As organizations integrate more cloud apps into their networks, security challenges grow. Cyber attackers can exploit these apps to access sensitive data and compromise systems. This blog provides essential insights on CASB security to help mitigate these risks effectively.
As enterprises accelerate cloud adoption, a pressing security challenge emerges - inadequate oversight and control over their data and cloud configurations. This vulnerability often arises from insufficient or absent Cloud Access Security Brokers (CASB), leaving sensitive corporate information susceptible to breaches.
Without effective CASB security measures, organizations risk critical data dispersing across multiple cloud services without sufficient protection. This can result in potential financial losses, damage to reputation, and legal repercussions.
In this blog, we explore the crucial role of CASB in enterprise security. If you're unsure about its function in an enterprise environment, rest assured—we'll walk you through it and more.
What is CASB Security Solution?
A Cloud Access Security Broker (CASB) is a security platform that acts as a control point between cloud service consumers and providers. Its primary role is to enforce enterprise security policies and protect sensitive data as organizations increasingly adopt cloud services. Further, it can identify and mitigate risks associated with cloud services, such as unauthorized access, data breaches, and compliance violations.
In short, CASBs play a crucial role in enhancing cloud security by providing visibility, risk management, data protection, and regulatory compliance across cloud environments. As organizations continue to adopt cloud services, CASBs serve as a vital component of their overall cybersecurity strategy.
What are the 4 Pillars of CASB Security?
.webp)
Below are the 4 foundational pillars of CASB security that contributes in securing your cloud environments:
1. Visibility
Visibility is crucial for organizations to effectively manage both managed and unmanaged cloud services. CASB solutions provide visibility into cloud usage patterns, allowing IT teams to understand who is accessing what data and applications. Instead of using a blanket approach of allowing or blocking all cloud services, CASB enables granular control. This means IT can approve beneficial cloud services while monitoring and governing access to activities and data within those services.
2. Compliance
Compliance is a significant concern when organizations migrate their data and systems to the cloud. CASB solutions help enterprises maintain compliance with industry regulations and internal policies. They provide features such as data encryption, access controls, and activity monitoring to safeguard personal and corporate data. By enforcing compliance measures, CASB solutions mitigate the risk of data breaches and regulatory penalties.
3. Data Security
Data security in the cloud relies on robust mechanisms like Data Loss Prevention (DLP). CASB security incorporate sophisticated DLP techniques such as document fingerprinting and context-aware detection to identify and protect sensitive data. These tools scan data within cloud applications and networks, detecting unauthorized access or data exfiltration attempts. When sensitive content is identified, CASB allows IT teams to take immediate action, such as encrypting or blocking data, or redirecting suspicious activity to on-premises systems for further analysis.
4. Threat Protection
Protecting against cloud-based threats is critical for enterprises. CASB solutions provide real-time threat protection by monitoring and mitigating risks associated with cloud services. They detect and block malware, phishing attacks, and other malicious activities that could compromise organizational data. For example, if an employee unknowingly uploads an infected file to a cloud storage service, CASB can detect and quarantine the file before it spreads further.
In summary, CASB security pillars—Visibility, Compliance, Data Security, and Threat Protection—work together to enhance organizational security in cloud environments.
Why Should Your Enterprise Use CASB Security?

Implementing CASB security offers numerous benefits for enterprises, bridging the gap between security needs and cloud service capabilities. Here’s why your enterprise should consider adopting CASB security:
1. Compliance Assurance Across Regulations
As more data moves to the cloud, ensuring compliance with diverse regulatory standards becomes increasingly complex and crucial. CASBs enforce compliance by providing tools for data discovery, classification, and encryption. They protect sensitive information, mitigate the risk of compliance-related penalties, and safeguard against reputational damage.
2. Advanced Threat Protection and Anomaly Detection
The cloud's dynamic nature exposes enterprises to various cyber threats, from malware to ransomware and phishing attacks. CASBs utilize advanced analytics, machine learning, and user and entity behavior analytics (UEBA) to effectively detect and mitigate these threats.
3. Enhanced Visibility and Control Over Cloud Services
CASBs offer comprehensive visibility into an organization’s cloud service usage, encompassing both approved and unapproved services. This visibility is critical for identifying and managing "shadow IT," where employees use unauthorized cloud services without IT oversight. By mitigating these risks, enterprises can maintain security and compliance standards.
