System for cross-domain identity management and just in time provisioning are popular web application provisioning strategies that help create and manage user accounts. Although they do share a similar purpose, the way they work varies. How? In this article, we’ll address that question, and along with that, we’ll also explore their (SCIM vs JIT) other differences.
Organizations often seek solutions that deliver precision while speeding up intricate processes like user account creation, updates, and deletions. Why so? The manual methods they rely on fall short of meeting these needs. They consume a significant amount of IT admins' time, demand relentless effort from them, and leave plenty of room for errors.
Imagine spending hours performing these tasks manually, only to realize that a mistake crept in. And now you have to re-do the entire process. All that time and effort goes down the drain. Frustrating, isn't it? No organization wants their IT admins to be caught in this endless loop of rework.
So, to address these challenges, web application provisioning methods (SCIM vs JIT) emerge as efficient alternatives to manual application provisioning methods. These methods automate intricate processes and deliver the desired outcomes without making extensive changes to your setup.
But you may question – ‘Which one will be more suitable?’ Now for that, you need to have a clear understanding of their (SCIM vs JIT) differences. So, let’s explore what sets them apart.
But before that, let’s quickly go through SCIM vs JIT provisioning’s overview to gain a basic understanding of the concepts.
Overview of SCIM & Just In Time Provisioning
System for cross-domain identity management provisioning, also widely known as SCIM provisioning, is a method of leveraging REST API (representational state transfer application programming interface) and HTTP (hypertext transfer protocol) to automate the creation, updation, and deactivation of user accounts across multiple web applications and domains.
On the other hand, just in time provisioning, also commonly known as JIT provisioning, is a method that leverages SAML (security assertion markup language) protocol to solely automate the creation of user accounts on-the-fly within web applications.
