Unsure how to regain control over compromised systems and applications during a security breach? Or perhaps you don't know what to do when your IT teams get locked out from systems due to technical glitches or server outages. If these issues sound familiar, break glass is the solution for you. What is it? In this article, we'll explore this concept in detail.
On September 15th, 2022, Uber fell victim to an organization-wide cybersecurity breach carried out by an attacker named 'Tea Pot,' who was associated with the Lapsus$ hacking group (famous for breaching NVIDIA, Samsung, and Microsoft).
The attacker first gained access to Uber's internal network*.corp.uber.com. Then, they found one PowerShell script that contained hardcoded credentials for a domain admin account for Thycotic (Uber's privileged access management solution).
They further used that admin access permission to log in and take over multiple services and internal tools that were actively used in Uber, such as AWS, Google Drive, Slack, GCP, the HackerOne admin console, Uber's internal employee dashboard, SentinelOne, and a few code repositories. After that, they leaked a large volume of data and made the system completely inaccessible to the security team by altering the security settings, creating havoc.
Since the attackers held admin-level access, Uber could not stop the breach, and towards the end, they considered completely shutting down their system. But just as things seemed to reach a breaking point, the hacker unexpectedly dropped everything and walked away.
Now, the question is — 'Is there a possibility of your organization falling victim to such an attack?' The answer is yes. If a multi-billion dollar organization like Uber can become a target, then you are no exception – in fact, no one is off-limits! However, unlike Uber, you might not get lucky.
So, don't take chances! Rather, prepare yourself well in advance to tackle such an attack. How to prepare? You can implement a break-glass approach that will help you regain control over the system and applications in case of an emergency. How? Let's find out.
What Is Break Glass?
Break glass is a contingency mechanism (incident responding action) designed to provide emergency access to critical systems, applications, or data in case of a security incident (it is activated when malicious actors infiltrate systems and alter/manipulate the security setting to block IT teams from entering or accessing their systems).
This term is derived from the “in case of emergency, break glass” concept. You may have seen physical emergency equipment such as fire extinguishers or emergency alarm boxes in schools, offices, or public spaces. You also may have noticed that they are generally kept behind glass panels with a note beside — ‘break the glass in case of an emergency to access the equipment.’ This means you have to break the glass to take charge of the situation and handle it before it escalates. This is exactly what break glass means in the digital access world.
However, you need to understand that break glass access, aka emergency access permission, is assigned to break glass accounts exclusively – no other accounts are authorized to hold this type of access.
What Is Break Glass Account?
Break glass accounts are high-privileged accounts (users/owners of these accounts are generally IT admins or security teams) that are used during security events to access systems and apps by bypassing the organization’s security systems, and regaining control over them.
However, these accounts are reserved strictly for emergency situations only (they are not meant for everyday operations/regular use).
Note: Most organizations tend to maintain two break glass accounts, so that if one fails to work, the other can take over and save the day in an emergency event.
Now let’s understand when exactly you should use these accounts as an IT admin or security team.
When Should A Break Glass Account Be Used?
Mentioned below are a few scenarios when you should actually use your break glass accounts.
Situation 1: Multi-Factor Authentication System Outage
Sometimes, multi-factor authentication systems become unavailable (stop working) or fail to function properly for a prolonged duration (often caused by network outages or technical glitches). This outage leaves users stranded; they cannot access critical systems or applications to complete their current tasks or proceed with new projects (the non-functional MFA system does not allow users to enter the systems). As a result, operations come to a halt.
So, to address such a situation, you as an IT team or security team can use the break glass/ emergency access account, bypass the non-functional MFA, and adjust its security setting (like temporarily disabling the MFA system and replacing it with a new one). By doing so, you can restore normalcy and bring everything back to its original state (streamlining the operation flow, which was interrupted by the MFA outage).
Also Read: How do I set up two-factor authentication?
Situation 2: Account Gets Locked Due to Multiple Incorrect Password Entries
When a user repeatedly enters (unintentionally) the wrong password multiple times, the authenticating system automatically locks the user’s account as a safety measure (the systems are configured to perform this action). This leaves the users with two options: wait until the system grants another chance (which might take hours and even days) or delete the existing account and create a new one.
