Microsoft Entra secures identities for digital workloads and controls employee access to cloud resources. Meanwhile, Okta strengthens connections between people and technology, offering features like MFA, sign-on policies, and role-based access.
However, both tools offer other unique functionalities that you, as an IT manager, can thoroughly examine before deciding which IGA tool to opt for.
To determine the most suitable choice between Microsoft Entra and Okta, it's crucial to thoroughly analyze each tool's capabilities and how they align with your GRC team's requirements.
Let's consider a scenario where an organization is transitioning to cloud-based applications and services and requires a tool to manage identity access effectively. So which IGA tool will be more appropriate for this scenario, Microsoft Entra or Okta?
Microsoft Entra would be particularly beneficial in this case, as it specializes in securing identities for digital workloads. It ensures that only authorized employees can access and utilize the cloud resources.
Whereas Okta is more suitable for organizations that put more emphasis on secure connections between people and technology. It offers features like MFA, sign-on policies, and role-based access control. This would help your IT teams ensure that your employees are properly authenticated and authorized to access specific SaaS apps and data, adding an extra layer of security to verify user identities.
This was just a gist of how a tool's features can greatly influence your decision-making process. However, relying solely on one particular functionality is not enough while determining the ideal platform; you need to evaluate and consider the distinctive features of each tool thoroughly.
So, let's move on and differentiate both tools based on different parameters to help you decide which IGA platform will best cater to your IT team's needs.
Also Read: Before choosing the suitable IGA tool, walk through How to choose a suitable IGA tool for your organization
Microsoft Entra Vs Okta: Detailed Comparison To Choose The Best IGA Tool
Below, we have compared the tools' functionalities in detail that will assist you in selecting the most suitable platform for streamlining identity governance and administration management.
1. Identity Governance & Administration
- Microsoft Entra Identity Governance enables your IT team to design workflows to automate employee identity creation, access updates, and access removal. It further allows your IT team to automatically assign SaaS apps and data access based on the employee's role, seniority, and department while ensuring Separation of Duties to prevent mishandling of access permissions.
Additionally, it ensures new employees get access to required applications on day one to increase their productivity and promptly revoke access when employees depart from organizations. This allows your IT team to safeguard crucial SaaS app data from potential security risks such as unauthorized access attempts.
Apart from that, Microsoft Entra utilizes automated insight to assess and maintain appropriate access for your employees. Furthermore, time and approval-based role activation mitigate excessive, unnecessary, or misused access to important resources. Your IT team can enhance employees' efficiency and strengthen security posture by doing so. - On the other hand, with Okta Identity Governance, where better security and enhanced productivity go hand in hand. It empowers your IT team to strengthen security measures, tackle modern security risks, and boost efficiency.
Through Okta Identity Governance, your IT team can seamlessly integrate IT and HR teams to automate your employees' onboarding and offboarding processes. This collaboration ensures a smooth and secure lifecycle management experience.
Furthermore, its core solution is access governance, enabling your IT team to maintain strict control over SaaS apps and data access. With it, they can ensure that the right employees have appropriate access to the necessary SaaS apps and data while minimizing unnecessary friction and complexities.
Additionally, your IT team can utilize Okta's Workflows platform to tailor complex identity governance requirements to their specific needs. Whether your team has coding expertise or not, they can leverage Workflows to customize and automate processes, streamlining identity governance workflows efficiently.
Also, compliance is made easier with automatic reports designed to meet auditor requirements. Moreover, it offers your IT team a complete view of every user's access patterns, enabling them to identify potential security concerns before they become critical issues.
Apart from that, Okta's self-service access request feature reduces frustration and empowers your employees to raise access requests without any hassle.
2. Passwordless Authentication
Both Microsoft Entra and Okta uniquely authenticate employees' identities securely and seamlessly. Let's find out how they make it possible:
- Microsoft Entra’s Passwordless AuthenticationMicrosoft Entra’s Passwordless authentication feature works as a form of multi-factor authentication (MFA) that eliminates the need for passwords. Instead, it relies on two or more verification factors securely stored and encrypted on the user's device. These factors can include biometrics like fingerprints or facial recognition, a device PIN, or a cryptographic key.
With this approach, the user's credentials never leave their device, effectively mitigating the risks associated with phishing attacks.
Furthermore, by adopting its passwordless authentication, your IT team can enhance the productivity of your employees by removing the burden of remembering passwords and reducing password fatigue.
