Identity isn’t just an IT function anymore; it’s the new perimeter.
As users, apps, and automation expand across cloud and SaaS environments, identity has become the control point for both access and risk. According to Gartner, by 2026, 70% of cyberattacks against enterprises will target identities, whether through credential compromise, privilege escalation, or unmanaged access.
And yet, most identity strategies still operate on outdated assumptions:
- Manual provisioning and ticket-based approvals.
- Point-in-time access reviews are conducted only during audit season.
- Siloed identity sources between HR, AD, Cloud, and SaaS.
- Orphaned access can persist long after employees or contractors have exited.
These gaps are no longer minor process issues; they’re open doors.
A modern identity strategy requires more than just adding another IAM tool. It demands a shift in architecture and mindset: one that’s automated, lifecycle-aware, and policy-driven from day 1. It means governing access dynamically, not reactively, and covering all identities, including non-humans like bots and service accounts, which are often overlooked.
This isn’t theoretical. Leading enterprises are already moving towards this approach, blending identity governance with SaaS management, security posture, and continuous compliance.
In this article, we’ll show you what that strategy looks like in practice. Whether you’re trying to fill gaps in your current platform or planning a next-gen IGA rollout, this will help you define a secure, scalable identity strategy that works in today’s environment.
What a Modern Identity Strategy Actually Looks Like?
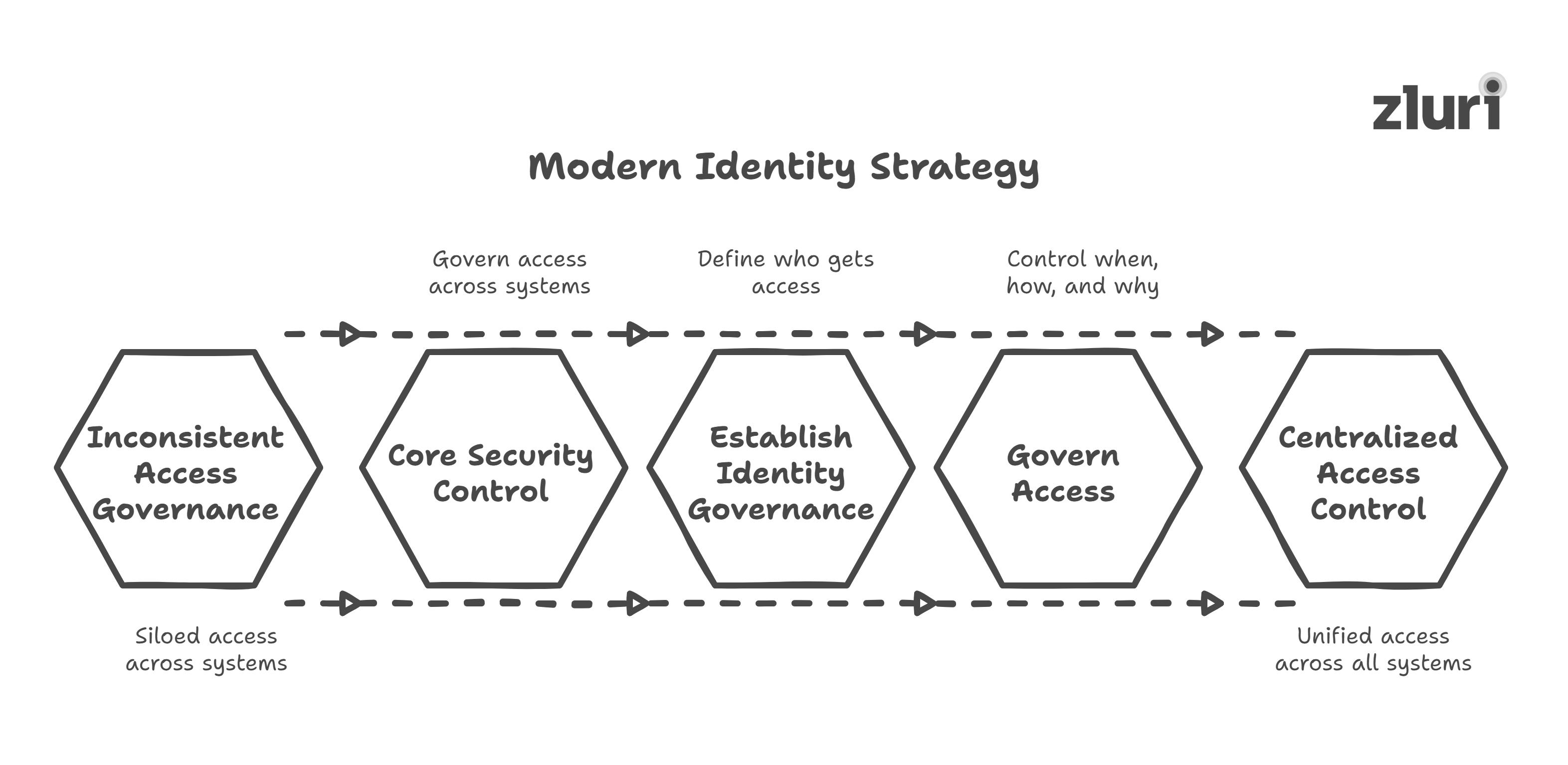
Let’s be clear: a modern identity strategy isn’t about implementing an IGA platform or checking boxes for compliance. It’s about establishing identity as the core security control, governing who gets access, when, how, and why, across every system in your stack.
