In a world driven by SaaS and rapid change, access isn’t just a convenience–it’s the perimeter of your business. Yet most organizations are working blind, leaving critical identities unmanaged, and audits stressful.
If you’re here, chances are that your current IAM setup isn’t scaling to meet the needs of your business.
Maybe you’re still managing access through spreadsheets and ticket queues. Or you have got tools that technically “work” but leave you blind to what’s actually happening across your environment. Perhaps audits are more reactive than you would like, or access reviews feel like a mere formality.
Either way, something is off.
And you’re not alone.
Identity and access management (IAM) has quietly become one of the most critical pillars of modern cybersecurity. But traditional approaches built around on-prem directories, static roles, and periodic certifications no longer hold up in SaaS-heavy, fast-moving organizations.
This guide is here to help you reset.
Not with generic best practices or vendor hype, but with a practical framework you can apply to modernize your IAM stack. One that:
- Recognize the realities of shadow IT, non-human identities, and hybrid workforces
- Helps you reduce risk without drawing in complexity
- Aligns security, IT, and business teams around a shared approach to access governance
- Shows you how to evolve your program incrementally, without needing to rebuild everything from scratch
Whether you’re building your IAM program from scratch or evolving past a legacy system that’s no longer serving you, this guide will walk you through the why, what, and how of IAM modernization–with real-world clarity.
Because access is your new perimeter, and it’s time your governance strategy caught up.
What IAM Modernization Really Means & What It Doesn’t?
.png)
“IAM modernization” is heard by the teams several times, but rarely with any clarity. For some, it sounds like replacing old tools with new ones. For others, it’s just about automating a few workflows.
But here’s the thing: modernizing IAM isn’t just a tool upgrade. It’s a mindset shift.
It’s about rethinking how you govern access in an environment that’s no longer centralized, predictable, or even fully human.
Let’s break it down.
What Does IAM Modernization Mean?
.png)
- Lifecycle-first, not directory-first: You’re no longer just managing AD groups and LDAP entries. You’re governing identities across HR systems, cloud platforms, SaaS tools, and third-party vendors.
Modern IAM starts with lifecycle events–joiner, mover, leaver–and governs access in response to real-world changes.
- Governance that’s continuous, not point-in-time: Instead of quarterly access reviews and one-time provisioning, you move toward continuous visibility and automated corrections. Access is adjusted when roles change, apps go unused, or risks emerge — not six months later during an audit.
- Designed for SaaS, not just on-prem: Your teams are in Google Workspace, Notion, Slack, and hundreds of other SaaS tools, not just your corporate AD. Modern IAM platforms integrate deeply with those environments, not just the “big five.”