Additionally, Microsoft Entra offers biometric technologies for different platforms, such as:
- Windows Hello for Business, offers a solution by replacing passwords with robust multi-factor authentication on Windows 10 platforms. Users can authenticate to enterprise apps, content, and resources using a biometric factor or a PIN without the need to store a password.
- Another one, the Microsoft Authenticator app, available for free on iOS and Android, offers another passwordless authentication method. It enables users to replace or supplement passwords with push notification approvals, one-time passcodes, and additional verification through a biometric gesture or device PIN.
- Lastly, FIDO2-compliant security keys are cryptographic credentials that come in various form factors, such as USB keys or NFC-enabled smartcards. To enhance security, they can be further protected with a second factor, such as a fingerprint integrated into the security key or a device PIN entered at sign-in.
- Password Management With Okta
Meanwhile, Okta removes the friction associated with traditional passwords so that your IT team can provide every employee a more convenient and secure experience. How does it do that?
With Okta's WebAuthn-based passwordless authentication, your IT team can eliminate reliance on passwords and strengthen the overall security posture. By following this method, your team can protect your employees' identities from the risks of phishing attacks.
It is not restricted to enhancing security; it further simplifies the authentication process. With WebAuthn, one authentication method can serve as two authentication factors which are equivalent to MFA. Your employees can authenticate once, and there is no need to undergo additional MFA steps. By doing so, you can improve employee experience without compromising security.
Furthermore, Okta also streamlines the authentication process by enabling employees to verify themselves by SMS and email across desktops, tablets, and mobile devices. This versatile solution offers flexibility and convenience while maintaining robust security.
3. Seamless Access Management
- Securely Managing Access With Microsoft EntraMicrosoft Entra’s secure, adaptive access feature ensures that access is protected through strong authentication and risk-based adaptive access policies. Your IT team can adjust access controls by analyzing various factors without compromising your employees' experience.
It provides an easy and fast sign-in experience, empowering your employees and increasing overall productivity and efficiency. With unified identity management, your IT team can efficiently manage all identities and access to SaaS apps, whether they reside in the cloud or on-premises. This centralized approach enhances visibility and control, simplifying identity management across your organization.
Furthermore, with Microsoft Entra's automated identity governance capabilities, you can ensure that only authorized users have access to applications and data. Also, it seamlessly discovers, remediates, and monitors permission risks for any identity, mitigating potential vulnerabilities and maintaining a secure environment.
This further helps your team achieve full visibility by discovering the SaaS apps and data accessed by each identity across your cloud platforms.
Apart from that, Microsoft Entra Permissions Management enables your IT team to assess identities, permissions, and resources from a multi-dimensional perspective, providing a complete view of risk.
Additionally, it enforces the least privilege policy, which helps prevent data breaches by detecting unauthorized access attempts. - Okta’s Universal Login
Whereas, with Okta, your IT team can authenticate your employees securely, ensuring their digital access is protected from the first click to the last. Further, it enables social login, allowing your employees to authenticate using their preferred social media credentials. This feature facilitates a seamless and fast authentication experience, reducing friction and improving employees' overall experience.
Additionally, Okta ensures an uninterrupted authentication experience with single sign-on (SSO). Your employees can access multiple applications seamlessly using a single set of login credentials, enhancing convenience and productivity. This also helps your IT team mitigate the risk of account hacking attacks and safeguard SaaS app data.
Also, it offers your team an intuitive dashboard to centrally control access to all SaaS apps and data centrally, streamlining administration and maintenance.
Apart from that, Okta's Universal Login conforms to WCAG AA standards, guaranteeing compliance with accessibility requirements and ensuring inclusivity for all users.
4. Security Parameters
- Microsoft Entra allows your IT team to enhance risk and compliance posture by identifying data risks and managing regulatory compliance effectively. With built-in privacy controls, its risk management features help your team leverage both native and non-Microsoft applications.
Further, your team can gain insights into user access activities and communications across your digital landscape through native signals and enrichments. This comprehensive visibility lets your team proactively identify potential risks and take appropriate measures.
Also, Microsoft Purview Insider Risk Management effectively addresses code of conduct policy violations that occur across company communications. Support a healthy work environment and meet industry-specific compliance requirements.
