When access spans hundreds of SaaS apps, contractors, and bots, fragmented identity data isn’t just inconvenient; it’s dangerous. Next-gen IGA solves that by becoming your system of record for every identity, human or not.
Identity governance has traditionally played a passive role. It enforced policies handed down from your HRMS or AD, ran access reviews on a schedule, and may have triggered a few provisioning workflows along the way. But it rarely acted as the single, reliable source of truth for identity and access.
The problem? That model doesn’t scale anymore.
Your workforce is dynamic. Employees join, switch roles, and come back as contractors. You’re working across dozens (if not hundreds) of SaaS apps, cloud platforms, and distributed teams. And you’re dealing with more than human users. There are service accounts, bots, and APIs that make decisions and access sensitive systems in real-time.
In this scenario, you can’t afford to rely on fragmented identity data or delayed syncs. You need something authoritative. Always up to date. Built to make real-time access decisions based on accurate context.
That’s where next-gen IGA comes in–not just to enforce rules, but to become your system of record for identity. When IGA becomes your source of truth, it doesn’t wait for updates from other tools. It knows who someone is, what access they have, why they have it, and whether or not they should keep it.
This shift changes everything – from how you govern access to how quickly you respond to audits to how confidently you operate.
What Does the System of Record Mean in the Identity Context?
You have probably heard the term “system of record” (SoR)several times, usually in reference to your HRMS or AD. However, when it comes to identity governance, it’s essential to understand what it truly means and why it matters.
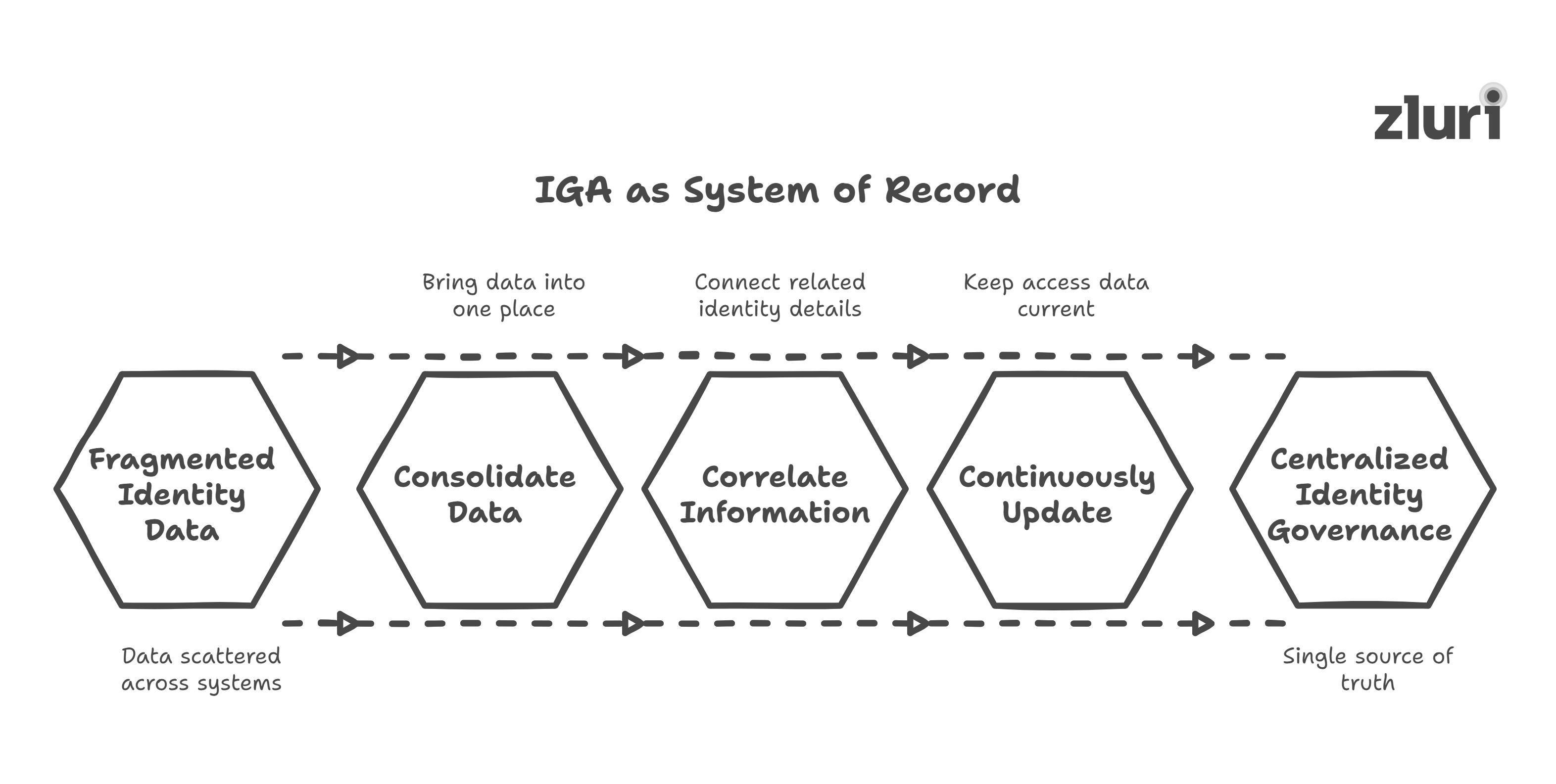
A system of record is the authoritative source of truth for a specific set of data. For example:
- Your HR system serves as the system of record (SoR) for employee details, including name, designation, department, and start date.
- Active Directory might be the system of record (SoR) for credentials and directory group memberships.
- An ITSM tool could act as the SoR for assets and services.
But here’s the catch: none of these systems were built to govern access. They hold fragments of identity information, but they can’t answer deeper questions like:
- Who has access to what?
- Is that access still justified?
- Is it based on usage, role, or just leftover entitlements?
That’s where things get risky.