- Built for all identities, not just full-time employees: Today’s access landscape includes contractors, vendors, interns, bots, APIs, and more. Modern IAM enables you to govern every one of them without requiring one-off workflows or exceptions.
- Context-aware decisions over static roles: Access is no longer binary; it’s contextual. Someone might need permission right now, but not tomorrow. Modern IAM brings in usage data, risk levels, and time-bound access to make smarter decisions.
What IAM Modernization Doesn’t Mean?
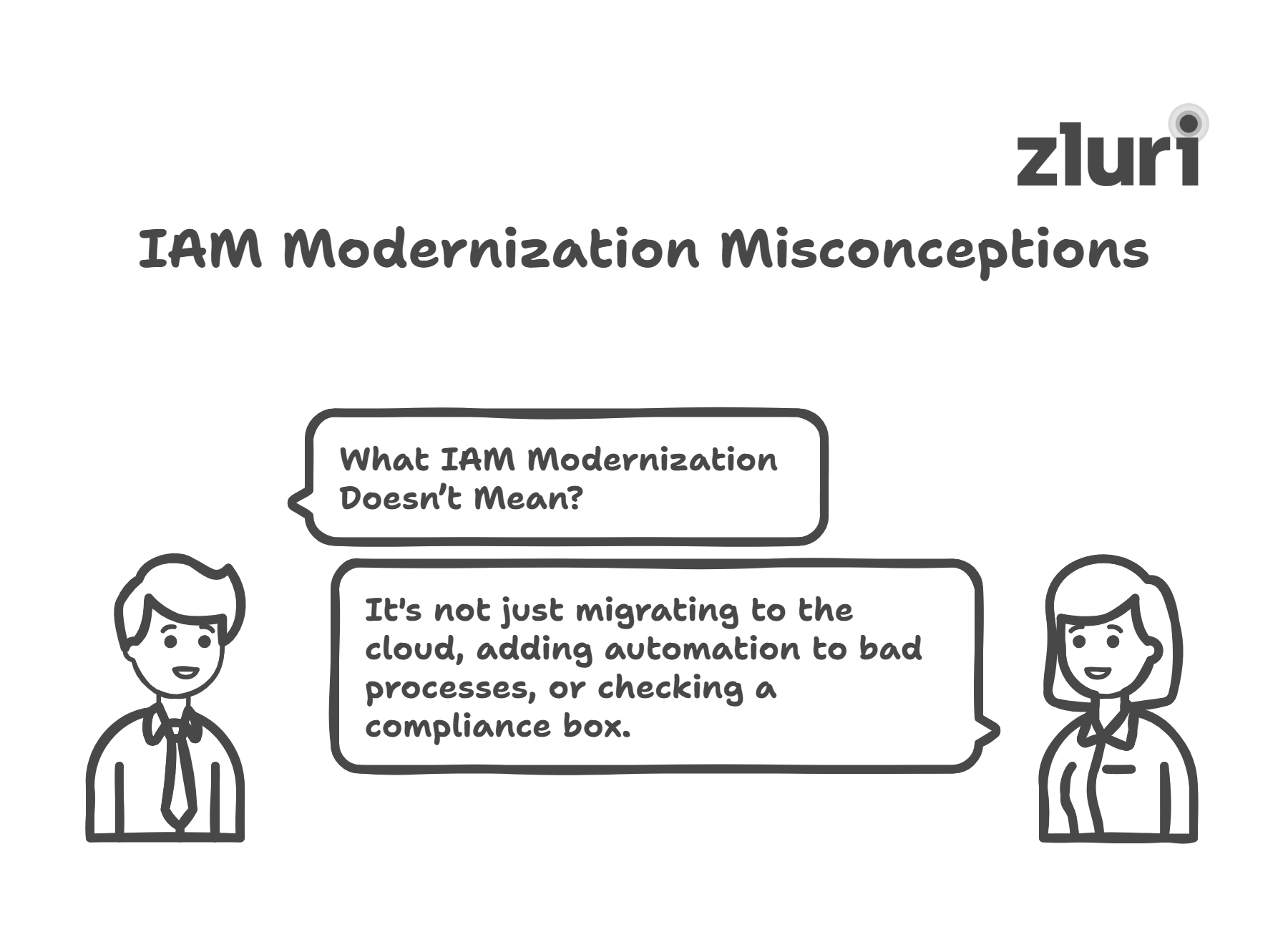
- Just migrating to the cloud: Lifting your existing IAM workflows into a cloud-based tool doesn’t modernize your governance; it just relocates your legacy problems.
- Adding automation to bad processes: If your access reviews are messy and manual, automating them without improving their quality won’t reduce risk. It will just help you rubber-stamp faster.
- Checking a compliance box: Yes, modernization improves your audit posture. However, if you treat it like a checkbox, you will miss the opportunity to address the actual access risks that may be hidden behind approved logs and clean reports.
Modern IAM means building an identity program that’s:
- Adaptive to business change
- Scalable across human and non-human identities
- Aligned with how work actually happens in a cloud-first world
And most importantly, it shifts you from constantly reacting to identity issues to proactively managing access before it becomes a problem.
Signs You Have Outgrown Legacy IAM

Sometimes the signs are obvious, like when an offboarded employee still has access to critical systems weeks after leaving. But more often, IAM gaps are subtle. They show up in the form of manual processes, blind spots, or stressful audits you have come to accept as “normal.”
If any of the following situations feel similar, it’s a clear signal that your IAM approach isn’t keeping up with your environment, and it may be time to rethink how you govern access.
If these signs sound familiar, you don’t need to fix everything overnight. But you do need to take a hard look at how access is managed today, and where you’re accepting risk just to keep things running.
Modern IAM helps you address these issues at their root by automating what’s repetitive, mitigating what’s risky, and providing visibility where you’ve had none.
IAM Modernization Goals: What You Should Be Aiming For?
Modernization isn’t about replacing old tools with newer ones. It’s about building an IAM foundation that supports how your organization works today and where it's headed tomorrow.
Here’s what it looks like when you modernize IAM the right way:
1. Automate identity lifecycle events across all user types
Provisioning and deprovisioning shouldn’t depend on IT tickets. Your IAM program should respond to real-life events, such as a new hire joining, a role change, or a contractor’s end date, automatically.
