IGA solutions manage identity lifecycles, ensure compliance, and reduce security threats. While Netwrix IGA has been reliable, it's crucial to explore alternatives that better fit your IT team's evolving needs and organizational growth.
Netwrix provides a SaaS-based Identity Governance and Administration (IGA) solution, automating and overseeing enterprise identities for robust control and governance. However, you might find that Netwrix doesn't quite meet all your specific needs. It could be due to its pricing, features, or the level of support offered. This can leave you feeling frustrated, as ensuring your IT environment's security and compliance is critical.
Thankfully, there are alternatives to Netwrix that can better align with your organization's needs. Exploring these options can help you find a tool that offers more user-friendly interfaces, customizable features, and comprehensive reporting. By switching to a more suitable solution, you can enhance your IT security, ensure compliance, and streamline your auditing processes.
To make an informed decision, it is imperative to understand both the features and limitations of Netwrix comprehensively.
Key Features Of Newrix IGA Platform
Netwrix Identity Governance and Administration (IGA) platform offers robust features designed to enhance identity lifecycle management, enforce compliance policies, and mitigate security risks. Key features of the Netwrix IGA platform include:
- Enhanced Identity Lifecycle Management: Netwrix facilitates seamless onboarding, role transitions, and offboarding through automated identity lifecycle management. This ensures the efficient and secure administration of user identities with minimal manual intervention.
- Holistic Access Governance: It helps you attain complete control over access rights, permissions, and entitlements, fostering robust governance and ensuring compliance across the organization. This comprehensive approach enhances security measures and regulatory adherence.
- Dynamic Role-Based Access Control (RBAC): It facilitates a sophisticated Role-Based Access Control system to assign and oversee access based on job roles. This mitigates the risk of unauthorized access and establishes a more secure operational environment.
- Robust Audit and Compliance Reporting: IT teams can generate intricate audit reports and compliance documentation to meet stringent regulatory requirements. This feature provides transparency into identity and access management activities, ensuring accountability and regulatory alignment.
- Proactive Policy Enforcement and Real-time Performance Monitoring: You can enforce compliance policies and monitor access activities in real-time. This dynamic approach allows for the swift identification and resolution of potential cyber threats or policy violations, enhancing overall risk management.
These advanced features collectively empower organizations to proficiently manage identities, ensure compliance, and fortify security measures in the ever-evolving landscape of today's business environment. Along with these features, it does have some drawbacks.
Potential Drawbacks Of Netwrix IGA Platform
While Netwrix Identity Governance offers robust features, it's essential to be aware of potential considerations before exploring Netwrix alternatives:
- Steep Learning Curve: The platform comes with a steep learning curve, requiring additional time and effort for your team to fully grasp its setup and maximize its usage. This might extend the implementation process and delay the realization of the tool's full capabilities.
- Specialized Training Requirement: Effectively managing the platform necessitates specialized training for your IT teams due to its intricate nature and the presence of numerous components. This training requirement can be time-consuming.
- Error Messages Complexity: In certain instances, the tool may present error messages during setup that could be challenging to interpret. This complexity may lead to confusion within your team, potentially impeding the tool's efficient utilization.
- Limited Integration Flexibility: The platform may pose limitations in terms of integration flexibility, which could impact its seamless incorporation with other systems in your organization. This limitation might require additional considerations when aligning the tool with existing IT infrastructure.
In light of the limitations and factors discussed above, let's delve into key considerations to consider when exploring alternatives to Netwrix.
Key Considerations Before Choosing Netwrix Alternatives & IGA Tools
Before you choose Netwrix alternatives and access governance tools, consider the following key factors:
- Functionality and Features: Evaluate whether the functionalities and features of Netwrix alternatives and access governance solutions align with your organization's specific access governance needs. Look for capabilities such as identity lifecycle management, access control, and compliance reporting solutions.
- Scalability: Assess whether the alternative solutions can scale according to your organization's growth. This is particularly crucial if you anticipate an increase in users, applications, or data over time.
- Integration Capabilities: Check how well the Netwrix competitors integrate with your existing IT infrastructure. A seamless integration ensures that the new solution works harmoniously with other systems in your organization.