If your IGA platform is depending on other tools to tell it what to do, you’re already operating with a lag. You’re basing access decisions on outdated, partial data. And when identities are scattered across SaaS apps, cloud platforms, and non-human users, this fragmentation multiplies.
Now, imagine flipping that model.
Instead of relying on other systems, what if your IGA became the system of record for all things identity and access? One place that consolidates, correlates, and continuously updates who has access, where, and why.
That’s the core idea behind next-gen IGA becoming your system of record. It’s not just about syncing identities anymore; it’s about owning the full picture.
Why Does Traditional IGA Fall Short?
If you’re using a traditional IGA tool, you’re probably familiar with how rigid and reactive it feels. It can pull in identities from your HRMS or Active Directory, trigger provisioning rules, and schedule periodic access reviews. But in today’s SaaS heavy, fast-moving environment, that’s just not enough.
.png)
Here’s a detailed look at where traditional IGA platforms fall short and why that gap puts your security and governance at risk.
1. They’re only as good as the data they’re fed
Most legacy IGA tools were never built to be the source of identity truth. Instead, they rely heavily on external systems, such as your HR platform or Active Directory (AD), to inform them of changes. If someone joins a new department or switches roles, your IGA has to wait for that update to sync from another tool.
.png)
That delay can lead to:
- Late provisioning: New hires don’t get access on day 1
- Stale access: Users retain old permissions long after switching roles
- Missed revocations: Access isn’t removed immediately when someone exits
When your IGA is constantly waiting for someone else to tell you what to do, you’re already one step behind.
2. They can’t see what’s really happening in SaaS
Legacy IGA tools were built in a world of on-premise systems and structured hierarchies. They were never designed to understand SaaS apps that live outside of your SSO, or track browser-based activity that doesn’t go through your directory.
.png)
Here’s what that means in practice:
- If a user logs into a third-party SaaS tool using a personal email or bypasses SSO, traditional IGA doesn’t catch it.
- If someone has access but hasn’t used an app in months, your IGA still sees them as “active.”
- If access is granted directly within an app (for example, a project manager adds someone to Asana), it won’t be reflected in your reviews.
