are looked at and confirmed consistently. This helps find and fix security problems fast. And if you schedule reviews, you're less likely to miss important access issues.
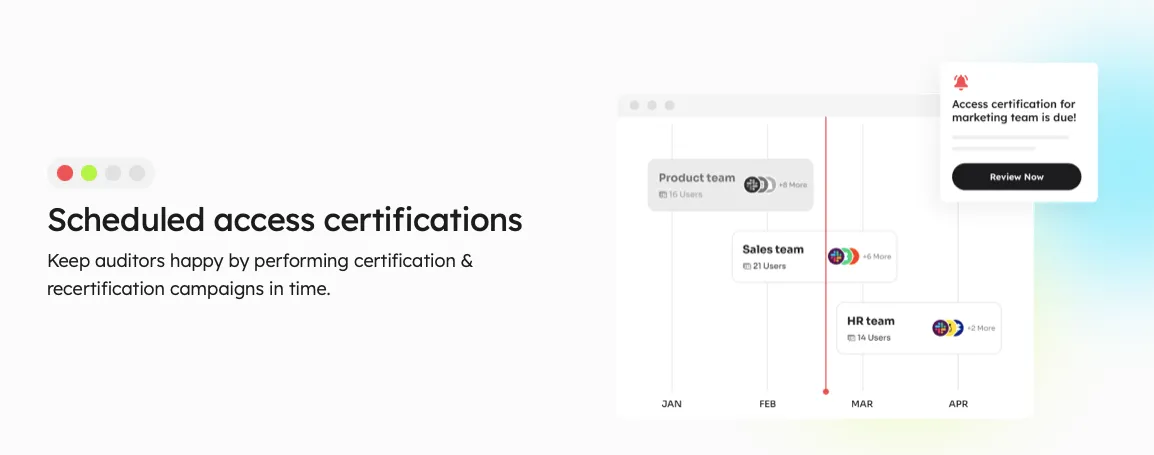
In addition, Zluri gives you templates that follow the rules everyone in the industry uses. These templates make it easy to do these checks and review the right way.
Real-time Access Reviews: Zluri uses the smarts of artificial intelligence (AI) to make your data safe and keep things compliant. It's like having a watchful eye that looks out for potential problems.
Zluri checks who's accessing your resources in real time and looks at how they're doing it. If anything seems strange or risky, it alerts you so you can stop issues before they impact your organization. This keeps your important info secure.
In addition, Zluri's AI compliance capabilities offer intelligent insights and recommendations. It aligns access controls with industry regulations and standards, reducing the risk of compliance violations. By simplifying the compliance process with AI technology, Zluri helps your organization meet regulatory requirements easily.
Customer rating
- G2: 4.8/5
- Capterra: 4.9/5
2. Omada Identity
Omada Identity is a cutting-edge IGA platform that empowers you and your team to efficiently manage user identities, streamline access control, and ensure compliance with industry regulations. Designed with a user-centric approach, Omada Identity aims to simplify complex IGA processes, allowing you to focus on strategic initiatives rather than getting bogged down by administrative tasks.
Moreover, Omada Identity seamlessly integrates with your existing IT infrastructure, including directory services, applications, and platforms. This ensures your IGA solution grows with your organization, adapting to changing requirements and technologies.
Key Features
- User Lifecycle Management: Omada Identity enables you to manage the entire lifecycle of user identities, from onboarding to offboarding. This intuitive feature simplifies the provisioning and deprovisioning of user accounts, ensuring that employees have the right access at the right time and that access is promptly revoked when needed.
- Role-based Access Control (RBAC): With Omada's RBAC capabilities, you can assign and manage access permissions based on user roles. This approach enhances security by granting employees only the access required to perform their tasks, reducing the risk of unauthorized data exposure.
- Segregation of Duties (SoD): Prevent conflicts of interest and potential fraud by leveraging Omada's SoD controls. This feature identifies and mitigates access conflicts, ensuring no single user possesses conflicting permissions that could lead to abuse or manipulation.
- Access Certification and Review: Maintaining compliance is effortless with Omada's access certification functionality. Regularly review and validate user access rights, making certain that they align with established policies and regulations, ultimately reducing compliance-related risks.
