Service accounts are non-human accounts primarily used for automating various system functions. Further, they often act as accounts that critical applications or services use to interact with operating systems to keep everything running smoothly.
But, with an increase in SaaS adoption, the number of service accounts is also rising, posing a significant challenge for IT teams to manage them efficiently.
Why is there a need to manage these service accounts? These non-human accounts come with their own set of access permissions and privileges, just like user accounts. So, mishandling their access permissions could potentially expose security vulnerabilities, jeopardizing the safety of organizations' sensitive SaaS app data.
For instance, often service accounts are linked to critical business applications, requiring privileged access to servers, databases, and other essential assets. So, if a single service account falls into the hands of an unauthorized user/malicious attacker. In an instant, they can exploit this backdoor to get complete control over privileged assets, endpoints, and sensitive data.
This is why it is essential to manage and protect service accounts adequately. Your IT team can safeguard the organization's data, apps, systems, and other assets by effectively managing these accounts.
However, this is not the only challenge that your IT team will come across while managing service accounts; there are several others that need to be mitigated. So, let's take a quick look at the other challenges to better understand the complexities involved.
Challenges IT Team Encounter While Managing Service Accounts
Mismanagement of service accounts can lead to significant security risks for organizations due to several reasons. Some of the reasons are stated below:
- In most cases, IT Operations and support staff lack a complete list of all services running under service accounts. This makes service accounts an easy target for threat actors seeking to move laterally across the network, making them a primary entry point for potential attacks. It is crucial for organizations to understand how service accounts function and adopt best practices for proactive management, limiting their privileges to the minimum necessary.
- Since non-human entities mainly use service accounts to perform operations, traditional security measures like two-factor authentication are not applicable as they require human interaction. Additionally, passwords of service accounts are typically set to be permanent to avoid disruptions. This lack of strong security controls makes service accounts vulnerable to attackers.
- With the rise of digital transformation and cloud computing, service account management has evolved from a one-time effort to an ongoing process that requires regular access reviews.
- Another challenge in managing service accounts lies in the absence of a centralized repository. For example, unlike user accounts managed through HR applications, service accounts lack a single system of record. They are tied to applications, many of which fall under the purview of development teams. This lack of a single source of record hinders efficient identity governance for service accounts.
- Furthermore, the identity of service account owners is often unknown, making it difficult to enforce service account management and lifecycle changes when account owners change. This lack of visibility and accountability can lead to security vulnerabilities and inconsistent access controls for service accounts.
Now that you know the challenges, it's time to explore how your IT team can tackle them head-on by implementing effective service account management strategies.
Effective Ways Of Managing & Governing Service Accounts to Mitigate Security Risk
By implementing the below strategies, your IT team can seamlessly manage and govern service accounts. This will further help them safeguard the organization’s SaaS app data.
- Identifying All The Service Accounts & Categorizing Them Based On Their Importance
Why is it so important to discover service accounts? Well, if IT teams don't know where the service accounts are or how many of them exist within the organization, it becomes challenging for the team to protect them. Due to a lack of visibility, these accounts could act as secret backdoors, allowing unauthorized users and hackers to breach and compromise sensitive data.
Also, it is important to identify all the service accounts because it further gets easier to categorize them based on their importance.
But it becomes difficult to identify these accounts when the IT team relies on manual method which is not only prone to errors but also inefficient. The solution to this is to opt for a modern identity governance and administration (IGA) platform like Zluri.
Why Zluri? It offers a data discovery engine feature that helps your IT team find all the service accounts present within the organization.
How does it work? Zluri uses nine discovery methods, i.e., MDMs, IDPs & SSO, direct integration with apps, finance & expense management systems, CASBs, HRMS, directories, desktop agents (optional), and browser extension (optional).

Zluri’s nine discovery methods
By implementing these methods your IT team will gain complete visibility into accounts, including how many service accounts are there, which users are accountable for these accounts, account status (active or inactive), the level of permissions these accounts hold, and more.