Forrester reports that over 65% of enterprises still struggle to govern access across SaaS apps and non-human identities, even after years of IAM investment.
So, what does a modern, enterprise-ready identity strategy actually look like?
Below are the core characteristics that separate modern identity strategies from legacy IAM platforms that often fall short.
.png)
- Identity becomes the security control plane, not just a directory
Access decisions aren’t made in isolation. They are governed centrally, with identity as the anchor. Whether it’s a full-time employee, a contractor, or a bot account, every action is tied back to a governed identity with clearly defined ownership, access context, and audit trail.
Why it matters? This is what enables zero trust. Without a reliable, unified identity layer, policy enforcement breaks down.
- Governance is embedded into daily operations, not reserved for audits
Quarterly reviews and audit prep cycles are reactive and insufficient. A modern strategy treats governance as a built-in, real-time function:
- Event-triggered reviews (e.g., role changes, department transfers)
- Risk-based prioritization
- Auto-remediation of violations
- Real-time policy enforcement with complete audit trails
Why it matters? This reduces review fatigue, keeps access aligned with business changes, and ensures you’re always ready.
- Lifecycle management is fully automated & policy-driven
From onboarding to offboarding, access is provisioned and revoked based on predefined policies, not ticket queues or human memory. This includes:
- JML automation ties to HRMS or contractor databases
- Auto-expiry of temporary or elevated access
- Delegated workflows with business logic (e.g., different flows for interns vs external vendors)
Why it matters? Manual IAM processes are a top cause of access sprawl and audit findings. Policy-based automation fixes that at the root.
- All identity types are governed: humans, contractors, and bots
This includes:
- Employees
- Contractors & third-party vendors
- Non-human identities (bots, API keys, service accounts)
Why it matters? Non-human identities often outnumber humans in modern organizations, and they rarely get the same governance. That’s a huge blind spot.
- SaaS apps & shadow IT are fully discovered & governed
A modern identity strategy doesn’t treat SaaS apps as afterthoughts. It:
- Discovers shadow apps automatically
- Maps entitlements within those apps (not just SSO status)
- Governs app access with the same rigor as on-prem systems
- Audits usage to right-size or revoke stale entitlements
Why it matters? SaaS makes up the majority of your app footprint, but most IAM tools only govern a fraction of it.
Together, these traits define what a scalable and audit-ready identity strategy looks like in 2025.
Next, let’s look at where most enterprises go wrong and why legacy approaches fail to keep up.
The Hidden Gaps Putting Your Identity Strategy at Risk
Even with IGA platforms and IAM processes in place, chances are your identity governance still has gaps. Not because you’re doing it wrong, but because the old way of managing identity wasn’t designed for the complexity you’re dealing with today.

Here are some of the common pitfalls we see in modern enterprise environments:
- Ineffective access reviews create a false sense of security
You’re likely running quarterly certifications just to check the audit box. But behind the scenes, reviewers lack context, entitlements get rubber-stamped, and stale access slips through.
“I don’t even know what this app does, so I just approve it.” – Sound familiar?
When governance is driven by deadlines rather than risk, it doesn’t improve your security posture; it merely creates a false sense of confidence.