So, while you’re busy certifying access in one system, real access might be drifting in another.
3. They fragment identity across systems
You might have a single person who appears in five different systems, once in your HR tool, twice in SaaS apps, and maybe as a service account in a cloud environment. Traditional IGA can’t always correlate and unify those fragments.
.png)
What you’re left with is:
- Duplicate identities you can’t confidently map
- Manual cleanup during reviews
- Gaps in ownership, especially when accounts are created outside of formal provisioning processes
This siloed view of identity breaks the chain of accountability and introduces a real security risk.
4. They operate on a delay
Traditional IGA syncs on a schedule, every few hours or once a day. That might have worked in the past, but today, access risks change in minutes.
.png)
Here’s where the lag hurts you:
- A terminated employee may still have access to sensitive data before their access is revoked.
- A high-risk permission granted in an app may go unnoticed until the next scheduled sync.
- Threat response is slowed because your IGA isn’t operating with the most current picture of access.
And in high-stakes environments like finance, healthcare, or critical infrastructure, that delay is more than inconvenient–it’s dangerous.
Traditional IGA isn’t inherently broken; it’s just built for a world that no longer exists.
It assumes identity is static, environments are predictable, and updates come from a single trusted system. However, your reality is far more complex: dozens of apps, multiple identity sources, dynamic workforce changes, and increasing volumes of non-human access.
To keep up, you need more than policy enforcement. You need a platform that sees everything, correlates in real-time, and makes informed decisions at the pace your business moves.
That’s what next-gen IGA delivers, and we’ll dig into that next.
The Rise of Next Gen IGA
You have seen where traditional IGA tools fall short. Now, let’s talk about how next-gen IGA changes the game and why it’s built to be your system of record from day 1.
Unlike legacy platforms that just react to changes from other systems, next-gen IGA is designed to observe, analyze, and act on identity and access data directly. It doesn’t wait for someone else to send it updates. It collects signals in real time, correlates them intelligently, and becomes your most reliable source of truth.

Here’s what makes it fundamentally different:
1. Built around a complete identity context
Unlike traditional tools that rely primarily on a single source of truth, next–gen IGA platforms are designed to capture identity signals across your entire ecosystem, typically in conjunction with your HRMS or AD.
They aggregate data not just from authoritative sources, but also from:
- SaaS applications
- Cloud platforms
- Endpoint activity
- Browser-level integrations
- Expense and usage data
This approach gives you:
- A unified identity graph that includes a 360-degree view of each identity (human or non-human)
- Live insight into access rights and usage, so you can see what each identity has access to and whether it’s still necessary.
- Governance decisions based on context, such as risk level, role changes, inactivity, or anomalous behavior
By eliminating blind spots, you gain a real-time view of every identity in your environment, enabling smarter, faster, and more secure access decisions.
2. Signal-driven, not schedule-driven
Traditional tools operate on fixed sync cycles, pulling data from HR or directories every few hours or once a day. In fast-moving environments, that delay can create a real risk: users retain access longer than they should, and violations go unnoticed until the next review cycle.
Next-gen IGA flips this model. It’s built to respond to real-time identity signals, not static schedules.
That means:
- When a user’s role changes, access can be adjusted immediately, without waiting for a batch job.
- If a contractor’s end date shifts, deprovisioning can happen the moment their access is no longer needed.
- When risky behavior is detected, workflows like access revocation, policy alerts, or escalated reviews can be triggered instantly.
By aligning governance with live system activity, next-gen IGA ensures your access decisions are always timely, precise, and responsive to risk.
3. Comprehensive SaaS & shadow IT visibility
Legacy IGA tools often lack the depth to effectively monitor SaaS environments. They typically depend on SSO integrations or directory data, which leave significant blind spots, especially when users access applications outside formal channels.
Next-gen IGA platforms take a more robust approach. They connect directly with SaaS APIs, analyze login activity, correlate expense reports, and leverage browser-level telemetry to uncover applications in use, whether sanctioned or not.
This expanded visibility enables you to:
- Identify every application in use, including those that bypass SSO or have not been formally onboarded.