4. Cost Management and Resource Optimization
CASBs assist enterprises in managing and optimizing cloud costs. By providing visibility into all cloud services, they identify redundant services and inefficient license allocations. This enables better resource management and significant cost savings.
5. Shadow IT Assessment and Management
CASBs provide detailed insights into all cloud application usage, allowing enterprises to assess and manage risks associated with shadow IT effectively. This proactive approach aligns cloud service usage with business goals and compliance requirements, enhancing overall security and operational efficiency.
Thus, adopting CASB security empowers enterprises to secure their cloud environments effectively, ensure compliance with regulations, protect against advanced cyber threats, optimize resource usage, and mitigate risks associated with shadow IT. By integrating CASB into their security strategy, organizations can enhance resilience, streamline operations, and maintain a competitive edge in the digital landscape.
How Does a CASB Security Work?
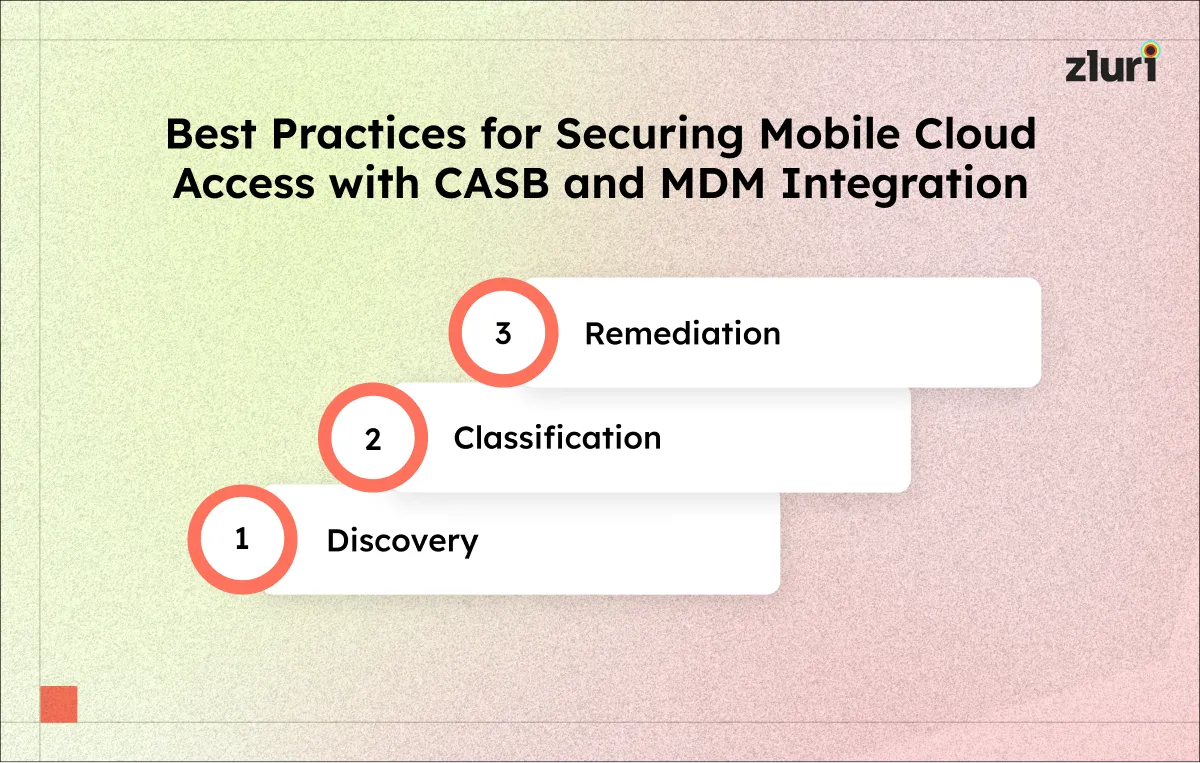
For enterprises, CASB (Cloud Access Security Broker) serves as a critical security layer that governs user interactions and cloud services. Here’s a detailed look at how CASB security functions in an enterprise environment, focusing on specific tailored aspects:
Step 1: Discovery
CASB begins with the discovery phase, where it identifies all cloud applications used within the organization. This includes both sanctioned and unsanctioned apps. CASB provides comprehensive visibility by mapping out which employees utilize these applications. It assesses cloud usage patterns, current states, and potential security risks.