- Unmonitored SaaS & shadow apps leave you blind to real risk
Your SSO covers core apps, but what about the long tail? Tools your teams adopted without IT approval? Apps where users log in directly, bypassing central controls?
Without visibility into shadow IT and in-app entitlements, you’re governing a fraction of your real risk surface.
- Delayed offboarding leaves orphaned access wide open
If your deprovisioning process still relies on IT tickets and shared spreadsheets that wait for a manager to flag someone’s exit, you’re not alone. But it also means users often retain access long after they have left.
Every delay in offboarding is an open door for both internal threats and external risk.
- Untracked bots & service accounts accumulate excessive privileges
Bots, service accounts, and API tokens often get created without clear ownership or a plan to retire them.
And because they don’t show up in your joiner-mover-leaver workflows, they often accumulate excessive privileges over time with zero oversight.
- Disconnected identity systems lead to governance gaps & access drift
Your HRMS says one thing, your SSO another, and your SaaS apps something else entirely. Meanwhile, automation is limited to isolated workflows and is not scalable.
Without a centralized identity source or coordinated policies, access decisions get made in silos, and drift becomes inevitable.
These issues aren’t signs of failure; they’re signs that your environment has outgrown traditional IAM models.
In the next section, we will guide you through a practical, modern framework that aligns your identity strategy with today’s complexity, enabling you to transition from fragmented processes to secure, scalable governance.
A Framework to Build Your Modern Identity Strategy
Once you have identified the gaps, such as manual offboarding, shadow access, and blind reviews, the next step is to build a modern strategy that closes them for good.
But modern doesn’t mean complex. It means coordinated, automated, and risk-aware.
Here’s a practical, scalable framework to guide your transition from fragmented controls to a secure, always-on identity strategy.