- Customization Flexibility: Look for an alternative to Netwrix that offers flexibility in customization. The ability to tailor the access governance solution to your organization's unique requirements enhances adaptability and efficiency.
- User-Friendly Interface: Consider the user-friendliness of the alternative solutions. An intuitive interface and straightforward processes contribute to quicker adoption, reducing the learning curve for both administrators and end-users.
- Cost-Efficiency: Compare the overall cost of each alternative & Netwrix competitors, including licensing fees, implementation costs, and ongoing maintenance expenses. Choose a solution that provides value for money and aligns with your budget constraints.
- Vendor Reputation: Investigate the reputation of the vendors providing alternative solutions. A reputable vendor with a proven track record of delivering reliable access governance solutions is more likely to offer a trustworthy platform.
- Support and Training: Explore the support and training options provided by the alternative solutions. A responsive support team and comprehensive training resources contribute significantly to successfully implementing and utilizing the access governance solution.
- Security Measures: Prioritize the security features of the alternatives to safeguard your sensitive access governance information. Verify that the solution complies with industry standards and regulations for data protection.
- User Testimonials: Seek Netwrix alternatives reviews and feedback from organizations implementing the alternatives. Insights from users with similar access governance needs offer valuable perspectives on each solution's performance, reliability, and effectiveness.
Each consideration plays a vital role in fortifying your access governance and identity security framework, spanning the evaluation of functional alignment and scalability to guarantee seamless integration and scrutinizing security features. By meticulously considering these elements, you can make well-informed decisions when selecting Netwrix alternatives, thereby bolstering your identity security framework.
List Of 10 Best Netwrix Alternatives & Competitors
Below are the 10 best Netwrix alternatives, each crafted to meet unique requirements, enhance operational efficiency, and fortify digital environments. These options present distinctive features tailored to tackle specific challenges, presenting organizations with diverse choices as they navigate the intricacies of identity governance.
1. Zluri
Zluri is transforming how organizations manage identity governance and access control. The platform effortlessly oversees user identities and access policies by offering an intelligent access management solution. Its robust integration with a variety of single sign-on (SSO) tools ensures strong authentication and authorization controls, all while maintaining continuous monitoring of user activities for compliance assurance.
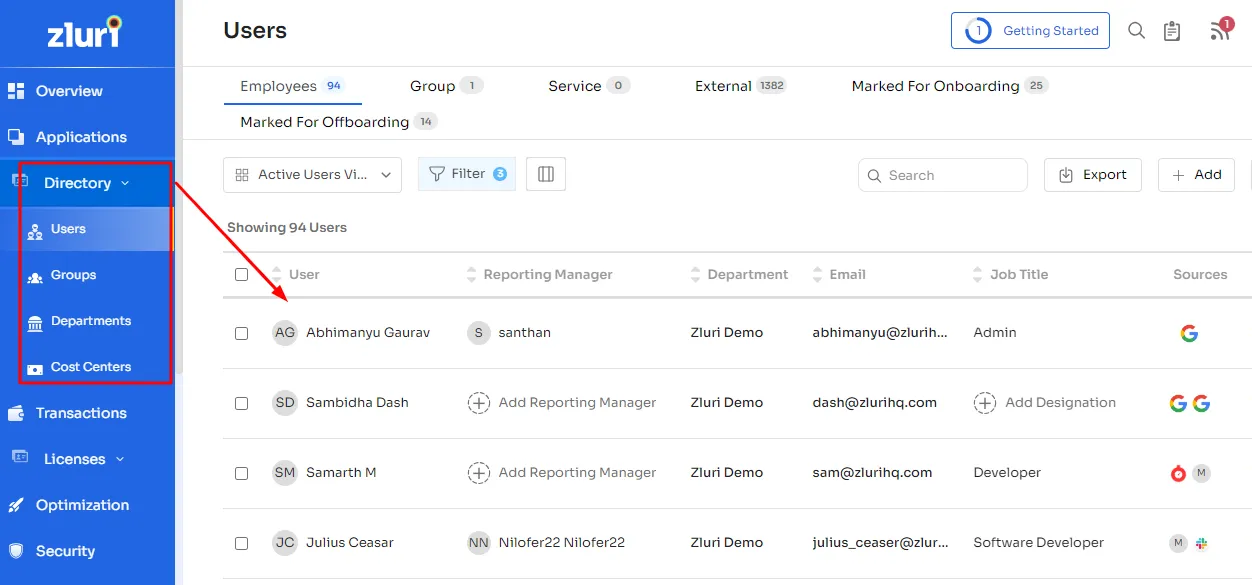
This integrated approach establishes a centralized access hub, streamlining the management and monitoring of privileged access. Whether granting or revoking access, the platform ensures a smooth and uncomplicated process.
