The escalating occurrence of data breaches and unauthorized access incidents necessitates vigilant oversight from IT managers. Elevating the security of systems, applications, and sensitive information to paramount importance is non-negotiable.
To proficiently combat these challenges, user provisioning tools have emerged as indispensable resources. They provide a holistic and robust solution that enhances security protocols and optimizes the efficiency of user provisioning procedures.
User provisioning tools provide a comprehensive solution to automate and optimize user accounts' creation and management, ensuring access rights are granted and revoked promptly and accurately. However, their significance extends far beyond administrative convenience.
These tools are pivotal in strengthening an organization's security posture by establishing robust access controls, enforcing compliance measures, and mitigating the risks associated with unauthorized access or data breaches.
Let’s delve into the crucial role that user provisioning tools play in enhancing security within an organization's IT infrastructure. Let’s explore the various ways and illustrate how user provisioning tools serve as powerful mechanisms for safeguarding critical resources.
Essential Practices for Ensuring Security through User Provisioning Tools
Let’s explore the essential practices for ensuring security, protecting of critical resources and minimizing the potential for data breaches using user provisioning tools.
1. Implementing robust authentication: Strengthening authentication mechanisms
As businesses increasingly digitize their operations and store sensitive data electronically, the risk of security incidents rises. Weak passwords, outdated authentication protocols, and inadequate access controls can leave your organization vulnerable to unauthorized access and data breaches. Establishing strong authentication and authorization practices is imperative to mitigate these risks.
Multi-factor authentication (MFA) is one of the effective approaches to enhance authentication and authorization. MFA adds an extra layer of security beyond passwords by requiring users to provide multiple verification forms. This could involve using biometric factors such as fingerprint or facial recognition scans in addition to a password. Implementing MFA makes it significantly more difficult for unauthorized individuals to gain access.

Zluri's MFA acts as a formidable shield, fortifying your organization's most valuable assets. Gone are the days of relying solely on passwords, which can be easily compromised. With Zluri, additional credentials are demanded, establishing an impenetrable fortress against unauthorized access. Even in the event of a compromised password, only users armed with the power of MFA can traverse further and unlock the secrets within.
Further, it offers a diverse range of authentication methods, including email, one-time passwords (OTPs), facial recognition, and fingerprint recognition. Choose the path of least resistance without compromising security, providing a seamless and impressive user experience.
During onboarding, new users must prove their authenticity through the MFA process, effectively separating genuine employees from potential impostors.
Zluri’s main interface stands as the central command center for managing your organization's SaaS information. Only users or employees with proper MFA authentication can access this dashboard and view sensitive data. This helps protect critical information and restricts access to authorized personnel, enhancing overall security.
2. Reinforcing role-based access control (RBAC): Limiting access and privileges
Among the myriad benefits of user provisioning tools, one stands out as a beacon of efficiency and control: enforcing role-based access control (RBAC).
RBAC offers a dynamic approach to access control, granting users access based on their roles and responsibilities within your organization. Zluri's RBAC solution simplifies access control and brings order to authorization processes, replacing chaos with controlled authorization. KuppingerCole's research and analysis suggest that zluri’s direct API integrations enable IT to enforce fine-grained access control and avoid SCIM/SSO overhead. By assigning specific access levels to different job roles, departments, or projects, you ensure that users can access only what they need, preventing any unauthorized breaches into sensitive areas.But Zluri doesn’t stop at the basics. RBAC feature empowers you with granular control over access and privileges, allowing you to customize user roles and permissions effortlessly. Assigning multiple roles to a user becomes a breeze, with each role equipped with its own set of meticulously tailored permissions.

