The ISO 27001 access control policy ensures that only authorized users can access the required SaaS app and its data. The primary goal of this compliance standard is to establish a well-controlled access environment. In which the allocation of access to the organization's SaaS app and its data is solely based on the necessity of individual users.
So, to adhere to this compliance standard, your IT team needs to conduct user access reviews on a periodic/regular basis. By doing so, they can effectively control, manage, and govern the entire organization's access landscape.
What benefits can you avail for adhering to ISO 27001? Meeting ISO 27001 compliance standards comes with numerous advantages.
- It strengthens security by enabling your IT team to control and manage who has access to what, effectively lowering the risk of data breaches and unauthorized access attempts.
- Another advantage of complying with ISO 27001 is reputation protection. In the event of a security breach, having effective access control management reduces the potential for penalties and helps minimize the negative PR impact of such an event.
Now, what if your organization doesn't adhere to ISO 27001? What consequences can one even face?
- Neglecting to comply with ISO 27001 can have some severe consequences. For instance, it's like handing out keys to your door to anyone who asks, essentially inviting potential attackers into your systems.
- The repercussions of such negligence can cause data loss, legal and regulatory fines/penalties, revenue decline, and, in the most severe instances, even pose risks to lives and lead to the closure of your organization.
So, to avoid these consequences, it is advisable to comply with ISO 27001 standards. Here's a quick brief on how your IT team can meet ISO 27001.
Focus On These Key Aspects To Comply With ISO 27001
To adhere to ISO 27001 compliance standards, your IT team needs to focus on certain key aspects related to user access management; these include:
- User Access Lifecycle: Establish a clear process for managing user access from when an individual joins your organization until they depart. This should include procedures for granting, modifying, and revoking access privileges as necessary.
- Requesting Access: Develop a systematic way for users to request access to various systems, applications, or resources. This could involve creating a formal request system where users specify their needed access.
- Approving Access Requests: Implement a flexible approval process but ensure only authorized personnel can grant access. This typically involves managers or supervisors verifying that the requested access aligns with the user's job responsibilities.
- Implementing Access: Once access is approved, ensure a structured approach to implementing it. This may involve provisioning user accounts, modifying access permissions, and setting up necessary security control policies.
- Managing Changes to Access: Users' roles and responsibilities can change over time. Establish protocols for managing these changes, including updating access permissions, revoking unnecessary access, or granting additional access as required.
- Monitoring Access: Regularly monitor user access to detect any anomalies or unauthorized activities. Utilize security tools and logs to monitor who is accessing what and when. This proactive monitoring helps identify potential threats.
- Revoking Access: When a user no longer requires access or leaves the organization, ensure access has been revoked promptly. This is critical to prevent unauthorized access after an individual's role has changed or they've left the company.
By addressing these security requirements of user access management effectively, your IT team can seamlessly comply with ISO compliance and ensure that access to your organization's systems and data is controlled, secure, and aligned with regulatory standards. So, let's move further and see how user access review helps meet ISO 27001 compliance requirements.
Here’s How User Access Review Helps Achieve ISO 27001 Compliance Standard
Basically, ISO 27001 includes Annex A, which provides a set of controls that your IT/GRC team needs to consider implementing in your information security management system (ISMS). One of these controls is a "periodic review of access rights." This means that it is mandatory for organizations to conduct regular access reviews to comply with ISO 27001 compliance standards.
Furthermore, it is important to implement Annex A control A.9.2.5 to ensure that all users who have access are authorized. This control serves as a security measure to ensure that access removal procedures are functioning correctly and to identify any unauthorized users with active access to the network.
Also, by conducting user access rights reviews, your IT team can mitigate the risk associated with disgruntled former employees, temporary employees, or contractors.