It empowers users to promptly identify suspicious activities, such as unauthorized access, in real-time. In the event of such incidents, immediate actions can be taken to safeguard invaluable application data.
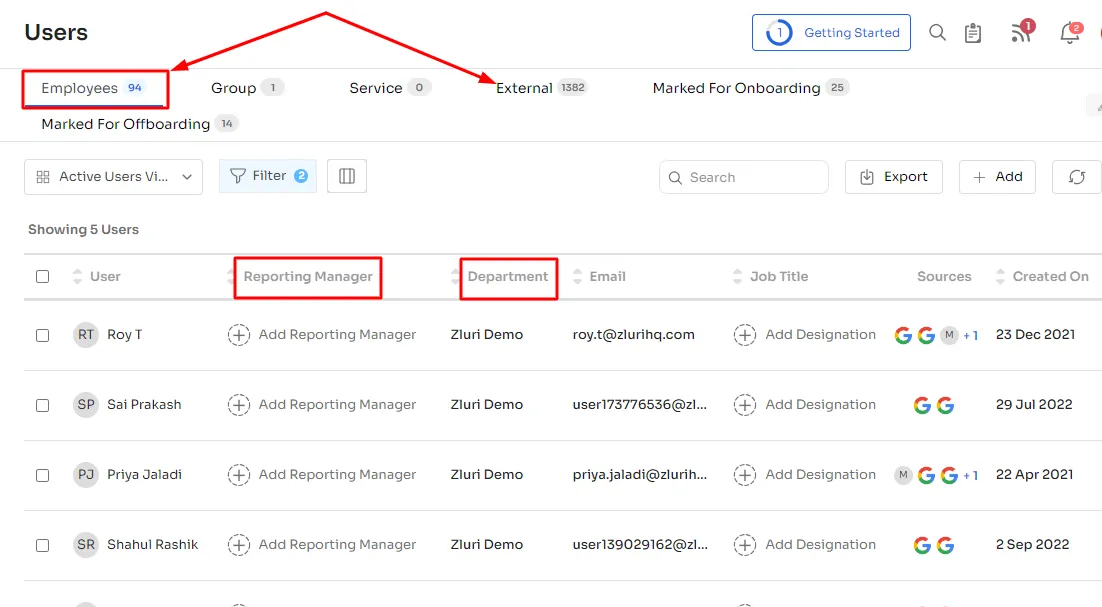
Zluri goes beyond the basics, providing additional features for precise control over user access. IT teams can customize each user's rights, ensuring only the right individuals can access crucial data, thereby preventing unauthorized access and enhancing overall security.
Key Highlights of Zluri's Access Governance Feature
- Discovery Engine for SaaS apps’ users and core Access Insights:
Zluri's Access Governance Feature encompasses a robust discovery engine that employs five methods to identify users with access to resources. This engine provides insightful analyses of SaaS applications and user-associated data, including single sign-on and identity providers.