- Audit and Reporting: Stay ahead of compliance audits with Omada's robust audit and reporting capabilities. Generate comprehensive reports detailing access activities, changes, and compliance status, providing a transparent overview of your identity management practices.
- Self-Service Portal: Empower users with self-service capabilities, allowing them to reset passwords, request access, and manage their own profiles. This reduces the burden on your IT team and enhances user experience and productivity.
Customer rating
- G2: 3.8/5
3. Okta Identity Governance
Okta Identity Governance is a powerful solution in the realm of IGA, tailor-made to address the challenges of managing user identities and access rights. With an emphasis on seamless user experiences and uncompromising security, Okta empowers your IT teams to efficiently oversee identity management while ensuring compliance with industry regulations.
Moreover, you can enhance security by implementing MFA through Okta Identity Governance. It requires multiple forms of verification before granting access, effectively mitigating unauthorized access attempts and safeguarding sensitive information.
The tool also seamlessly integrates with your existing IT ecosystem, including applications, directories, and platforms. This ensures that your IGA solution remains adaptable to your organization's evolving needs and technological advancements.
Key Features
- Automated User Lifecycle Management: Okta identity governance offers automated user lifecycle management, from initial onboarding to eventual offboarding. This intuitive feature streamlines user provisioning and deprovisioning, ensuring that individuals have timely access and that access is promptly revoked as needed.
- Role-based Access Control (RBAC): Simplify access management with Okta's RBAC capabilities. You can assign access permissions based on user roles, enhancing security by granting employees only the privileges necessary for their tasks, and reducing the risk of unauthorized data exposure.
- Policy-driven Access Certification: Ensuring compliance becomes effortless with Okta's policy-driven access certification. This feature facilitates regular review and validation of user access, guaranteeing alignment with established policies and regulations and ultimately minimizing compliance-related risks.
- Segregation of Duties (SoD): Prevent potential conflicts of interest and fraud with Okta's SoD controls. This feature identifies and mitigates access conflicts, ensuring no single user possesses conflicting permissions that could lead to misuse or data manipulation.
- Comprehensive Auditing and Reporting: Stay audit-ready with Okta's robust auditing and reporting capabilities. Generate detailed reports detailing access activities, changes, and compliance status, providing a transparent overview of your identity management practices.
Customer rating
- G2: 4.5/5
- Capterra: 4.7/5
4. Saviynt IGA

Saviynt IGA emerges as a powerful solution tailored to address these needs, providing you with a comprehensive solution to manage identities, access, and compliance seamlessly. It simplifies the process of managing user identities throughout their lifecycle – from onboarding to offboarding.
With a user-friendly interface, your IT admin can efficiently grant, modify, or revoke access rights based on roles, responsibilities, and business needs. This eliminates manual errors and enhances operational efficiency.
Key Features
- Privileged Access Management: Safeguarding privileged accounts is critical for preventing unauthorized access to sensitive information. Saviynt IGA allows you to monitor and control privileged access effectively, reducing the risk of insider threats and unauthorized data exposure.
- Role-Based Access Control (RBAC): The RBAC feature of Saviynt IGA allows your team to create and manage access policies based on predefined roles within the organization. This ensures that employees have the right level of access they need to perform their tasks, minimizing the risk of unauthorized access and potential data breaches.
- Compliance Management: Saviynt IGA assists organizations in meeting regulatory requirements effortlessly. The solution provides pre-configured compliance frameworks and automated workflows to streamline audit processes. Your team can demonstrate compliance by generating detailed reports and maintaining a transparent audit trail.
- Segregation of Duties (SoD) Analysis: Preventing conflicts of interest and fraud is essential for maintaining a secure environment. Saviynt IGA conducts thorough SoD analysis to identify and mitigate access conflicts that might lead to fraudulent activities. You can proactively address these issues and ensure data integrity.
- Self-Service Portal: Empower end-users with a self-service portal that enables them to request access, reset passwords, and manage their accounts independently. This feature reduces the burden on your IT help desks, freeing up their resources for more strategic initiatives.
