Unsure how to determine whether your implemented controls are functioning as intended or not? If so, conducting a user access review for SOC is your solution. How is a user access review supposed to help validate the effectiveness of internal controls? Most importantly, how to perform this review? In this article, we’ll discuss it in detail.
Let's have a quick Q&A round to help you clearly understand, 'How does user access review for SOC help validate the implemented internal control effectiveness?' (Don't worry; we've got the answers ready for you).
Therefore, to find out whether the implemented controls are performing as expected – you need to check if only authorized users are accessing the application or if unauthorized users or external attackers are holding access to the apps. How will you check that? This brings us to user access review, which is the only way to effectively track who is accessing what within your organization (which ultimately helps determine if controls are functioning properly or not).
Now, let’s proceed further and understand how to perform a user access review for SOC.
How To Perform User Access Review For SOC?
Before we discuss how to perform a user access review for SOC, you, as an organization, first need to select the type of SOC report you want to obtain (don’t just pick randomly; choose the one that is truly relevant for your organization). Note that — this isn’t a mere formality! This decision (the report type you will pick) will directly influence how your user access review for SOC will be carried out.
Now, you may question — ‘How will one figure out which report type is relevant for their organization?’ To clarify your confusion, below, we’ve created a table outlining the types of reports, their purpose, and who should obtain them.
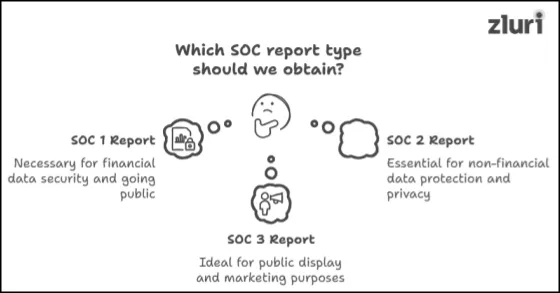
Once you’ve decided which report to obtain, you need to implement internal controls accordingly. For instance — if you choose SOC 1 report, you need to implement controls such as financial transaction processing controls, access controls, data reconciliation controls, and a few more to maintain the accuracy and security of financial reporting. Likewise, for SOC 2 and 3 reports, you need to implement controls such as security controls, data privacy and confidentiality controls, data retention controls, and a few others to align with trust services criteria (TSC).
Also Read: SOC 2 Trust Services Criteria: Implementing Effective Controls
Once all the necessary controls are implemented, the next step is to perform a user access review for SOC — putting your controls’ effectiveness to the test.
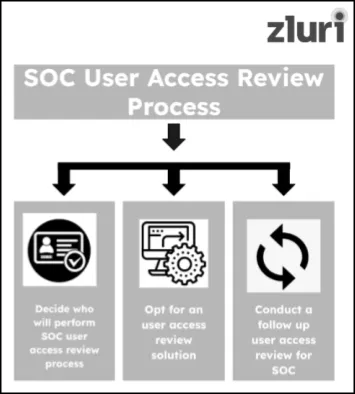
Step 1: Decide Who Will Perform Your User Access review For SOC — Either The Internal Team Or The External Auditor
Since this is the pre-assessment phase (which means you are preparing for the final SOC audit), you have the complete flexibility to decide – to whom you want to assign the task of performing user access review for SOC, either the internal team or external auditor. How do you determine which one is the right choice for this task?
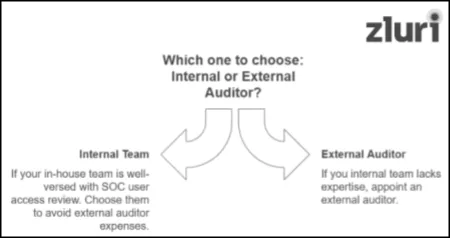
- It's quite straightforward. If you already have a team of experts who are well-versed in the auditing process and access review, you should choose your in-house team to carry out user access reviews for SOC. There is no need to bear the extra expenses of hiring an external auditor.