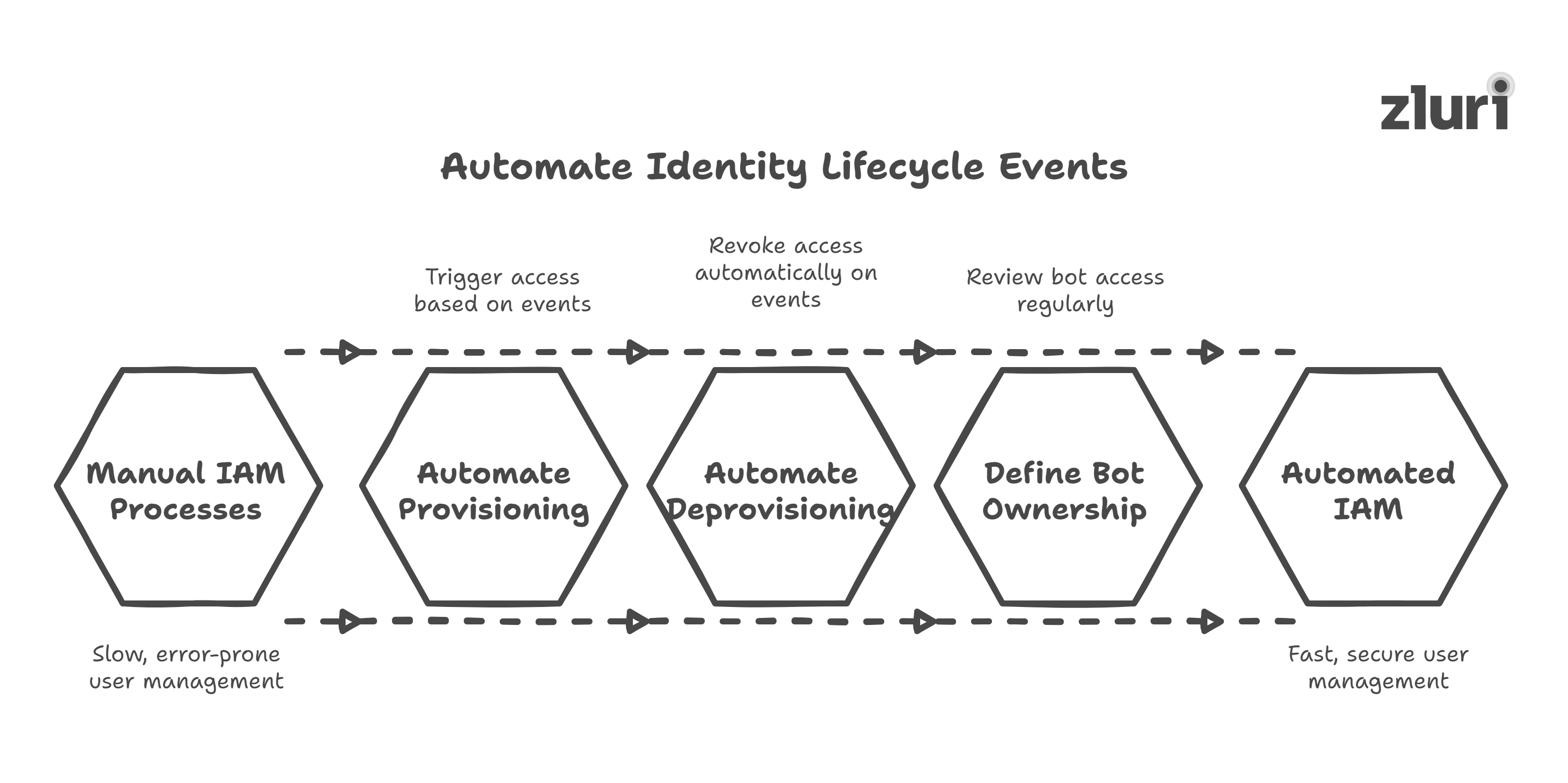
- For employees: Access is granted and revoked based on role, department, or location, with no manual intervention required.
- For contractors and interns: Access is time-bound and scoped from the start.
- For bots and service accounts, ownership is defined, and their access is reviewed just like that of any other user.
Outcome? Faster onboarding and offboarding, and fewer gaps for attackers to exploit.
2. Eliminate access creep with continuous visibility
Access shouldn’t accumulate over time just because no one notices. A modern IAM system gives you ongoing visibility into what users actually use and flags dormant or excessive access for cleanup.