Now that you are familiar with the basics of SCIM vs JIT provisioning, let’s dive into the comparison to gain more clarity on what sets them (SCIM vs JIT) apart.
SCIM vs JIT Provisioning: Differentiation Based On Distinct Parameters
Below we’ve compared SCIM vs JIT provisioning web application provisioning methods based on different criteria in a detailed manner.
1: SCIM vs JIT Provisioning Functionality Difference
SCIM vs JIT provisioning both have a distinct way of sharing/syncing user details between two systems and authenticating those details to create, update, or delete user accounts. So, let's find out how SCIM vs JIT provisioning functions.
- This is how the system for cross-domain identity management (SCIM) provisioning works.
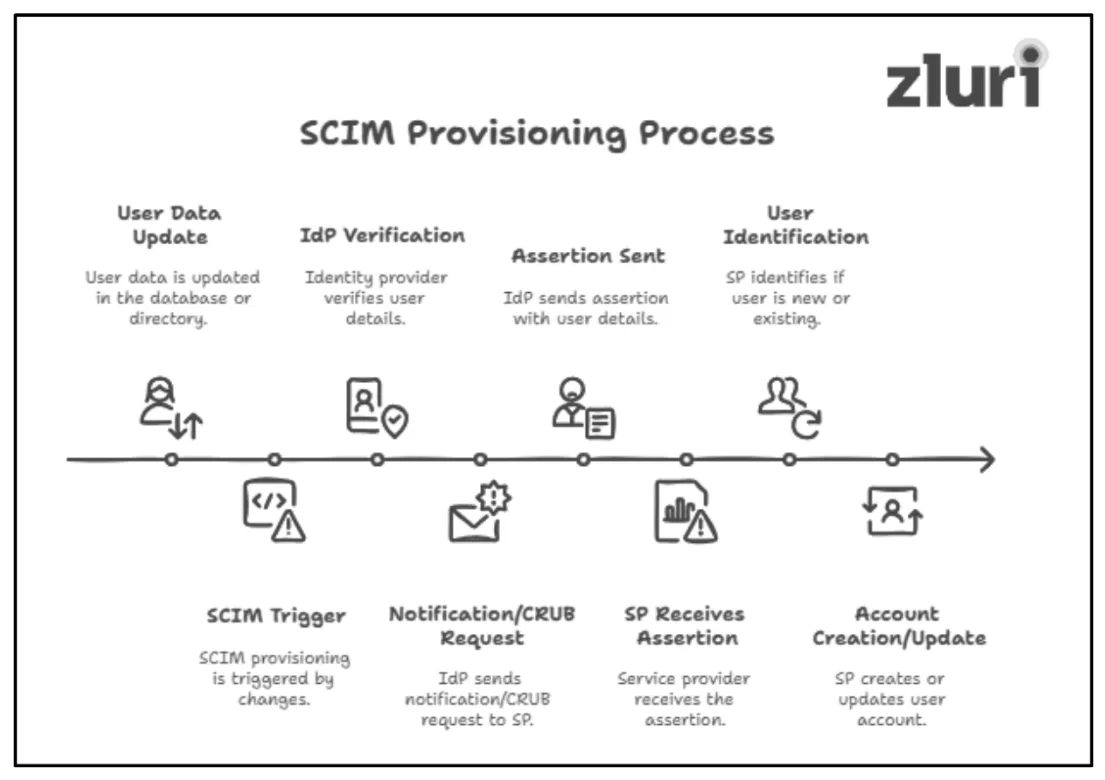
Step 1: When a new user is added, or any changes are made to the user's details, their data is automatically updated (or you can manually update the data) in the organization's database or identity provider's directory. Now, whenever any new changes in the directory occur, SCIM provisioning gets triggered (you have to configure the systems before enabling these actions).
Step 2: Next, the identity provider (IdP) verifies the details and directly sends notification/CRUB requests along with assertion (that includes authentication token and user details like name, ID, or role) in a standardized form (defined by SCIM) to the service provider (SP)/your application.
Also Read: Identity Providers: What They Are & How Do They Work?
Step 3: Once the app (service provider) receives the assertion, it processes the data to determine whether the user is new or existing (it checks the unique ID to track that down). Based on the details, it creates an account for new users and updates the details for existing user accounts.
- On the other hand, this is how the just in time (JIT) provisioning works.
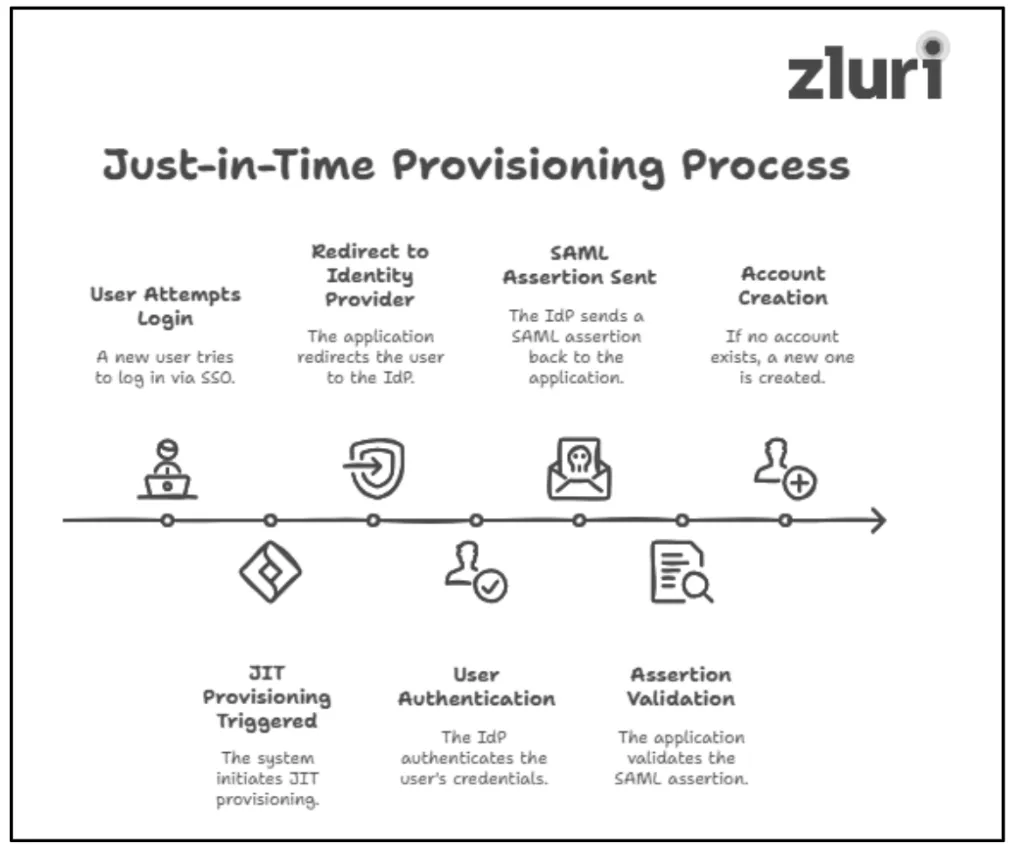
Step 1: When a new user attempts to log in to an application via single sign-on (SSO) for the first time, just-in-time provisioning is triggered (similar to SCIM provisioning, you have to configure the systems well in advance to enable these actions).
