Orphaned accounts, left active when employees exit or change roles, pose security risks. IT managers should identify them, and mitigate risks to enhance security and compliance. This article will guide you through the concept of orphaned accounts in detail.
Orphaned accounts are a hidden threat within many organizations. These are user accounts that remain active even after employees leave or change roles. For IT managers, these forgotten accounts can become a major security risk, exposing sensitive data and creating vulnerabilities. This can lead to unauthorized access, data breaches, and compliance issues.
However, identifying and mitigating orphaned accounts is entirely possible with the right strategies. Regular audits, automated tools, and strict offboarding processes are key. By implementing these measures, you can enhance security, prevent unauthorized access, and ensure compliance with security policies, protecting their organization from potential threats.
Now, we will help you understand the concept of orphaned accounts in detail. Let’s begin.
What are Orphaned Accounts?
The term "orphan accounts" refers to user accounts that have been abandoned. An orphan or orphaned account refers to a user account that can grant access to corporate systems, services, and applications but lacks a valid owner. This stands in contrast to an active user account owned by a currently employed individual.
To illustrate the significance of addressing orphaned accounts and the potential security risks they pose, consider this scenario. Imagine a skilled content marketer who dedicated five years to a company and now decides to move on. While most user accounts are properly deactivated or deleted during offboarding, one account slips through the cracks. This particular account provides access to a legacy system the marketer rarely uses.
As time passes, this neglected account becomes an "orphaned account." Its existence goes unnoticed and remains active, creating a security vulnerability. If exploited, it could result in unauthorized access to sensitive data or systems.
This example highlights the concept of orphaned accounts, where user accounts or access privileges are left unattended after an employee's departure, posing potential security risks. It emphasizes the importance of understanding and effectively managing these accounts.
Implementing proper procedures, conducting regular audits, and utilizing automated solutions are crucial for promptly identifying and addressing orphaned accounts. This approach ensures a robust cybersecurity posture and safeguards critical resources.
What Are the Risks of Orphaned Accounts?
Orphaned accounts pose several risks to the security and integrity of an organization's digital environment. Here are the key risks associated with orphaned accounts:
- Unauthorized Access: Orphaned accounts, when left unattended, can become a gateway for unauthorized access to sensitive data, systems, or applications. Hackers often target these overlooked accounts as potential entry points into an organization's network.
- Data Breaches: If exploited, orphaned accounts can lead to data breaches, exposing confidential information. Unauthorized users gaining administrative access to these accounts may compromise sensitive data, resulting in financial losses, reputational damage, and legal consequences.
- Compliance Violations: Orphaned accounts can lead to non-compliance with industry regulations and data protection laws. Failing to manage access properly may result in severe penalties, especially in sectors where strict compliance is mandated, such as healthcare, finance, and government.
- Increased Vulnerability to Cyber Attacks: Cybercriminals often exploit forgotten accounts as potential entry points for launching attacks, including phishing, malware injection, or lateral movement within the organization's network. This heightened vulnerability can lead to a broader security compromise.
- Data Tampering or Destruction: In certain cases, unauthorized access through orphaned accounts may lead to data tampering or destruction. This can have severe consequences for an organization, affecting its operations, reputation, and stakeholder relationships.
- Difficulties in Incident Response: During security incidents or breaches, orphaned accounts can complicate incident response efforts. Identifying and mitigating the impact of a breach becomes more challenging when there are overlooked accounts with active access privileges.
- Resource Wastage: Orphaned accounts represent unused resources that can potentially be reallocated for malicious purposes. This resource wastage may include computational power, storage, or network bandwidth, which could otherwise be utilized more efficiently.
- Internal Threats: Orphaned accounts may be targeted by disgruntled former employees or insiders with malicious intent. Without proper management, these accounts may serve as a tool for internal threats, enabling individuals to exploit their previous access privileges.
To sum up, recognizing and addressing the risks associated with orphaned accounts is crucial for maintaining a secure and compliant digital environment. Organizations must implement effective identity and access management practices to mitigate these risks and uphold the overall security of their systems and data.
Why It Is Important To Detect & Manage Orphaned Accounts?
The comprehension and proactive management of orphaned accounts play a pivotal role in upholding a robust cybersecurity posture for any organization. Let's delve into the significance of understanding and efficiently addressing orphaned accounts to safeguard your organization's security.
- Security: Neglected accounts pose a potential risk, serving as exploitable gateways for malicious entities to gain unauthorized access to your systems. This vulnerability could lead to severe data breaches, compromising sensitive information and exposing your organization to potential financial repercussions. Consequently, prioritizing safeguarding your sensitive data and intellectual property becomes imperative.
- Compliance: In today's regulatory landscape, adherence to industry standards and data protection laws is non-negotiable. Your teams are tasked with maintaining vigilant oversight of user access, consistently assessing privileges, and retracting unneeded permissions. Overlooking orphaned accounts could potentially result in violations of compliance protocols, inviting substantial penalties.
- Resource Optimization: Orphaned accounts act as unused seats on a fully-booked flight, consuming valuable resources such as licenses, server space, and IT support without contributing to your business objectives. Identifying and eliminating these accounts frees up resources for active users, optimizes your operations, and saves costs in the process.