Armed with these insights, your team can further categorize them based on their criticality and the systems they can access, for example, service accounts that handle sensitive data and are vulnerable to attacks, will be categorized under critical accounts.
- Ensure That All Service Accounts Follow The Principle Of Least Privilege
IT teams need to implement a least privilege policy to ensure all the service accounts only have access permissions that are required to perform their designated operations. This approach minimizes the attack surface and limits the potential damage that could occur in the event of a security breach.
But how to implement the least privilege policy? Well, with Zluri your team can effectively enforce the least privilege policy. It strictly adheres to the policy and helps your IT team ensure only the right accounts are granted the access to right apps, systems, and data, with limited access permission required to perform certain tasks.
By doing so, your IT team can significantly reduce the chances of unauthorized access, data leaks, and other security vulnerabilities associated with excessive privileges.
- Get Rid Of Service Accounts That Are No Longer Needed
Remove service accounts that you no longer use, as outdated and inactive accounts often become an easy target for attackers trying to breach into your system. Not only this but if they clutter up the directory, it becomes challenging for the IT team to manage the service accounts properly. However, by removing unnecessary accounts, your IT team can ensure and maintain a more secure environment for sensitive data.
How does Zluri work in this scenario? It sets rules and policies for controlling access, allowing service accounts to access only the most important data or SaaS apps. If there's any mismanagement and a service account tries to access apps or data it shouldn't, your IT team gets an immediate alert. They can quickly block or suspend the account to stop any unauthorized access.
Zluri also lets your IT team decide how long a service account can have access. After the assigned time is up, Zluri automatically revokes the access, so the account no longer has unnecessary privileges to the SaaS app data.
Additionally, Zluri helps your IT team find inactive and outdated service accounts, which they can then terminate. By setting up these policies, your team can control specific privileges and prevent unauthorized access to your network and resources, safeguarding your crucial SaaS app data from security threats.
- Conduct Timely Access Review To Govern Service Accounts Access Permissions
To ensure the security and efficiency of your service accounts, it is essential to conduct regular access reviews. These reviews help your IT team examine whether the permissions granted to each service account align with your organization's established policies and adhere to compliance requirements.
Furthermore, by regularly reviewing the access of service accounts, your IT team can identify and rectify any instances of excessive or unnecessary privileges that may have been granted over time. This proactive approach helps in minimizing the risk of security breaches such as Zluri restricting unauthorized users from accessing critical systems and sensitive SaaS app data.
How does Zluri conduct an access review? Zluri automates the entire access review process, gathering all the necessary service account access data in one place. This makes the reviewing process much easier and more efficient for your team.
Not only that, Zluri's unified access review feature helps your IT team easily see which users can access the service accounts. Zluri gets this information from an access directory where all the access-related data is stored in one central place.
Using this data, your IT team can check which service accounts can access which all systems, what access permissions they are assigned, and more. Armed with these insights, your IT teams can ensure the service accounts have the right access privileges based on their designated roles.
To keep everything running smoothly, Zluri's activity & alerts feature provides real-time updates on service account activities and notifies IT teams about new logins. These insights help reviewers quickly and confidently make decisions during the access reviews process, ensuring the right service accounts have the right access all the time.
So no more manual headaches with spreadsheets and JSONs, your IT team can automate the access reviews process seamlessly. Just head to Zluri, create a certification, and select the apps and accounts you want to review, and rest the reviewers will review and update you about the compilation via email.
By automating this process, you get 10 x better results than manual methods and save your IT team's efforts by 70%.
Furthermore, once you have gained access to contextual data through Zluri’s unified access feature, you can step further by creating access rules around these insights. For example, if any service account has admin-level access permissions on Salesforce, you can easily set up a review policy specifically tailored to that scenario.
Next comes the schedule certification feature, where you can create certifications based on the gathered information. This allows you to take action based on the insights you've gained. For instance, you can use data like last login, service account status (active or inactive), and more.
