Third-party access management is one of the biggest challenges that IT managers face. How can you ensure their access doesn't compromise security or compliance? Understanding every aspect of it will help protect your data while enabling smooth collaboration.
Third-party access management is becoming an increasingly pressing concern for organizations. While vendors, contractors, and partners will inevitably request access to IT systems, this can significantly increase security risks. Temporary access, while necessary, can, by default, expose the system to potential security gaps or non-compliance if not effectively managed.
Without oversight, third-party users quickly become a weak spot in your environment. Unauthorized access, accidental data leakage, or misuse of privileges might jeopardize security and confidentiality. This is an inevitable threat if more people are to engage with your company, and the complexity involved in determining who is allowed to have access to what for how long continues to rise.
Therefore, having third-party access management strategies or best practices in place can be beneficial. It will ensure that only the necessary data is accessed by the outside user—nothing more, nothing less. Strong policies and automation safeguard your IT systems while providing smooth collaboration.
Here, we will discuss the importance of third-party access management, its components and challenges, and best practices to implement in order to improve your organization’s security posture.
Importance of Managing Third Party Access
Third parties require access to your systems, data, or resources to carry out essential tasks. This access can expose security vulnerabilities, create compliance challenges, and raise privacy concerns. Let's explore why third-party access management is crucial for your organization.
Why Does It Matter for Security?
Third-party access exposes your systems to external threats. Hackers often exploit vendors or contractors with weaker security protocols to infiltrate larger organizations. Without strict controls, unauthorized users can exploit these vulnerabilities. Strong access management protects your data and systems from such risks by limiting access to what is necessary and monitoring all activities.
Why Is It Important for Protecting Privacy and Compliance?
Third-party access impacts more than just security—it also affects data privacy and compliance. Organizations are responsible for protecting sensitive information, as mandated by regulations such as the GDPR and HIPAA, among others. If a third party mishandles your data, your organization may face significant fines or reputational damage. Managing access ensures that third parties only deal with the data they need. It also helps prove compliance in audits or investigations.
However, third-party access management does not follow the same principle across industries. The challenges and risks vary significantly across different sectors. For instance:
- Healthcare: Patient data must always be kept private. Access unauthorized might result in breaches of data and associated legal implications.
- Manufacturing: In manufacturing, unauthorized access can disrupt operational flow by interfering with critical systems.
- Financial: Access control prevents fraud and unauthorized transactional activities.
Thus, having this risk knowledge will enable you to develop bespoke controls. This allows you to target the critical systems to guard the sensitive information most relevant in your industry.
Key Components of Third Party Access Management
Here are the main components of third party access management.
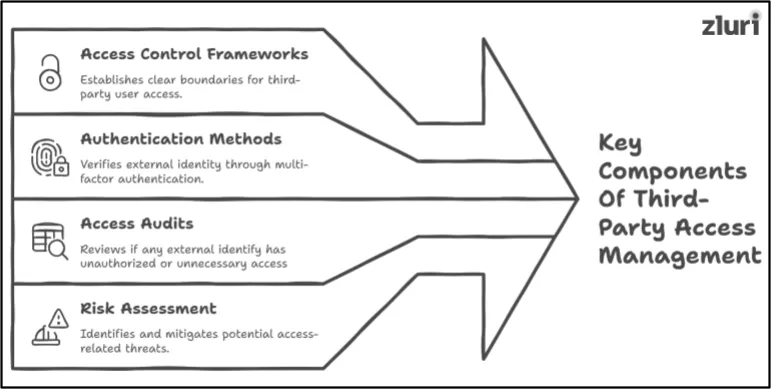
1. Access Control Frameworks
Access control frameworks define rules for granting and restricting access to resources. These frameworks enable you to establish clear boundaries for third-party users. They ensure that users gain access only to specific systems or data, based on their respective roles. The use of frameworks, such as role-based access control (RBAC), enables the minimization of unnecessary access, thereby preventing misuse and protecting critical assets.
2. Authentication Methods
Authentication methods verify the identity of third-party users. Strong techniques include multi-factor authentication, which enhances security. These methods require multiple credentials from users, such as a password and a code sent to their phone. They ensure that only authorized individuals gain access. Authentication is the first step in building trust with external partners.
3. Access Audits
Access audits are regularly conducted to review who has access to what. These audits identify any unauthorized or unnecessary access by third parties. They also ensure compliance with security policies and regulations. By conducting regular audits, you can quickly address potential issues. This improves overall access management and accountability.
4. Risk Assessment
Risk assessment evaluates potential threats associated with third-party access. It will enable your organization to identify vulnerabilities and prioritize mitigation efforts. For instance, some high-risk users require more controls and strictly limited access. Risk assessments ensure that access policies align with the organization's security needs.
Challenges of Third Party Access Management
Let’s explore the key challenges of third-party access management.
