Secure web gateway (SWG) and cloud access security broker (CASB) are crucial for protecting digital assets, each with unique functions. Their roles in cybersecurity differ, so IT teams must compare them to find the best fit for their security needs.
As technology advances, giving rise to evolving security threats, the imperative arises to choose a highly effective solution for safeguarding vital SaaS app data. Yet, it's essential to carefully assess which option aligns best with your organization's specific needs.
Take, for example, the option of implementing SWGs to fortify your network, users, and devices against various web-based threats, including malware and phishing attacks. On the other hand, if your objective is to shield cloud applications and revoke unauthorized access, CASB may be your preferred choice.
It's not advisable to rely solely on one criterion when determining the optimal security solution. There are other pivotal factors to consider. So, in this article, we will discuss different parameters and compare each solution’s unique capabilities, which will help you understand which solution will enable your IT team to prevent security risks more efficiently.
Before diving into the SWG vs CASB comparison, let's first delve into a detailed understanding of these security solutions individually.
Secure Web Gateway (SWG): A Quick Overview
A secure web gateway (SWG) is a network security solution that can be implemented on-premises or via the cloud. It acts as a robust defense system by enforcing organizational policies and meticulously scrutinizing outbound internet traffic. The primary objective of an SWG is to shield an organization from the ever-present online security risks and malicious content lurking on the web.
Operating as a protective barrier between users and the internet, SWGs employ advanced security measures to scrutinize web requests and ensure compliance with corporate policies. This ensures that potentially harmful programs and websites are flagged and prevented from being accessed by corporate devices. A comprehensive SWG solution integrates a range of critical security functions, including:
- Data Loss Prevention (DLP): SWGs help prevent the unauthorized transmission of sensitive data, guarding against data leaks and breaches.
- URL Filtering: By categorizing and controlling website access, SWGs enable organizations to restrict or permit access to specific categories of websites, enhancing security and productivity.
- Antivirus Protection: SWGs incorporate real-time antivirus scanning to detect and block malicious files and downloads, reducing the risk of malware infections.
- Application Control: They offer the ability to manage and control the use of various applications and services, ensuring that only approved applications are accessed.
- HTTPS Inspection: SWGs inspect and analyze secure (HTTPS) web traffic to identify hidden threats and vulnerabilities, providing an additional layer of security.
By integrating these security functions, a secure web gateway serves as a multifaceted defense system, safeguarding organizations against various web-based threats and ensuring that web traffic adheres to corporate security policies.
Cloud Access Security Broker (CASB): A Quick Overview
CASB (Cloud Access Security Broker) solutions offer deployment flexibility either as an on-premises appliance or as a cloud-based service. Their primary function is to serve as a gateway between cloud service providers and their customers, playing a pivotal role in enforcing corporate security policies and reducing risk while ensuring regulatory compliance for access requests to cloud-based data.
The range of features provided by CASB solutions is diverse and comprehensive. Among the fundamental functions within a CASB solution, a few of them are:
- Authentication: CASBs enhance security by implementing robust authentication mechanisms and verifying the identity of users attempting to access cloud resources. This helps ensure that only authorized individuals gain access to sensitive data.
- Single Sign-On (SSO): Single sign-on capabilities simplify user access by allowing them to use a single set of credentials to access multiple cloud services. This not only improves user convenience but also enhances security by minimizing the risk associated with multiple passwords.
- Credential Mapping: CASBs facilitate detecting both authorized and unauthorized usage of cloud resources by mapping and monitoring user credentials. This helps in identifying potential security breaches and ensuring that cloud access adheres to established policies.
CASB software solutions are versatile and may encompass functionalities commonly found in Secure Web Gateways (SWG). These can include:
- Malware Detection and Prevention: CASBs incorporate mechanisms for detecting and preventing malware within cloud services, reducing the risk of infection and data compromise.
- Data Loss Prevention (DLP): DLP capabilities in CASB solutions enable organizations to monitor and control the movement of sensitive data within the cloud, helping prevent data leaks and breaches.
By offering these features, CASBs empower organizations to effectively manage and secure their interactions with cloud service providers, ensuring that data and resources in the cloud are accessed consistently with corporate policies and security standards.
SWG vs CASB: Which Is The Perfect Fit for Your Security Requirements?
Several security solution options are available in the growing market, out of which you have to choose the more apt one. Both SWG and CASB are formidable security solutions but possess unique strengths and focuses. This SWG vs CASB section dissects the intricacies of SWG and CASB, enabling you to discern which aligns best with your organizational requirements, ultimately securing your digital landscape with precision.
SWG and CASB are popular cloud-based proxies, intermediary servers that act as gateways between the users and the internet, helping your IT team safeguard SaaS app data against cyber threats. They act as a better replacement for firewalls used for network security and protecting data.
However, they have very different use cases. The optimal selection between SWG and CASB primarily depends on your organization's individual requirements, infrastructure, and risk environment. To make it easier to decide which one will be the perfect fit. Here's a quick comparison between the two.
1. Unique Features To Deal With Security Threats
- SWG features include URL filtering, malware detection, content inspection, and encryption. URL filtering blocks access to web-based resources known to be malicious or inappropriate. At the same time, malware detection helps identify and prevent downloading harmful SaaS applications from the internet.
