Service accounts are meant to operate without the intervention of humans, as they are used by systems and software. Meanwhile, user accounts are particularly assigned to individual users, enabling them to access SaaS apps and data and perform IT tasks within the system.
To help you understand better, let's take a look at this example; you have a computer system with various services and human users. In this situation, a service account serves as an identity for a system service.
It is given a descriptive name like "NetworkService" or sometimes no name at all. By naming the accounts, it helps to distinguish the services running on machines from the individuals who use them.
On the other hand, user accounts are specifically assigned to people and are associated with human names such as "John Smith." These accounts represent the identity of individual users and enable them to access the system and its resources.
Wistia_ID: xdyx0ms4d9
This was just a brief distinction, so let's move further to learn in detail about each account and how they differ.
Service Accounts Vs User Accounts: What Sets Them Apart
Below we've outlined detailed comparision table for service accounts vs user accountsand highlighted the key factors that distinguish them. This will help you gain a clearer insight into the unique characteristics of each account.
Now, let's see in detail for service accounts vs user accounts comparison.
1. Definition & Account Types
- What are service accounts?
A service account is nothing but a non-human privileged account that is used by an operating system to run SaaS applications, virtual machine instances, automated services, and other background processes.
For example, just like humans, computers also need access to various resources like apps, databases, and files. Thus, service accounts provide a means to assign identity and permissions to computer programs or processes that perform specific tasks. Also, they have privileges that allow extensive access to system resources, either across a domain or locally.
- Types of service account
Given below are the types of service accounts:
- Service accounts in Linux and Unix
In Linux and Unix systems, service accounts are usually referred to as "init" or "inetd" accounts. These accounts are unique types of privileged accounts that work as non-human entities. They have the ability to execute apps, run automated services, manage virtual machine instances, and perform different other processes.
- Service accounts in the cloud
Cloud service accounts are also known as virtual service accounts or cloud compute service accounts. These accounts are designed to be used by apps or compute workloads rather than by individual users.
- Service accounts in Windows
As per Microsoft's definition, a service account is a user account particularly designed to provide a security context for services running on Windows Server operating systems. The security context plays an important role in determining the service's ability to access both local and network resources. Furthermore, these service accounts are frequently associated with mission-critical applications that need elevated privileges.
The most common types of service accounts in Windows are as follows:
- Domain user account
- Local user account
- NetworkService
- LocalSystem
- What are user accounts?
Meanwhile, a user account is a unique identity created for an individual in a computer or computing system. It can also be created for machine entities like service accounts for program execution, system accounts for managing system files and processes, and root and administrator accounts for system administration.
These privileged accounts possess additional privileges compared to normal user accounts. Other examples of such privileged accounts include service accounts, database accounts, root accounts, system accounts, and administrator accounts.
- Types of user accounts
Below are the types of user accounts:
1. Interactive account - a standard user account
The regular user account assigned to an individual is commonly referred to as an interactive account or a standard user account. These users typically have the ability to log in using a password and can run programs on the computer.
- Non-user account
The term "non-user account" is occasionally used to refer to all user accounts that are not considered standard user accounts.
Also Read: To know more about service accounts, you can go through Service accounts best practices, Service account management tools.
2. Importance Of Each Account
- Why are service accounts important?
Service accounts play a crucial role in supporting critical business programs and processes. They are particularly valuable for running persistent programs like websites and databases that need continuous operation.
Moreover, service accounts act as intermediaries, performing tasks on behalf of users. This helps protect sensitive data and system resources by preventing unauthorized users from accessing them directly.
Due to their extensive privileges and the need for widespread knowledge of their credentials, service accounts possess significant access capabilities. The main app and all associated programs that interact with them must recognize and authenticate them. However, these distinct characteristics also make service accounts appealing targets for hackers.
So you need to implement best practices to securely manage your service accounts and opt for tools that offer functionality that helps your IT team secure your service accounts from hackers.
- Why are user accounts important?
Whereas user accounts allow your IT team to control who can access specific information. For example, an employee in the accounting department may not have authorization to access HR records on the company network, and vice versa. User accounts ensure that only authorized individuals can view relevant data, maintaining confidentiality and privacy.
Furthermore, these accounts enable your employees to work on multiple computers within the organization. Whether they have a permanent workstation, use hot desks, or work remotely, user accounts allow seamless access to their personalized settings, files, and resources. This flexibility enhances productivity and convenience.
Additionally, by setting up user accounts, unauthorized access to computers or networks by visitors, tradespeople, or intruders can be prevented. User accounts act as a safeguard against potential security breaches, ensuring that only authorized individuals have access to your organization's SaaS apps and sensitive information.
3. Enhancing Security
- One of the best things about service accounts is that they can automate tasks and access resources without needing humans to do anything. This is really helpful for applications that need to keep running all the time or do things like monitoring, reporting, and processing data.