- Real-time Monitoring and Alerts: With Saviynt IGA's real-time monitoring capabilities, you receive alerts for suspicious activities or policy violations. This proactive approach allows for a swift response to potential threats, enhancing overall security.
Customer rating
- G2: 3.5/5
- Capterra: 4.5/5
5. Tuebora
Tuebora offers a comprehensive IGA solution that caters to the unique needs of modern IT managers. The solution empowers your organization with a centralized access management system. Efficiently manage user identities, roles, and permissions from a single dashboard.
It simplifies access provisioning, deprovisioning, and ongoing management, reducing the risk of unauthorized access and ensuring compliance with industry regulations.
Further, it seamlessly integrates with your existing applications, systems, and directories, ensuring a smooth flow of data and processes. This minimizes disruption and maximizes the value of your existing investments.
Key Features
- User Lifecycle Management: Managing user access throughout their lifecycle is a critical aspect of IGA. Tuebora automates user onboarding, changes, and offboarding processes, ensuring that access is granted, modified, or revoked in a timely manner. This helps maintain data security and minimize the risk associated with orphaned accounts.
- Role-Based Access Control (RBAC): Tuebora's RBAC capabilities enable you to define and enforce granular access rights based on job roles and responsibilities. This not only enhances security but also enhances productivity by ensuring users have the right level of access they need to perform their tasks.
- Segregation of Duties (SoD): Prevent conflicts of interest and potential fraudulent activities through Tuebora's SoD controls. Identify and mitigate access conflicts by setting up rules that prevent users from having conflicting roles or permissions. Tuebora's automated detection helps your organization maintain a robust internal control environment.
- Streamlined Compliance Audits: Tuebora understands the challenges of compliance audits. With its powerful reporting and auditing features, you can generate comprehensive reports showcasing access changes, user activity, and compliance adherence. This capability ensures you're well-prepared for audits, reducing compliance-related stress and effort.
- AI-Powered Insights: Leveraging the potential of artificial intelligence, Tuebora provides intelligent insights into access patterns and potential risks. Identify anomalous behavior and patterns that might indicate security breaches or policy violations. This proactive approach enhances your organization's ability to detect and respond to threats swiftly.
6. SecurEnds
SecurEnds offers an IGA solution tailored to meet your organization's unique challenges. With the increasing complexity of your IT ecosystems and regulatory requirements, effective identity management has become a backbone in safeguarding your organization's digital assets.
SecurEnds provides a centralized platform that streamlines user provisioning, access requests, and role management. This unified approach reduces the risk of errors and ensures consistent access control practices across the organization.
SecurEnds boasts an intuitive user interface that empowers your IT team to easily manage identities and access, reducing the learning curve and enhancing productivity.
Key Features
- Intelligent Access Reviews: Stay ahead of access-related risks with SecurEnds' intelligent access review capabilities. Effortlessly schedule and conduct access reviews based on predefined criteria, enabling you to promptly identify and rectify inappropriate permissions. This proactive approach mitigates the chances of unauthorized access.
- Entitlement Management: Crafting and managing roles can be intricate, but not with SecurEnds. The solution simplifies role creation, modification, and retirement, aligning with the principle of least privilege. This feature boosts security and optimizes user workflows by providing them only the access they truly need.
- Automated Compliance Auditing: Navigating the complication of compliance regulations can be a headache. SecurEnds eases this burden by automating compliance audits. Effortlessly generate compliance reports, demonstrating adherence to industry standards and regulations, and confidently sail through audits.
- User Lifecycle Automation: Onboarding and offboarding employees can be a logistical challenge. With SecurEnds, automate user lifecycle processes, including provisioning, deprovisioning, and access adjustments. This ensures quick and accurate user management, enhancing operational efficiency.
- Risk Analytics and Insights: Make informed decisions with the help of SecurEnds' risk analytics. Gain insights into user behavior, access patterns, and potential security vulnerabilities. Armed with this data, you can proactively address risks and fine-tune your access policies.
Customer rating
- Capterra: 4.8/5
7. Veza
Veza understands that managing user identities throughout their lifecycle can be daunting. With its intuitive interface, you can effortlessly provision and deprovision users across your organization.