- Understood actual usage patterns, including who is accessing what, how frequently, and whether that access is still justified.
- Optimize licensing and automatically revoke unused access to reduce both risk and waste.
This isn’t just about identifying apps, it’s about governing them continuously, based on real usage, across the full SaaS environment.
4. Unified identity lifecycle and governance
In traditional IGA setups, identity lifecycle management and access governance often operate in silos. An HR event may trigger provisioning, while certifications are run separately on fixed schedules with little connection to real-time context.
Next-gen IGA platforms break down that divide by integrating lifecycle automation and governance into a single, continuous flow. As users join, move across roles, or leave the organization. Their access adjusts in alignment with policy and context.
With this unified model, you can:
- Automate provisioning based on role, department, location, or other attributes, ensuring users get the right access from day 1.
- Trigger access reviews conditionally, based on specific events or risk factors, rather than relying solely on periodic certifications.
- Revoke access immediately across all connected systems when an exit is detected or a policy violation occurs.
Everything is governed centrally: from assigning to review to removal, eliminating delays, manual approvals, and ticket-based workflows.
This convergence of lifecycle and governance reduces both overhead and risk, while ensuring that access remains accurate throughout the identity journey.
5. Flexible, scalable, and built for modern IT environments
Your IT environment is no longer static. You’re onboarding employees across geographies, managing a fluid contractor ecosystem, and overseeing a surge in non-human identities from service accounts to API tokens. Traditional IGA tools weren’t built for this scale or complexity.
But next-gen IGA is.
These platforms are cloud-native, API first, and highly extensible, making them well-suited to dynamic environments where scale, speed, and adaptability are non-negotiable.
With next-gen IGA, you can:
- Support diverse identity types–including employees, vendors, freelancers, bots, and service accounts- within a unified governance framework.
- Adapt to organizational changes quickly, from Mergers and Acquisitions (M&A)- Driven restructuring to shifts in business units or reporting hierarchies.
- Integrate with evolving SaaS and cloud stacks through a wide range of prebuilt connectors and customizable workflows.
Whether you’re running a centralized IT model or enabling decentralized teams, next-gen IGA provides the agility and resilience needed to keep access aligned with business demands, without introducing operational overhead.
So, why was all this necessary? Next-gen IGA isn’t just an upgrade. It’s a shift in philosophy.
It puts your governance engine at the center of identity truth, fed by real-time signals, grounded in complete context, and built to act autonomously. When that becomes your system of record, access isn’t just compliant, it’s accurate, timely, and secure by design.
How Does Next-Gen IGA Become the System of Record?
In most modern IT environments, identity data is often scattered across multiple systems. Your HR system may be the source of truth for employees' attributes, but it doesn’t know anything about SaaS entitlements. Your directory might hold group memberships, but not who’s actively using which apps. And your ticketing system logs access requests, but can’t verify if the access was ever removed.
This fragmentation creates risk, slows down audits, and makes it nearly impossible to enforce consistent access policies.
Next-gen IGA solves this by becoming the central authority on identity and access across your organization–your system of record.