Additionally, utilizing Microsoft Purview eDiscovery capabilities such as near-duplicate detection, email threading, relevance, themes, and smart tags, enable your GRC team to effectively reduce and cull large volumes of data, streamlining the eDiscovery process. - On the other hand, with Okta, your IT team can protect your employee's accounts and SaaS app data from credential theft and fraud with its multi-factor authentication (MFA) solution. By implementing MFA, your team can secure customer-facing and enterprise SaaS apps that hold sensitive data, ensuring that only authorized individuals can gain access.
Further, to provide an extra layer of security, leverage Okta's ThreatInsight, which automatically blocks suspicious IP addresses that have attempted identity attacks on other organizations within Okta's customer base.
Also, it integrates external risk signals from various security vendors to enhance your overall security and fraud prevention stack, gaining better visibility into potential threats. This integration allows your team to step up authentication or block requests when necessary without causing an unnecessary interruption in the flow of work.
With Okta, your IT team can also create contextual access policies that assess risk factors such as device, network, location, travel, IP, and other relevant contexts at each step of the authentication process.
It also ensures that you comply with the authentication assurance levels demanded by your industry.
After thoroughly comparing Microsoft Entra and Okta, you might have understood which tool best aligns with your IT team's specific needs. However, it's crucial to note that other platforms are also available and worth considering. One such exceptional platform is Zluri, which offers remarkable features that help your IT team streamline the identity governance process.
So, let's have a quick look at how Zluri is a better alternative to Microsoft Entra and Okta.
Zluri: The Most Ideal Identity Governance & Administration Platform For Your IT Team’s
In the era where SaaS adoption and work decentralization is taking a hike, managing and reviewing user access has become more complex for IT teams. As they lack visibility into user access which further poses a security risk to the data stored in SaaS applications. Fortunately, there's a solution that can help address these challenges, i.e., Zluri. Why Zluri? What does it do that others can’t?
Zluri is a modern identity governance and administration (IGA) platform that prioritizes identity governance by focusing on data security and compliance, which are prime concerns for most organizations. How does Zluri do it? Well, it offers features like a data discovery engine, automated access reviews, auto-remediation, and more. That further enables your IT team to gain full visibility into access, assisting them to define policies for reviews, remediating access post-review, and more, ensuring effective access governance.
Moreover, it takes a step further by introducing additional benefits, i.e. identity administration features, allowing your IT team to manage access requests and streamline provisioning and deprovisioning processes through automation. By leveraging these features, both your IT team and employees can improve their productivity and efficiency, eliminating the need for manual work.
To help you understand better, let’s take an example, previously, when the perimeter (number of users and applications) was small, IT teams found it easier to manage and govern access. However, as more apps were introduced, and remote work became prevalent, IT teams were lacking visibility into the access environment and unable to accurately detect which systems, network the users were using. This compromises data security by increasing the chances of data breaches.
So here’s what Zluri does to overcome this scenario. It comes to the rescue by providing unified access through its data discovery engine, enabling IT teams to identify who has access to which all SaaS apps. With these insights in hand, they can closely keep a tab on the entire access environment, detect threats, and take prompt actions to remediate them, either through automation or manual intervention (if critical data is involved during access management or review).
This is just a brief overview of how Zluri works. The bigger picture is yet to be explored. So, let’s learn about its exclusive capability one by one to understand how Zluri sets itself apart from its competitors and provides an unparalleled solution for effective access governance.
1. Discover User Access Data With Zluri Data Discovery Engine
Zluri is better than competitors at discovering data since it is primarily a SaaS management platform. This background has given Zluri a distinct advantage, making it highly effective and proficient in identifying SaaS app data. One area where this expertise proves exceptionally valuable is in the area of user access data identification.
With Zluri’s five discovery methods, i.e., SSO or IDP, finance systems, direct integrations, browser extensions (optional), and desktop agents (optional), your IT team gains the ability to explore and unveil essential details. They can seamlessly identify which users have access to particular SaaS apps, what all access rights are granted to them, identify the user status (active or inactive), and more.
These insights are a game-changer for user access management and SaaS app data security. Armed with such granular knowledge, your IT team finds it easier to conduct access reviews. Also, the process becomes streamlined, efficient, and less prone to oversight, ensuring access privileges align with user role and compliance requirements.

2. Automate Access Management With Zluri’s Automation Engine: Ensuring User Access Aligns With Their Role & Responsibilities
Effective access management begins right from the moment an employee joins a company. The IT team is responsible for ensuring that from day one, the right access is granted to the right applications. However, when IT teams manage the provisioning process manually, it becomes prone to errors, affecting productivity and efficiency.