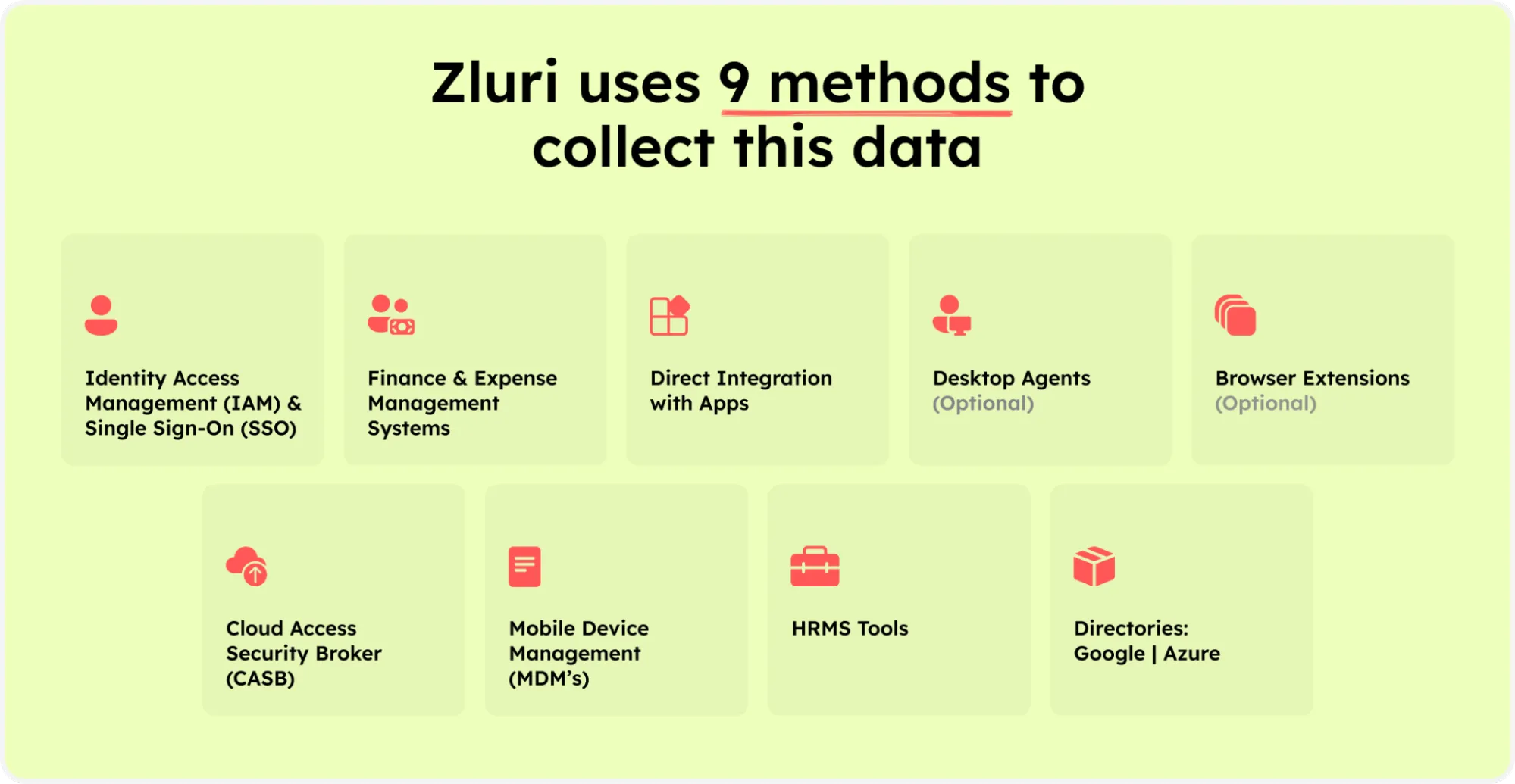
Zluri’s nine discovery methods
Also, as per Kuppingercole's research and analysis report, it reveals details such as application access, active user presence, granted authorizations, and user classifications for comprehensive insights.
- Automation Engine for Robust Identity & Access Governance:
The Automation Engine within Zluri reinforces access governance by overseeing access workflows. It ensures accurate authorization assignments and unwavering policy compliance.
Through automation rules and triggers, customized and self-sufficient access and review workflows are implemented, optimizing administrative procedures.
- User Lifecycle Management with Automation:
Zluri's approach to effective user lifecycle management involves streamlining the entire user lifecycle journey from onboarding to offboarding. It offers unified provisioning and de-provisioning capabilities and customizes workflows to ensure the right resources during a user's tenure while seamlessly revoking access when needed.