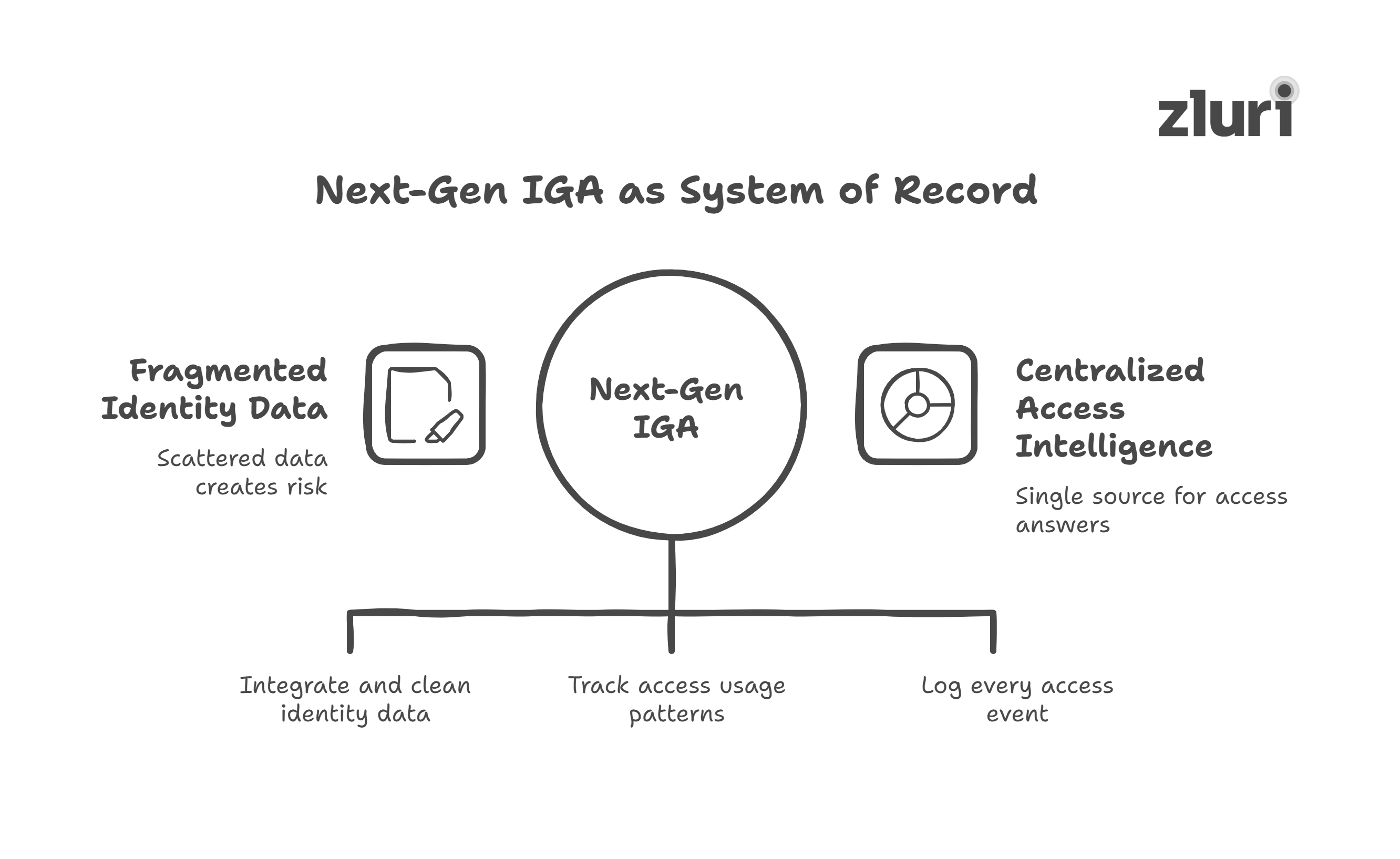
Here’s how it achieves that:
1. Aggregates & normalizes identity data from everywhere
Next-gen IGA integrates with all your critical systems, including HRMS, directories, SaaS apps, expense tools, endpoint agents, and even spreadsheets. But it doesn’t just pull data in. It correlates, cleans, and normalizes it.
You get a continuously updated inventory of:
- Every identity: human, contractor, or bot
- Every entitlement across apps, roles, and groups
- The reason behind the access
- Who approved it, and when
No more jumping between tools to piece things together. You get the complete picture in one place.
2. Builds a live view of access based on real usage
Being a system of record isn’t just about storing entitlements; it’s about tracking how access is actually used. Next-gen IGA monitors login patterns, app activity, and usage frequency to show you what’s still relevant and what’s not.
With this, you can:
- Make smarter provisioning and certification decisions
- Deprovision dormant or unused access automatically
- Provide auditors with usage-based evidence
Instead of managing theoretical access, you govern based on how things work in practice.
3. Captures a full history of access changes
You need more than a current snapshot. You need a traceable history. Next-gen IGA logs every access event, including when access was granted, changed, or removed, who approved it, and whether it complied with policy.