Step 2: Classification
In the classification stage, CASB thoroughly evaluates each identified cloud application. It categorizes these apps based on the types of data they handle and assesses the associated risk factors. Criteria for assessment typically include data sensitivity levels, compliance requirements, and the security features provided by each cloud service.
Step 3: Remediation
The final step involves formulating and implementing a tailored security policy for the organization’s cloud infrastructure. This policy is customized to meet specific enterprise needs, focusing on controlling access, protecting data, and ensuring compliance with regulatory standards. CASB continuously monitors the cloud environment through remote access, actively searching for any indicators of security breaches or potential threats.
When a security risk is detected—such as a data breach, policy violation, or suspicious activity—CASB swiftly initiates remedial actions. These actions may include blocking access, encrypting data, or quarantining affected resources to mitigate the risk and safeguard organizational assets.
By integrating CASB into your security infrastructure, It teams can effectively manage and secure their cloud environments while maintaining compliance and protecting sensitive data from emerging threats
Key Considerations When Choosing A CASB Security Tool
Implementing a Cloud Access Security Broker (CASB) is a strategic move for enhancing your data security. A CASB integrates with other core data security tools and technologies to offer a comprehensive solution. Since every provider has a unique offering, it's crucial to select one that aligns with your organization's specific security needs.
Here are key factors to consider when choosing a CASB provider:
1: Range of Security Features
Evaluate the CASB’s security features, including real-time threat protection, data loss prevention, and encryption. Look for advanced capabilities such as entity and behavior analytics, user analytics, anomaly detection, and secure collaboration tools. These features ensure robust security and help in identifying and mitigating threats effectively.
2: Deployment Model
Determine which deployment model suits your organization best—on-premises, cloud-based, or hybrid. Each model has distinct advantages in terms of scalability, control, and cost. Your choice should align with your IT strategy, security policies, and regulatory requirements.
3: Vendor’s Reputation and Support
Research the vendor’s market reputation by reviewing testimonials, case studies, and reviews from customers, especially those in similar industries. Assess the vendor's customer support, including their technical expertise, risk assessment experience, availability, and responsiveness. Reliable support is critical for addressing security issues promptly.
4: Compatibility with Existing Cloud Services
Ensure that the CASB is compatible with your existing cloud services or plans, such as AWS, Azure, Google Cloud, and various other SaaS platforms. The CASB should integrate seamlessly without disrupting your current workflow or endpoint protection, and without requiring extensive modifications to your setup.
5: Compliance and Data Privacy Regulations
Choose a CASB that supports compliance with relevant regulatory requirements such as HIPAA, GDPR, and CCPA. The provider should offer tools for data classification, discovery, encryption, audit trails, and reporting functionalities. These features help maintain comprehensive protection and manage data privacy effectively.
By considering these factors, you can select a CASB security provider that not only meets your security needs but also enhances your overall data protection strategy.
Challenges of CASB Implementation in an Enterprise

Implementing a Cloud Access Security Broker (CASB) in an enterprise is a strategic move to enhance network security, but it presents several challenges that need to be addressed for optimal performance and seamless integration.
Here are some common challenges enterprises might face when using a CASB security platform:
1: Difficult Integrations
Integrating a CASB with an existing network infrastructure can be complex. This complexity is heightened if the enterprise already uses numerous cloud services and solutions. Ensuring that the CASB is compatible with all existing systems and operates seamlessly within the current setup is a significant challenge. Integration issues can lead to disruptions in service and require extensive configuration and testing to resolve.
Mitigation Strategy: To mitigate integration issues, it is crucial to have a comprehensive understanding of the existing network infrastructure. Engage with CASB providers early in the process to determine their solutions' compatibility and integration capabilities.
2: Complex Policy Management
Managing security policies across multiple cloud services and applications is inherently complex. Enterprises must ensure consistent policy enforcement and compliance across a diverse range of platforms. This requires ongoing attention, as policies must be regularly updated to address new threats and changes in the cloud environment. Additionally, the policies must be aligned with various regulatory requirements, which can vary by region and industry.