Now, let's explore the root causes behind orphaned accounts within organizations.
How Do Orphan Accounts Occur? - Key Reasons
Understanding the underlying causes of orphaned accounts is pivotal in bolstering cybersecurity defenses. Recognizing these potential pitfalls enables proactive implementation of strategies to mitigate risks and maintain a resilient digital infrastructure.
- Employee turnover:
Employee turnover refers to the rate at which employees leave an organization and new employees join. When employees depart, their user accounts might remain active and unmonitored, especially during the transition period. The rush of managing these transitions can lead to unintentional oversight of deactivating or deleting accounts, thus causing orphaned accounts.
- Mergers & acquisitions or organizational changes:
Mergers, acquisitions, and other organizational changes can significantly challenge managing user accounts. Amidst the complexity of restructuring, some accounts might be neglected, resulting in dormant and unnoticed accounts.
- System migrations:
Migrating to new and advanced systems can be exciting but overwhelming. During such transitions, certain accounts might not be properly transferred or deactivated, potentially leaving vulnerable access points in the system.
- Negligence or oversight:
Even well-intentioned admins may occasionally overlook the need to remove no longer necessary accounts. This inadvertent negligence can create opportunities for unauthorized access to your organization's resources.
Consider a reputable law firm that unintentionally retains the account of a paralegal who departed the firm twelve months back. The paralegal's account retains its ability to access sensitive case documents and client correspondences. This situation could potentially result in unauthorized access to the firm's valuable resources.
- Outdated documentation:
Documentation might not always keep pace with changes in the dynamic business environment. Outdated or inaccurate records can lead to orphaned accounts that go unnoticed among the vast amount of data.
For instance, a tech startup hires new employees and assigns privileged accounts based on an old organizational chart. This leads to new hires receiving access to systems they shouldn't have access to, causing a breach in confidentiality.
- Account holder's inactivity or departure:
A list of accounts can become abandoned when the holder remains inactive for extended periods or takes a prolonged leave of absence. Without periodic reviews, these accounts might be forgotten and left active.
For instance, the head developer goes on an extended sabbatical in an engineering firm without appropriately deactivating their account. During this absence, an unauthorized individual can gain entry to the developer's account and exploit their login credentials.
- Security breaches:
In the unfortunate event of a security breach, immediate attention focuses on damage control. During this chaos, some accounts may remain unattended, providing openings for further exploitation by malicious actors. It is essential to promptly address and secure all accounts to prevent further damage.
Now comes the real challenge: how to identify these orphaned accounts. So, here it goes!
How to Find Orphaned Accounts Within Your Organization?
Detecting orphaned accounts in your organization is crucial for ensuring a secure and efficiently managed digital environment. Follow this comprehensive guide to identify and address orphaned accounts effectively:
- User Account Audits: Regularly conduct audits of user accounts to meticulously review and evaluate the status of each account. Verify whether accounts are actively linked to current employees or if they remain dormant.
- Access Reviews: Perform a thorough access review process for systems, applications, and databases. Confirm that each user account is associated with an active employee or an approved role. Investigate any account not connected to an existing employee or role.
- Integration with HR Systems: Integrate your identity and access management tools with HR systems for real-time updates on employee status. This integration facilitates the automatic deactivation of accounts for individuals who are no longer part of the organization.
- Automated Tools and Scripts: Employ specialized automated tools and scripts to discover orphaned or unused accounts. These tools efficiently scan your network, identify inactive accounts, and generate detailed reports for further analysis.
- Review Log Files: Scrutinize log files and system activity records for any unusual or unauthorized account access. Anomalies in user activity may signal the exploitation of orphaned accounts.
- Collaboration with IT and HR Departments: To streamline the offboarding process and foster collaboration between IT and HR departments. Promptly deactivate accounts when employees leave the organization, minimizing the chances of accounts becoming orphaned.
- Periodic Access Certification: Implement periodic access certification processes where managers and administrators validate the necessity of user accounts within their purview. This ensures that only relevant accounts remain active and reduces the risk of orphaned accounts.
- Documentation and Record-Keeping: Maintain comprehensive documentation of user accounts, access permissions, and employee status. Regularly update and cross-reference this information to identify any discrepancies or orphaned accounts.
- Alerts and Notifications: Configure alerts and notifications within your identity and access management system to highlight accounts showing signs of inactivity or potential orphaned status. Automated alerts prompt timely investigation and action.
- Training and Awareness: Conduct training sessions for IT staff and system administrators to emphasize the importance of identifying and managing orphaned accounts. Knowledgeable personnel are better equipped to address and mitigate this security risk.
By implementing these strategies, your organization can successfully identify and address orphaned accounts, fostering a more secure and streamlined digital environment.
Now, you may wonder, even if we successfully identify orphaned accounts, how can we effectively manage and mitigate them? Let's delve into some best practices to address this concern.
4 Best Practices For Managing Orphaned Accounts
To enhance security and minimize the risks associated with orphaned accounts in your organizational systems, consider implementing the following best practices:
1. Ensuring robust account deprovisioning & access control procedures