That means you’re always ready to:
- Respond to audit requests with clear, timestamped records
- Investigate incidents with a full access timeline
- Demonstrate how exceptions or risks were handled
It gives you the accountability that regulators and your security team expect.
The result? A single place for access intelligence. When IGA becomes your system of record, you stop chasing access answers across disconnected tools. You get one place that tells you:
- Who someone is
- What they have access to
- Why do they have it
- Whether it’s still needed
That clarity isn’t just operationally useful; it’s essential for security, compliance, and scalability.
The Benefits of Next Gen-IGA as a System of Record
When your IGA platform becomes the system of record for identity and access, you’re no longer making decisions in the dark or relying on outdated, disconnected data. You have a real-time, unified foundation that drives clarity, consistency, and confidence across your entire organization.
.png)
Here’s how that translates into meaningful benefits:
1. Stronger access controls, driven by real context
With accurate, centralized access to data, you can enforce least privilege more effectively, avoiding overprovisioning and relying on assumptions. You can:
- Grant access based on actual needs and roles, not just job titles
- Identify and remove access that’s no longer used or justified
- Confidently automate provisioning, deprovisioning, and reviews
The result? Fewer violations, access gaps, and more consistent policy enforcement.
2. Continuous compliance, not just point-in-time readiness
Most organizations panic when it’s time to prepare for audits because identity data is scattered and unreliable. With IGA as your system of record, compliance becomes part of your daily operations.
You can:
- Run access reviews based on real-time risk and usage.
- Maintain complete, timestamped audit trails for every access decision.
- Demonstrate adherence to frameworks like SOX, HIPAA, ISO 27001, and more without manual effort.
Instead of reacting to compliance requirements, you’re always prepared.
3. Faster response to identity risk
When identity and access data is centralized and up-to-date, your security response can be both faster and smarter.
You can:
- Immediately detect anomalies like excessive access, orphaned accounts, or unused entitlements.
- Trigger workflows to investigate or remediate risk automatically.
- Feed identity context into your SIEM stack to enrich threat detection and response.
This reduces the window of exposure and provides your security team with the necessary context to act decisively.
4. Improved operational efficiency
When governance and lifecycle management are integrated into one system, you eliminate redundant work and reduce dependency on manual processes.
You benefit from:
- Fewer tickets to the helpdesk for access requests or removals.
- Less back-and-forth during audits and certifications.
- Streamlined onboarding, offboarding, and access changes, all handled through automation.
You spend less time chasing access data and more time improving governance outcomes.
5. Better business alignment
By tying access decisions directly to identity attributes, app usage, and risk posture, IGA becomes more than a security control. It becomes a strategic enabler.
You gain:
- Clear visibility into who has access to what, across teams, departments, and vendors.
- A foundation to support M&A activity, role restructuring, and workforce transformation.
- The ability to scale identity governance as your business grows without adding complexity.
How Zluri Delivers as a Platform for Next-Gen IGA?
Zluri isn’t just adapting to the next generation of identity governance; it’s purpose-built for it. Designed specifically for modern, SaaS-heavy environments, Zluri helps you govern every identity (human or not), automate lifecycle changes, and make smarter access decisions based on real usage data.
Here’s how Zluri stands out as a next-gen IGA platform and why it’s uniquely suited to be your system of record for identity and access:
Or
Next-gen IGA isn’t just about modernizing an outdated system; it’s about solving challenges that current solutions still struggle with. Zluri is built from the ground up to meet that challenge. It helps you govern every identity, streamline access across apps (even the hard-to-integrate ones), and automate decisions with precision at scale.
Here’s how Zluri stands out as a next-gen IGA platform:
1. Connects seamlessly to apps others can’t reach
Most IGA tools struggle with unfederated, non-SCIM, or legacy apps. Zluri doesn’t. Its native iPaaS engine lets you integrate with virtually any application, within minutes, not months.