.png)
- See when a user hasn’t accessed an app in 90+ days
- Detect over-privileged roles based on real behavior
- Spot unused licenses and revoke them with approval workflows
3. Make access reviews meaningful, not manual
Access certifications don’t have to be painful. Instead of long lists and rubber stamps, modern IAM lets you:
.png)
- Review only what’s relevant, like risky permissions or dormant access
- Involve business owners who understand the context
- Automate revocations for unused or unjustified access
Outcome? Reduced review fatigue and stronger access governance that holds up under audit.
4. Extend governance to SaaS and shadow IT
Most legacy IAM platforms fall short when it comes to SaaS. Modern IAM provides visibility and control beyond your core stack, encompassing all the tools teams use to accomplish their work.
.png)
- Discover apps outside your SSO
- Map who has access, how it was granted, and whether it’s still needed
- Bring them into your JML and review workflows even without native APIs
Outcome? Full access visibility, fewer surprises, and a real SaaS governance model.
5. Prepare for audits without the last-minute chaos
When access is continuously governed, audits become a report export, not a week-long activity. You should be able to:
.png)
- Show who has access, why, and when it was approved or removed
- Prove the enforcement of SoD, least privilege, and time-bound access
- Track identity ownership and activity across all user types
Outcome? Stronger compliance posture with less manual effort from IT teams.
6. Shift IT teams from reactive to strategic
.png)
When access is automated and governance is continuous, your IT teams can stop chasing tickets and start moving towards strategy.
- Design better role structures
- Support secure scaling during M&A or rapid hiring
- Focus on improving controls, not just enforcing them
Outcome? IT becomes an enabler, not a bottleneck.
A Modern IAM Framework: 6 Steps to Get There
You don’t modernize IAM overnight, and you don’t need to. What matters is that you take the right first step, based on your current state, and build from there with a clear direction.
Here’s a practical 6-step framework you can follow, whether you’re starting from scratch or evolving a legacy setup.
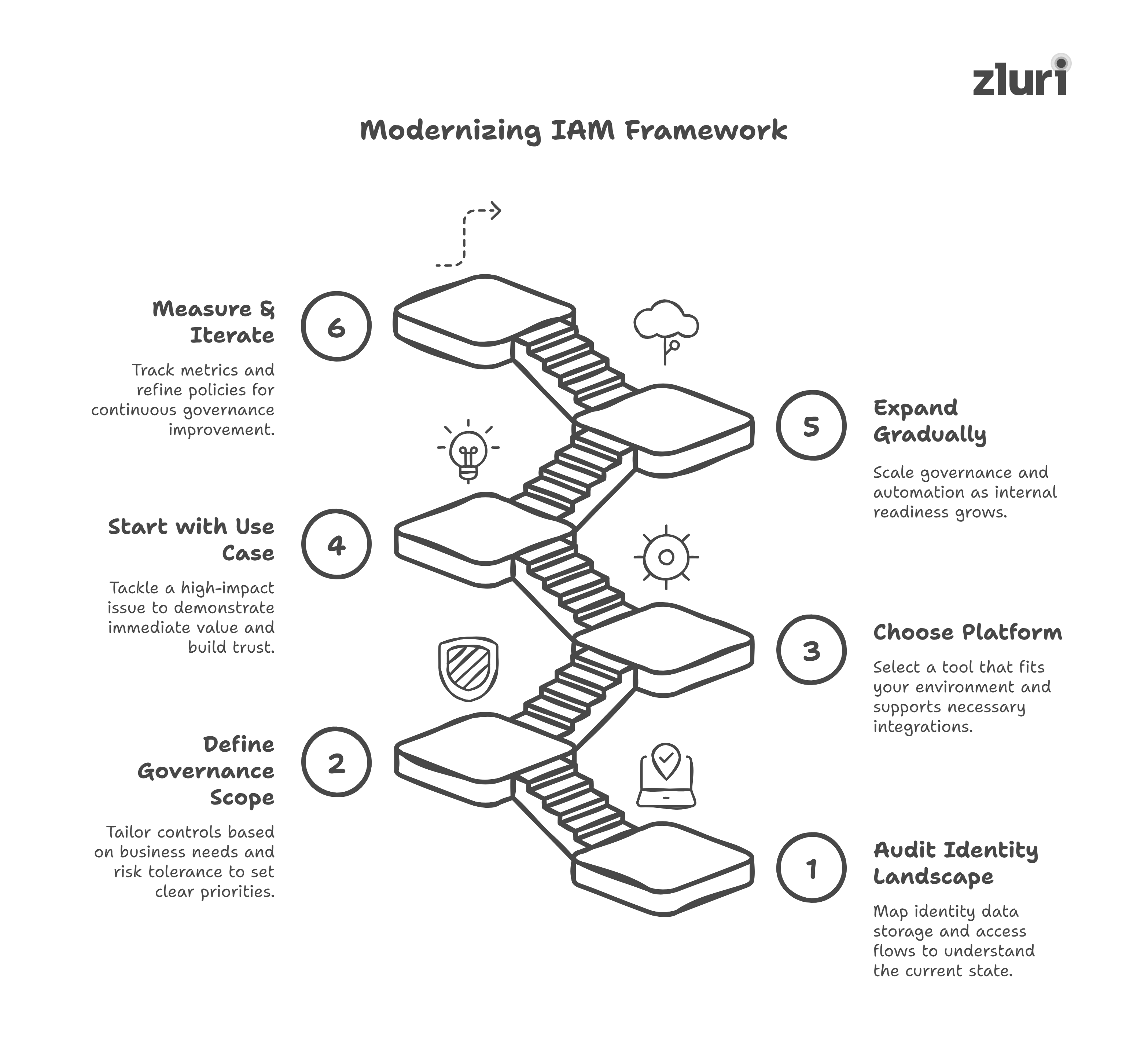
Step 1: Audit your identity landscape & access flows
Start by mapping where identity data is stored and how access is currently granted.