With Zluri's context-rich information, your team can confidently take actions that align with your access management policies. It's a smarter, more efficient way to ensure the right access for the right users, all while keeping your data secure. Zluri's automated access reviews and access rules are the key to simplifying your access governance process.
After completing the access review, the necessary changes will be implemented based on the actions set during certification creation. These actions, such as access modification or removal, are all part of a secure access orchestration process. This process ensures that access is managed securely and efficiently, protecting your organization's data and resources.
For example, when creating a new certification in Zluri, your team will encounter configuration actions to set up deprovisioning and modification playbooks. If the reviewers decline access permissions, the deprovisioning playbook will automatically run. The same goes for the modification playbook. Reviewers must provide reasons for declining or modifying access permissions, in both cases.
It's important to note that these actions will happen automatically after the review is completed, which is why this process is called auto-remediation.
Here’s how you can create access certification in Zluri:
Step 1: From Zluri’s main interface, click on the ‘Access Certification’ module.
Step 2: Now select the option ‘create new certification.’ You have to assign a certification name and designate a responsive owner to oversee the review.
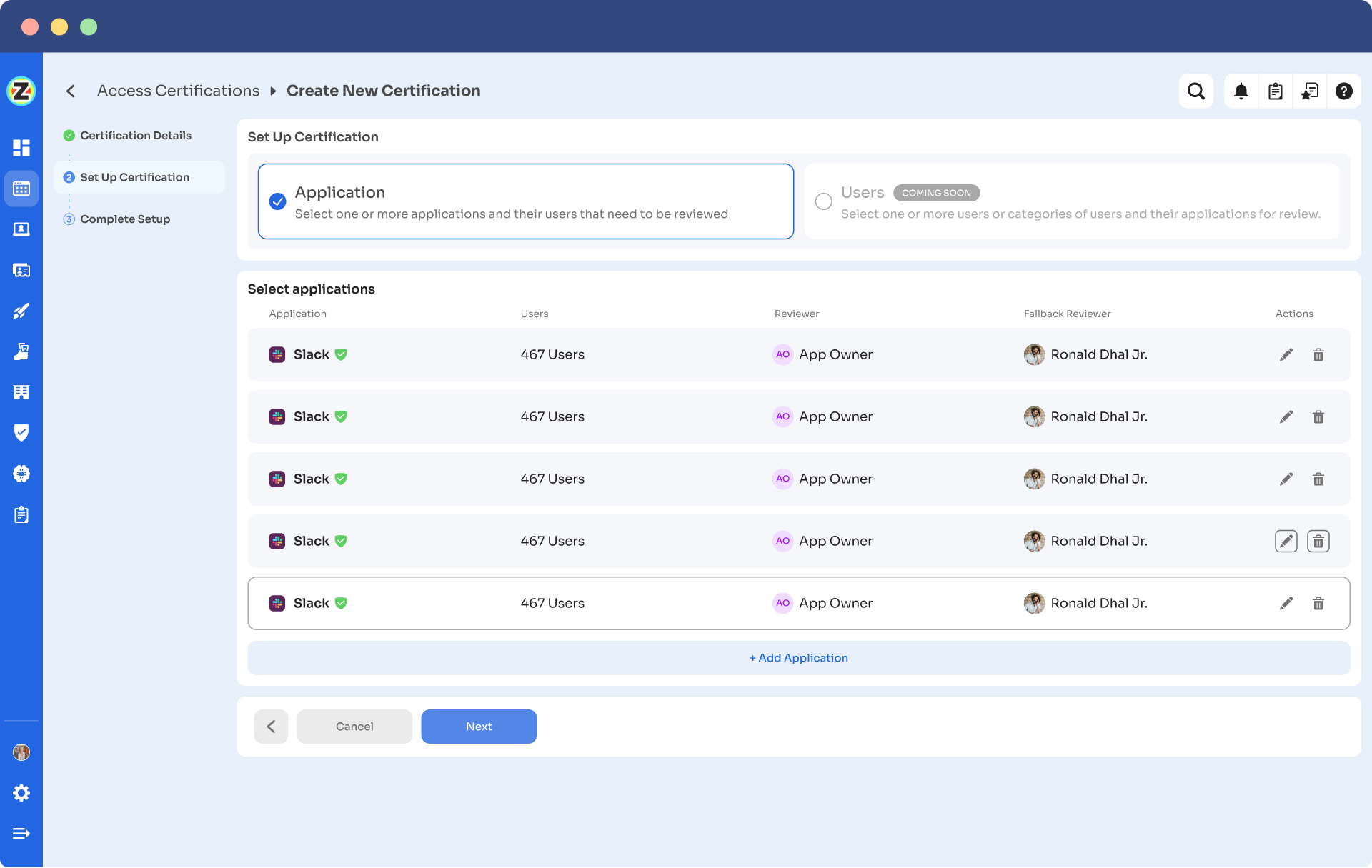
Step 3: Under Set Up Certification, choose the ‘Application’ option. Proceed further by selecting the desired application for which you want to conduct the review and choose a reviewer (generally, the primary reviewers are the app owners) accountable for reviewing access to that particular application.