This further helps in enhancing security. Also help separate different roles and responsibilities, which lowers the chances of someone misusing or stealing credentials. Service accounts are usually only given the permissions they need for a specific job. By limiting their access to only what they need, the risk of someone gaining too much power and causing problems is minimized.
Also, service accounts help prevent mistakes when it comes to things like logging in, changing passwords, or resetting passwords. They make sure that these processes are done consistently and without any human errors.Apart from that, service accounts make auditing easier. Instead of being tied to individual users who might come and go, service accounts are linked to specific applications or systems. This makes it simpler to keep track of and review the activity logged by those accounts. - On the other hand, user accounts often have more privileges than they really need, which can make it easier for mistakes or data breaches to happen. However, since user accounts are tied to specific individuals, your IT team can identify who is accountable for accessing particular apps and data.
Hence, each user is responsible for their actions and can be held directly accountable for any security breaches or unauthorized access. This helps in identifying the source of any potential security issues more easily.
Also, in cases where an individual leaves the organization or no longer requires access, user accounts can be easily deactivated or removed, instantly revoking their access privileges. This ensures that former employees or contractors can no longer enter sensitive resources, reducing the risk of unauthorized access.
Now that you have gained an understanding of the difference between service accounts and user accounts. You also need to understand that one thing is common between the two: your IT team has to manage the access permissions for both. For this, you need to consider opting for a platform. Though there are multiple platforms available, the one that stands out is Zluri, which is designed to streamline your access management process. So, here's a quick overview of what Zluri has to offer.
Zluri: Your One-Stop Solution To Streamline Access Management & Governance
IT teams often struggle a lot while managing both service accounts and user accounts due to the absence of a proper solution. For example, most of the IGA solutions are unable to provide proper visibility into these accounts' access data and activities.
Furthermore, another concern is since both types of accounts are used to access organizational resources, ensuring data safety and security requires effective and efficient management by the IT team.
So, to address this challenge, Zluri, the modern IGA platform, emerges as the ultimate solution. It seamlessly manages service accounts and user accounts, providing control over their access to various applications and ensuring timely governance.
Zluri achieves this by offering a wide range of capabilities designed to provide complete visibility into which accounts access which applications, automate the process of granting, modifying, and revoking access, as well as automate the access review process. Let's explore these capabilities in detail to gain a deeper understanding.
1. Unveil All The Service & User Accounts With Zluri’s Data Discovery Engine
Zluri helps your IT team to analyze and discover all the service accounts and user accounts seamlessly with its nine discovery methods, i.e., MDMs, IDPs & SSO, direct integration with apps, finance & expense management systems, CASBs, HRMS, directories, desktop agents (optional), and browser extension (optional). With the help of these methods, your team can find who has access to accounts, what permission is granted to them, whether the employee accessing the account falls under critical users, and more.