Ask yourself:
- What are your sources of truth? (HRMS, IdP, AD, contractor databases?)
- Which systems grant access? (SSO, SaaS apps, internal tools?)
- What are the manual steps, exceptions, or inconsistencies?
- Are all identities, employees, vendors, and bots accounted for?
Then, assess what access visibility you have:
- Can you see which users have access to which apps?
- Do you know how that access was granted, and when it was last used?
Goal? Establish a clear picture of your current state. You can’t fix what you can’t see.
Step 2: Define your governance scope & risk priorities
IAM modernization isn’t one-size-fits-all. You’ll need to tailor your controls based on business needs and risk tolerance.
Define:
- Which identities need to be governed: Full-time, contractor, vendor, API/service accounts
- Which apps are most critical to secure (think: finance, customer data, core infrastructure)
- What policies matter to your organization? Examples include SoD enforcement, least privilege, and time-bound access.
This helps you avoid overcomplicating governance where it’s not needed and strengthens it where it matters most.
Goal? Set a clear, risk-aligned scope that informs everything from automation to reviews.
Step 3: Choose a platform that matches your environment
Your tool should help you govern access across the actual apps and users in your environment, not just the ones a legacy IAM tool happens to support.
Look for:
- Deep SaaS integrations (not just SSO-level)
- Native support for JML workflows
- Visibility into usage, not just entitlement
- Non-human identity support
- Fast, API-friendly deployment
- Review workflows that business users can actually manage
Goal? Choose a platform that fits in your environment, not one that forces you to adapt to it.
Step 4: Start with one high-impact use case
Don’t try to fix everything at once. Instead, tackle one issue with real impact, something that reduces risk or effort immediately.
Some strong starting points:
- Automate offboarding to prevent excessive or unwanted access
- Reduce unused licenses and access creep
- Run a usage-based access review for a critical system
- Clean up orphaned or ungoverned service accounts
Choose a use case that’s high-risk or high-visibility, so you can show quick value.
Goal? Deliver a visible win that earns trust and demonstrates the model's effectiveness.
Step 5: Expand gradually–roles, apps, & identity types
Once you build trust and prove impact, you can scale:
- Introduce automated provisioning for common roles
- Add more apps to the JML and review flow
- Extend governance to contractors, interns, and vendors
- Bring long-tail SaaS & shadow IT into your access controls
- Add business ownership to access reviews
The key is to expand gradually, layering governance and automation as your internal readiness grows.
Goal? Make IAM governance scalable without overwhelming your teams.
Step 6: Measure, monitor & iterate
Modern IAM isn’t static. You need a feedback loop to keep improving. Track key metrics:
- & of users provisioned automatically
- Time to revoke access after offboarding
- % of unused access revoked
- Time to complete an access review cycle
- & of unmanaged SaaS apps brought under governance
Use those insights to
- Refine access roles and policies
- Strengthen review cycles or make them risk-triggered
- Show ROI to finance teams and auditors
Goal? Evolve your IAM program from one-off improvements to continuous governance and management.
With this framework, you’re no longer reacting to identity chaos; you’re building a foundation that gets smarter over time.