After that, you need to select the fallback owner/reviewer; if the primary reviewer is unavailable, the fallback owner can review the user access (you can select anyone for the fallback reviewer whom you think is responsible enough). Also, the reviewers will get notified through the mail that they will conduct a review.
Once you are done selecting the reviewers, you can click on Next.
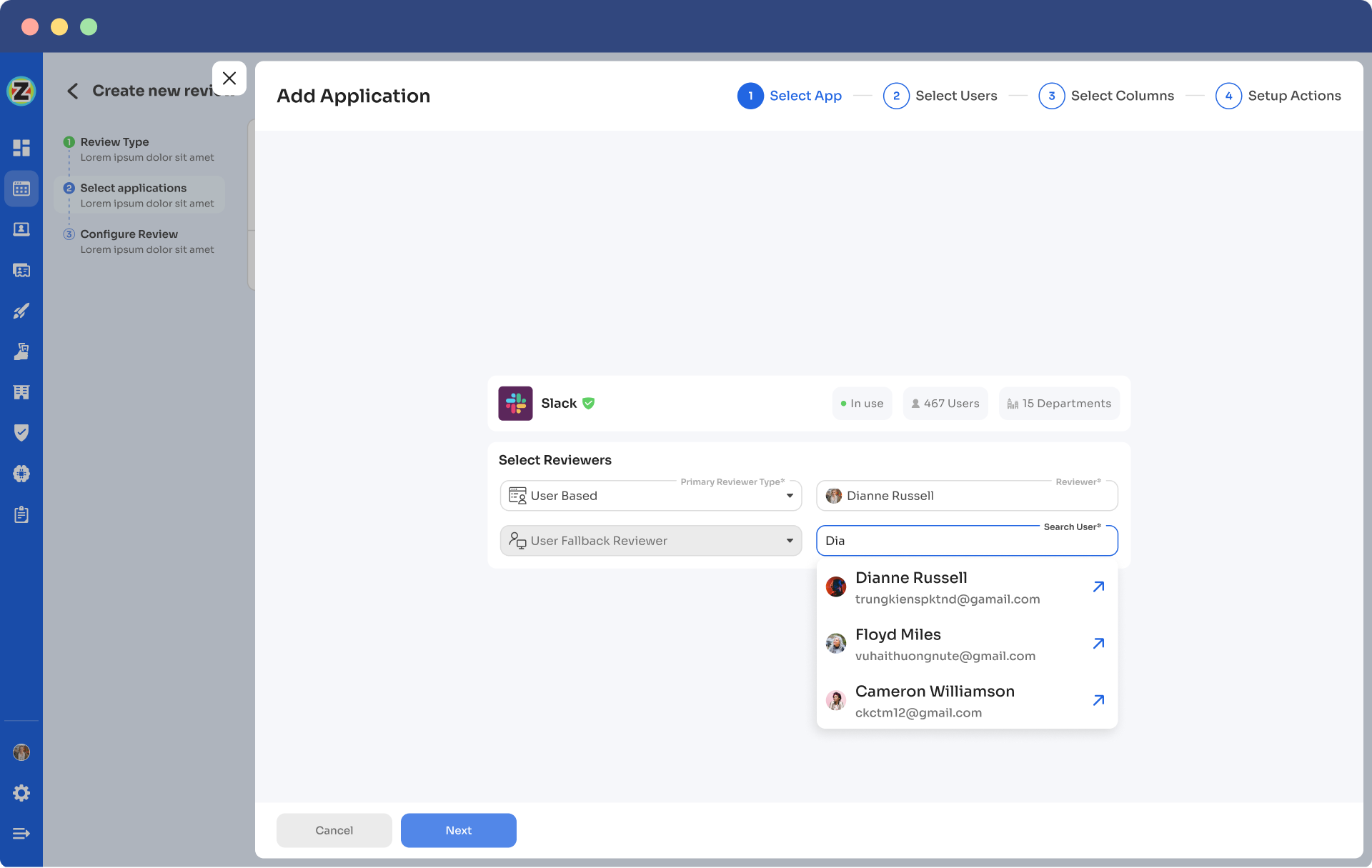
Step 4: Select Users for Review; choose the users you want to review for the selected application. Once you are done selecting the users, click on next. You will be able to view all the information related to the users. Then you need to specify the criteria or parameters such as user department, job title, usage, etc. Now click on update and then click on next.
Note: Select only relevant data points you wish your reviewers to see while reviewing the access. By filtering the criteria appropriately, you enable your reviewers to make swift and well-informed decisions, streamlining the review process and ensuring efficiency.
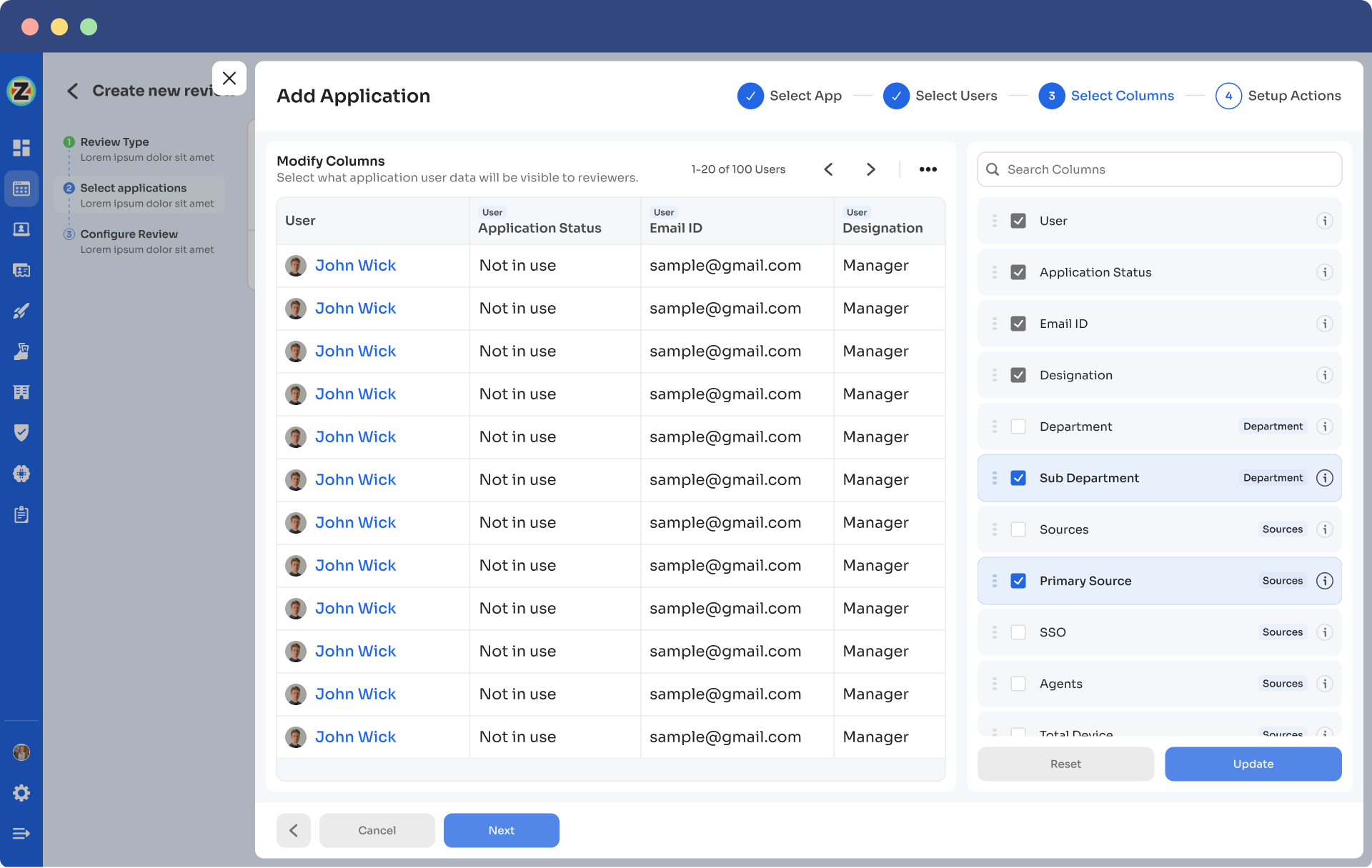