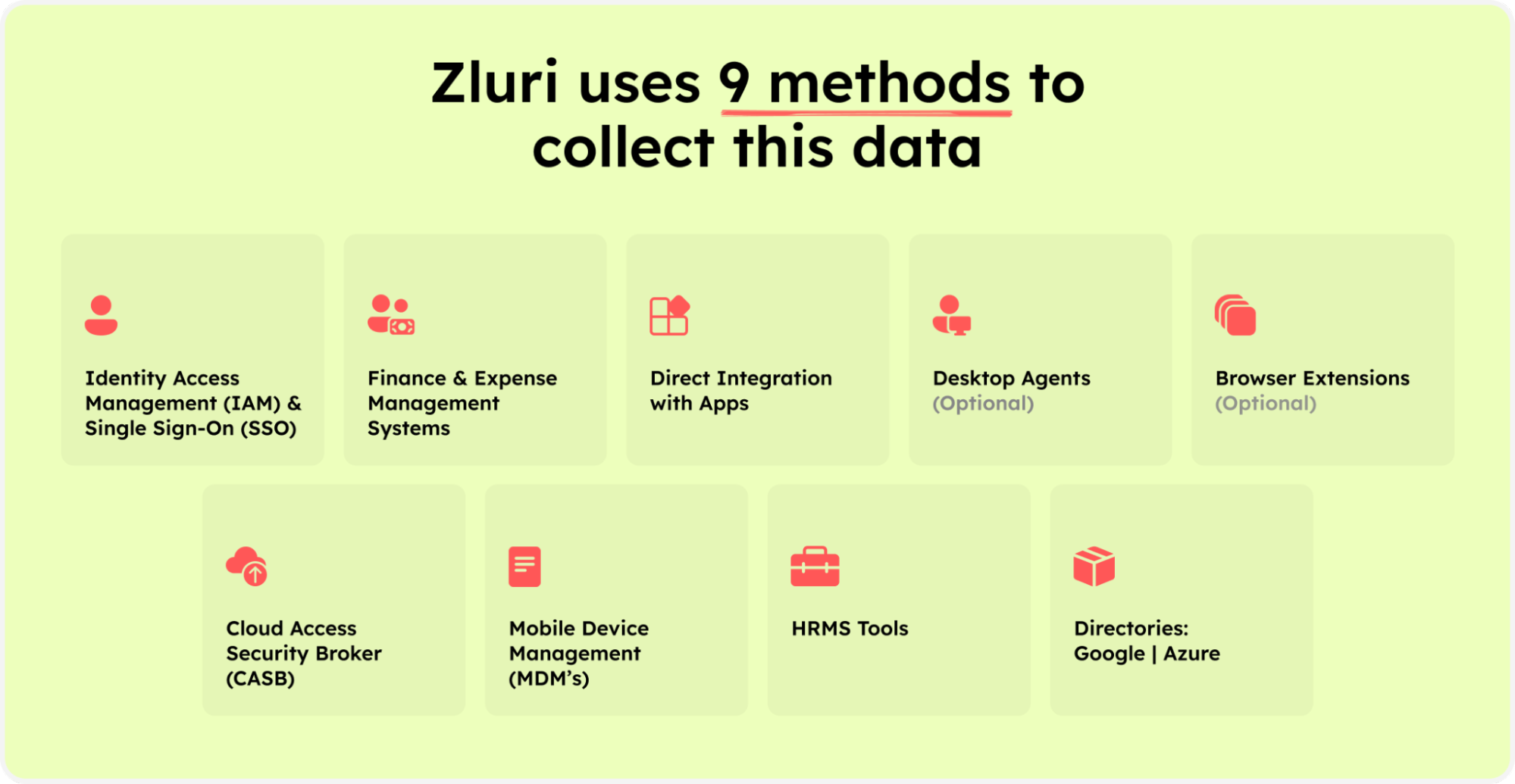
Zluri’s nine discovery methods
Further, it helps your IT team promptly identify the most alarming aspects and generate a personalized report highlighting the risks. This report can be downloaded and shared by your IT team to take proactive measures and enhance the security of your service accounts. It serves as an excellent initial step towards uncovering and safeguarding your service accounts.
Furthermore, it automates the identification of unmanaged and unfamiliar accounts. This automation alleviates the manual workload of documenting, categorizing, and cataloging service accounts, leading to substantial time and resource savings.
In addition, Zluri also offers the capability to manage employee access, including those who serve as owners of service accounts. Through Zluri, your IT team can simplify access management, ensuring that the right employees have the appropriate permissions for service accounts. By offering a comprehensive solution for both service account management and employee access control, Zluri empowers your IT team to uphold a strong and secure environment.
How does it make it all possible? It offers advanced identity governance and administration capabilities such as user lifecycle management, access request management, access certification, and more. Let’s learn more about it in detail.
2. Automate Access Management Process With Zluri’s Automation Engine
Zluri enables your IT team to efficiently manage employees (who act as an owner of service and user accounts) or the regular employees' access throughout their entire tenure with the organization with its automated and intelligent user lifecycle management platform. It simplifies access provisioning, streamlines access modifications for changing requirements, and automates access revocation when needed.
Let's explore how Zluri streamlines and automates the access management process.
- Effortlessly Manage Provisioning & Deprovisioning
Zluri automates the entire process, freeing your IT team from the repetitive cycle of managing access permissions. Your team no longer needs to waste time manually provisioning and deprovisioning; with Zluri, your team can automate these processes. Ensuring the right level of access is granted to authorized employees to required SaaS apps and data at the right time while reducing the risk of human errors and over-provisioning.
How does Zluri do that? Well, your IT team can create and customize onboarding and offboarding workflow. By creating these workflows, your team can securely grant SaaS apps and data access to multiple new joined simultaneously with just a few clicks per their job entitlement (role, position, and department) and revoke access when the employee’s tenure gets over. This helps boost your team’s efficiency, increases employee productivity, and maintains a secure environment for your users ’ identities and SaaS app data.
Not only that, as per Kuppingercole's research and analysis Zluri’s automated onboarding/offboarding also saves hours and hours of manual effort invested by IT teams.
So now the ultimate question is how to create these workflows.
Your IT team can easily create an onboarding workflow by following the given below steps:
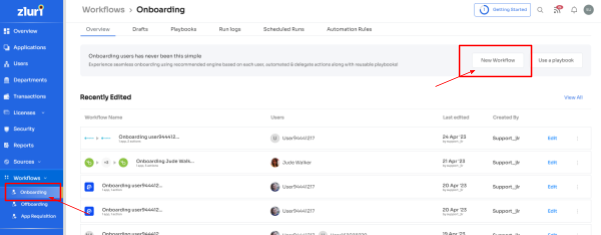
- Step 1: From Zluri's main interface, click on the workflow module and select the onboarding option from the drop-down list. Proceed by clicking on New Workflow.
- Step 2: Select the user for the onboarding box will appear; from there, select the employee(s) whom you want to onboard. Also, you can search for a particular employee in the search bar. Once you are done selecting the employee, click on continue.