Step 2: The application (service provider) redirects the user's login requests to the identity provider (IdP), which authenticates the user's entered details.
Also Read: Types of Authentication Methods (Digital Authentication Methods)
Step 3: Once successfully verified, the IdP sends a SAML assertion back to the application (SP). This assertion contains the authentication token and the user's details, such as user identity (e.g., username), user attributes (e.g., user roles and permissions), and other relevant information.
Step 4: After that, the app (SP) validates the SAML assertion and checks its database to determine whether the user identity already has an account. If no match is found, the app uses the SAML assertion information to automatically create a new account for the user.
Note: Both SCIM vs JIT provisioning automatically synchronizes/updates the same user data in both the identity provider and service provider systems simultaneously to eliminate data inconsistency.
However, SCIM provisioning synchronizes data between IdP and SP prior to performing any actions (creation, updation, or deletion of user account). Meanwhile, JIT provisioning synchronizes data between IdP and SP during the account creation process (basically, when it receives the user details, it syncs the data between both systems at that very moment).
2: Difference Between SCIM vs JIT Provisioning Protocol Dependency
By understanding the SCIM vs JIT provisioning protocol dependency, you can determine which method uses a protocol that is compatible with your organization setup.
Note: Generally, organizations prefer to opt for a web application provisioning method that uses familiar protocols (as in, the IT team is familiar with them or the organization is already using them) as it not only simplifies the integration part (integration with existing setup/apps) but also speeds up the implementation process.
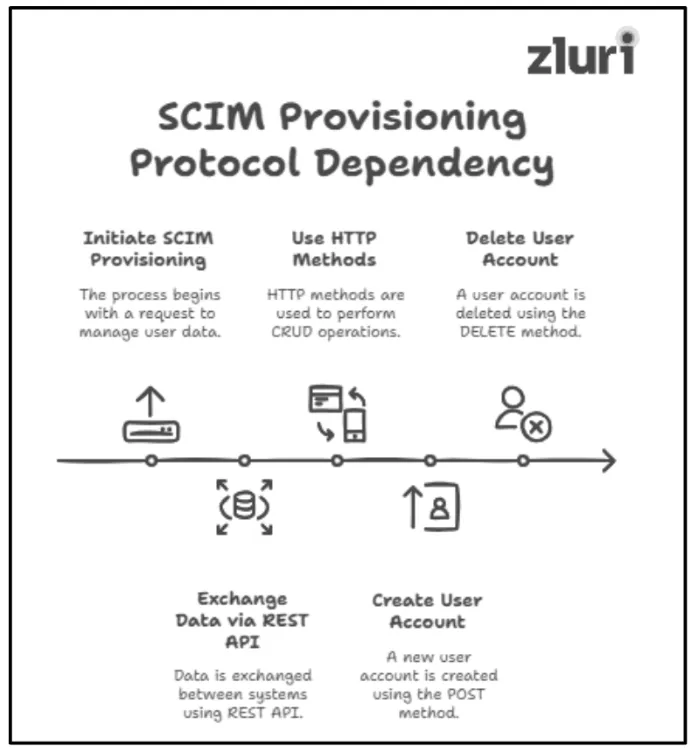
- SCIM provisioning relies on REST API to exchange user identity data {in a data format called JavaScript Object Notation (JSON)} between two systems: enterprise identity provider and cloud service provider over the Internet. Additionally, SCIM provisioning further uses HTTP request methods (POST, GET, PUT/PATCH, and DELETE methods) to perform CRUD operations (create, read, update, and delete actions).
