What looks like a simple way to manage access today can turn into tomorrow’s audit nightmare.
If you’re using group-based access control to manage permissions across your apps, you’re not alone. It’s fast to set up, easy to replicate, and works well–at first. However, as your environment expands, group-based models can become a security risk.
Over time, what starts as a well-structured set of AD or Entra ID groups turns into a tangled web of nested roles, stale memberships, and overprovisioned users. A single group tied to critical apps may have dozens of members who no longer need access, but no one has noticed. And during an audit, that becomes your problem.
You’ve likely seen this before:
- Groups granting excessive or unnecessary access.
- There is no clear ownership or documentation on who manages which groups.
- Inherited permissions from nested groups nobody remembers creating.
- Difficulty enforcing least privilege without disrupting teams.
The issue isn’t that groups are flawed; it’s that they’re too static for today’s dynamic cloud-first environments. And when access stays open longer than it should, you increase the attack surface, introduce compliance risk, and lose control over who can do what across your systems.
This article isn’t about discarding groups; it’s about managing the risks associated with them. Below, we’ll walk through 4 actions you can take to reduce group-based access risks, regain visibility, and enforce governance without slowing teams down.
.png)
4 Ways, 1 Goal: Better Group Governance
Group-based access issues don’t fix themselves. To reduce risk, regain visibility, and tighten controls, you will need to take certain measures. Below, we have mentioned 4 ways that can make an immediate difference.
1. Audit Group Memberships & Nested Hierarchies
One of the most common blind spots in group-based access control is indirect access through nested groups. A user might not be directly in a high-privilege group. However, if that group includes another group, and that one includes another, the user can still inherit access several layers deep.
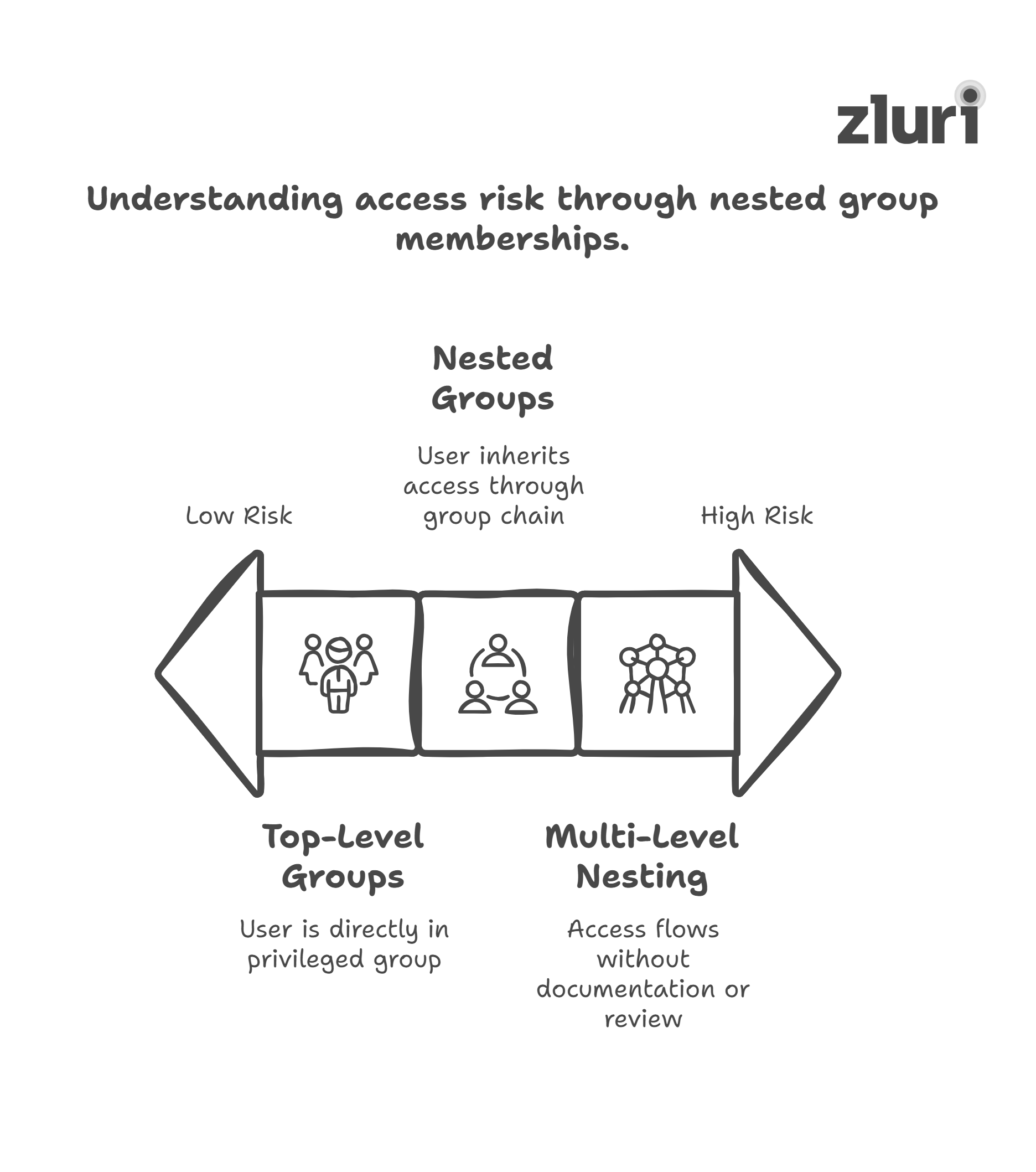
This is especially risky when:
- Access to sensitive apps is granted through multi-level nested group structures.
- Teams rely on legacy AD/Entra ID group designs without proper documentation.
- No one owns or reviews how access is flowing through the group chain.
What you should do:
- Map all access paths to critical systems: Start with your most sensitive applications. Identify every group (direct or nested) that grants access, and generate a user-level view of who ultimately receives permissions through those groups.
- Trace inherited permissions: Use IGA tools to detect users who are gaining entitlements through group relationships, not just those in top-level groups.