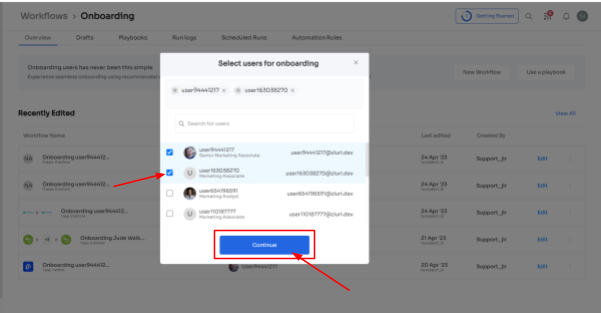
Note: You can even select multiple employees; this helps onboard multiple new employees in one go
- Step 3: With its intelligent feature, Zluri would suggest some apps under recommended apps based on the employee's department, role, and seniority. Choose any of those, then execute the required action for the selected applications.
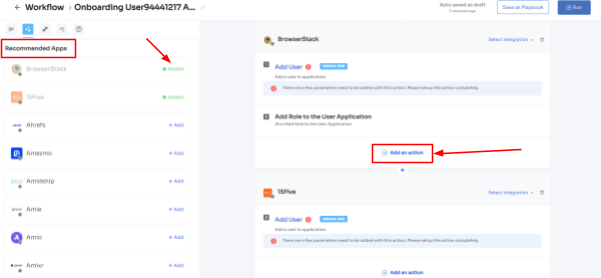
- Step 4: To execute certain actions, you need to click on Edit Task and enter the required details. Your team can schedule the actions to execute the workflow on the day of onboarding. In order to save the actions, click on Save Task, and the actions will automatically be saved.
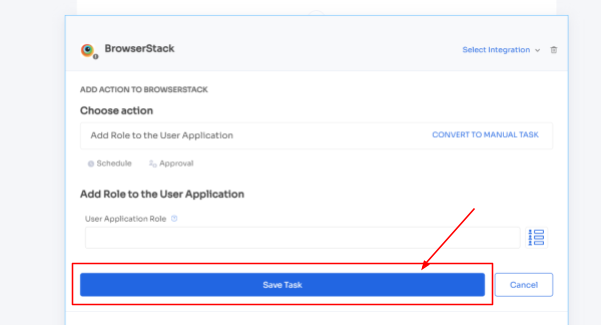
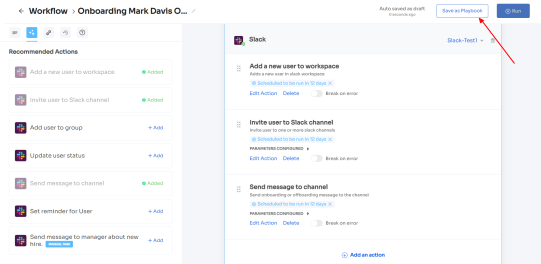
Also, your team can add your employees to channels or send an automated welcome greeting using Zluri's in-app suggestions. The actions can vary for different applications and are mentioned under recommended actions.
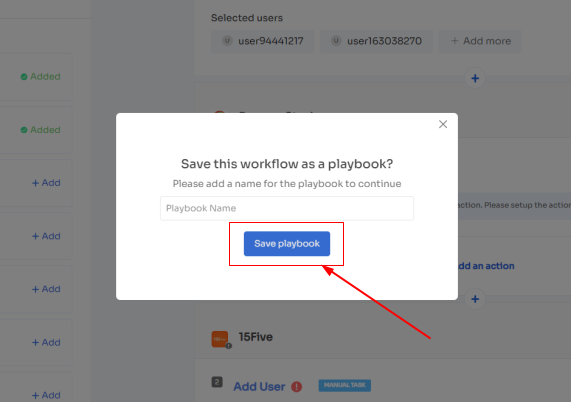
- Step 5: Finally, click on Save as Playbook to save the workflow. Then, you'll get a dialogue box with instructions to name the playbook. Add a name, proceed further by clicking on Save Playbook, and the onboarding workflow is ready.
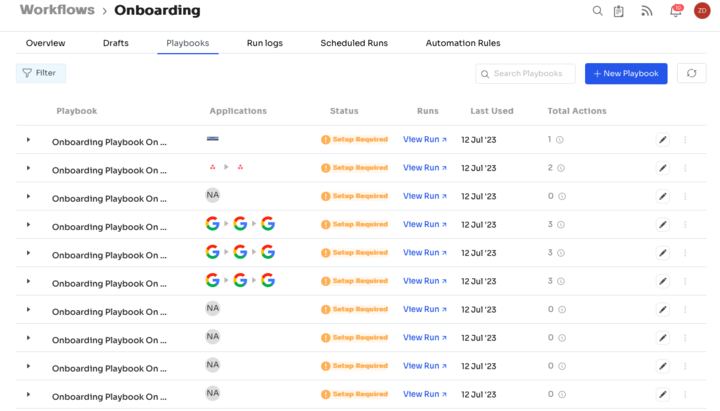
For added efficiency, Zluri offers automated playbooks (i.e. collections of recommended applications for automation) that can be customized for different roles, departments, and designations. This feature streamlines the onboarding of new employees, making it as easy as a few clicks to set up their access.