When an employee departs from your organization, prompt and efficient deactivation or deletion of their accounts becomes crucial. Failing to do so can expose your organization to significant security risks, potentially leading to unauthorized access and the misuse of valuable company resources.
To safeguard against these threats, a well-defined process should be established to revoke user access to all systems and applications, thereby ensuring that former employees no longer retain any privileges within the organization.
By adhering to such practices, your teams can significantly reduce the likelihood of security breaches stemming from orphaned accounts. The deprovisioning process acts as a vital line of defense, preventing unauthorized access to sensitive information and bolstering the overall cybersecurity infrastructure.
Implementing robust account deprovisioning and access control procedures demonstrates a commitment to safeguarding confidential data and maintaining the integrity of business operations. Your partners and clients are more likely to trust your organization if you take proactive measures to protect their information.
2. Conducting regular & thorough account audits & reviews
Employee roles may shift, or team members might depart from your organization, inadvertently leaving behind inactive or orphaned accounts within your systems. Such dormant accounts can serve as vulnerable entry points for unauthorized access or malicious activities, posing substantial risks to your sensitive data and confidential information.
By implementing a well-structured routine for account audits, you gain the ability to promptly identify and eliminate these dormant or unnecessary accounts from your network. This proactive approach aids in mitigating security threats and safeguarding your organization's valuable assets.
Furthermore, conducting regular account reviews ensures that all active accounts align with the latest security policies and compliance requirements. Staying updated with the rapidly changing cybersecurity landscape is essential, and these reviews act as a safeguard against unauthorized access, reducing the likelihood of potential breaches and data leakages.
Conducting periodic user account audits and reviews demonstrates your commitment to maintaining a robust and secure your business environment. It reflects your dedication to safeguarding your company's proprietary information and the sensitive data entrusted to you by your clients and partners.
By continually optimizing your access control infrastructure through these audits, you reinforce confidence in your business relationships, showcasing your adherence to industry best practices and data security standards. Ultimately, this approach fosters trust and reliability, positioning your organization as a reliable and security-conscious partner in the SaaS landscape.
3. Utilizing automated solutions for effective orphaned account detection
Manual identification of orphaned accounts can be a cumbersome and error-prone process, consuming valuable time and resources. To optimize this workflow and ensure precision, your organization should turn to the power of automated solutions specifically designed for detecting and handling orphaned accounts.
You can significantly improve your account management procedures by embracing automated tools tailored to orphaned account detection. These cutting-edge solutions continuously monitor user activity across various systems and applications, efficiently cross-referencing it with the employee database. As a result, any inconsistencies or dormant accounts are promptly identified and flagged for immediate action.
The real value of automated solutions lies in their ability to save time and effort and their capacity to offer real-time visibility into account activity. This real-time insight empowers your teams to stay ahead of potential issues and take proactive measures to address them promptly. As soon as an orphaned account is detected, alerts are triggered, prompting swift action to revoke access and prevent any unauthorized usage.
4. Implementing role-based access control & least privilege principles
Role-based access control (RBAC) is a proven strategy that streamlines access management by assigning permissions based on job roles. Rather than granting blanket access, RBAC ensures that employees receive only the necessary privileges to fulfill their specific responsibilities. This approach aligns access rights with job functions, creating a clear and organized system for managing user permissions.
For example, in an organization, RBAC would grant marketing personnel access to marketing tools and data while restricting their access to financial systems. Conversely, finance personnel would have access to financial data and tools but not marketing resources. This role-centric approach limits the risk of data breaches and unauthorized access by reducing the exposure of sensitive information to only those who genuinely require it.
Complementing RBAC, the principle of least privilege further strengthens cybersecurity. It operates on the premise of granting the absolute minimum permissions necessary for users to perform their specific tasks effectively. This means that employees have access to only the essential resources and data, even within their designated roles, leaving out unnecessary privileges.
By adhering to the principle of least privilege, your teams can minimize the potential impact of security breaches, even if an account becomes orphaned or compromised. For instance, if an employee's account remains active after their departure, the limited access granted through RBAC and the principle of least privilege would restrict the potential damage that could be caused by unauthorized users attempting to exploit the account.
In larger organizations with a significant number of users, manual detection of orphaned accounts can be time-consuming and prone to errors. Automated solutions, integration with HR systems, access reviews, RBAC, and monitoring user activity are crucial to efficiently and effectively detect and manage orphaned accounts. These measures help maintain a secure and well-governed IT environment, minimizing the security and compliance risks associated with orphaned accounts. That’s where Zluri stands out. Let’s explore how!
Managing Orphaned Accounts with Zluri's Access Management
Effective access management and permissions are crucial for upholding both security and productivity. Yet, the intricacies of overseeing user access can lead to the creation of orphaned accounts, presenting substantial risks to data security and impeding operational efficiency. Zluri's access management platform emerges as a dynamic solution mitigating the challenges of orphaned accounts and streamlines access management to drive enhanced productivity.