Furthermore, content inspection monitors web traffic and blocks access to sensitive data. At last, encryption helps to protect crucial data in transit and prevent data theft. - On the other hand, CASB includes cloud discovery, access control, data protection, threat detection, and compliance reporting. It Identifies all SaaS applications and services being used within an organization and enforces authentication and authorization policies for accessing SaaS apps and cloud resources.
Furthermore, it protects crucial data by encrypting and/or tokenizing sensitive data before it is uploaded to the cloud. Also detects threats by monitoring data leakage and other suspicious activities within the cloud environment.
It also provides reports on cloud usage and security to help your IT team comply with regulatory requirements.
2. Pros and Cons
Pros of SWG
- The benefit of SWG is that it allows screening and filtering of the web content before it reaches your organization's systems. The internet is full of cyber risks, and SWG has changed its deployment location from on-premises appliances to cloud-based SWG services rather than their core functions.
Cons of SWG
- SWG requires traffic to transit through to start the protection. This security solution may be deployed as a standalone solution with all traffic routed through it or be essential to a secure access service edge solution.
Pros of CASB
- Meanwhile, CASB solutions are designed to interact with cloud service providers' application programming interfaces. When these APIs are available, they make CASBs work very effectively.
Cons of CASB
- A common limitation of CASB is that it must be integrated with other standalone security solutions to achieve a comprehensive security architecture. Dependency on other standalone solutions makes security management costly, complex, and less efficient.
3. Primary Usage
- SWG filters web traffic in real-time, blocking access to known malicious sites and preventing your employees from downloading malware. It uses antivirus and anti-malware software to detect and block malicious content that may be embedded in web traffic.
Furthermore, this solution monitors and controls data flow between your employee’s device and the internet, preventing sensitive data from being leaked or stolen. Also, restrict access to specific web applications or control how they are used, helping to prevent unauthorized access or misuse.
Apart from that, SWG can provide insights into user behavior and traffic patterns, helping your IT team identify potential threats and improve security policies. - Whereas CASB's primary use is to discover and control shadow IT. This solution provides visibility into the cloud services being used within your organization that help identify shadow IT. It also enforces policies to block or control access to these services.
Furthermore, with the help of data loss prevention (DLP) and encryption features, it allows your team to safeguard sensitive data in the cloud by monitoring data activity in SaaS apps.
Additionally, CASB helps your team identify which user's account is compromised, allowing them to take immediate action to guard against cloud-based threats. It detects and blocks risky behavior, such as login attempts from suspicious locations, to prevent unauthorized access to cloud applications.
4. Replacement Of Firewall
SWG and CASB are proxies, offer data and threat protection, and replace firewalls in cloud-based environments. But they serve as complements for two very different use cases.
- SWG is a direct replacement for a firewall, which means for the same use case, be it for network and perimeter protection, your IT admins can use either a firewall or cloud SWG. Cloud SWG is delivering network security services via the cloud.
- CASB comes into play for a different use case that makes the firewall obsolete. When an outside user tries to connect to a cloud app, that traffic is blocked by the corporate network, which leads to the rise of CASBs. CASB gains at the expense of the firewall by every % increase in the amount of off-network cloud traffic.
Using this comparison, you should now have a clearer understanding of the optimal choice for your organization's needs. To simplify, here's a quick reference table comparing SWG vs CASB.
Comparison Table: SWG vs CASB
Here's a simplified comparison table between SWG:Secure Web Gateway vs CASB (Cloud Access Security Broker) based on key features and functions:
Please note that the choice of CASB vs SWG depends on the specific needs and priorities of your organization. This table provides a basic overview, and you should conduct a detailed analysis to determine which solution aligns best with your security and compliance requirements.
After comparing SWG and CASB, you must have understood which security solution will be best for your IT team to prevent security threats. But what if you want a combination of both (i.e., SWG vs CASB)?
Can SWG & CASB Converge & Work Together?
Is it possible to collaborate the two: SWG vs CASB? The central aggregation point through which all traffic flows is the intersection of the SWG and CASB, be it to the web, SaaS, or cloud applications.
Where there is a potential risk, like data loss, downloading malware, and oversharing, your security teams can implement SWG because it provides visibility into all the traffic. With CASB, your team can enhance SWG's ability to manage traffic and enforce security policies. But here, CASB should simply remain an add-on to the SWG foundation.
CASB, added to SWG or proxy, gives an extra layer of security that helps your IT team determine whether traffic is malicious or risky. It also determines which traffic goes to which application and what policy is in place to dictate what is done with it.
When striving to protect your organization's digital assets, the evaluation of CASB vs SWG has shed light on the unique benefits and use cases that each solution brings to the table.
Now, it's up to you which solution you want, as your decision will make a difference to your enterprise's security system. However, before deciding, you can take a quick look at one more efficient tool, Zluri, which can strengthen your security system.
Zluri - A Modern Solution For SaaS App Security & Compliance
You must be wondering, what is Zluri? How will it strengthen your organization's security system? Zluri is an intelligent SaaS management platform that helps your IT team protect your organization’s SaaS apps and data by providing a range of security features to detect and respond to security threats in real time.