For instance, if an account remains active after an employee departs from the organization, there is a risk that the ex-employee could potentially misuse their existing credentials to gain unauthorized/inappropriate access to the network, applications, or sensitive data.
The consequences could range from unauthorized data access or disclosure to more severe scenarios involving malicious attacks on resources, data leaks, or the installation of malicious code.
So, depending on the size and complexity of the organization, the review of user access rights can take various forms, ranging from simple data extractions from the organization's active directory or similar directory services to the deployment of sophisticated toolkits and analytical methods. Let's proceed further and learn how your IT team can conduct a user access review.
Best User Access Review Practices For Ensuring ISO 27001 Compliance
Now that we've discussed why user access reviews are crucial for compliance and security, you might be wondering how to perform these audits. It can seem daunting, especially in a mid-sized business with many employees, each with access to numerous systems and applications.
Trying to manually review every IT permission in your company's network is nearly impossible. If your approach involves spending hours sifting through endless lists of accounts and access rights, you'll quickly find yourself overwhelmed and not making much progress.
So, by establishing the right foundations through an access management framework, you can narrow down the scope of the audit, reduce the number of decisions each data owner needs to make, and ensure that reviews are completed on time. This strategic approach simplifies the process and makes it more manageable.
Let's discuss a few strategies your IT team can implement to streamline user access review and comply with the ISO 27001 regulatory standard.
1. Implement Role-Based Access Control To Simplify User Access Review Process
RBAC is a system where your IT team assigns specific sets of permissions to different job roles, like sales, marketing, or design. So, when new users join, they automatically get the access privileges related to their job functions. This makes onboarding easier because instead of setting up accounts and permissions one by one, admins just put people in the right roles to give them all the IT tools they need.
Role based access control also ensures that when someone's job changes within the company, your IT teams revoke the employees outdated permissions and grant them new permissions for their new role. So, if someone goes from Sales to Support, they lose Sales permissions and gain support permissions. With RBAC, you don't need to manually check default permissions. This makes access reviews simpler because you only need to review special permissions that employees might have.
2. Set Up And Update Access Policy
Even though tools like RBAC can automatically give out permissions, it's still the organization's job to figure out what permissions people need for their jobs. To do this, the organization needs to make a set of rules called an access policy. This document explains what each group of users is allowed to access. The idea is to only give users the permissions they really need for their job and nothing unnecessary. If someone needs more permissions, that can be decided case by case.
But setting up access rules is not a one-time task. As your IT system and what users do change, your access policy should change too. For example, if your development team starts using a new tool, they might not need the old one anymore. Or if you make a new department for event planning, you might need to create new roles. The point is organizations keep growing and evolving according to the market trend, and so should the rules about who can do what.
3. Decide How Often The Access Review Should Take Place
Once you come to a conclusion about who will do the access reviews and what they'll check, you need to plan further how often these reviews will take place and when. Basically, this depends on the compliance requirements that you need to follow and how precise the review needs to be.
To work as an effective safety measure, your team needs to conduct regular reviews. However, you can choose different review frequencies for different organizational IT resources. For instance, you might want to review critical financial data more often than others.
4. Make Sure To Record The Audit Results
Keeping a record of what your reviewers discover during access reviews is important. It's not just about following rules; it can also help your IT team identify possible problems with the access review process or how specific IT systems are managed. For example, if your team often shares files with outside contractors and forgets to take back access until the next review, maybe you need a better way to keep track of shared files.