- Flag redundant or conflicting memberships: Identify users who are members of multiple groups that, when combined, create toxic access combinations or exceed their role requirements.
- Prioritize review based on sensitivity: Not all nesting is risky, but focus first on access tied to sensitive areas such as finance, HR, infrastructure, or customer data.
Note: If you’re using tools like Entra ID or Okta, it won’t always show complete nested group access by default. Utilize custom scripts or an identity platform to identify all indirect group relationships and gain a comprehensive view of who has access to what.
2. Identity & Remediate Orphaned Accounts
As teams evolve, projects wind down, and users transition into new roles, access groups often get left behind. What once made sense–a project-specific group or a cross-functional team role–quickly becomes stale. But the access? It stays open.
Worse, some groups have no clear owner or active members. No one’s using them. No one’s managing them. Yet they continue to grant permissions to sensitive apps.
These stale or orphaned groups are low-maintenance for IT teams, but high-risk for security.
What you should do:
- Find inactive groups: Identity groups that haven’t been updated or used in the last 90 days. Flag them for review.
- Check for orphaned groups: Look for groups with no active members, no group owner, or unclear purpose. These are often legacy artifacts.
- Assign ownership: Every active group should have a designated owner, ideally someone from the team that uses it. This builds accountability into your access model.
- Create a review cadence: Set time-bound rules to review or automatically expire temporary groups, especially those created for projects, contractors, or testing.
Note: Don’t wait for quarterly reviews. Automate detection of stale groups and alert group owners (or IT teams) monthly to revoke them before they become a liability.
3. Replace Static Group Access with Dynamic, Attribute-Based Rules
Groups were never designed to reflect the rapid changes in roles, teams, and contexts that occur in modern environments. Someone joins a project, moves departments, or takes on a temporary role — but what about the group memberships? They often stay the same long after the need has passed.
This is the problem with static access: it remains fixed in place, not moving with the user. And when access isn’t tied to real-time context, it either gets overprovisioned or forgotten altogether.
That’s why progressive teams are shifting from static group-based access to attribute-based access control (ABAC), where access is granted based on real-time user attributes such as department, role, location, or employment type.