Key Features Of Zluri contributing to a seamless access control
- Intelligent Data Discovery To Identify Orphaned Accounts
Zluri's smart data engine uses nine discovery methods, including MDMs, IDPs & SSO, direct integration with apps, finance & expense management systems, CASBs, HRMS, directories, desktop agents (optional), and browser extension (optional). This ensures precise identification of users and critical app access, reducing the risk of overlooking orphaned accounts.
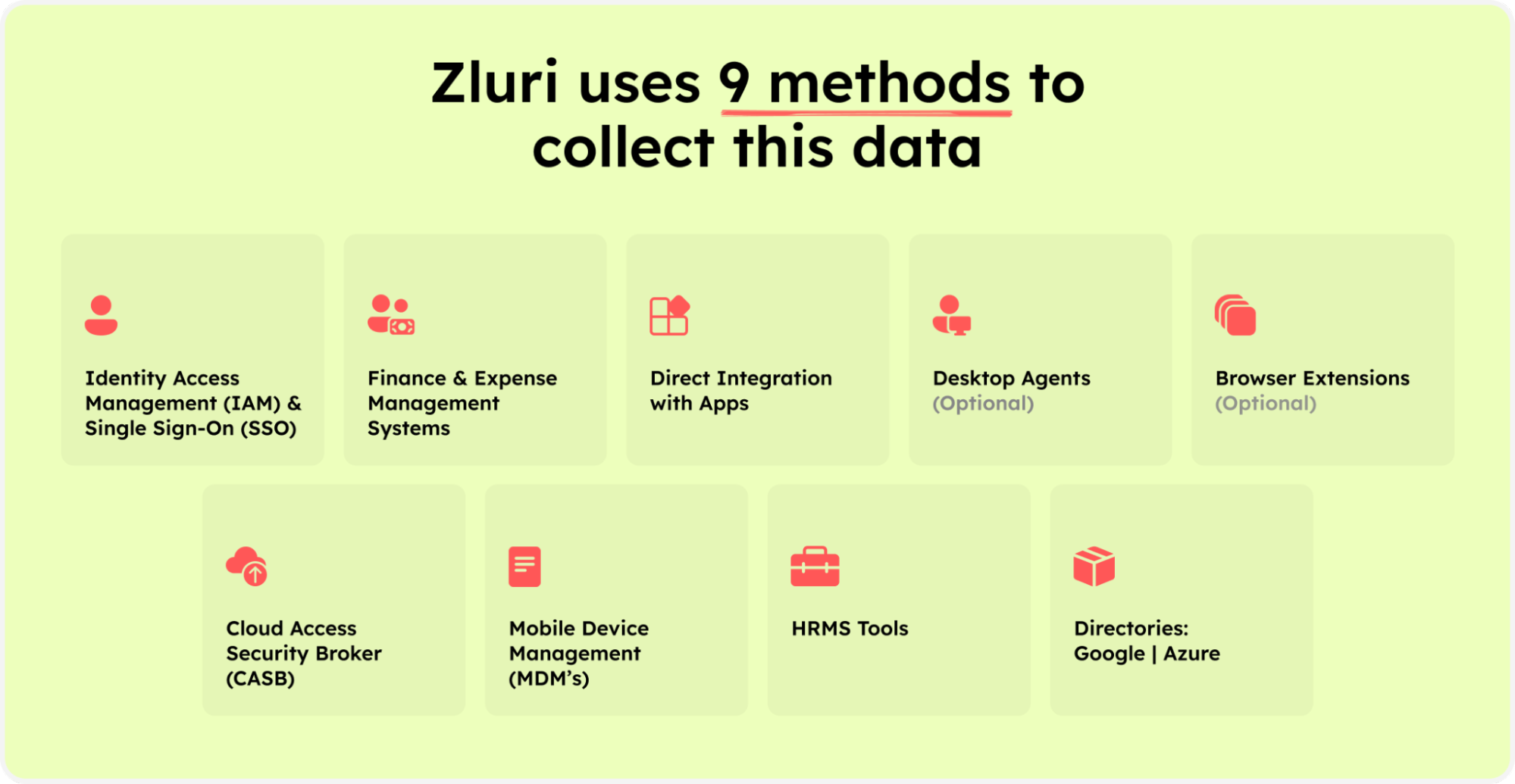
Zluri’s nine discovery methods
- Preventing orphaned accounts With Automated User Access Management:
Zluri's automation engine simplifies access management tasks, automating user provisioning, deprovisioning, and adjustments. This ensures accurate and prompt user account management, minimizing the risk of orphaned accounts during employee transitions.
Advanced algorithms proactively manage user access throughout the organizational lifecycle, dynamically adapting permissions during role changes, preventing the formation of orphaned accounts.
- Real-time Activity Tracking and Alert System For Anomalous Access :
Zluri's vigilant monitoring system tracks user activities in real-time, alerting admins to any suspicious behavior promptly. This proactive approach ensures a swift response to potential security risks, preventing orphaned accounts from becoming vulnerable access points.
- Effortless User Access Provisioning/ Deprovisning with efficient Onboarding & Offboarding Workflows:
Zluri streamlines onboarding with customizable workflows, ensuring precise access levels for new hires and minimizing the risk of orphaned accounts. Further, its offboarding solution automates access revocation and secure data backup, preventing the creation of orphaned accounts during departures.
- Strict orphaned account control with Self-Service Solution - Employee App Store (EAS)
Zluri's Employee App Store (EAS) is a self-service solution for efficient access request management. It enables effective collaboration between team members and approvers in reviewing and approving requests, ensuring employees get precise access levels for their roles. The EAS operates on a robust approval system, fostering collaboration and understanding within the organization.