Whether granting access to new employees, adjusting roles, or ensuring the smooth offboarding of departing staff, Veza's centralized platform simplifies the process, minimizing errors and reducing administrative overhead.
Key Features
- Role-Based Access Control (RBAC) Mastery: Veza's advanced RBAC capabilities empower you to define specific roles and associated permissions. This ensures that employees have access to the resources they need for their roles – no more, no less. This not only enhances security by preventing unauthorized access but also streamlines the access request process, boosting overall productivity.
- Compliance Made Easy: Veza simplifies compliance by automating policy enforcement, ensuring that your organization adheres to industry standards and internal policies. Through real-time monitoring and auditing, you can swiftly identify any anomalies or unauthorized access attempts, maintaining a robust security posture while staying compliant effortlessly.
- Seamless Integration: Veza seamlessly integrates with your existing infrastructure, allowing for smooth data synchronization and consistent user management across different systems. This means less time spent on manual data entry and more time focusing on strategic IT initiatives.
- Actionable Insights through Analytics: Through its powerful analytics dashboard, you gain a holistic view of user activities, access patterns, and potential risks. These insights empower you to make informed decisions, identify potential security gaps, and optimize your IGA strategy for maximum efficiency.
Customer rating
- Capterra: 5/5
8. Entitle
Entitle is a cloud permission management platform that offers IGA capabilities. It provides you with a robust solution to efficiently manage identities, control access, and ensure compliance within your organization. Entitle provides the stability and innovation you need to keep your systems secure in a world where data breaches and regulatory requirements constantly evolve.
Moreover, Entitle's IGA solution offers a centralized platform to manage user identities across the organization. You can easily streamline onboarding, offboarding, and role assignments, reducing administrative burdens and enhancing efficiency.
Key Features
- Automated Provisioning and Deprovisioning: Entitle's IGA solution automates the provisioning and deprovisioning of user accounts and access rights. This eliminates manual errors, enhances security, and accelerates the onboarding and offboarding processes.
- Role-Based Access Control (RBAC): Simplify access management with RBAC. Assign predefined roles to users based on their responsibilities, ensuring they only have the necessary access privileges. This minimizes the risk of unauthorized data exposure and prevents potential breaches.
- Access Certification and Review: Stay compliant effortlessly with Entitle's access certification and review features. Review user access to sensitive resources regularly and ensure that permissions align with employees' current roles. This proactive approach mitigates the risk of unauthorized access and maintains compliance with industry regulations.
- Audit and Reporting: Gain deep insights into identity and access activities through comprehensive audit logs and reporting. As an IT manager, you'll have a clear overview of user actions, changes, and potential security threats, allowing you to respond effectively.
- Multi-Factor Authentication (MFA): Elevate your security posture with MFA. Entitle's IGA solution supports multiple authentication methods, ensuring that only authorized users can access critical systems and resources.
Customer rating
- G2: 4.8/5
9. CyberArk Identity Security Platform
CyberArk's Identity Security Platform is a powerful tool designed to streamline and strengthen IGA practices. You can rest assured that this platform provides a centralized hub for managing user identities, permissions, and access across your organization's digital landscape.
Whether it's on-premises, cloud, or hybrid environment, this solution unifies identity management with a focus on security, efficiency, and compliance.
Key Features
- Identity Lifecycle Management: Simplify the management of user identities throughout their lifecycle. Create, modify, and retire user accounts with ease, ensuring access remains aligned with roles and responsibilities.
- Access Governance: Establish well-defined access policies that dictate who can access what resources. The platform allows you to monitor and control permissions, preventing unauthorized access and potential security breaches.
- Privileged Access Management (PAM): An integral aspect of IGA, the platform extends its capabilities to privileged users. Safeguard critical systems and data by enforcing strict controls on privileged accounts, reducing the risk of misuse.
- Role-based Access Control (RBAC): Assign roles to users based on their job functions, making access management more intuitive and scalable. With RBAC, permissions are structured in a logical manner, reducing complexity and errors.