Note- Apart from that, your team can set automation actions, such as by triggering if and but conditions, they can grant Kissflow access to all the employees of the finance department.
Now let’s see the steps to create an offboarding workflow:
- Step 1: From Zluri's main interface, click on the workflow module and select the offboarding option from the drop-down list. Proceed by clicking on New Workflow.
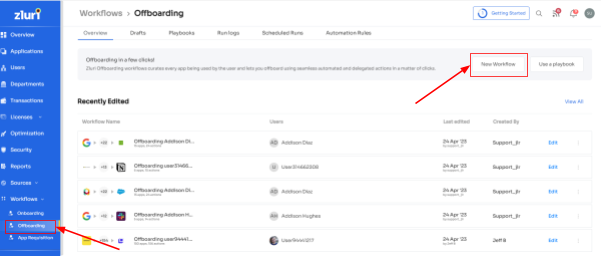
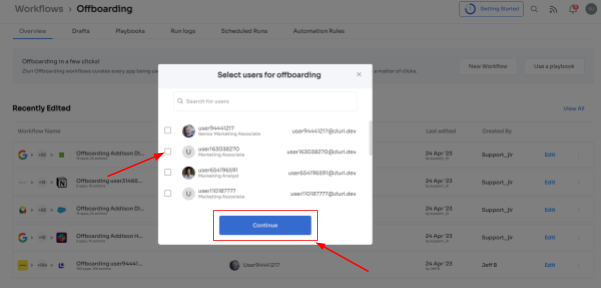
- Step 2: A popup labeled 'Select the user for offboarding' will appear. Select the employee(s) you want to offboard, or you can look for them in the 'search box. Click on continue after selecting the employee.
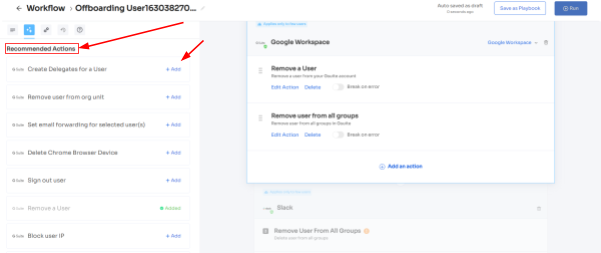
- Step 3: Your team will be able to view all the applications your employee can access. Now when you click on the app, Zluri will display some suggested actions under recommended actions. Select any of those or multiple actions, and then execute the required action for your chosen applications.
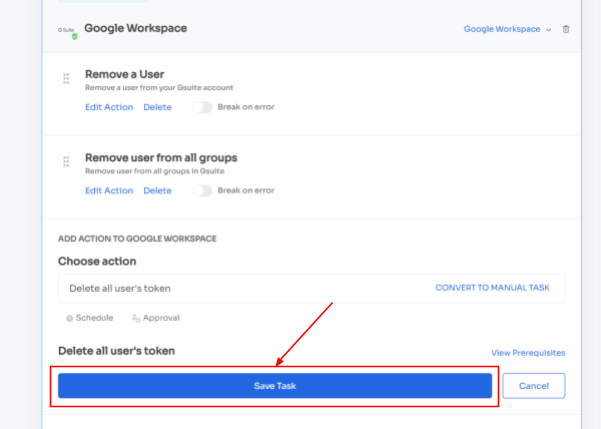
- Step 4: To add other actions, click Add an Action, fill in the required details, and proceed by clicking on Save Task; the actions will be saved.
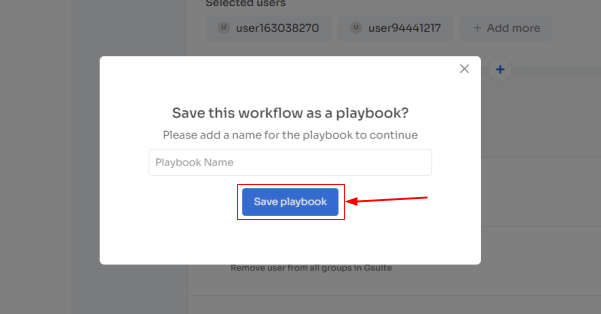
- Step 5: Save the workflow by clicking Save as Playbook. A dialogue box will appear, instructing to name the playbook.