- Ensuring Right Access Is Granted To Right Employees
So what Zluri does is it ties user profiles with their digital identity during onboarding. Further, when your IT team verifies user identity to grant them access during the provisioning process, they can simply cross-check the details from a centralized dashboard. Thus, this integration allows your IT teams to assign user access that aligns with their job role accurately.
But it doesn't stop there; Zluri automates the entire provisioning process, granting new employees access with just a few clicks. By automating the process, your team can ensure the right access is granted to the right employees with the right level of permissions to necessary apps. That further boosts employees' productivity by enabling them to start working from day one.
You must be wondering how Zluri automates the provisioning process? Well, your IT team can create onboarding workflows. All they need to do is select users they want to grant access to or onboard and apps (you can even choose from recommended apps option), which all apps they want the users to access.
Then, your team can take necessary actions easily by clicking "add an action." Here, they can schedule the workflow and more.
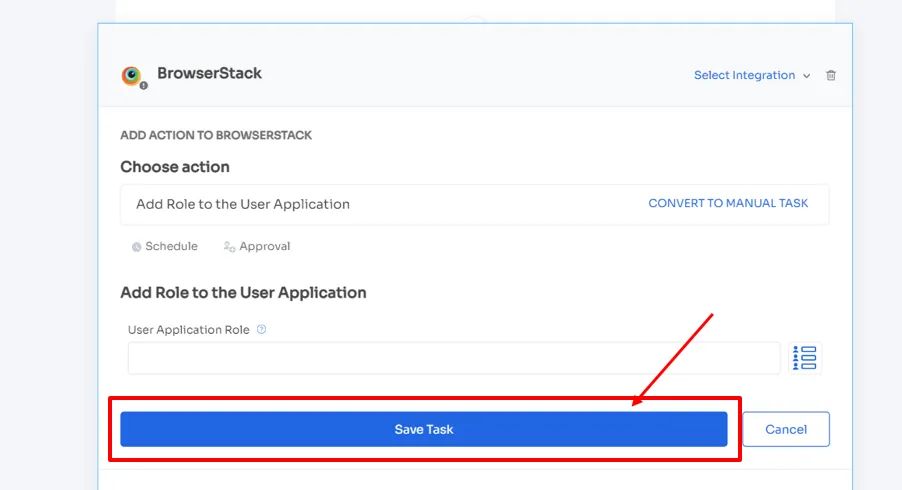
- Zluri even provides in-app suggestions, allowing your team to add employees to different channels, groups, or projects or send automated welcome messages.
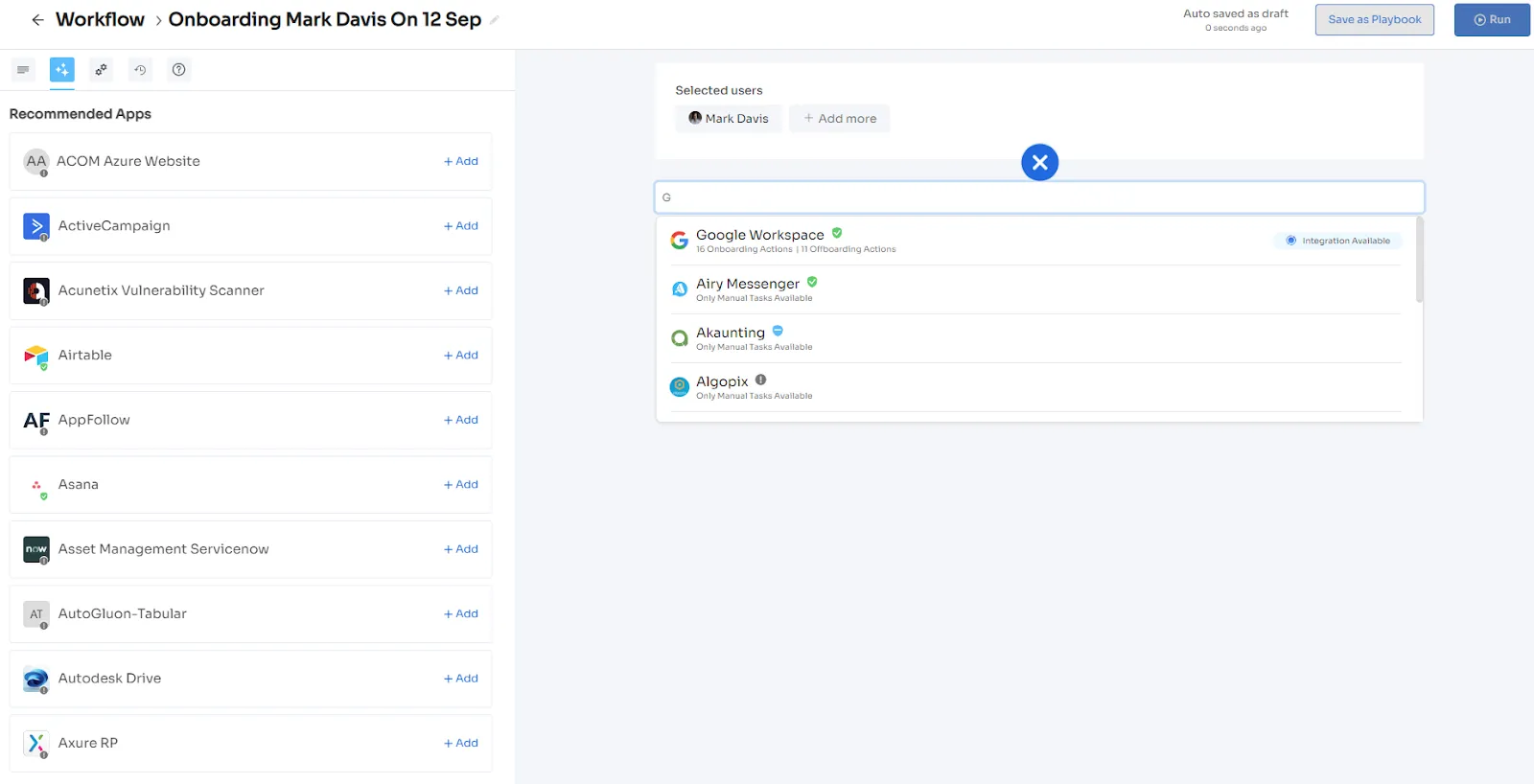
- The actions can vary for different applications and are mentioned under recommended actions. Once all the actions are set, you can directly run the workflow or save it as a playbook for future use. For added efficiency, Zluri offers automated playbooks (i.e., collections of recommended applications for automation) that can be customized for different roles, departments, and designations. This feature streamlines the onboarding of new employees, making it as easy as a few clicks to set up their access.

- Note- Apart from that, your team can set automation actions, such as by triggering if and but conditions, they can grant Kissflow access to all the employees of the finance department.
- Ticketless Access Management
Now comes a critical phase where the risk of access mismanagement arises. As employees transition to new roles, departments, or require access to certain apps for specific tasks, their access requirements keep on changing. Generally, they have to wait for days to get their app access request approved, since the manual method involves multiple steps. So what Zluri does is it eliminates the time-consuming manual access request process through automation. Let’s see what it does?
In order to stay updated with the changes, Zluri integrates with HRMS. With the help of this integration, Zluri automatically retrieves and displays updated employee data on a centralized dashboard. By leveraging this integration, your IT team can easily access and verify employee details without manual effort.
This streamlined process ensures that access permissions align with current employee roles and responsibilities. Whether granting or revoking access, your team can efficiently manage user privileges based on the most up-to-date information available.