- Policy Enforcement and Compliance: Ensure your organization adheres to industry regulations and internal policies. The platform facilitates real-time compliance monitoring, audits, and reporting to address potential gaps in security.
- Automated Provisioning and Deprovisioning: Save time and resources by automating the provisioning and deprovisioning of user accounts. When an employee joins or leaves the organization, access is granted or revoked promptly, reducing the risk of lingering access.
Customer rating
- G2: 4.4/5
10. Lumos
Lumos presents a comprehensive solution for identity governance and identity administration that caters to the specific needs of IT managers. It simplifies identity management by providing a unified dashboard where you can effortlessly oversee user identities, roles, and permissions across various systems and applications. This centralization streamlines administration, reduces errors, and enhances security.
Moreover, the solution seamlessly connects with various platforms, directories, and applications, ensuring a smooth transition without disrupting your ongoing operations.
Key Features
- Automated Provisioning and Deprovisioning: Lumos automates user onboarding and offboarding, ensuring new hires get the right access instantly, and departing employees have their permissions revoked promptly. This not only enhances efficiency but also prevents unauthorized access.
- Role-based Access Control (RBAC): Lumos empowers you to implement RBAC with precision. Define roles, assign corresponding permissions, and seamlessly enforce these across your organization. This approach minimizes the risk of over-privileged users and ensures adherence to the principle of least privilege.
- Access Review: Lumos's access review feature empowers your team to maintain airtight security by regularly reviewing and managing user access to critical resources and data. This feature eliminates the risk of unauthorized access, reduces data breaches, and ensures compliance with industry regulations.
- Policy Enforcement and Compliance: Lumos lets you define access policies aligned with your compliance requirements. The solution actively enforces these policies, ensuring only authorized users access sensitive data or systems.
- Real-time Visibility and Auditing: Lumos provides real-time insights into user activity and access patterns. With comprehensive audit trails and monitoring capabilities, you can quickly identify any suspicious behavior or potential security breaches. This proactive approach helps maintain a robust security posture.
- Intelligent Analytics: Lumos's intelligent analytics offer actionable information about access patterns, user behavior, and potential risks. This empowers you to optimize access management strategies and continuously enhance security.
Customer rating
- G2: 4.8/5
11. ForgeRock Identity Governance
ForgeRock's Identity Governance solution offers a holistic approach to identity management, enabling you to efficiently control access, maintain compliance, and strengthen security.
In addition, ForgeRock's IGA solution supports various MFA methods, adding an extra layer of protection to user accounts. This reduces the risk of unauthorized access, even in the event of compromised credentials.
Key Features
- Automated Access Management: ForgeRock's IGA solution simplifies user access management by automating the entire process. It intelligently provisions, revokes, and updates user privileges based on predefined policies and user attributes. This automation enhances efficiency and reduces the risk of human errors that could lead to security breaches.
- Comprehensive Compliance: The solution provides comprehensive auditing and reporting capabilities, ensuring that your organization adheres to industry standards and regulations. With detailed logs and customizable reports, you can confidently demonstrate your compliance posture during audits.
- Role-Based Access Control (RBAC): ForgeRock's IGA solution allows you to define roles and associated permissions, making it easier to grant appropriate access to users based on their job responsibilities. This improves security and enhances operational efficiency by eliminating unnecessary access requests.
- Self-Service Capabilities: ForgeRock's self-service portal enables users to request access or permissions themselves, freeing up your IT teams from manual request processing. The solution includes built-in approval workflows, ensuring that all access requests are appropriately reviewed and approved.
- Identity Lifecycle Management: Effectively manage user identities throughout their lifecycle with ForgeRock's IGA solution. From onboarding to offboarding, you can ensure that user access is provisioned and deprovisioned promptly and securely. This minimizes the risk of orphaned accounts and unauthorized access.
- Customizable Workflows: With its customizable workflows, you can tailor access request and approval processes to align with your organization's specific requirements. This flexibility ensures that the solution seamlessly integrates into your existing operations.
Customer rating
- G2: 4.4/5







.png)

.svg)