You can connect to:
- Unfederated apps (not tied to your IdP)
- Non-SCIM apps
- Legacy/on-prem tools
- GenAI-based apps and tools with no public APIs
Zluri also offers over 300 pre-built connectors, making it easy to hook into HRMS, finance, and collaboration apps without writing code. And if you do need something custom, developer toolkits (SDKs) let your team build out integrations for even the most stubborn.
2. Gives you unified visibility across your SaaS stack
With Zluri’s patented discovery engine, you get complete visibility into your SaaS ecosystem–across users, access, and apps (sanctioned or not).
You will see:
- All identities: employees, contractors, service accounts, and vendors
- Managed and unmanaged apps, including shadow IT
- App activity trends (30/60/90 days), last used timestamps, and dormant access
- Risk signals like overprovisioning or unused entitlements
It all comes together in a central dashboard, giving you a live system of record that’s accurate, up-to-date, and actionable. You can use it to review access, trigger automation, revoke dormant licenses, or simply keep your SaaS under control.
3. Automates identity workflows with granular precision
Zluri doesn’t just automate access; it gives you control over what gets automated and how it's done. With over 3500 actions across 160+ apps, you can design workflows that reflect exactly how your organization operates.
- In-app actions
Need to add new hires to specific Slack channels or set fine-grained permissions in Okta? Zluri lets you do that directly within the onboarding workflow.
During offboarding, you can transfer data, revoke access, reassign licenses, and ensure nothing is left behind.
- Conditional playbooks
You can build workflows that run based on dynamic conditions. For example:
“If a contractor hasn’t logged in for 30 days, remove access to high-risk apps automatically.”
Zluri executes the logic and updates access in real-time, eliminating the need for manual intervention.
- Policy-based automation rules
With Zluri, you get the flexibility to define your own granular automation rules. For example:
When a new employee from Marketing is added via Workday, assign them all the approved marketing tools.
These rules can also enforce RBAC and contextual access controls, such as granting access only to users based in India or restricting access to users from sanctioned geographies.
4. Supports workflow variables for dynamic communication
Do you need to automate reminders or approval requests? Zluri supports workflow variables, so you can personalize and trigger emails based on live user or app data.
For example:
Send a reminder to all finance app owners to approve access for [user] to [app] by [deadline].
Simply configure the variables, and Zluri takes care of the rest - no more manual emailing or chasing people down.
5. One license, no surprise fees
Unlike many IGA platforms that charge extra for every integration or add-on module, Zluri offers a transparent, all-inclusive pricing model. You get everything–connectors, workflows, custom rules, automation engine–without being charged extra.
That means you can scale your governance program confidently, without worrying about hidden costs.
Thus, it won’t be incorrect to say that Zluri doesn’t just modernize IGA; it redefines it. Legacy tools weren’t designed for the fast-moving, SaaS-heavy environments you manage today. Zluri helps you close that gap.
It gives you:
- Deep, continuous visibility into every app and identity.
- Automated, usage-aware lifecycle and access governance.
- Scalable control across users, vendors, bots, and more.
- A true system of record for identity and access.
If you’re serious about moving beyond checkbox compliance and toward proactive, identity-first security, Zluri is the next-gen platform that gets you there. To know further, book a demo today.
Why the Future Of Identity Governance Starts Here
Identity is no longer just an IT concern; it’s the foundation of how your organization stays secure, agile, and compliant. And in a world where users, apps, and access patterns constantly evolve, static, outdated IGA tools simply can’t keep up.
Next-gen IGA flips the script. It gives you:
- Real-time visibility across your SaaS and cloud environments.
- Lifecycle automation that adapts to change, not just predefined rules.
- Governance based on actual usage, not assumptions.
- A single, reliable system of record that reflects how your organization truly operates.
This isn’t just about improving processes. It’s about building an identity-first foundation that strengthens your security posture, eliminates operational inefficiencies, and gives your teams the confidence to scale.
And with platforms like Zluri, that future isn’t operational; it’s available right now.
If you’re ready to modernize identity governance, move beyond compliance checklists, and take full control of your access ecosystem, this is your moment. In today’s world, organizations that govern identity effectively are the ones best equipped to thrive.









.svg)