- Self-Serve Model for Ad-Hoc Access Requests:
Empowering organizations with the Employee App Store (EAS), Zluri enables self-serve ad-hoc access request management. This model streamlines the handling of ad-hoc requests, allowing IT teams to evaluate and grant temporary access. The user-friendly interface of EAS enables employees to track the status and updates of their requests, fostering transparency.
- Security & Compliance Maintenance through Access Certifications:
Zluri simplifies access control and reinforces compliance through centralized user access reviews. It provides comprehensive audit trails for clarity on resource access and incorporates automated access certifications, intelligent automation, auto-remediation capabilities, and real-time access reviews with anomaly detection.
Furthermore, Zluri incorporates AI-powered compliance insights and industry-standard certificate templates for robust compliance efforts.
Say goodbye to complex user management and embrace the simplicity and efficiency of Zluri. Schedule a demo right away!
Pros
- Zluri provides a centralized and intuitive platform, streamlining the administration of access rights to diverse applications and resources. This not only reduces administrative overhead but also enhances overall security.
- The tool plays a crucial role in helping organizations adhere to data protection regulations, reinforcing security practices. By ensuring that only authorized individuals access sensitive data and applications, Zluri actively contributes to compliance and robust security measures.
- Distinguished by its deep discovery capabilities and a unique SaaS data platform, Zluri stands out among existing Netwrix alternatives. It excels in delivering optimal performance and security within cloud-based environments, making it a standout choice for access management needs.
Cons
- Zluri may not be the most suitable choice for smaller organizations with fewer employees. The platform's features are predominantly designed to meet the demands of larger or mid-sized companies, potentially providing functionalities that surpass the requirements of smaller-scale operations.
Customer Rating
- G2: 4.9/5
- Capterra: 4.9/5
2. Okta Identity Governance
With Okta's Identity Governance, your IT team gains access to a powerful platform that effectively manages user access across diverse systems and applications. The platform simplifies the process of granting or revoking access to resources by consolidating all access controls into a centralized location. Its unified IAM and Governance solution elevates your security posture, mitigates modern security risks, and enhances overall efficiency.
Enhanced with robust auditing and reporting features, the platform enables close monitoring of user activities. This capability allows your team to track, analyze, and generate detailed reports on user actions, ensuring compliance with regulatory requirements during audits. Thus serving as one of the leading alternatives to Netwrix.
By leveraging Okta's Identity Governance, your IT team can optimize user access management, streamline administrative or repetitive tasks, reinforce security measures, and effortlessly adhere to industry regulations.
Pros
- The tool's user-friendly and intuitive interface enables effortless navigation and efficient management of user accounts, resulting in a streamlined experience for your IT teams.
- Okta's SSO seamlessly integrates with a wide range of applications and systems, ensuring smooth authentication and access management processes within your organization.
Cons
- The platform's setup process can be challenging, resulting in complexity for your team and additional time spent on configuration, delaying user access management.
- If you operate in a mid to large organization, Okta may not be the most suitable choice due to the potential costliness of its API rate limiting tiers when scaling up. As your organization grows, the expenses associated with maintaining these tiers can significantly increase.
Customer Rating
- G2: 4.5/5
- Capterra: 4.7/5
3. Lumos IGA
Lumos IGA stands as a robust tool that revolutionizes compliance management, empowering your team to excel in identity governance and administration (IGA). By offering a comprehensive suite of features, Lumos IGA addresses the intricacies of compliance and enables your team to navigate the regulatory landscape easily.
One of the primary areas Lumos IGA focuses on is authentication, ensuring that users are securely and accurately identified before granting access to resources.
With robust authorization capabilities, the tool enables your team to effectively control and manage user permissions, allowing for granular access controls that align with your organization's policies and regulatory requirements. Moreover, regulatory compliance is at the core of Lumos IGA's capabilities. The tool assists your team in monitoring, documenting, and enforcing compliance solutions with various regulations and industry standards.
Pros
- The tool's user-friendly interface offers significant advantages for your IT teams. It ensures ease of use, allowing team members to navigate and operate the tool effortlessly, ultimately enhancing productivity within the team.
- It provides an auto-provisioning feature that revolutionizes the user-provisioning process. Automating the setup and configuration eliminates the need for manual intervention. This feature saves your team valuable time and guarantees consistent and precise provisioning across all your systems and applications.