Now that you are familiar with the effective user access review strategies, let's move ahead and look for an ideal IGA platform that will simplify the access review process. Managing user access reviews manually can be challenging, especially for IT teams in large organizations.
Although various IGA solutions are available to automate this process, but one particular solution that stands out is Zluri. What exactly is Zluri, and how can it assist your IT team in complying with regulatory standards? Let's take a quick look.
Stay Compliant With The Ever-Changing Regulatory Standards With Zluri IGA
Is your IT team struggling to effectively conduct access review, which is a mandate to meet ISO 27001 compliance requirements? If yes, look no further, as Zluri, a modern, automated, and autonomous identity governance and administration platform, emerges as a solution to address this critical compliance issue.
Zluri IGA is designed to simplify the access review process to adhere to ISO 27001 compliance. How does it do that? Well, it offers a wide range of exclusive features, such as automated access review, auto-remediation, activity and alerts capabilities, and more; with the help of these features, your IT team can effectively manage user access and meet the stringent requirements set forth by the ISO 27001 Annex A.
To help you gain more clarity on how Zluri IGA works, let's take an example:
B is an intern in your organization, and he was told to explore different departments to learn every bit of the company. So, whichever department he goes to, he gets access to all related SaaS apps and systems.
If B is fortunate, the company might offer him a permanent position after his internship. Now, B is still an intern and has yet to get converted into a full-time employee, but he still retains all the permissions he accumulated along the way.
Even though B doesn't intend to misuse those access permissions, there is still a risk that can’t be ignored. What if B accidentally clicks on a phishing link, and his account falls into the wrong hands? The more privileges a user has, the more severe the potential consequences of malware attacks and data breaches become.
So what Zluri does to avoid such a scenario is it conducts frequent reviews and helps your IT team revoke access permissions from users/employees that it no longer requires. Also, it auto-remediates access permissions if critical users or critical apps are not involved.
This example hints at how Zluri's advanced capabilities help your IT team manage, control, and govern user access and adhere to critical regulations like ISO 27001. However, there is yet to explore more, so let's get into details on how Zluri IGA's exclusive features help in maintaining data security and ensuring ISO 27001 compliance seamlessly.
- Discover User Access Data Without Any Hassle With Zluri’s Data Discovery Engine
The manual process of collecting insights regarding user access to SaaS apps is susceptible to errors and inaccuracies. Moreover, not to mention the repetitive back-and-forth that IT teams go through to cross-check each data point.
So, this is where Zluri's data discovery engine capability steps in as the solution, providing full visibility into user access data. This advanced feature enables your IT team to conduct a thorough analysis of how your organization’s users interact with SaaS apps, data, and critical systems and gather insights based on it, saving your IT team's productive time while ensuring accuracy.
Furthermore, Zluri utilizes five discovery methods: SSO or IDP, finance systems, direct integrations, browser extensions (optional), and desktop agents (optional). These methods enable IT teams to obtain in-depth insights into user access contexts.
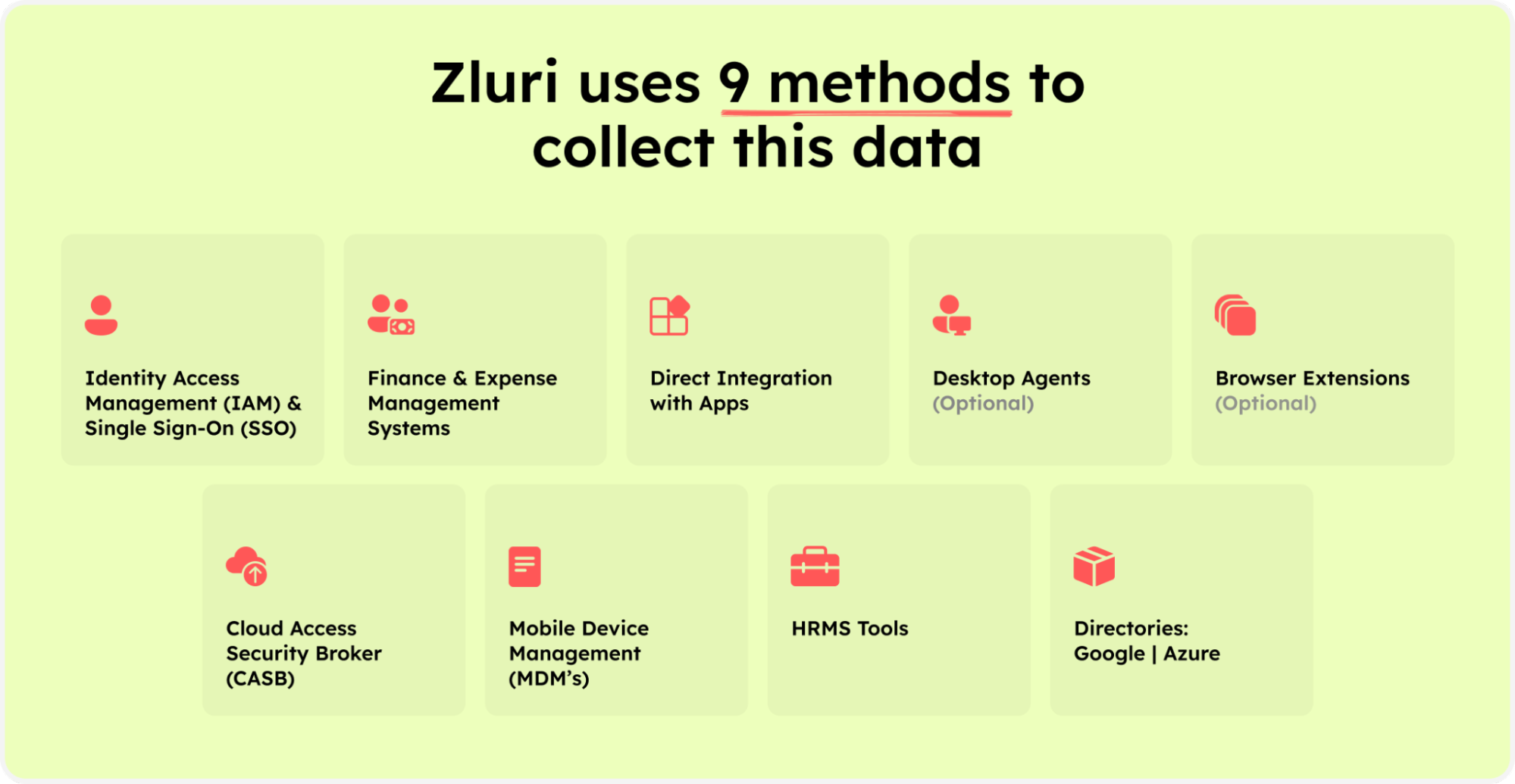
Zluri’s nine discovery methods
They can easily identify which user has access to which applications, their login/logout time, whether the user status is active or inactive, which department the user belongs to, the level of access permissions they possess, and more.
Furthermore, with the help of these detailed data points, your IT team can proactively monitor user activities and identify any suspicious user behaviors or anomalies. By detecting potential insider threats early, your IT team can take corrective measures to prevent breaches, data leaks, and other security risks.
Not only that, it also automates the process of identification of managed, unmanaged, and shadow IT apps. This automation eliminates the need for manual efforts in categorizing SaaS apps and documenting user access information, significantly saving time and resources.
Also, identifying user access data allows your IT team to have a view of who has access to what. This transparency ensures that access is granted based on defined roles and responsibilities, and further, it helps streamline the user access review.