Step 5: Now, the Configure Action page will appear; basically, here, you have to choose actions. These actions will run post the review.
There are three actions:
Approved - Once reviewers approve the user access, Zluri won't run any action, the users can continue with their same access without any interruption.
Rejected - When the reviewer declines or doesn’t approve the user access, you have to run a deprovisioning playbook to revoke that application's access from the user. If the user has access to critical apps, then you can request the assigned reviewer to manually deprovision the user access, or else Zluri will auto-remediate if it’s not critical access.
Modify - In this last case, you again need to create a playbook to modify the user access. However, you need to state whether the access permission needs to be upgraded or degraded.
Step 6: You can schedule the actions by setting up the start date and within what time you want the review to be completed.
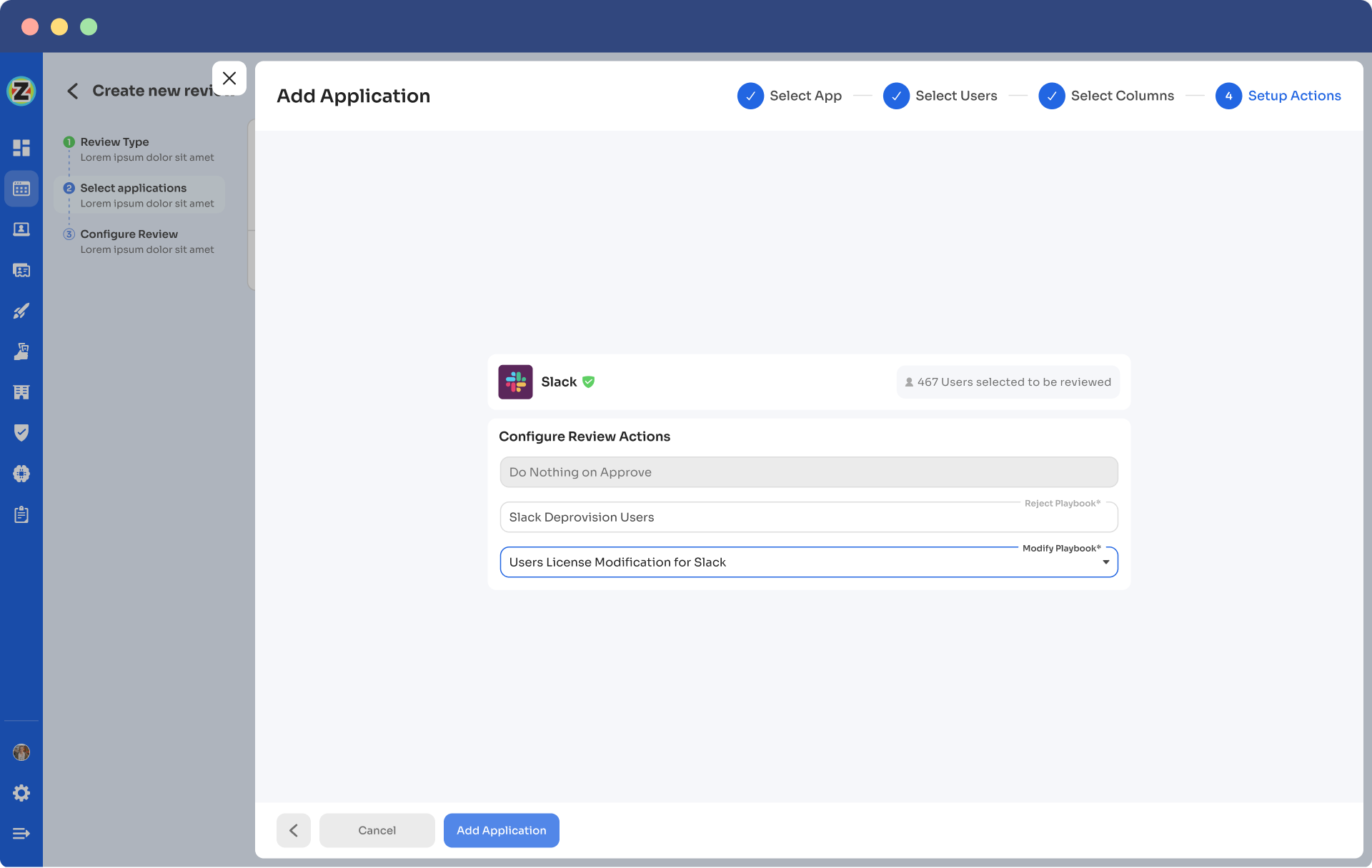
Step 7: Lastly, you can keep track of the automated access review process by clicking on the ‘Review Status’ and view whether the review is still pending, modified, declined, or approved.