Cons
- Lumos lacks transparent pricing information (such as their plans and pricing tiers) on their website, which can cause confusion and make it difficult to compare Lumos with other tools in the market.
Customer Rating
- G2: 4.8/5
4. Fischer Identity
Fischer Identity offers your IT team a centralized platform that effectively manages identities, streamlining the complete lifecycle of user accounts. Your team can effortlessly create, modify, and deactivate user accounts, ensuring access aligns seamlessly with your business needs and regulatory requirements.
This robust solution empowers your team to define access policies and rules based on user roles, responsibilities, and business requirements. Using a role-based access control approach, Fischer Identity minimizes the risk of unauthorized access and strengthens compliance measures.
Furthermore, Fischer Identity offers self-service capabilities, enabling users to request access and obtain approvals through a simplified workflow. This self-service functionality enhances user convenience and reduces administrative burden. The solution goes beyond access management by generating comprehensive audit logs and reports. These logs facilitate regulatory compliance assessments and provide valuable visibility into access activities.
Pros
- The tool offers great implementation support to your IT teams, even in the most intricate systems. With their expertise and guidance, your IT teams can navigate through complex setups and configurations effortlessly, ensuring a smooth and successful implementation process.
- If you're seeking a tool with a seamless workflow engine, this can be a suitable choice. It offers an efficient workflow engine that automates access management and enables user access tracking for audit purposes.
Cons
- The tool has a steep learning curve, necessitating a significant time investment from you and your team to fully grasp and utilize its capabilities.
- Moreover, there's a limitation in seamless integration with your existing tools, potentially impeding your team's efficiency in managing access and obtaining crucial audit data.
Customer Rating
- G2: no reviews
5. One Identity Manager
One Identity Manager empowers your IT team by governing and securing data and users, meeting uptime requirements, and mitigating risks. It ensures compliance by granting users access to the necessary data and applications they need. Centralizing identity and access management, the software streamlines processes and ensures consistency throughout the organization.
It facilitates efficient provisioning and deprovisioning of user accounts, simplifies the management of user roles and permissions, and enforces robust authentication methods.
Furthermore, One Identity Manager offers advanced features for access governance, including access certifications and compliance reporting. These capabilities enable your IT team to conduct regular reviews and validate access rights, ensuring adherence to regulations and internal policies.
Pros
- This tool is ideal if you're seeking a platform that is easier to implement. It offers a streamlined and efficient implementation process, allowing for a smoother deployment that saves valuable time and resources for your IT team.
- The tool offers strong support for seamless integration with a wide range of cloud-based applications, facilitating efficient connectivity and centralized management. This promotes smooth collaboration and simplified access control throughout your organization's cloud ecosystem.
Cons
- Its product documentation lacks important details for certain modules, which can impede your team's or end-users' comprehension and implementation of those specific features, potentially leading to challenges in utilizing the tool to its best.
- The platform lacks a self-service portal, meaning users cannot independently request access for themselves, groups, or specific roles. This limitation requires additional manual work from your IT teams and may result in delays in granting access to users.
Customer Rating
- G2: 3/5
- Capterra: 5/5
6. JumpCloud IGA
JumpCloud's IAM and IGA platform provides a comprehensive solution for managing identities, securing access, and ensuring compliance across your organization's systems and applications. Its centralized platform simplifies identity management processes, streamlining the entire lifecycle of user accounts.
One of the key strengths of JumpCloud's IGA platform is its ability to support a wide range of IT resources, including both on-premises and cloud-based systems. This flexibility enables your IT team to manage user identities and access across diverse environments from a single console, reducing complexity and enhancing operational efficiency.
Additionally, JumpCloud's IGA platform provides comprehensive auditing and reporting features. It tracks user activities, generates detailed reports, and helps meet compliance requirements by providing visibility into user access, changes, and other relevant events.
Pros
- The platform provides flexible deployment options, enabling your IT team to customize the setup process according to specific requirements.
- Seamlessly integrating with Google Workspace simplifies the management of user accounts, allowing for smooth provisioning and authentication, optimizing productivity and ensuring a seamless user experience.