See! Waiting is still manageable if you don’t have urgent work lined up, but deleting the account might introduce some complicated issues.
For example, you are a senior executive, so typically, your account will hold access to multiple critical applications, documents, and data.
Suppose your account gets blocked (due to repeated incorrect password entries), and you decide to delete the account. So, what will happen is you will lose all the access permissions and have to re-request access to regain those permissions. In the worst-case scenario, you might lose access to exclusive documents (with no copies) that you only had access to. As a result, this small mishap will turn into a major setback!
Rather, you can request that your IT teams use emergency access accounts and fix this lockout by changing or adjusting account settings. Once your team does what is needed, you can regain access to your account and continue performing your daily tasks.
Situation 3: During Cyberattack Or Security Breach
Attackers often exploit the weak points/vulnerabilities and use them as a gateway to infiltrate the organization’s ecosystem. Once they get the entry, the first thing they do is — alter security settings to lock out the IT admins/security teams and even make every single system and app completely inaccessible to users.
To tackle such situations and prevent attackers from causing further damage, you have to use your emergency access account. This account will help you bypass the attacker's restriction and regain control over your ecosystem. Once you’re back in charge, you can immediately re-configure security settings, revoke the attackers' access, and restrict/block them from further accessing apps and systems, putting a stop to the attack!
Now that you are familiar with the concept of break glass and when these accounts can be used, let’s proceed further and understand how to create and manage these accounts.
How To Create & Manage Break Glass Account?
Below, we’ve outlined the steps to create and manage break glass account:
Step 1: Create A Break Glass Account
The process of creating a break glass account is similar to setting up a standard digital user account. The only difference is that — these account credentials are not made for single users; rather, they are shared between two trusted individuals (usually IT admins or senior executives).
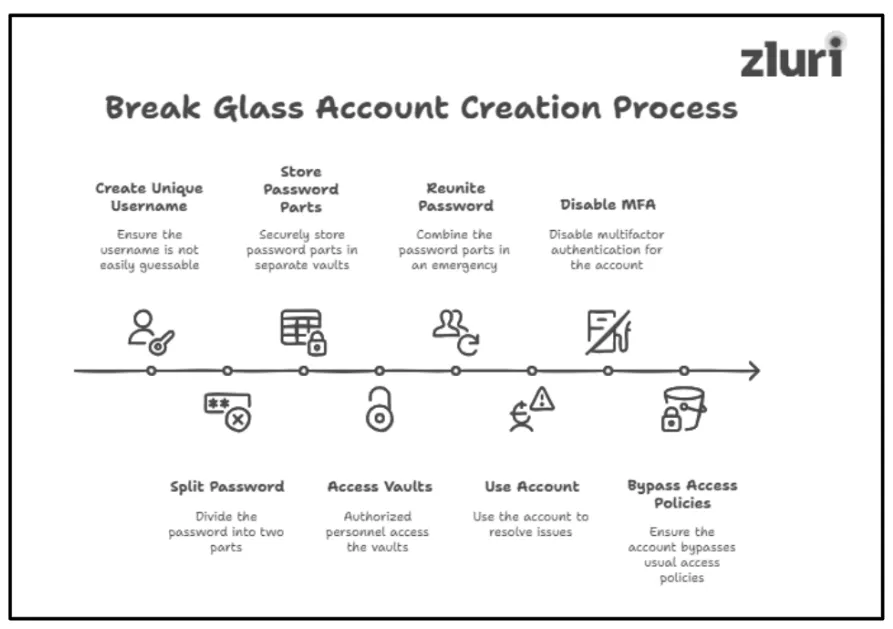
Also, there are a few things that you need to take into account while creating these accounts, such as:
- Make sure the username for this emergency access account is not easy to guess — just try to create a username that’s beyond the obvious.
- Next, split the password into two parts and securely store them in separate digital vaults (make these vaults only accessible to trusted personnel). In case of an emergency, authorized/trusted personnel can directly access the vault, reunite the halves, and use the account to resolve issues and regain control.
Note: Some organizations take it a step further by using FIDO2 Yubikeys to secure these accounts. However, make sure to keep these keys in a safe space.