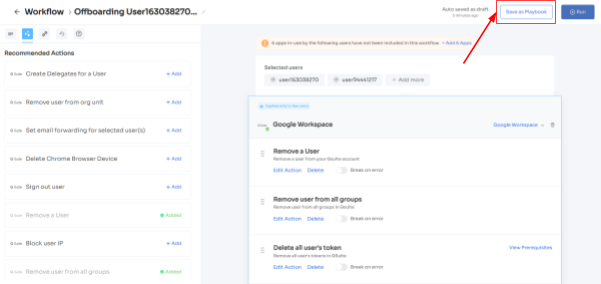
Add a name, click Save Playbook, and the offboarding workflow is ready.
- Ticketless Access Request Management
That’s not all; it simplifies the access request and approval process by offering your employee an App Catalog & Access Request, a self-serve model, a collection of SaaS applications approved and verified by IT admins. This empowers employees with the flexibility to choose from the EAS and gain quick access to their required applications.

But you might be wondering how your team can stay informed about changes in employee roles. Zluri offers a convenient solution to address this concern. Through seamless integration with your organization's HR system, Zluri automatically retrieves and displays updated employee data on a centralized dashboard.
By leveraging this integration, your IT team can easily access and verify employee details without manual effort. This streamlined process ensures access permissions align with current employee roles and responsibilities. Whether granting or removing access, your team can efficiently manage user privileges based on the most up-to-date information available.

This improves your IT team’s productivity and enhances your employee’s overall experience.
Now let’s see how your employees can raise an access request in EAS:
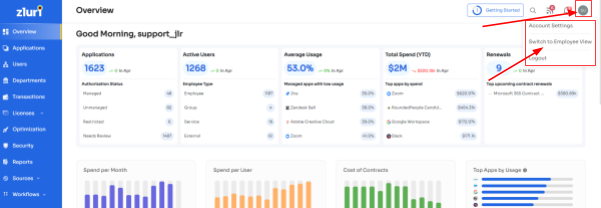
- Step 1: Your employees will receive an icon on the Zluri main interface's upper right corner; click on that, and a drop-down menu will appear; From there, click Switch to Employee View.
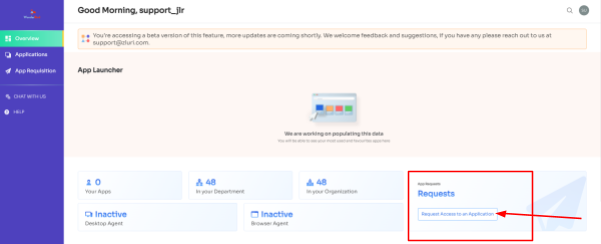
- Step 2: Overview dashboard will appear by default; now click on 'Request Access to an Application
- Step 3: Your employees will see a dialogue box where they need to enter the application name they require access to. Then, click on Continue.
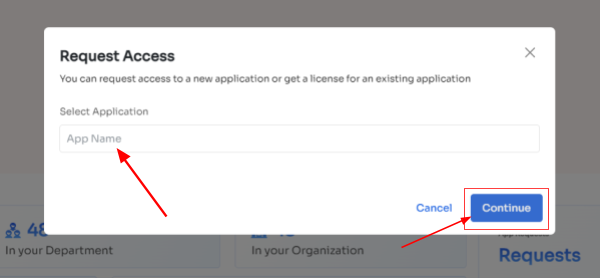
- Step 4: Some applications will not be used in the organization. However, your employees can still request that application. Click on continue, and another dialogue box will appear, showing similar applications that are being used in the organization.
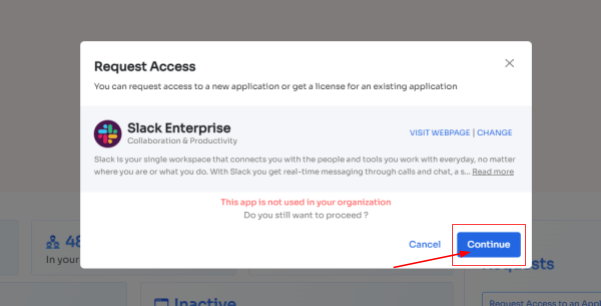
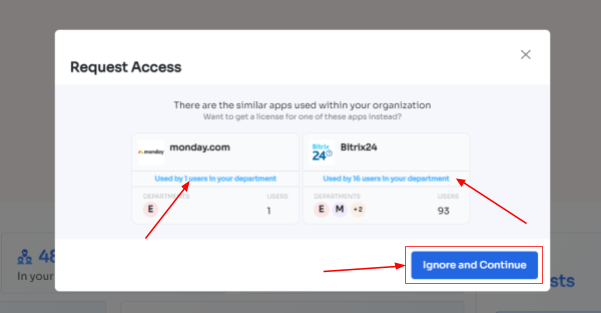
- If your employees want to opt for a similar application, they can simply click on the application or click on Ignore and Continue to proceed forward with your request.
- Step 5: Further, they have to fill in the required details like selecting the license plan, subscription duration, and description of why they need the application and attach supporting documents. Once filled, click on Confirm request.