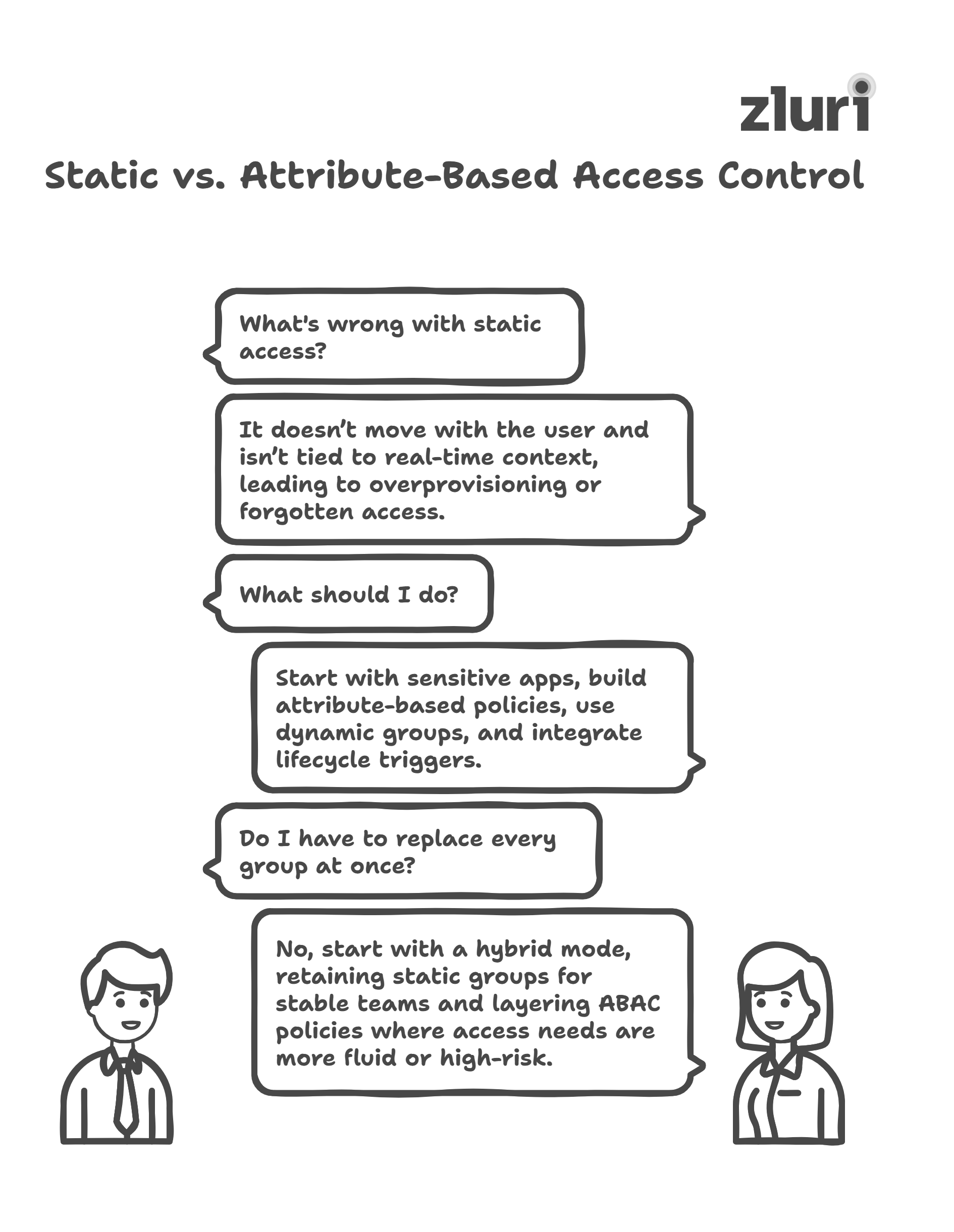
What you should do:
- Start with sensitive apps: Identify high-risk systems where static access poses a clear risk (e.g., finance, customer data, infrastructure tools).
- Build attribute-based policies: Utilize identity data, such as team, job title, or employment status, from your HRMS or directory to inform access decisions.