This granular level of customization guarantees that users have precisely the access they require to fulfill their responsibilities, reducing the risk of inadvertent exposure or misuse of critical resources.
Picture this: You’re responsible for a financial institution's network security. By utilizing Zluri's RBAC feature, you effortlessly assign roles like \"network administrator\" and \"help desk support\" to employees, granting precise access levels. Unauthorized breaches are minimized, ensuring data protection. Real-time monitoring allows you to track user activity, swiftly detecting and addressing potential security threats.
This feature streamlines access management strengthens security, and equips you with comprehensive monitoring capabilities, allowing you to track user activity and keep a vigilant eye on access to your IT systems and applications. With this real-time visibility, you can swiftly detect any suspicious or unauthorized behavior, fortifying your organization's security posture and putting potential threats on notice.
3. Automating user provisioning: Streamlining access management process
Automating user provisioning has become a critical aspect of modern IT management, and with good reason. Traditional manual processes for granting access to essential tools and applications can be time-consuming, error-prone, and detrimental to overall productivity. As an IT manager, you understand the importance of streamlining access management processes to ensure your employees can hit the ground running from day one.
Zluri's intelligent user provisioning solution revolutionizes user provisioning by automating and streamlining access management processes. By leveraging customizable workflows, reusable playbooks, and task scheduling capabilities, Zluri empowers your IT admin and team to provide seamless access to essential tools and applications, enhancing productivity and enabling your employees to make an immediate impact.
To streamline the onboarding process using Zluri, follow these straightforward steps:
- Access Zluri's workflow module and select \"Onboarding\" from the dropdown. Click on \"New Workflow\" to start creating your onboarding workflow.
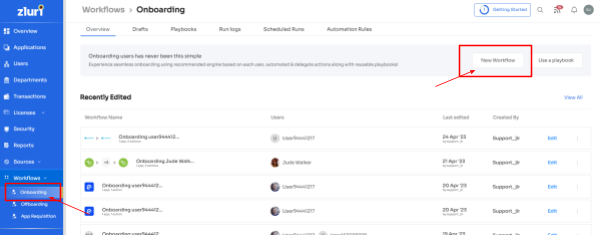
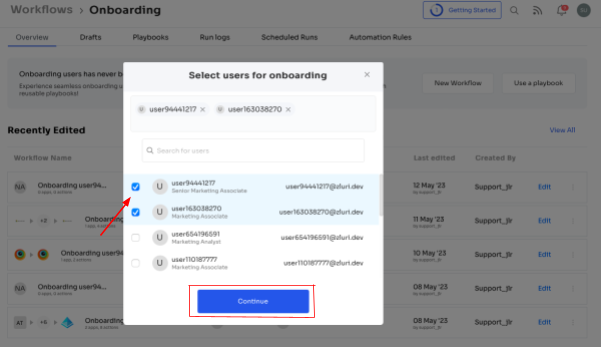
1. In the \"Select user for onboarding\" box, choose the user(s) you want to onboard. You can select them or use the search bar to find specific employees and click \"Continue.\"
2. From the left side, select the required apps from under the 'Recommended apps' for the user and define the desired actions for each application.
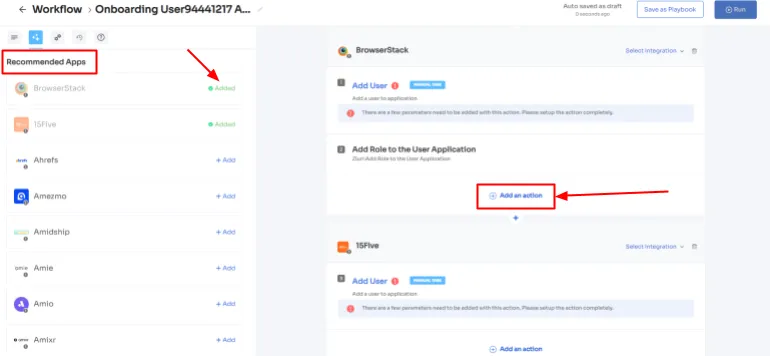
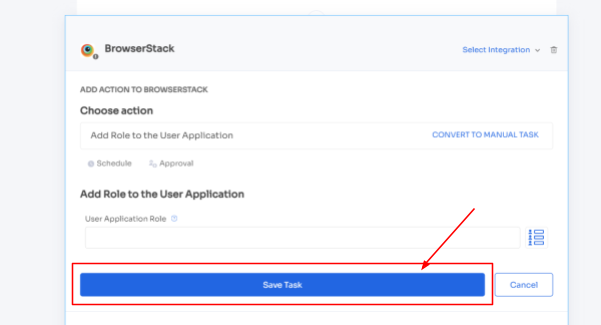
3. Customize the actions by clicking on \"Edit Action\" and entering the required details. You can also schedule these actions to be executed on the day of onboarding. Once you're done, click on \"Save Task\" to save the actions.
4. To save the workflow for future use, click on \"Save as Playbook.\" A dialogue box will prompt you to name the playbook. Simply provide a name, click on \"Save Playbook,\" and your onboarding workflow is ready to go.
5. The best part? These playbooks are reusable and can be easily updated as needed, ensuring ongoing efficiency in your onboarding process.Following these simple steps, you can automate and simplify the user provisioning process with Zluri's intuitive workflow module. It eliminates the risk of cyber threats and data breaches, safeguarding the company from potential financial losses.Say goodbye to manual onboarding tasks and hello to streamlined efficiency and productivity for your organization.
4. Continuous monitoring & auditing: Proactively ensuring security
With a multitude of vulnerabilities to address, effective reporting and auditing practices are crucial to maintaining a secure and compliant IT environment.
Consider the scenario where your organization deals with sensitive financial information. In such a context, ensuring a secure IT environment becomes imperative for uninterrupted business operations. As an IT manager, the responsibility falls on your shoulders to guarantee the security and compliance of your systems and applications. This is precisely where Zluri comes into play.
Zluri offers a comprehensive suite of reporting and auditing capabilities designed to empower your IT teams in fortifying their systems and applications. Through an intuitive interface, your IT admins can effortlessly generate reports that shed light on user access, activity, and real-time events, enabling the swift detection and prevention of potential security threats.
The reporting features enable your IT teams to acquire crucial insights into user behavior, access privileges, and application usage. Armed with this information, you can make informed decisions and enforce policies more effectively.
Additionally, Zluri allows the creation and maintenance of meticulous audit trails, ensuring a record of user actions and system activities that can be scrutinized for compliance and security purposes.
By harnessing Zluri's robust reporting and auditing capabilities, your IT teams gain the proactive monitoring abilities necessary to swiftly identify and address potential threats or policy violations. This heightened visibility and control facilitate the enforcement of access policies, safeguarding sensitive data, and meeting stringent compliance requirements.
So, let Zluri be your trusty companion in the ever-evolving quest for cybersecurity, for it holds the key to a secure and fortified future for your organization. Book a demo now!









.svg)



.svg)
.svg)
.svg)
.svg)

.svg)

.svg)

.svg)
















.webp)







.webp)
.webp)





.webp)