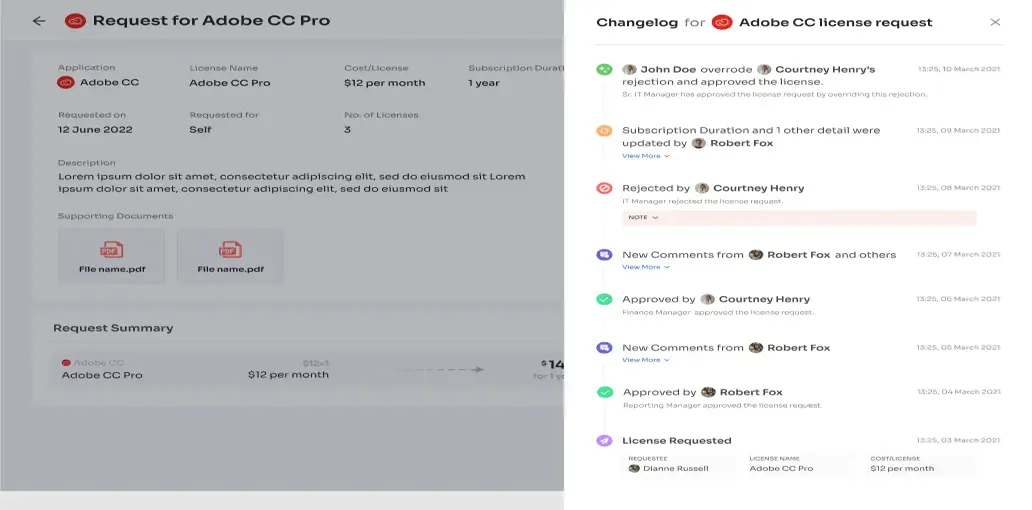
- It doesn't stop there, Zluri takes a step further to streamline the access request process by making it ticketless. It offers an App Catalog & Access Request, a self-serve model, which is a collection of applications pre-approved by your IT team. With this self-serve model, employees enjoy the flexibility of choosing any application from the app store and gaining quick access in no time.

- All they need to do is raise a request, and the IT team will verify and review their identity before providing access to the requested application. If approved, employees gain access right away. If access is declined, they receive prompt notifications along with reasons for the decision, any modifications made, or suggested alternatives for the application, all viewable in the \"Changelogs.\"
- Revoke Access When Not Required By The employees
Revoking access from departing employees or those who no longer require certain application access is a critical task for IT teams. Even a single oversight in this process can potentially lead to security breaches, jeopardizing data security.
Zluri recognizes this concern and provides a solution by automating the deprovisioning process. With just a few clicks, your IT team can effortlessly revoke the required or all access from employees without missing any crucial steps. This automation ensures timely and thorough revocation, safeguarding SaaS app data from potential security breaches such as unauthorized attempts.
Furthermore, to automate the process, your team can simply create an offboarding workflow. All they need to do is select the users from whom they want to revoke app access and then they will come across a list of recommended actions (such as signing out users, removing them from org units, and more).
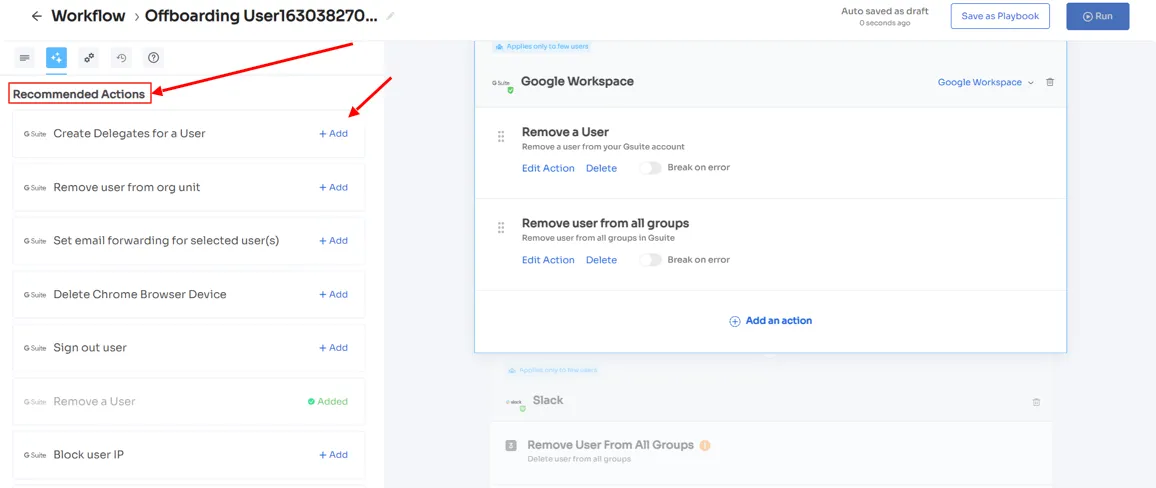
- Your team can choose one or multiple actions at once from the list; a point to note is that these actions will be executed post the deprovisioning process. Once all desired actions are added, your team can run the workflow instantly or save it as a playbook for future use.