- Create a unified identity foundation that powers governance & audit
You can’t govern what you can’t see, and fragmented identity data is one of the biggest roadblocks.
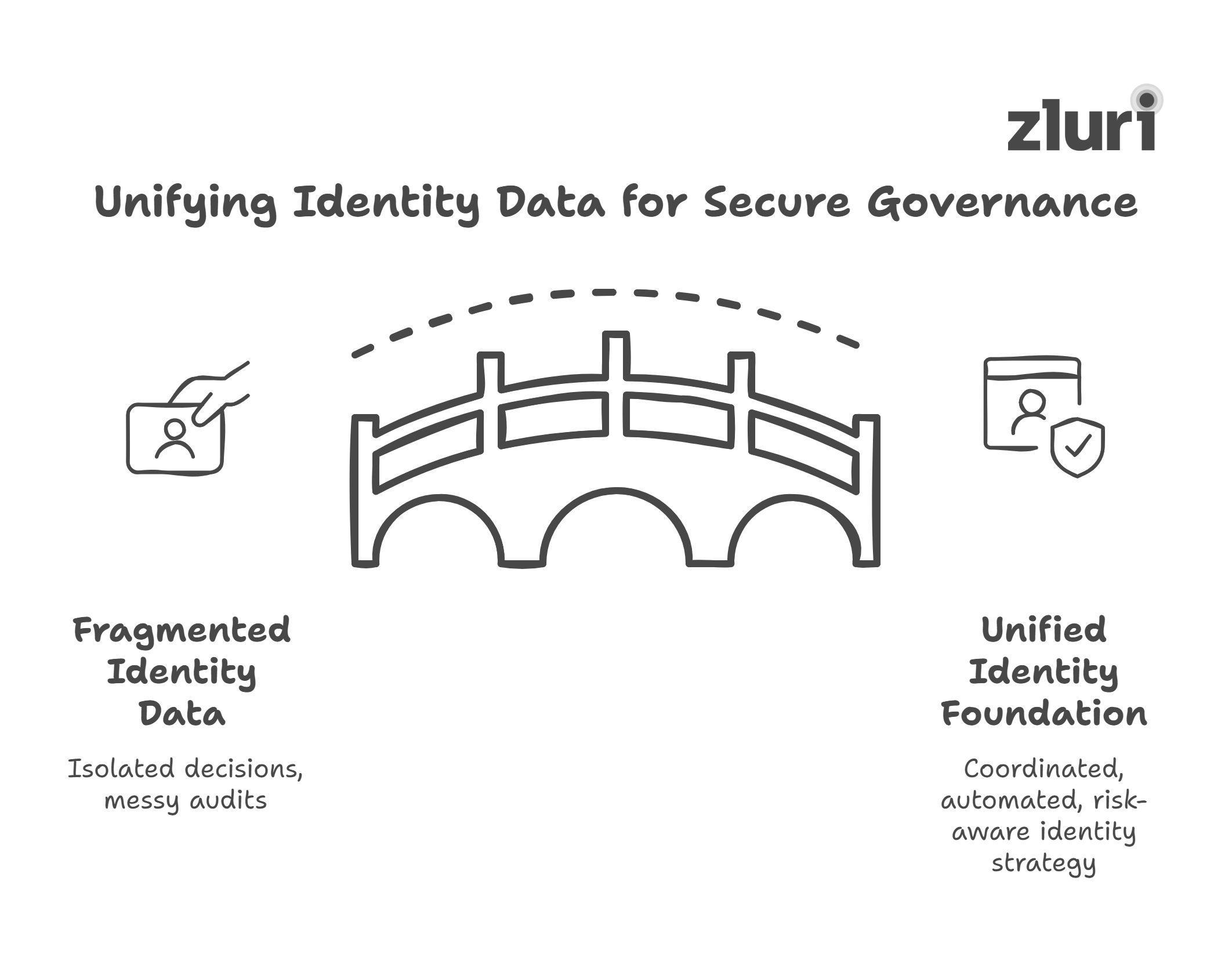
Start by consolidating identity data across:
- HRMS (for employees and role metadata)
- ITSM (for contractors, vendors, and interns)
- Active Directory, Azure AD, and IdPs (your authentication layer)
- SaaS apps and cloud platforms (where real access and entitlements live)
When this data is unified, it becomes your single source of truth, driving every provisioning rule, review process, and access decision. More importantly, it creates an audit-ready trail of who has access to what, when, why, and with whose approval.
Without this foundation, identity decisions happen in isolation, and audit prep becomes a mess instead of a byproduct.
- Automate identity lifecycle with policy-based JML workflows
Manual provisioning and offboarding are not just time-consuming; they’re risky.
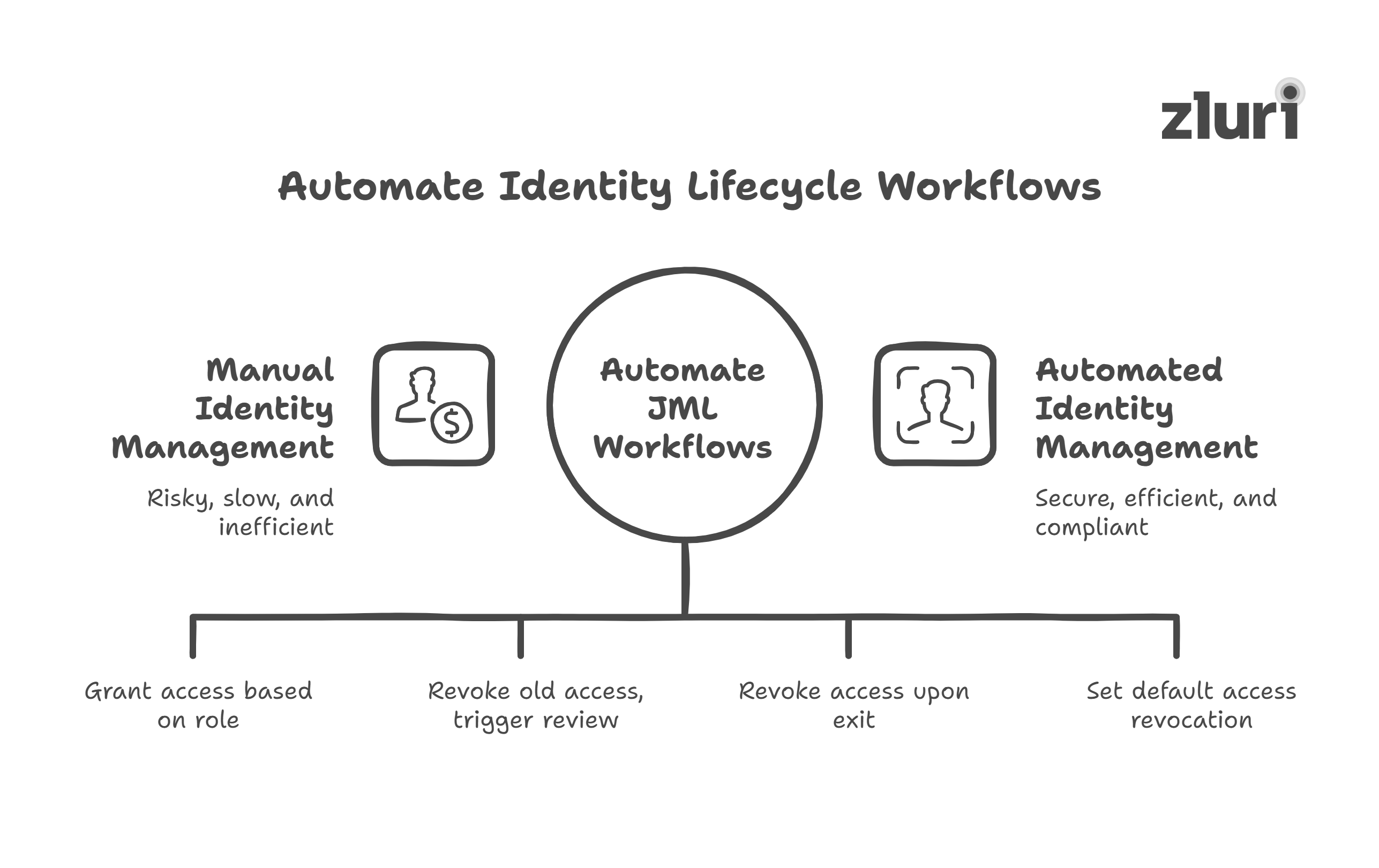
You need to enforce automated identity workflows that align with business context:
- Joiners: Grant access automatically based on role, location, team, or employment type
- Movers: Revoke old access and trigger a contextual review the moment someone changes roles
- Leavers: Revoke access across SSO and directly integrated apps the moment they exit, no ticketing delay
You should also account for edge cases, like interns, vendors, or short-term project teams, by setting default access revocation and auto-recertification triggers.
Automating JML isn’t just about efficiency; it’s the most effective way to prevent access creep and privilege accumulation.
- Extend governance beyond the obvious: SaaS, shadow IT, & non-human identities
Legacy IAM tools often stop at the surface, focusing on core apps, SSO, and user identities. But your biggest risks often live beyond those boundaries.

- Shadow SaaS: Apps adopted without IT approval, often accessed via direct login or personal email.
- In-app entitlements: Roles such as “workspace admin” and “project owner” are often buried deep within tools like Notion, Jira, or Salesforce.