For instance, due to the increase in SaaS adoption, IT teams find it challenging to keep track of each app, device, and system manually, giving way to Shadow IT. This increases the threat to crucial data, as unidentified apps or devices are easy for hackers to barge in.
So, with Zluri’s 9 discovery methods, which are MDMs, IDPs & SSO, direct integration with apps, finance & expense management systems, CASBs, HRMS, directories, desktop agents (optional), and browser extension (optional), your IT team can discover all the SaaS applications used in your organization. Providing your team with complete visibility into your organization's SaaS stack which allows them to eliminate shadow IT.
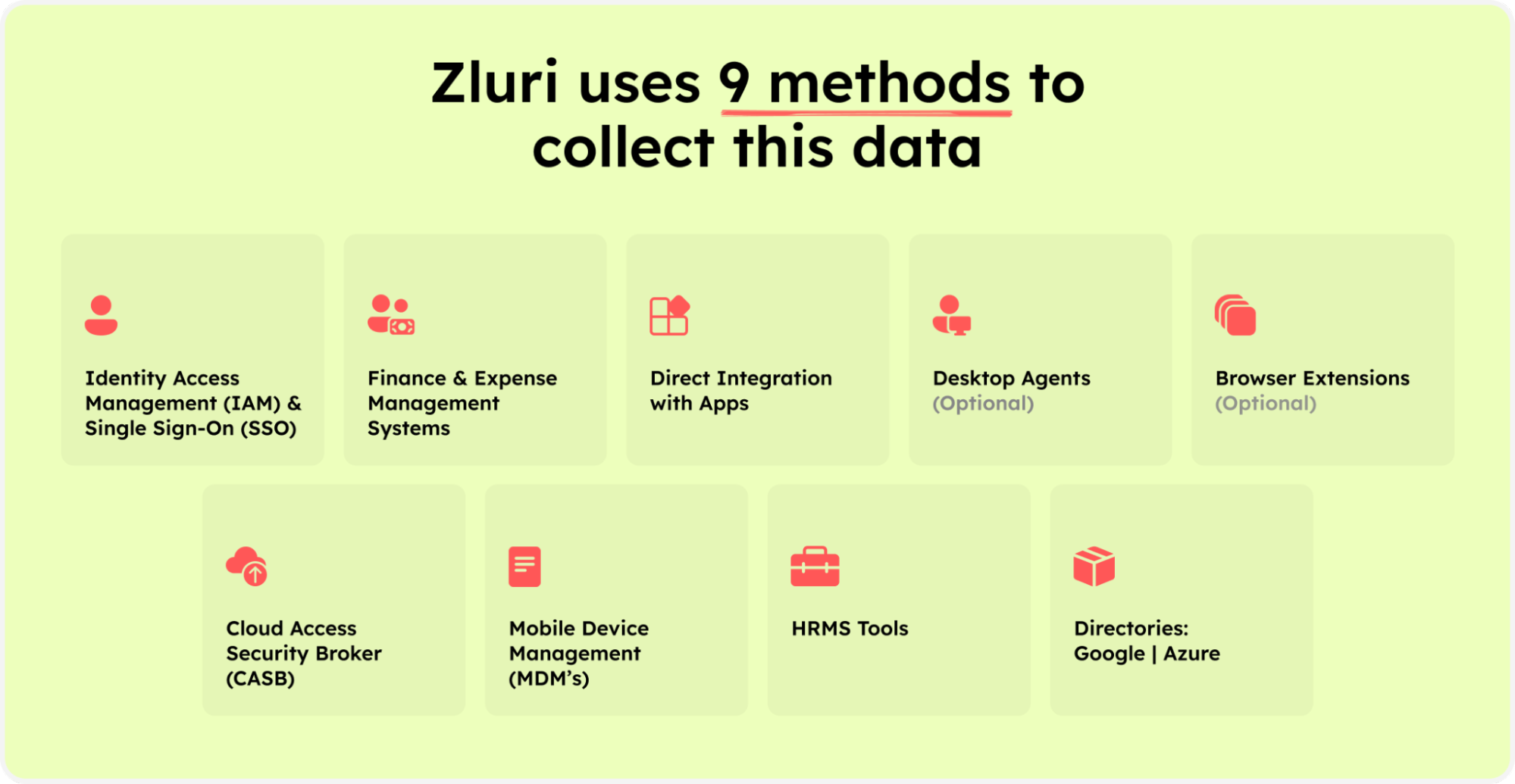
Zluri’s nine discovery methods
SaaS apps identification & categorization:
Zluri categorizes the SaaS apps under managed, which are approved by IT teams, unmanaged, which are unapproved, restricted, which are not allowed to use due to security reasons, and need review, all in a centralized dashboard. As per Kuppingercole's report, thisfeature helps your team keep track of each application, preventing security breaches.