3. Creating Access Certification Has Never Been This Easier: Govern Access Seamlessly
Now comes the most critical aspect of access management: access reviewing. Ensuring that each user has the appropriate level of access permissions to apps and data is quite important to maintain data safety. Manual access reviewing can be time-consuming and inefficient, requiring IT teams to gather user lists, user statuses, access patterns, and all the apps to which users have access.
For instance, a user previously had admin-level access to a specific application, but their access permissions were revoked by your IT team two months ago since they no longer required such high privileges. To ensure that user access remains appropriate, your team needs to review their permissions periodically and check if they still have the right level of access or have been granted admin-level permissions again. If they have been granted admin-level access again, what is the reason? Manually handling this process would be a significant waste of time.
To streamline access reviewing, Zluri comes to the rescue with automated solutions. Zluri automates the entire access review process, gathering all user access-related data in a centralized place. This simplifies the reviewing process for your team/reviewers, eliminating the hassle and making it more efficient.
This was just an overview; Zluri is not only restricted to these few access review capabilities; it has more to offer, which is exclusive and sets it apart from the competitors. So, let’s explore them one by one.
- Unified Access Review
Zluri’s unified access review feature allows your IT team to identify which users have access to all SaaS apps and data. Where does Zluri get all these insights from? Well, it has an access directory where all the user access-related data is stored in one central place.
Further, with the help of these insights, including whether the users are admins, regular users, which departments they belong to, and more, your IT team can examine users' access privileges and ensure their access aligns with the roles.
Additionally, Zluri’s activity & alerts capabilities come into play to keep things running smoothly. This feature provides real-time information about users' last activities and notifies IT teams about new logins. With the help of these insights, reviewers can make quick and informed decisions during access reviews, ensuring the right people have the right access at all times. - Automated Access Review
No more manual headaches with spreadsheets and JSONs! Zluri takes the hassle out of access reviews by automating the entire process. Just head to Zluri, create a certification, select the apps and users you want to review, and rest the reviewers will review and update you about the compilation via email.
So, by automating this process, you get 10 x better results than manual methods and save your IT team's efforts by 70%. Now let’s move ahead and see how it works. - Once you have gained access to contextual data through Zluri’s unified access feature, you can step further by creating access rules around these insights. For example, if someone is an admin on Salesforce, you can easily set up a review policy specifically tailored to that scenario.
- Next comes the schedule certification feature, where you can create certifications based on the gathered information. This allows you to take actions based on the insights you've gained. For instance, you can use data like last login, departments, user status (active or inactive) and more to make informed decisions during the review process such as whether the user can carry on with the existing access or need any modification.
With Zluri's context-rich information, your team can confidently take actions that align with your access management policies. It's a smarter, more efficient way to ensure the right access for the right users, all while keeping your data secure. Zluri's automated access reviews and access rules are the key to simplifying your access governance process. - Secure access orchestration/auto-remediation
After completing the access review, necessary changes will take place as per the set actions during certification creation, so all these actions, like access modification or removal, are part of secure access orchestration. The seamless process ensures access is managed securely and efficiently, safeguarding your organization's data and resources.
For example, while creating a new certification in Zluri, your team will come across configuration action under which they need to create deprovisioning playbooks and modification playbooks. If the reviewers decline the access permissions, the deprovisioning playbook will automatically run, and the same goes for the modification playbook. Also, for both scenarios, the reviewers need to provide relevant reasons stating why the access permission is declined or modified.
Point to note-These actions will take place automatically post the review, that's why this process is also known as the auto remediation process.