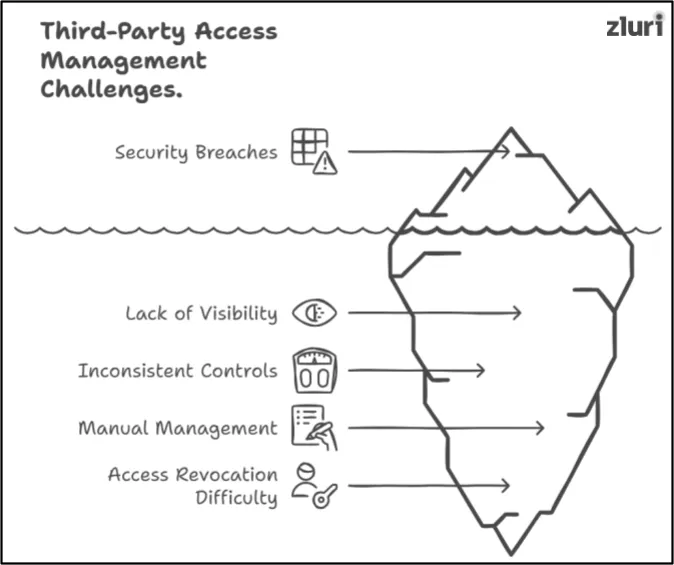
1. Lack of Visibility into third party Activities
One of the key challenges is limited visibility into what third party users are doing within your systems. Once access is granted, monitoring their activities becomes difficult without proper tools. You might often have no clear insight into what data is being accessed, modified, or shared. This blind spot can lead to unintentional errors or even deliberate misuse of privileges, creating vulnerabilities in the system.
2. Inconsistent Access Controls
Inconsistent access control practices are another common issue. Not all third parties need the same level of access, but implementing granular controls can be challenging. Without a standardized approach, some users may gain excessive privileges. This increases the risk of unauthorized access to sensitive data or critical systems, leaving your organization exposed to potential breaches.
3. Manual Management Leading to Errors
Manual means of third party access would pose a challenge to it since the process is long in terms of assigning permissions to users, tracking activities about the users, and how it may be revoked. These are all time-consuming and highly prone to human error, as one simple oversight might either result in unauthorized access or fail to revoke the given permission when it is no longer needed. Such mistakes in user activities are compliance violations.
4. Difficulty in Revoking Access Post-Projects or Contracts
Revoking access after a project ends or a contract is terminated is often overlooked. You may lose track of which third party users still have access to the network. This creates lingering security risks, as former vendors or contractors could retain unauthorized access to sensitive systems. The longer these permissions go unchecked, the greater the potential for misuse.
Overcoming these challenges requires a holistic approach. Your organization needs best practices to implement third party access management efficiently. By doing so, you can ensure that third party access is secure, efficient, and aligned with organizational policies.
Best Practices for Third Party Access Management
Now, let’s explore the best practices for overcoming the challenges of third-party access management.
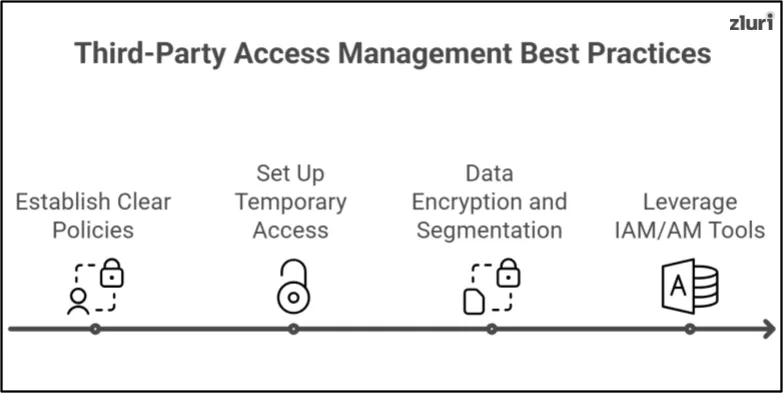
1. Establishing clear policies
Managing third-party access is a critical task for IT teams. To protect systems and data, clear policies must guide every step of the process. These policies should cover access requests, approvals, and revocation. Without proper rules, even small gaps can lead to significant security risks.
Start with access requests. What information should be included? Requests must specify who needs access, why they require it, and for what duration. This ensures only necessary access is granted. A defined process helps avoid confusion and speeds up the evaluation process.
Approval rules are just as important. Who is responsible for approving access? Ensure roles are clearly assigned and approval criteria are both simple and thorough. Sensitive systems may require multi-level approvals to implement additional checks. Always document approvals to maintain accountability.
How will access be revoked when no longer needed? Define timelines for access to expire automatically. Create rules to revoke access when a project ends or a third party's role changes. Regularly reviewing active access ensures no permissions are left unused.