Mitigation Strategy: Consider consolidating cloud services under a single provider to simplify policy management. This consolidation can streamline the creation and enforcement of security policies, reducing the administrative burden.
3: Higher Costs
CASB solutions can be expensive, particularly those that use a per-user pricing model. As the number of SaaS applications and users increases, so do the costs. Moreover, there can be hidden costs associated with implementing a CASB, such as the need for additional hardware, software licenses, and ongoing maintenance and support. Enterprises must carefully evaluate the total cost of ownership (TCO) of a CASB solution to ensure it is a financially viable option.
Mitigation Strategy: Evaluate the cost-to-benefit ratio of different CASB solutions and consider alternatives like set management platforms that might offer better ROI. Look for solutions that offer flexible pricing models or volume discounts to manage costs more effectively.
4: Increased Network Latency
One of the significant concerns with CASB solutions is the potential for increased network latency. Since CASB solutions route traffic through their service for inspection before it reaches its destination, this additional step can slow down data transmission. Increased latency can negatively impact the performance of cloud applications and user experience, which can be particularly problematic for real-time applications that require low latency.
Mitigation Strategy: Research and select a solution that balances security with performance. Some modern solutions offer more efficient routing and inspection processes to minimize latency, ensuring that security does not come at the expense of performance.
Addressing these challenges requires a thorough evaluation of CASB solutions and strategic planning to ensure successful implementation and operation within an enterprise. By understanding and mitigating these issues, organizations can leverage CASB security to enhance their security posture effectively.
Strengthening Cloud Data Protection with CASB Security
The importance of CASB security for cloud data protection cannot be overstated. As enterprises continue to embrace cloud technologies, the need for robust security measures becomes increasingly critical. CASB solutions offer a comprehensive approach to safeguarding sensitive data, ensuring compliance, and mitigating risks associated with cloud services.
By implementing strong CASB security measures, enterprises enhance their security posture and leverage cloud technologies more confidently and effectively. However, if you're seeking a solution to enhance your organization's compliance and security, Zluri is here to help. Zluri offers a robust access review solution designed to streamline compliance audits. It quickly assesses access, providing comprehensive visibility into users, roles, and entitlements across all applications.
Whether you're complying with SOX, HIPAA, GDPR, or PCI DSS, Zluri ensures adherence to diverse regulatory frameworks while bolstering security. It provides real-time data on access and compliance risks, keeping you informed and prepared. Additionally, you can generate detailed reports on users, actions, and reviewers and automate access remediation to promptly address overprivileged access, strengthening defenses against potential threats.
Frequently Asked Questions (FAQs)
1.How do you choose a CASB?
When selecting a CASB, it's important to consider several key factors. These include compatibility with existing cloud services and security infrastructure, the range of security features offered, and the ability to help comply with laws like GDPR, HIPAA, or CCPA. Other considerations should include the deployment model that suits your organization’s needs, the scalability and performance to accommodate growth, and the vendor’s reputation and quality of customer support.
2. What is the Security Service Edge (SSE)?
Security Service Edge (SSE) is a comprehensive security framework that combines multiple security services such as CASBs, Secure Web Gateways (SWG), and Zero Trust Network Access (ZTNA) into a single, unified cloud service. This framework is designed to secure access to data, applications, and services from anywhere, making it a critical component of the broader Secure Access Service Edge (SASE) architecture.
3. What is the difference between CASB and SIEM?
While both CASB and SIEM are integral to enterprise security, they serve distinct functions. A CASB secures and governs data across cloud services, providing specific solutions for cloud applications, including visibility, compliance, and threat protection. In contrast, an SIEM system focuses on the management and real-time analysis of security alerts across an organization's entire IT environment, integrating log and event data to enhance security management and incident response.
4. What is CASB most commonly used for?
CASBs are primarily employed to manage and secure cloud environments. They gain comprehensive visibility and control over cloud services, ensure compliance with regulatory standards, protect sensitive data through robust security measures such as encryption and access controls, detect and mitigate security threats with advanced analytics, and manage access policies effectively to secure user interactions with cloud applications.


%20Security%3F.webp)




.png)

.svg)