- Additionally, it offers efficient device management capabilities to streamline the process of managing and maintaining devices, allowing admins to focus on more strategic initiatives. Thus, it contributes to a more streamlined workflow and improved operational efficiency.
Cons
- This may not be ideal if you have budget constraints or are looking for more cost-efficient options. The tool's pricing is relatively high as an additional cost is attached for the advanced features, impacting its affordability and cost-effectiveness.
Customer Rating
- G2: 4.5/5
- Capterra: 4.7/5
7. Saviynt IGA

Saviynt IGA is an extensive IGA platform that prioritizes seamless user application and infrastructure access while maintaining strict compliance. It simplifies the identity governance and administration (IGA) process by leveraging automation and intuitive workflows to enhance organizational agility.
With Saviynt IGA, users can effortlessly access applications and infrastructure, ensuring uninterrupted productivity. The tool streamlines IGA operations by automating essential processes and employing intuitive workflows, making identity management more efficient and user-friendly.
In addition, Saviynt IGA ensures compliance by implementing robust controls and policies. It assists organizations in meeting regulatory requirements, enforcing segregation of duties (SoD), and preventing unauthorized access, thereby reducing the risk of compliance violations.
Pros
- The platform's extensive collection of out-of-the-box connectors enables seamless integration with various applications and systems, eliminating the need for complex custom integrations and saving valuable time and resources for your team.
- With its intuitive and well-designed interface, the tool gives your team a user-friendly experience, allowing them to effortlessly navigate and utilize its extensive range of features to maximize their productivity.
Cons
- Certain system features may experience malfunctions, leading to capability issues for your team. For example, when users switch roles, their entitlements should be updated accordingly. However, in some cases, Saviynt fails to properly re-issue entitlements, leaving users without any entitlements and causing identity management complications.
Customer Rating
- G2: 3.5/5
- Capterra: 4.5/5
8. Omada Identity
Omada Identity offers a streamlined solution to enhance identity governance within your organization. With robust features, Omada Identity empowers your team to manage identities and access privileges efficiently.
The platform consolidates identity data, establishing a centralized hub for all user-related information. This single source of truth provides comprehensive visibility and control over user access across diverse systems and applications. With this holistic view, you can effectively monitor and govern user access, mitigating the risk of unauthorized or inappropriate access.
In addition, Omada Identity simplifies and automates the entire user lifecycle management process. The platform offers intuitive workflows and role-based access controls from onboarding to offboarding. This ensures that users are granted appropriate access rights based on their specific roles and responsibilities, enhancing security and compliance while reducing administrative overhead.
Pros
- The tool's well-integrated and detailed approach enhances the ease of management and modification, empowering your IT admins to effectively tailor the tool to your organization's needs.
- Its user-friendly approach and swift access enablement contribute to your admins' seamless account management experience, ensuring efficient and effective user access management in your organization.
Cons
- The tool's interface lacks smoothness, hindering efficient user access management and resulting in time-consuming delays that impact your team's productivity.
- The initial setup process is time-consuming, which may hinder user access's smooth and timely management, affecting users' productivity within the organization.
Customer Rating
- G2: 3.8/5
9. Bravura Identity
Bravura Identity offers a seamless IAM and IGA solution for managing the entire identity lifecycle. From user onboarding and provisioning to access certification and offboarding, the platform provides a centralized view of user identities and their access rights.
With Bravura Identity, you can enforce granular access controls, ensuring users only have access to the resources necessary for their roles. The platform provides a user-friendly interface for configuring role-based access controls, implementing segregation of duties, and establishing approval workflows.
One of the standout features of Bravura Identity is its detailed audit logs, which capture all changes made to user accounts and access rights. This feature enables your team to track user activity, monitor access requests and approvals, manage data governance, and generate compliance reports for internal and external stakeholders.
Pros
- The tool's workflow for processing requests, including the approval process and delegation capabilities, functions exceptionally well, providing your IT team with a smooth and efficient experience for managing and handling requests.
- If you're looking for an easy-to-use tool, this solution is well-suited for your team. It allows for seamless adaptation and enables effective governance, risk prevention, and compliance maintenance, maximizing its full potential.