What about urgent access needs? Establish a process for handling exceptions that ensures security is not compromised. Even temporary access should follow strict guidelines to prevent misuse. Policies should be easy for all parties to understand and follow.
2. Set up temporary access
Temporary access is a smart approach to managing third-party interactions. Most third parties within your organization may not require full-time access to your systems. By limiting their access to only the time they need, you can reduce risks and keep sensitive data safe. This practice adds an extra layer of control to your security measures.
Moreover, granting temporary access ensures that third parties have permissions only for a specific task or project. Once their work is done, their access should automatically expire. This prevents unauthorized use after their involvement ends. It also reduces the chances of forgotten or inactive accounts becoming a security threat.
Setting up temporary access also helps you monitor activity more effectively. When access is time-bound, it’s easier to track who is doing what and when. This visibility ensures accountability and helps detect any unusual behavior.
To make this work, use tools that support temporary access policies. Automating the process ensures consistency and minimizes human error. Clearly communicate the time limits to third parties so they understand their boundaries. This keeps the process smooth and avoids delays.
Furthermore, by adopting temporary access as a standard practice, you protect your data without complicating workflows. It’s a simple yet powerful way to ensure your systems remain secure while allowing third parties to do their job.
3. Data encryption and segmentation
Data encryption and segmentation are among the best practices for securely managing third-party access. Encryption will ensure that your organization's sensitive data stays protected, even if it’s intercepted. Only authorized parties with the correct decryption keys will be allowed to access the information. This will keep your data safe from breaches and unauthorized use.
Segmentation adds another layer of control. It separates systems and data into smaller, secure sections. Third parties can access only what they need, without exposing your entire environment. This minimizes the risk of accidental or intentional misuse of sensitive resources.
Together, encryption and segmentation provide better visibility and control. You can monitor who accesses specific segments and track how data is being used. This helps you identify any suspicious activity early and respond quickly.
By using these practices, you can confidently allow third-party access without compromising security. They create clear boundaries and reduce the impact of potential breaches. This makes managing third-party access safer and more efficient for your team.
4. Leverage IAM/AM tools
Automating third-party access management is crucial for maintaining security and efficiency. Manual processes can lead to errors, delays, and oversight, putting your systems at risk. To automate effectively, you need tools like identity and access management (IAM) or access management (AM). These tools simplify access control and reduce the chances of unauthorized activity.
IAM/AM tools will also help you manage access by enforcing strict policies. This ensures third parties get access only to the resources they need and only for as long as required. You can also automate approval workflows, monitor usage, and revoke permissions when necessary. This not only saves time but also strengthens your security posture.
If you're looking for a solution to simplify this process, Zluri will be a great fit. Zluri’s access management solution ensures seamless integration with over 300 SaaS apps, enabling you to track all your third-party access needs. The integration helps provide visibility into third-party access activities, enabling you to track third-party access and mitigate the potential impact of threats.
Furthermore, Zluri streamlines third-party access management with automated workflows and rigorous access controls. It ensures third parties only access what they need for a limited time. With real-time monitoring and secure deprovisioning options, Zluri protects your sensitive data. Its seamless processes make managing third-party access secure and efficient for your organization.
Also Read: If you want to explore various IAM tools, go through the Top 13 IAM Tools.
Strengthen Your Third Party Access Management to Enhance Security
Third-party access management is not just about security; it’s about building trust and ensuring seamless collaboration. A well-structured approach minimizes risks while enabling external partners to contribute effectively. Strong management practices create a balance between access and control, fostering a secure and productive environment.
By staying proactive and adapting to emerging challenges, you can maintain a robust defense against potential threats. Thoughtful strategies and reliable tools ensure your organization remains secure and efficient. Prioritize third-party access management as a critical part of your IT strategy to safeguard your organization’s future.
Also Read: If you’re interested in knowing about managing your vendor’s access, go through Vendor Access Management.
Frequently Asked Questions (FAQs)
1. What is third party access management?
Third party access management is the process of controlling and monitoring how external users interact with your IT systems. These external users often include vendors, contractors, or business partners who need access to perform specific tasks. This access is usually temporary and must be limited to only the resources they require.
2. What is third party remote access management?
Third party remote access management is a specific subset of access management. It focuses on controlling how external users connect to your systems remotely. This is especially important in today’s digital workplace, where many vendors work offsite.
3. What is a third party access management policy?
Third party access management policies require owners of natural monopoly infrastructure facilities to grant access to those facilities to parties other than their own customers, usual competitors, in the provision of the relevant services, on commercial terms comparable to those that would apply in a competitive market.
4. What is an example of privileged access management?
Privileged access management includes centralized credential management, multi-factor authentication, session recording, and automated auditing, all of which can secure privileged access for both on-premises and cloud environments.








.svg)