- If your team doesn't have the necessary knowledge and expertise, then it would be more appropriate to outsource an external auditor for this task. But, just don't randomly choose an auditor. Ensure the external auditor you select is a Certified Public Accountant (CPA certification is issued by the American Institute of Certified Public Accountants and is only given to auditors who qualify for the CPA exam and commit to delivering unbiased, accurate results).
What's the issue with non-certified auditors? If you pick a non-certified auditor, there is a high possibility that they may provide you with inaccurate findings (such as wrong information about your internal control effectiveness), which will further hinder your preparation for the final SOC audit.
Also Read: To gain more clarity, read this blog post — How to Choose an Auditor: 5 Factors To Consider
Step 2: Opt For An Access Review Solution To Perform User Access Review For SOC
Note: We've assumed that you have assigned the task of performing user access review for SOC to your internal IT/audit team. So, below, we've shared a perspective of what your team needs to do. We simply chose to focus on your in-house team because external auditors don't need any guidance, as they are already well aware of what needs to be done. However, you can track whether they perform user access reviews for SOC correctly by cross-checking the details in their reports below.
Ideally, there are two ways to perform user access review for SOC: manual and automated. Let's take an example to help you understand the difference between both approaches. (Since all three SOC report types primarily focus on data security, confidentiality, and privacy, we've framed an example specifying a control designed to help meet these core principles.)
Your organization has implemented least privilege access control (granting only authorized users with bare minimum access) across applications to maintain data security, confidentiality, and privacy.
Note: By limiting user's access to only what's necessary, you can significantly reduce the likelihood of accidental disclosure of confidential data. Along with that, you can prevent malicious actors from exploiting or tamper data (as with PoLP in place, even if hackers manage to get hold of user accounts, they won't be able to cause much damage due to limited access).
Also Read: 6 Ways To Implement Least Privilege
So, to check if the control is performing effectively, you need to conduct an assessment (user access review for SOC).
- Now, let's say you, as an IT team or audit team, opted for the manual approach (a method that most organizations still rely on) to check the effectiveness of PoLP access control.
So, the first thing you will do is compile the list of users, applications (that hold the client's sensitive data), and user access rights by going through multiple databases or directories and jotting the data down in a spreadsheet. After that, you will review each user one by one to find out whether they should hold access to those apps and, if they have app access, what permissions level they have been granted.
If any discrepancies or misalignments in access rights, such as users holding excessive or inappropriate access permissions, are detected (which indicates that the control you have implemented is not performing effectively and is not able to grant users limited access), you need to record them again.
That's not all; post review, you have to assemble another team to address/resolve the access misalignments and improve the effectiveness of PoLP (by reconfiguring it).
Now, by looking at the steps, you may have realized how much time and effort this manual approach demands. On top of that, even after investing so much time and effort, there is no surety that the control's effectiveness results will be accurate or reliable.
- However, this is not the case with an automated approach. You simply need to opt for an access review solution like Zluri, and all the tasks involved in reviewing the effectiveness of PoLP are automated. How?
Zluri offers an 'automated access review solution' that performs in-depth access reviews of applications that store client's data and different user types that hold access to these apps. During this user access review process, it first automatically integrates with the application and gathers all the user's information such as name, status (active or inactive), department, position, and a few more (note that – you have to specify which app and user type you want to review beforehand). After that, it uses the gathered user info to automatically evaluate whether each user is authorized (has the approval) to access the app or not and whether the level of access permission they hold is necessary or not.
If, in case, it detects misalignment in user access permissions, such as a user holding unauthorized access or excessive permissions (which highlights that the PoLP control failed to function as intended), it runs auto-remediation actions to safeguard financial data from being compromised or misused.
Finally, it logs all the misaligned user permissions or anomalies in its UAR report and mentions the actions taken to address the issues (these reports are free from inaccuracies because there is no manual involvement). You can evaluate these reports to understand where your PoLP falls short and fix it.