- Use dynamic groups where possible: In Entra ID or Okta, dynamic groups can assign access based on rules rather than manual membership.
- Integrate lifecycle triggers: Ensure access updates automatically when someone joins, exits, or changes roles — without waiting for manual intervention.
Note: You don’t have to replace every group at once. Start with a hybrid mode–retain static groups for stable teams, but layer ABAC policies where access needs are more fluid or high-risk.
4. Automate Group Access Reviews with Risk Context
Most teams conduct access reviews because they have to, not because they trust the outcome. And when group memberships are reviewed manually, without context, the result is usually surface-level approvals and missed risk.
The problem? A group might grant access to a critical finance app, but the reviewer has no idea what it is. Or the group has 200 users, and no one checks whether half of them still need access.
To make reviews effective, and not just compliant, you need to automate them and layer in risk signals.

What you should do:
- Automate group access certification: Set up recurring reviews for all high-risk groups to ensure ongoing compliance. Ensure reviewers understand who is in the group, what the group grants access to, and why the user is included.
- Include risk and context: Add details like app sensitivity, user activity, and group modification history. This helps reviewers make informed decisions rather than simply granting access.
- Route reviews to the right people: Group access shouldn’t only be certified by managers. Loop in group owners, app owners, or security leads–who actually understand the implications.
- Track remediation outcomes: Approving or revoking access is just the first step. Ensure your IAM/IGA system closes the loop by automatically removing users and updating entitlements.
Note: Don’t treat all groups equally. Review high-risk groups monthly, medium-risk quarterly, and low-risk annually. Let risk drive frequency — not a fixed schedule.
How Zluri Helps You Take Control of Group-Based Access?
You have seen what it takes to reduce risk: audit nested access, revoke access to stale groups, shift to dynamic controls, and automate reviews with content. However, manually or using traditional IAM platforms can be slow, error-prone, and unsustainable at scale.
Zluri solves that.
Built for modern, SaaS-driven environments, Zluri gives you complete visibility and control over group-based access. Whether you’re managing Entra ID groups, Okta assignments, or internal access roles across hundreds of SaaS apps, Zluri helps you govern them all– intelligently and automatically.
Here’s how:
- No more guessing who has access to what & through which group
Zluri maps out every access path (directed or inherited), so you can see exactly how users are gaining access to critical systems. You get a flattened, user-level view of group relationships, even across deeply nested structures.
- Reduce your attack surface by revoking orphaned & unused groups
Zluri lags groups with no active usage, no owner, and no unclear business purpose, so you can clean up access before it becomes a compliance risk. You can automate alerts, set expiry policies, and trigger reviews on idle groups.
- Enable dynamic access through HR & ITSM integration
By integrating with your HRMS, ITSM, and directory, Zluri enables attribute-driven access controls. You can automate group assignments (or bypass them entirely) based on real-time attributes, such as department, employment status, or role.
- Automate context-rich group access reviews
Zluri makes certifications meaningful, not just a checkbox. Reviewers get visibility into:
- What the group grants access to
- Who’s in it and why
- The risk associated with each member
And once access is revoked, Zluri ensures removal is enforced automatically across all connected systems.
- Focus effort where risk is highest, not where it’s easiest
Instead of treating all groups equally, Zluri uses risk score, app sensitivity, and user behavior to help you prioritize which groups to review, which to restrict, and which to revoke.
Don’t Let Group Access Become a Governance Gap
Group-based access was built for efficiency and scale — but without the right checks, it quickly becomes a blind spot. Nested access, orphaned accounts, and static entitlements can quickly disrupt your least privilege model, introduce audit failures, and risk exposure.
The good part? You don’t need to overhaul your entire SaaS ecosystem to fix it. Start with small, high-impact actions:
- Audit how access is inherited & granted
- Revoke whichever access no longer serves the purpose
- Replace rigid groups with dynamic groups where it matters most
- Make access reviews efficient, not just more frequent
Every action you take toward visibility and control helps you reduce your attack surface and strengthen your governance foundation.
Because, in today’s environment, it’s not about who’s in the group–it’s about what that group unlocks.








.svg)