- User Access Reviews/Certifications for Orphaned Account Detection:
Zluri's access management solution features an access certification process that autonomously detects orphaned accounts with precision. The automated user access review ensures higher accuracy and consistency in evaluating user permissions, enhancing the security and organization of digital environments. Further, it's also highlighted in Kuppingercole's research and analysis report that it automatically triggers remediation actions, including access revocation and notifications, addressing security threats promptly without manual intervention.
In short, Zluri centralizes user information, ensuring accurate and accessible records for streamlined access reviews, fortified security, and reduced administrative burdens.
So what are you waiting for? Book a personalized demo today!
FAQS
1. How frequently should organizations conduct user access reviews to detect orphaned accounts?
The frequency of user access reviews depends on organizational policies, industry regulations, and the rate of employee turnover. However, conducting reviews at least quarterly is a common best practice to promptly identify and address orphaned accounts.
2. Can automated solutions help prevent orphaned accounts?
Yes, automated solutions, such as identity governance and access management platforms, can significantly help prevent orphaned accounts. These tools streamline onboarding and offboarding processes, automate access adjustments, and facilitate regular user access reviews for enhanced security and compliance.
3. What are the consequences of regulatory non-compliance due to orphaned accounts?
Regulatory non-compliance resulting from orphaned accounts can lead to severe consequences, including legal penalties, reputational damage, and loss of trust from stakeholders. Ensuring proper access management is crucial for meeting compliance requirements.









.svg)



.svg)
.svg)
.svg)
.svg)

.svg)

.svg)

.svg)
















.webp)







.webp)
.webp)





.webp)