The best part is that, unlike the manual approach, you do not have to assemble a team to fix the misaligned access permissions; Zluri automatically fixes them (as discussed above), saving time and effort.
Take this interactive access review tour to understand how Zluri performs access reviews. Discover how seamless the process becomes with Zluri.
Step 3: Conduct A Follow-Up User Access Review For SOC To Validate The Implemented Changes (If Required)
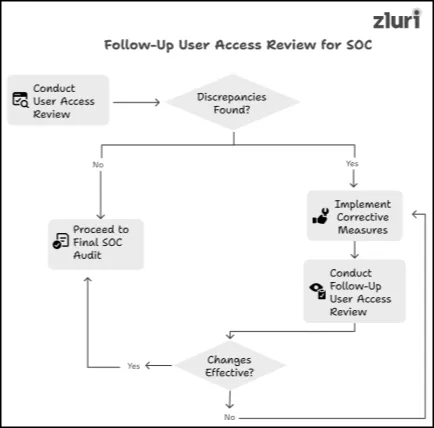
If, after conducting a user access review for SOC, you don’t find any discrepancies or anomalies (weaknesses in your implemented internal controls – they are performing as intended), then you can directly proceed toward the final SOC audit (which will be conducted by the external certified user and will grant you SOC certification).
However, if you uncover any inefficiencies in your controls while performing a user access review for SOC, then you have to implement necessary corrective measures to improve the effectiveness of your controls (like re-configuring them). Once you have made those changes, you need to conduct a follow-up user access review for SOC again. This practice will help ensure that the necessary changes that you have made to improve internal controls effectiveness are working properly, and then you can undergo the final SOC audit (with assurance).
Successfully Achieve SOC Certification By Conducting a User Access Review For SOC
Perhaps you might wonder, ‘Why bother going through the hassle of performing pre-assessment (user access review for SOC)?’ After all, during the final SOC audit, auditors will eventually evaluate the effectiveness of implemented controls. ‘Why prepare a report in advance?’
Well, here’s the thing — during the official SOC audit (last phase), external CPA certified auditors (who will issue the SOC certification) request organizations to present proof of evidence (reports) that demonstrates their implemented controls are effective and truly align with TSC. They also have to provide management assertion (which states the information they have provided is accurate). This isn’t just a procedural formality; it’s a mandatory requirement.
But what’s the point? Will they find the answer during the audit? Auditors generally ask for this evidence because they want to see how serious an organization genuinely is about data security (after all, the one that puts in more effort shows its true commitment). They also use this evidence for cross-checking purposes (so nothing is overlooked during the final SOC audit).
In short, don’t treat the user access review for SOC as just another task on your checklist. Rather, consider it a strategic move reflecting your commitment to security diligence, which will help you achieve SOC certification without any hassle.
Also Read: How to Get SOC2 Certified in 2024
Frequently Asked Questions (FAQs)
1. What Do External Auditors Specify In The Final SOC Audit Report?
In their report, auditors outline the methods and auditing standards they used to assess the controls, how long they took to evaluate each control, what types of issues were found, and recommendations to fix them. (Note – in case no issue is detected, SOC certification is issued directly).
2. What Is The Difference Between Type 1 and Type 2 SOC Audit?
The main difference between a type 1 and type 2 SOC audit is that type 1 focuses solely on evaluating the controls’ design at a specific point in time. Meanwhile, type 2 examines internal control's design and effectiveness over a specific duration (6-12 months). Basically, it not only checks if the controls are well-designed but also if they are consistently functioning as intended over time.
3. How Often Should You Perform User Access Reviews for SOC?
You can conduct a user access review for SOC quarterly, bi-annually, or annually. However, if issues are detected, the frequency of reviews will vary (as you need to re-conduct this review every time you detect an issue and perform a follow-up audit to validate the implemented changes).






.svg)