Also, you can add multiple applications and follow the same process for each selected application.
Zluri also provides the owner access to a snapshot view of the entire certification process status. Also, they can get an overview of the pending reviews and monitor the status of each app’s review status, including their assigned reviewers and completion status.
You can even send reviewers reminders who are yet to complete their reviews.
Further, to streamline the process for reviewers, Zluri provides reviewers with all the user access data in a single screen, i.e., the reviewer screen. For the same screen, reviewers can approve, modify, and decline access by verifying the data, and also they have to add relevant comments on the same.
Now, you will be able to view the entire status of the review process on the chart, and once the process is completed and the owner (assigned reviewer of the certification process) is fine with the review. You can click on conclude, and it will straight away send the reports to the reviewers' email.
Zluri is not restricted to these only, It offers additional capabilities like integration and reporting features. Zluri’s integration features are quite beneficial when gathering access data. Though Zluri already has data within its platform, but integration allows it to gather even more valuable insights. Leveraging these integrations further enhances your access review process and strengthens the organization's overall security posture.
Additionally, Zluri generates reports that are commonly associated with audit logs or audit trails. These audit reports serve as valuable documentation to share with auditors or keep as a reference for future reviews. And audit trails act as roadmaps, showcasing the changes made during previous reviews.
Now you know how Zluri can be the perfect IGA solution to mitigate the cornering access management challenges. So why wait any longer? Book a demo now and witness how with Zluri, your IT team can govern, manage, and control access by ensuring that service accounts have the right access aligned with their roles and responsibilities, mitigating potential security risks.









.svg)



.svg)
.svg)
.svg)
.svg)

.svg)

.svg)

.svg)
















.webp)







.webp)
.webp)





.webp)