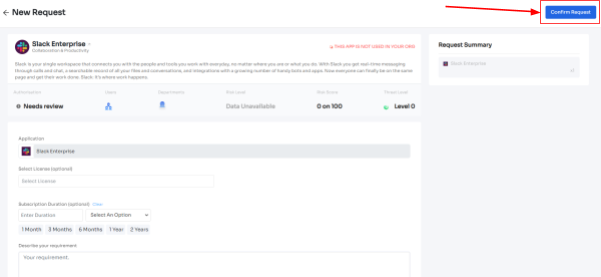
Note: Additionally, if the request has been modified in any way or if one of the approvers suggests any substitutes for the application, your employee can check it in the "Changelogs."

And that's it. The app access request has been submitted.
Now how to monitor these access management processes effectively? Zluri has a solution for that as well. With Zluri, your IT team can easily monitor which employees have access to different apps, what level of permission they have, and if any access has been taken away. All this information is available in one easy-to-use dashboard.
Moreover, Zluri helps your IT team spot any suspicious behavior from users. It can detect when someone tries to access something they shouldn't or if they're doing something unusual. When this happens, Zluri sends an alert to your IT team so they can take quick action to prevent any security risks.
By being able to quickly identify and respond to these incidents, your team can improve the overall security of your organization. It helps protect important data in your software apps from being breached or compromised.
3. Be Audit Ready By Streamlining Access Certification
The next critical step in access management is conducting access reviews, ensuring that each user has the appropriate level of access to applications and data to maintain data security. However, manual access reviews can be time-consuming and inefficient, as IT teams need to collect user lists, user statuses, access patterns, and all the applications to which users have access.
To streamline the access review process, Zluri provides access review capabilities that automate and structure the access certification process. This enables your IT team to efficiently review and validate user entitlements, ensuring that access privileges are regularly audited, unauthorized access is detected, and compliance requirements are met.
However, Zluri offers more than access review capabilities. It provides exclusive features that set it apart from competitors. Let's explore these features one by one.
- Unified Access Review
Zluri's unified access review capabilities enable your IT team to find out which users have access to all SaaS apps and data. It gathers these valuable insights from its centralized access directory, where all user access-related data is stored.
With these insights in hand, including user roles (admins or regular users), department information, and more, your IT team can thoroughly review access privileges and ensure each user's access aligns with their role and responsibilities.
Additionally, to keep track and maintain the flow of work, Zluri’s activity & alert capabilities come into play. This feature provides real-time insights on the last activities users performed and notifies IT teams about any new logins. With the help of these insights, reviewers can make informed decisions while reviewing access, ensuring the right people have the right access at all times.
- Automated Access Review
Previously, the IT team used spreadsheets, JSONs, and more, to gather data such as users list, which user has all access permissions, and more. Further, these insights are used for the manual access review process. However, this way of reviewing access was prone to error and not accurate.
So what Zluri did is, it simplified the access reviews process by automating it. All your IT team needs to do is just log in to Zluri, create a certification, and choose the apps and users you wish to review. From there, the reviewers will conduct the review and update you on the results via email.
By automating this process, you can achieve results that are 10 times better than manual methods and save your IT team's efforts by 70%. Let's explore how this automation works in detail.
- After accessing contextual data through Zluri's unified access feature, your team can take it a step further by establishing access rules based on these insights. For instance, if an individual holds an admin role on Salesforce, you can effortlessly create a review policy designed specifically for that situation.
- Following that, the schedule certification feature comes into play, enabling your team to generate certifications based on the gathered information. This empowers you to take actions aligned with the insights you've obtained.
For instance, you can utilize data such as last login, departments, user status (active or inactive), and more to make well-informed decisions during the review process. These decisions may include determining whether the user's current access should be maintained or if any modifications are required.
With Zluri's context-rich information, your team can confidently take actions that align with your access management policies. This intelligent and efficient approach ensures that the right users have the appropriate access, all while maintaining data security.
- Secure access orchestration/auto-remediation
After completing the access review, necessary changes will take place as per the set actions during certification creation, so all these actions, like access modification or removal, are part of secure access orchestration. It's the seamless process that ensures access is managed securely and efficiently, safeguarding your organization's data and resources.
For example, while creating a new certification in Zluri, your team will come across configuration action under which they need to create deprovisioning playbooks and modification playbooks. If the reviewers decline the access permissions, then automatically, the deprovisioning playbook will run, and the same goes for the modification playbook. Also, for both scenarios, the reviewers need to provide relevant reasons stating why the access permission is declined or modified.
Point-to-note actions will take place automatically after the review; that's why this process is also known as the auto-remediation process.