- Non-human identities: Bots, service accounts, and API tokens that never expire and rarely get reviewed.
A modern strategy must continuously discover new apps, map entitlements within them, and enforce policies across all identity types, not just employees.
If you only govern what’s connected to SSO, you’re missing the riskiest 30-40% of your access landscape.
- Shift from periodic reviews to continuous, risk-based governance
Quarterly access reviews are too late and too broad.

Instead of rubber-stamping every user’s access in one spreadsheet, modern platforms:
- Trigger reviews based on events: Like role changes, inactivity, or flagged risk
- Prioritize by sensitivity: More frequent reviews for privileged roles or critical systems
- Empower business reviewers: By showing them what the access does, whether it’s used, and how it compares to peers
This reduces review fatigue, increases accuracy, and aligns governance with real-time risk, with no audit deadlines.
When reviews are contextual and risk-aware, governance shifts from a checkbox exercise to a true control mechanism.
Together, these 4 pillars give you the structure to govern identity at scale, without relying on spreadsheets or manual approvals.
However, strategy only works when backed by the right platform —one that’s purpose-built for today’s SaaS-first, fast-moving environments.
What to Expect From a Modern IGA Platform?

At this stage, you’re likely evaluating platforms side by side, looking beyond theoretical capabilities to actual outcomes.
Here’s what to benchmark when assessing whether a platform is built for your environment:
If your IGA platform can’t deliver on these outcomes, it’s not built for the complexity you’re trying to manage. These aren’t some aspirational features; they’re baseline requirements for enterprises navigating complex identity environments.
How Zluri Enables a Modern Identity Strategy Without Complexity?
Modern identity governance isn’t just about adopting more tools; it’s about making access decisions faster, smarter, and more consistent across an increasingly fragmented environment.