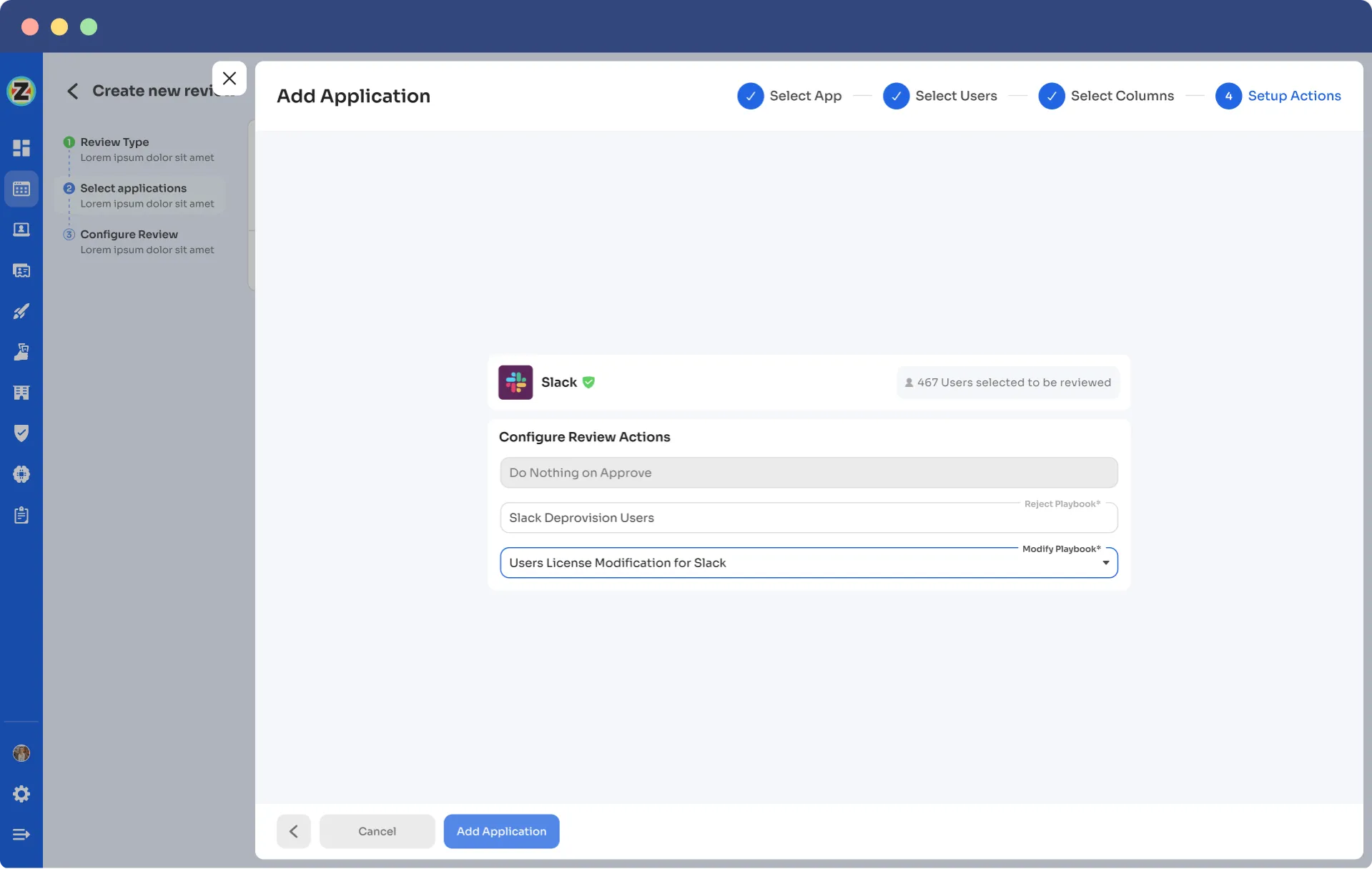
Apart from that, Zluri also offers integration features that are quite beneficial at the time of gathering access data. Though Zluri already has data within its platform, but integration allows it to gather even more valuable insights. By leveraging these integrations, it further enhances your access review process and strengthens the overall security posture of the organization.
For example, the top priority for the company is to review the Identity System and core applications, as they pose the highest risk. The Identity System, which stores crucial employee data, requires timely and thorough reviews to ensure security. So what Zluri does is it integrates with Salesforce, Okta, Azure, and other applications. Further, these integrations play a crucial role in gathering identity system and SaaS app data, providing valuable insights, and streamlining the review process.
Additionally, Zluri generates reports that are commonly associated with audit logs or audit trails. These audit reports serve as valuable documentation to share with auditors or keep as a reference for future reviews. And, audit trails act as roadmaps, showcasing the changes made during previous reviews.
For instance, if an employee's admin-level permissions were changed to user-level, it becomes essential to review and ensure that the access remains appropriate or if there were further changes back to admin. Understanding the reasons behind any upgrades is crucial for maintaining proper access control.
So Zluri automatically generates reports on such changes, which further helps in the reviewing process.
So why wait? Book a demo now and witness how Zluri enables your GRC team to streamline identity governance.
Also Read: Know Why is Zluri the Best IGA Platform?






.png)


.svg)