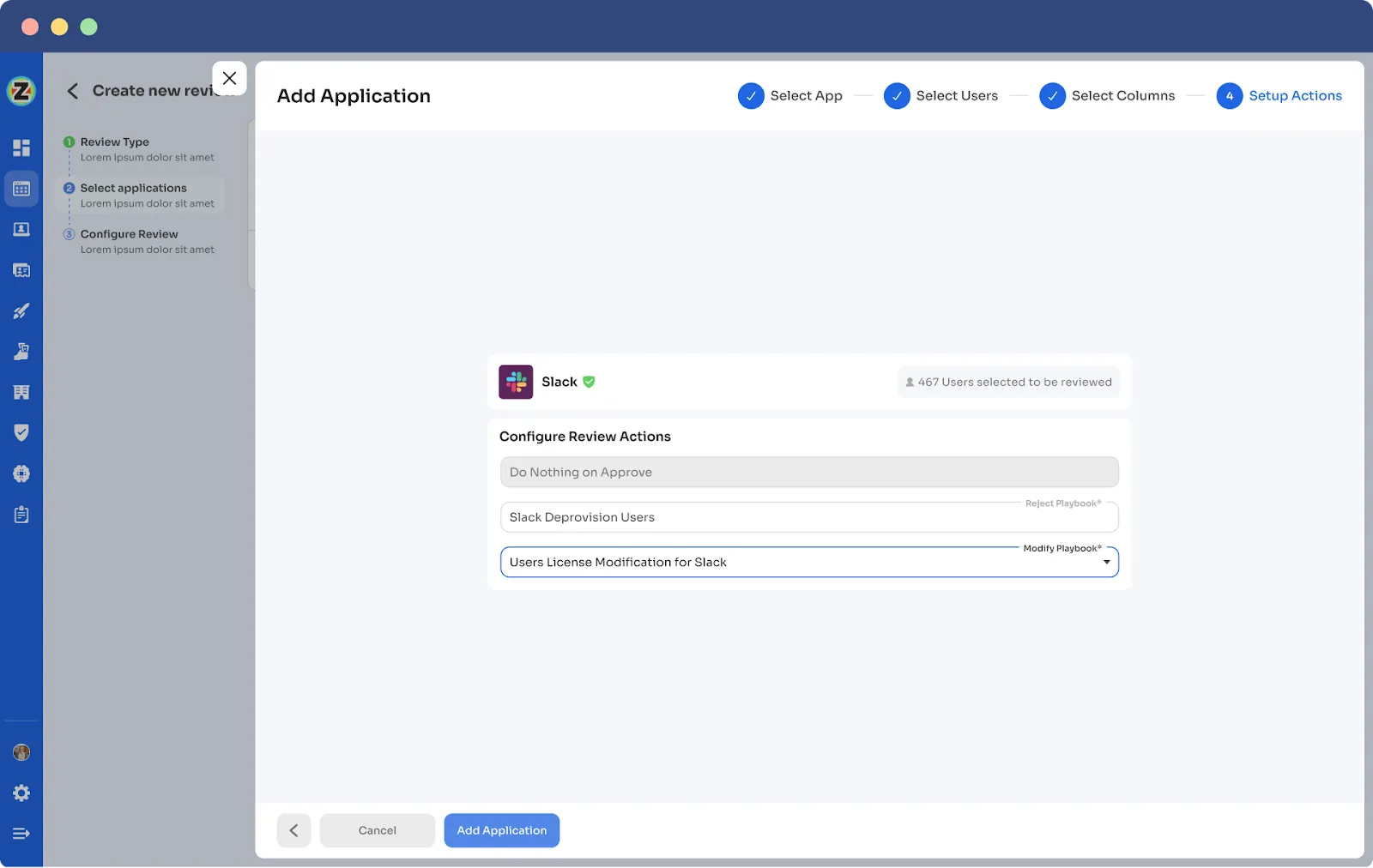
Furthermore, Zluri also offers integration features that are quite beneficial at the time of gathering access data. By leveraging these integrations, Zluri enhances the access review process and improves the organization's overall security posture.
For instance, when reviewing critical components like the Identity System and core applications, Zluri seamlessly integrates with platforms such as Salesforce, Okta, Azure, and others. These integrations are vital in gathering crucial data from the identity system and SaaS apps, providing valuable insights, and streamlining the review process.
Also, Zluri generates reports commonly associated with audit logs or audit trails. These audit reports serve as valuable documentation to share with auditors or keep as a reference for future reviews. And audit trails act as roadmaps, showcasing the changes made during previous reviews.
For instance, if an employee's access level was downgraded from admin to user, it becomes crucial to review and ensure that the access remains appropriate or if there were any subsequent changes back to admin. Understanding the reasons behind such upgrades is essential for maintaining proper access control.
So, don't wait any longer! Book a demo now and see for yourself how Zluri can help your IT team effortlessly manage access.









.svg)



.svg)
.svg)
.svg)
.svg)

.svg)

.svg)

.svg)
















.webp)







.webp)
.webp)





.webp)