- Simplify The Complex Process Of Adhering To Compliance Standards With Zluri’s Access Review Capabilities
Staying compliant with evolving regulatory standards can be a task to manage for the GRC/IT team. But not with Zluri IGA, it offers exceptional access review features to help your GRC/IT team simplify the user access review process and adhere to ISO 27001. With this feature, your IT team ensures every employee has the right access to the right SaaS apps, data, and system with the right level of access permission at the needed time while maintaining data integrity.
It performs regular/periodic access reviews to ensure access rights align with employees' roles and responsibilities and prevent unauthorised access by evaluating access patterns and user behavior. Also, with Zluri, your IT can ensure all the compliance frameworks requirements are met and become ready for upcoming audits.
Not only that, Zluri takes it a step further by offering unique capabilities to help your IT streamline the entire access review. So let's understand in detail how Zluri's access review capabilities function.
- Unified Access Review
Zluri's unified access review feature enables your IT team to determine which users have access to particular SaaS apps, data, and critical systems. To gain this insight, Zluri utilizes an access directory that centralizes all user access-related data in one centralized place.
With the valuable data points provided by the access directory, such as what access permissions the user has (admins, users, or others), which department or position they are from, and more, your IT team can thoroughly examine users' access privileges and ensure they align with their designated roles.
Furthermore, to keep the operation running smoothly, Zluri's activity & alerts capabilities come as a great help. This feature provides real-time data on users' recent activities and notifies IT teams about new logins or any suspicious actions attempted by unauthorized users.
Armed with all these data points, reviewers can quickly make decisions during access reviews, ensuring that the right users continue to have the right access privileges until the end of their tenure.
- Automated Access Review
With Zluri, your IT team can automate the entire access review process; they create a certification, select the apps and users you want to review, and the rest of the reviewers will review and update you about the compilation via email.
So, by automating this process, you get 10 x better results than manual methods and save your IT team's efforts by 70%. Now let's move ahead and see how it works.
Now, let’s take Azure AD as an example to see how you can automate access review in Zluri.
So, don't wait any longer! Book a demo now and see for yourself how Zluri enables your IT team to effectively control, manage, and govern user access while ensuring data security and adhering to evolving compliance standards.
Also Read: How User Access Review Helps Organization Adhere To SOX Compliance









.svg)



.svg)
.svg)
.svg)
.svg)

.svg)

.svg)

.svg)
















.webp)







.webp)
.webp)





.webp)