For instance, when you want to ‘create’ (CRUD operation) a new user account, you can use the ‘POST method’ (HTTP request method). If you want to ‘delete’ (CRUD operation) a user account, you can use the ‘DELETE method’ (HTTP request method).
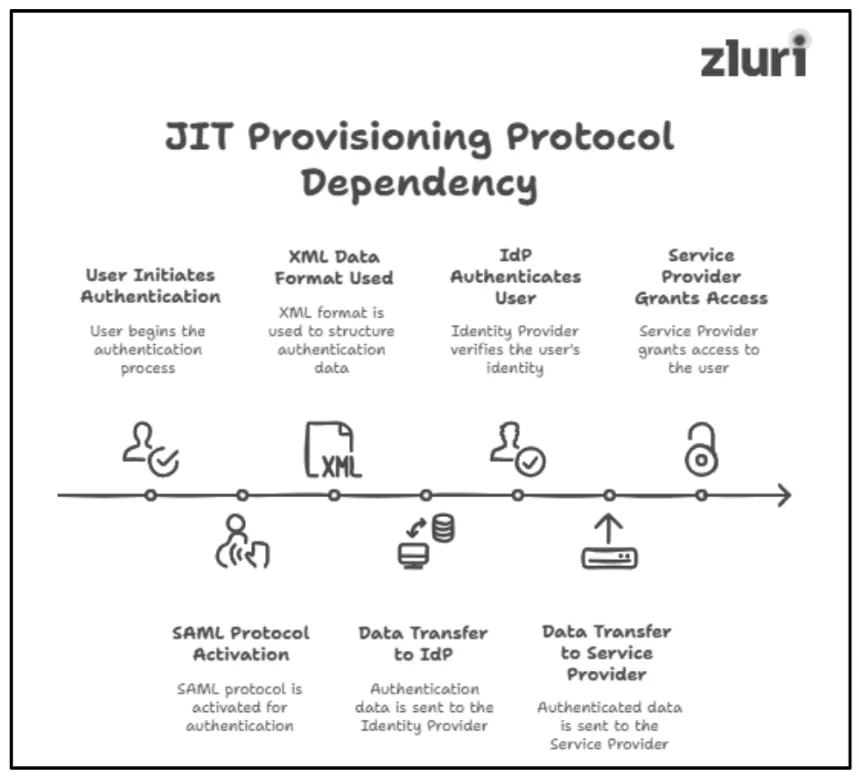
- Meanwhile, JIT Provisioning relies on SAML protocol, which is an open standard used for authentication (authenticating user’s identity for service providers) purposes. It leverages a specific type of data format called extensible markup language (XML) format to transfer/share user authentication details between two parties, i.e., the identity provider (IdP) and the service provider.
3: Comparison Between SCIM vs JIT Provisioning Key Benefits
SCIM vs JIT web application provisioning offers unique benefits, for example:
- SCIM provisioning offers the following benefits:
- By using a standardized way of sending data (e.g., using JSON payloads) and pre-setting addresses (endpoints) where this data should go, SCIM provisioning sets up a clear communication route between IdPs and SPs. This communication pathway enables IdPs and SPs to exchange users' data faster, which in turn helps accelerate the creation, updation, or deletion of users' accounts.
- SCIM provisioning can handle bulk CRUD (create, read, update, delete) requests, which means it can provision hundreds or even thousands of user accounts at once.
- Whereas JIT provisioning offers the following benefits:
- SAML JIT provisioning eliminates the need to pre-configure user accounts for each web application by automatically creating them the moment a user logs in to an app for the first time. This, in turn, also saves IT admins time, allowing them to focus on other key aspects of business operations.