Zluri doesn't stop here; once all the SaaS apps are identified, Zluri enables your IT team to inspect each application thoroughly, providing details related to events, shared data, compliance, and security probes. This will help your team meet compliance standards while also fulfilling security objectives.
From where will all these details be visible? Your team can follow these few steps.
- Step 1: On Zluri's main interface, click on applications; it will display all applications that are categorized under managed, unmanaged, restricted, and need reviews.

- Step 2: Click the application that your team wants more information about. All the related details will be displayed, including how many active users are using the app, the IT owner of the app, risk level, which departments are using the app, and more.

- Step 3: To get in-depth detail, click on the security & compliance tab; it will display 4 tabs events, data shared, compliance, and security probes.
Zluri's pivotal SaaS security features:-
- Events
By clicking on the events tab, your team can view all events related to the applications. Zluri fetches this information from multiple authentic online sources, including critical updates, data breaches, security vulnerabilities, and other news associated with the application.

The score will vary depending on the event's impact; if the event has a high-security impact, the score will be low, and vice versa. For instance, the score will be low due to X application's multiple security breaches.
- Data shared
Moving ahead, in data shared, your team can view who has read-only, modify, and delete access. If any user has read-only access, the threat level is comparatively low compared to users having to modify and delete access. Also, the more sensitive the data that an app accesses, the higher the threat level.

For example, an app with access to Google Drive and the ability to delete files would be considered a high threat.
- Compliance Tab
Moving forward, in the compliance tab, your team will be able to view which compliance standard the application adheres to. This lets your team ensure the application meets your company's compliance regulations.

Moreover, Zluri's risk scoring system considers the number of compliance standards that an app complies with is taken into account. The higher the number of compliance standards, the higher the score; the lower the number of compliance standards, the lower the score.
- Security Probes
Lastly, in the security probes tab, your team can get a view of technical scanning, which is conducted every once a month.

- Secure Encryption Algorithms
Not only this; it utilizes secure encryption algorithms; Zluri places a high priority on the protection of your crucial data. Additionally, it gives your team access to a thorough log of important activities that can be audited, allowing you to keep tabs on all actions that pertain to the security of your app.

Also, unless a request for removal is made, all collected data, including usage statistics for SaaS applications, is kept forever. Zluri backs up all data for 60 days and keeps it encrypted to ensure it is always accessible.
- Robust Reports Generation
Apart from that, it conducts timely audits and generates reports on employee activity, access permissions, app usage, unauthorized access, and more to detect threats or any suspicious activities. Such as, whenever an employee tries to access restricted apps, Zluri sends alerts to the IT team so that they can take immediate action if needed.

- Critical Apps & Critical Users
Furthermore, it also provides your team with a view of critical applications with high-risk scores and threat levels. It sends your team alerts immediately if your employee tries to access these critical applications, preventing data breaches.

Having gained insight into its functionality, Zluri is strategically positioned to safeguard vital data using its array of security features and capabilities, empowering organizations to fortify their SaaS security infrastructure.

Why wait any longer? You can try Zluri right away. So, schedule a demo today and determine whether it will be apt for your enterprise.









.svg)



.svg)
.svg)
.svg)
.svg)

.svg)

.svg)

.svg)
















.webp)







.webp)
.webp)





.webp)