Also Read: Credential Management
- Passwords should be set to ‘not to expire’ so that during an emergency, the trusted personnel doesn’t have to reset passwords (which can interrupt security events).
- Also, make sure to disable multifactor authentication for these accounts. This is necessary because, often during breaches, malicious actors take over the authentication system. If you continue to keep MFA enabled for these accounts, the trusted person won’t be able to access the account—as hackers won’t verify them or authorize them to access it.
- Make sure this account is not bound by conditional access policies or any usual access control so that trusted personnel can immediately access it during an emergency.
Step 2: Assign Necessary Permissions To Break Glass Account
If you want your break glass accounts to help you tackle security incidents, you need to grant them high-level access privileges (i.e., admin rights).
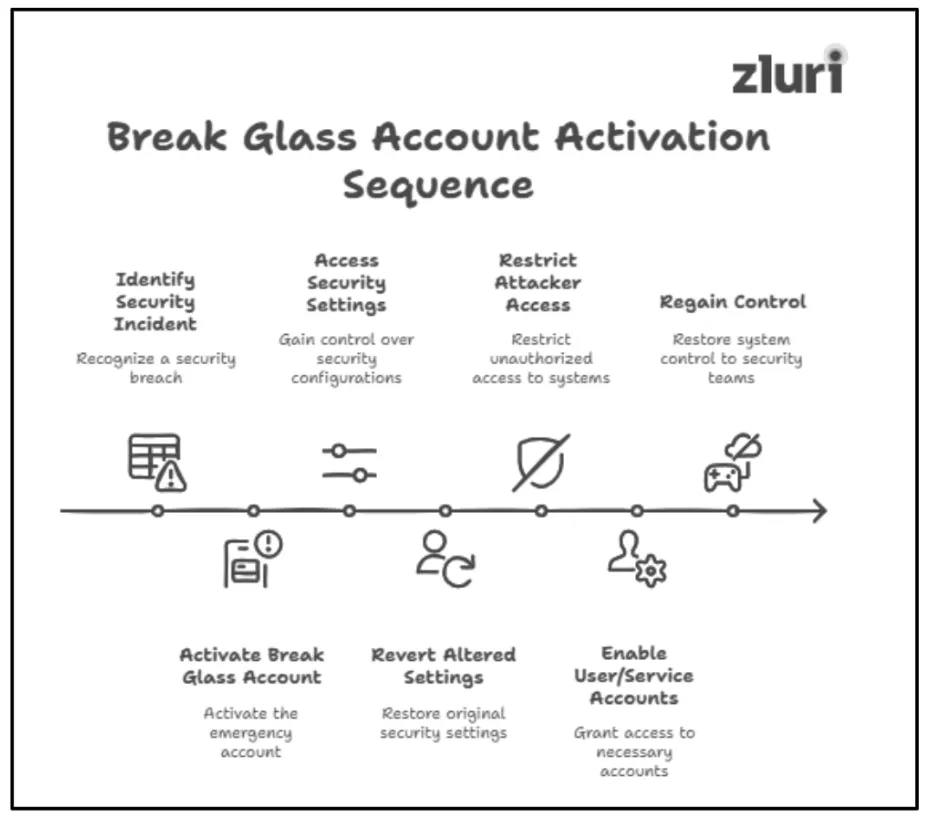
By providing necessary access permissions, these accounts will be able to —
- Access security settings and revert the settings if hackers have altered them to lock out everyone.
- Restrict attackers' access rights to prevent further damage.
- Make user and service accounts accessible to the security and incident response teams so they can take immediate actions to regain control.
Also Read: Service Accounts Vs. User Accounts: What Is The Difference?