Cons
- The platform requires significant time for customization according to your specific requirements. This can limit your team's ability to focus on other important tasks, potentially impacting productivity.
- The tool's heavy reliance on components for proper functionality can lead to issues if any of them are unavailable or encounter problems. This dependency introduces vulnerabilities and stability concerns for your IT team.
Customer Rating
- G2: 4/5
- Capterra: 4.2/5
10. Symantec IGA
Symantec IGA offers a comprehensive suite of access governance and identity management capabilities. With this solution, you can seamlessly manage user access to both on-premise and cloud applications. The platform automates the provisioning of new entitlements and the removal of unnecessary ones throughout the identity life-cycle, simplifying access management processes.
Symantec IGA also includes self-service functionality, empowering end users to request new access, manage their profile attributes, and reset forgotten passwords. This self-service capability reduces the burden on your service desk, enhancing operational efficiency and improving user satisfaction.
Furthermore, the solution streamlines the access governance processes associated with reviewing and approving entitlements. By ensuring a least privileged access posture, Symantec IGA aids in maintaining a secure environment by granting users only the necessary access, minimizing potential risks.
Pros
- The tool provides a user-friendly interface, enabling your IT teams to easily adopt and use it with their existing systems. This convenience enhances efficiency and ensures a smooth transition for your organization.
- The tool provides robust reporting and auditing capabilities, enabling your team to track and analyze user activities, access permissions, and system events. This promotes tight access control throughout the organization.
Cons
- When encountering problems or errors, the tool may lack comprehensive troubleshooting features or detailed error messages, making it challenging for your team to pinpoint the root cause of the issue.
- The tool has difficulty in enforcing custom approvals, which can lead to inefficiencies and potential gaps in the overall access management process within your organization
Customer Rating
- G2: 3.4/5
- Capterra: 4/5
Choosing the Right Netwrix Alternatives for Your Organization
As we conclude our analysis of the best Netwrix alternatives & competitors, it's crucial to highlight the importance of a meticulous selection process. Making an informed decision requires a deep understanding of your organization's specific needs and a thorough examination of the available options. The ideal alternative to Newtrix should address your current requirements and allow you to adapt to your organization's growth and future challenges.
Effectively evaluate Netwrix alternatives by assessing their alignment with your needs, scalability, user-friendliness, data security measures, and compatibility with your budget. Ensure seamless integration with your existing tools and anticipate future scenarios. Additionally, seek insights from user reviews to make a judicious selection.
By adopting this approach, you will be well-prepared to choose an alternative that not only meets but surpasses your organization's evolving needs in the dynamic landscape of IT solutions.
FAQs
1. What is Identity Governance and Administration (IGA)?
Identity Governance and Administration (IGA) is a comprehensive approach to managing an organization's user identities and access rights. It encompasses processes and technologies that ensure the right individuals have appropriate access to critical resources, and it plays a crucial role in maintaining security and compliance.
2. Why Consider Alternatives to Netwrix IGA?
While Netwrix IGA is a robust solution, organizations may explore alternatives to address specific needs or preferences. These alternatives could offer unique features, scalability, or integration capabilities that align more closely with the organization's requirements.
3. What Criteria Should Be Considered When Evaluating IGA Alternatives?
When evaluating Netwrix competitors, consider factors such as scalability, ease of integration with existing systems, customization options, compliance features, and user-friendliness. It's essential to align the chosen solution with the organization's size, industry, and specific identity governance needs.
4. How Do These Alternatives Enhance Identity Governance?
Each alternative on the list aims to enhance identity governance by providing robust tools for managing user identities, access requests, and compliance reporting. These solutions often streamline workflows, automate provisioning and de-provisioning processes, and offer complete visibility into access rights across the organization.
5. Are These Alternatives Suitable for Small and Large Enterprises?
The Netwrix alternatives listed cater to a range of organizational sizes. Some may be well-suited for small to medium-sized enterprises, offering cost-effective solutions, while others may provide the scalability and advanced features required by large enterprises. The suitability depends on the specific requirements and scale of the organization's identity governance needs.







.png)

.svg)