- When IT admins manually create user accounts, they sometimes unintentionally create duplicate accounts (accounts with the same user identity) and inactive accounts. This usually happens because they often manage multiple account creations at once. To top it off, they also don't clearly understand which users' accounts are already created. As a result, unnecessary user accounts accumulate over time. This clutters both the SP and IdP systems and increases potential security risks by expanding the attack surface.
However, SAML JIT provisioning addresses this by automatically checking for existing user accounts before creating new ones. If no existing account is found for the user, it only creates a new one (only when needed).
After going through the SCIM vs JIT provisioning differences, you may have gained a slight clarity regarding which one will be suitable for your setup. However, if you are still doubtful, take your time and evaluate a few factors to guide your decision. What are these factors? Let's quickly find out.
SCIM vs JIT Provisioning: Which Web Application Provisioning Methods Is Right For Your Organization?
While deciding between SCIM vs JIT provisioning, you can consider evaluating factors such as your organization size, your key requirements, your budget, or how frequently role change takes place within your organization. For example–
- If you’re running a large organization and frequently hire new employees, then SAML JIT provisioning can be a perfect solution. It will automatically create accounts for new users and give them access to the app the moment they log in to an app for the first time – without the need for IT admin involvement.
- Meanwhile, if users within your organization frequently undergo role changes (which means their account details need to be updated), then you should opt for the SCIM provisioning method. It will automatically update the user account whenever any changes are made to their details/attributes.
- Also, in case your organization is operating on a tight budget, then SAML JIT provisioning is a more suitable option. It delivers efficiency without the hefty price tag, unlike SCIM provisioning, which comes with high setup and maintenance costs (but note that the high expense is relevant because it does manage the entire user account lifecycle). Plus, why waste time on manual account creation when JIT provisioning can streamline the process effortlessly.
However, in the end, the decision lies in your hands—so take your time, weigh the options, and pick the one that truly meets your expectations.
Implement The User Account Management Method That Align With Your Unique Needs
After you've made your choice between SCIM vs JIT provisioning, take a moment and cross-check — whether the application you are using within your organization supports the web application provisioning method you've selected. If your application doesn't support the chosen web application provisioning method, you will have to — either switch to another method or find an alternative app that's compatible. Either way, you'll need to put in some extra effort.
However, in case you are short on time to do either of the things, you can consider opting for a hassle-free solution- Zluri (you don't even have to do the compatibility check because it seamlessly integrates with 350 off-the-shelf and 800+ apps). What is Zluri?
Zluri is an access management solution that directly integrates with your HRMS to create unique user IDs/accounts, update user account details, and delete user accounts when requested. Here's how it works: Zluri pulls the user's details from the HRMS (through integration) when a new user is onboarded and instantly assigns the user a unique ID/account. Later, Zluri evaluates and verifies the user's ID/account and seamlessly grants them access to relevant applications (suitable for their role).
Now, whenever user account details change, Zluri automatically fetches the updated information from your HRMS and uses it to update the user account. Likewise, when IT admins mark a user for offboarding, Zluri automatically deletes the user's accounts from all connected apps, revokes all app access, and removes them from groups, channels, and projects.
Basically, it's even more efficient and simpler to implement than web application provisioning ( SCIM vs JIT); all you need to do is implement Zluri's access management solution and integrate it with your HRMS, and Zluri will take care of the rest.
Frequently Asked Questions (FAQs)
1. Can SCIM And JIT Provisioning (SCIM vs JIT) Work Together?
Yes, in some cases, SCIM and JIT provisioning (SCIM vs JIT) can be used together. For instance, you can implement SCIM provisioning to handle ongoing user account updates, while to manage the initial account creation process when a user first logs into an application, you can implement JIT provisioning.
2. Is Just In Time Provisioning the Same As Just In Time Privilege?
No, they are not the same. Just-in-time privilege is an access control that solely focuses on granting authorized users access to apps for a limited duration. Meanwhile, just-in-time provisioning is a SAML protocol-based method that does a totally different thing: automating the user's account creation.








.svg)