Pitfalls to Avoid When Modernizing IAM
Modernizing IAM pays off, but only if you avoid the traps that can stall or even reverse your progress.
These pitfalls are common because they seem logical in the moment. However, if you want long-term success, it’s worth identifying them early and resolving them accordingly.
Here’s a quick table to help you check your direction:
Don’t just think about what IAM modernization adds; think about what it helps you avoid: blind spots, burnout, and broken processes carried into a new system.
What Modern IAM Looks Like in Practice: A Hypothetical Scenario
.png)
Picture this: You’re leading IT at a mid-sized, fast-growing tech company.
You have approximately 700 users, including employees and contractors. The SaaS stack is sprawling, comprising Google Workspace, Jira, GitHub, Notion, Slack, AWS, and more, with new additions made every quarter. You have implemented an SSO and have some provisioning workflows in place, but do you have governance in place to support them? It’s mostly held together with tickets, spreadsheets, and a lot of hope.
Before Modernization
Your day starts like this:
You log in and see 3 Slack messages from hiring managers:
“Hey, can you onboard Alice?”
“Is Bob offboarded yet?”
“FYI, we added a new intern yesterday. Needs access to Salesforce.”
You check your ticket queue. There’s a pile of provisioning requests. Some are marked urgent. A few are duplicated. One’s from last week.
Meanwhile, you can’t deny the feeling that several contractors still have access to AWS even though their projects ended. You would have to check, but that would mean hopping between admin consoles and manually pulling reports.
An auditor's email lands:
“We need a full list of active users with access to Notion, including contractors and service accounts. Please include last login dates and approval logs.”
You sign.
Later that day, your team begins the quarterly access review. You already know how it will go:
Managers will bulk-approve access they don’t understand, reviews will continue for weeks, and someone will miss the deadline. Again.
And still, no one knows how many apps are lying around outside SSO. Marketing? Finance? Who knows what they have signed up for?
After Modernization
Fast forward 90 days. You have restructured IAM to be automated, usage-aware, and governed continuously.
Now, your day starts like this:
New hires are automatically provisioned on day 1, based on their role in the HRMS. They get only what they need, no more, no less. Contractors receive scoped access, are time-bound, and are tied to a clear owner. No Slack chases. No tickets.
You check the identity dashboard and see:
- Dormant access has dropped by over 60%
- Non-human accounts are reviewed regularly
- Every user has an access trail and an owner
App usage is monitored in real time. If someone hasn’t used a tool in 6 months, it’s flagged. If a manager bulk-approves access, the system asks for justification.
Audit? It’s a button click now. Everything is logged, including every approval, revocation, and change.
You’re not dealing with a mess anymore. You’re governing with clarity.
What does this transition tell you? Modern IAM isn’t just about solving technical debt. It’s about designing identity governance that scales with your company, not against it.
Start with the messiest pain point: offboarding, contractors, shadow SaaS. Then build on what works.
You don’t need to fix everything at once.
But once you move from scattered to systemized, access becomes a strength, not a liability.
How to Build Internal Buy-In for IAM Modernization?
Even when you know your IAM platform needs to evolve, getting internal alignment can be the most challenging part. Security wants one thing, IT another. Leadership seeks risk but hesitates when it comes to the budget. Meanwhile, teams just want access to work fast.
So, how do you drive modernization without much hindrance?
Here’s how you can position the case clearly across stakeholders.
Instead of pitching “we need to modernize IAM,” start with a specific pain point:
- We still don’t have a consistent offboarding process across applications
- We can’t show auditors who have access to service accounts
- Managers bulk-approve access reviews without context
Then offer modernization as the solution to that problem, not just a major platform that requires buy-in.
Your Next Step Towards IAM Modernization
You have seen what modern IAM tools are like and why legacy approaches no longer work in a world of SaaS sprawl, hybrid workforces, and identity-driven risk.
But here’s the good news: modernization doesn’t mean starting from zero. It means shifting your IAM platform from manual and reactive to automated, with increased visibility and continuity.
You don’t need to solve everything overnight.
You just need to start with one workflow, one risk surface, or one identity type that has been overlooked for too long.
Because every small fix adds up, and every automated decision is one less access gap to chase later.
Ready to take the first step? Start by mapping your current identity flow, including joiners, movers, leavers, contractors, and bots.
It’s often the simplest exercise that surfaces the biggest risks.
If you’re looking for a platform that helps automate these flows, uncover blind spots across SaaS, and give you continuous visibility into access, Zluri is purpose-built to help.









.svg)