Step 3: Define Break Glass Policy
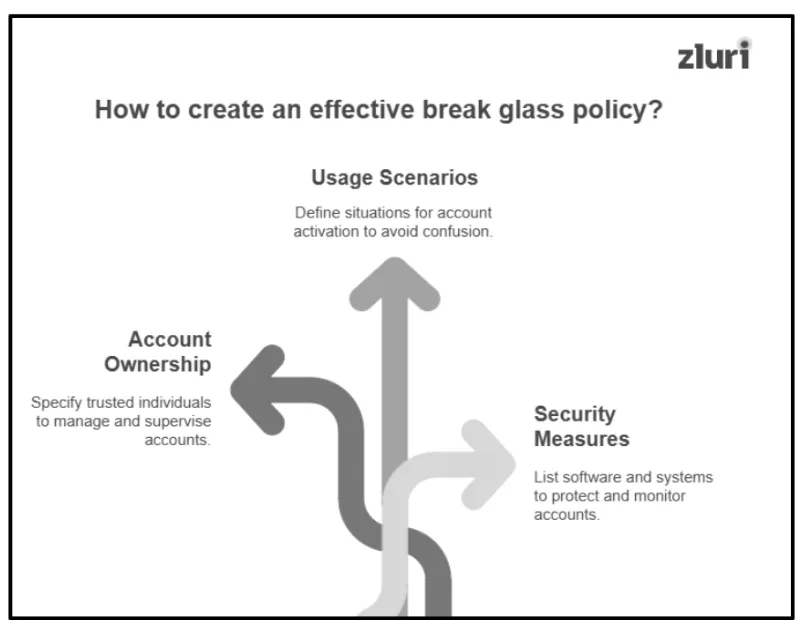
In order to create an effective break glass policy (a formal set of guidelines), you have to incorporate the following key points:
- Who will hold the account ownership?
You need to specify which trusted individuals will be given account ownership (such as who will manage, use, and supervise these accounts).
- When to use the account?
You have to clearly mention the situations/emergencies where these accounts should be used (for example, system failure, cyberattack, or lockout). In fact, you also have to prepare a contingency plan/incident response plan well in advance and specify exactly when and how these accounts will be activated during critical moments to avoid any confusion.
- Which software or systems will be in place to secure and monitor these accounts?
List all the software and systems you’ll use to protect and monitor these accounts. This way, in case any unknown or unauthorized system/software interacts with these accounts (that is not specified in the list), you will be able to quickly spot them, and accordingly, you can take immediate action (like block the software or restrict the system) to prevent them from compromising these accounts.
Step 4: Review the Break Glass Account Every 90 Days
Lastly, to ensure that your emergency accounts can effectively perform during an emergency situation, you have to review them on a periodic basis (90 days). To do so, you can hire an ethical hacker (also known as a white hat) to perform a simulated attack to breach your system, and then you can use these emergency access accounts to tackle the attack.
If the account works flawlessly (that means it helps enter your system and allows you to regain control), you are all set to address real-time threats. If it does not perform as intended, you need to make the necessary adjustments (like granting additional access privileges) so that it functions properly during security breaches.
Take Precaution To Prevent Security Event In The First Place
You need to clearly understand one thing: break glass accounts are your emergency escape hatch, a last resort for regaining control after a major security incident. However, they are part of a reactive approach, not proactive measures. [meaning, these emergency access accounts are solely used for responding to crises (when damage is already done), not to prevent them from occurring in the first place.]
Therefore, you cannot solely rely on them to maintain the app and data security, integrity, and confidentiality—rather, you have to incorporate preventive measures into your security strategy. What can be done?
You simply have to follow the golden rule — restrict access to authorized users only and review the access right periodically to detect and close access gaps (that occur due to access misalignment).
Now, this may seem like quite an easy task to perform, but in reality, things get a little tricker – as you have to manage and govern multiple (100s, sometimes 1000s) user's access permissions. On top of that, if you rely on manual methods to perform these tasks (like using spreadsheets and checking each user's access right one by one), then you will just open doors for more mistakes.
So, to avoid going through the hassle, you can instead consider opting for solutions like Zluri. Zluri offers two distinct solutions – access management and access review, each designed to manage different aspects of user access. Zluri's access management solution helps ensure authorized users hold the right level of access to apps throughout their tenure by implementing access controls and automating provisioning, deprovisioning, and access modification. Meanwhile, Zluri's access review solutions conducts regular audits to detect access misalignments (like users holding excessive permissions or unauthorized access) and auto-remediates them to prevent the creation of access gaps that malicious actors can exploit to infiltrate systems and apps.









.svg)