Most identity strategies fail not because of a lack of intent, but because execution is too manual or slow to keep up with today’s SaaS-first, hybrid environments. Zluri flips that dynamic.
By combining deep SaaS intelligence, real-time automation, and granular governance in one platform, Zluri enables you to implement a modern strategy that’s not only secure and scalable but also usable by IT teams.
- From siloed identities to a single source of truth
Zluri unifies all identity and access data across full-time employees, external users, service accounts, and hundreds of SaaS applications – into a single, unified system of record.
At the core of this is Zluri’s data discovery engine (built on its iPaaS layer), which connects to your stack and continuously pulls identity, access, and usage data from:
- Core IT-managed tools like Google Workspace, Workday, Okta, and Azure AD
- Collaboration and project tools like Slack, Notion, Jira, GitHub
- Shadow IT surfaced via browser agents and finance system integrations
You gain full visibility into who has access, what they have access to, and whether it remains valid, without needing to chase app owners or navigate multiple spreadsheets.
For harder-to-integrate tools, such as those without native APIs, Zluri supports webhook-based event ingestion. This allows you to continue tracking activity and enforcing governance workflows, even in edge cases.
For example, if a new user is added to a custom-built application, Zluri can trigger a webhook event to log that identity, validate ownership, and ensure access is governed properly.
This unified approach doesn’t just streamline provisioning; it also helps you maintain a clean audit trail for every identity, app, and entitlement. No more reconciling data across systems during audit season. It’s all there, always up to date.
- Lifecycle automation that works without tickets, scripts, or delays
Still relying on IT tickets for provisioning? Or hoping a manager flags a leaver before their access is revoked? That might’ve worked years ago—but today, it's too slow, too error-prone, and too risky.
Zluri automates every part of the identity lifecycle—from onboarding to offboarding—without scripts, manual intervention, or helpdesk delays. You set the rules. Zluri enforces them.
Here’s how it works across the full JML cycle:
- Governance that goes beyond SSO: SaaS, shadow IT, in-app roles, non-human identities
Most IGA platforms stop at what they can see through SSO. But in a modern SaaS environment, that’s not enough.
Your real risk lives outside the obvious:
- Apps your teams adopted without IT’s approval
- Admin roles are hidden deep inside collaboration tools
- Bots and service accounts running with excessive, unmonitored access
Zluri helps you govern all of it, so nothing slips through the cracks.
With Zluri, governance isn’t limited to what your SSO knows. It’s identity-first, SaaS-aware, and complete, covering every user, every tool, and every entitlement that could expose you to risk.
- Turn access reviews into a smart, always-on control layer
Access reviews aren’t just about passing audits; they’re your frontline defense against access sprawl, privilege creep, and policy violations. However, when reviews are conducted using spreadsheets without context or follow-up, they become ineffective.
Zluri transforms reviews from a compliance checkbox into a real-time, risk-aware governance layer – automated, contextual, and built to scale with an access review platform.
From rubber stamping to real governance, with Zluri, reviews become:
- Contextual: Reviewers don’t guess, they act based on usage and risk signals.
- Scalable: Multi-level workflows and bulk actions make it practical at enterprise scale.
- Automated: No follow-ups, no lag–playbooks handle remediation instantly.
You no longer depend on scattered approvals or informal decisions. With Zluri, access governance becomes a structured, enforceable process – always-on, audit-ready, and aligned with real-time risk.
Ready to move from periodic reviews to continuous governance? Zluri helps you close access gaps before they become audit findings or security incidents. If you’re looking to modernize your identity strategy, start with the platform built for it.
See Zluri in action | Talk to our experts
Your Identity Strategy Can’t Wait for Legacy to Catch Up
Most identity strategies don’t fail because teams lack awareness; they fail because the tools they rely on weren’t built for how modern enterprises actually operate.
You’re not managing static roles behind a firewall anymore. You’re governing access across SaaS apps, contractors, cloud platforms, APIs, bots, and business teams that move faster than your review cycles.
That’s why the real challenge isn’t knowing what to fix; it’s choosing a platform that helps you execute without any issue or delay.
The good news? You need to rebuild your entire stack or run a year-long project to get started. You just need a strategy and the platform to move ahead.


.png)






.svg)














