Oracle enables your IT team to manage your organization's SaaS app data effectively by providing secure access to SaaS apps and preventing security breaches. Meanwhile, SailPoint allows your IT team to seamlessly manage digital identities, employee permissions, data access, and compliance.
However, apart from their primary capabilities, both Oracle and SailPoint offer a variety of other features as well that you, as an IT manager, can carefully evaluate. Moreover, these functionalities are crucial to consider when choosing the perfect IGA tool for your IT teams.
To choose the ideal platform between Oracle and SailPoint, you need to carefully assess the capabilities of each tool and how well they meet your IT team's needs.
Let's take an example to help you understand better; an organization requires an IGA tool that best suits the enterprise segment and effectively handles connectors to streamline integration processes. So which IAM tool will be more apt for this scenario, Oracle or SailPoint?
SailPoint will be a better choice in this situation as it comes with default connectors. This simplifies the integration process as you don't have to worry about individually installing and configuring connectors for different applications or systems. Also, this platform is suitable for large-sized organizations with 1000 plus employees.
Whereas, in the case of Oracle, individual connectors need to be installed separately, and configuration is required for each connector. For example, if you want to integrate with a specific application or system, you need to install and set up the connector specifically designed for that application or system. Furthermore, this tool is well-suited for small-sized organizations with 50 or fewer employees.
This was a brief overview of how the features of these tools can significantly influence your decision-making process. However, it's crucial to note that relying solely on one functionality is insufficient while determining the ideal solution; you need to thoroughly evaluate and consider each tool's distinctive features.
So, let's move on and differentiate both tools based on key features to help you decide which IGA platform will best meet the requirements of your IT team.
Oracle Vs SailPoint: Comparison Based On Different Parameters
Given below are the few parameters based on which we'll compare the tools and help you determine which tool will effectively streamline identity governance and administration management.
1. Solution Categories
- Oracle is categorized as a cloud directory service.
General Features Of Oracle
- Oracle offers a wide range of general features such as access control, alert/notifications, application security, compliance management, password management, reporting/analytics, self-service access request, single sign-on, and two-factor authentication.
- On the other hand, SailPoint is categorized as sensitive data discovery.
General Features Of SailPoint
- SailPoint provides features like compliance control, automated provisioning, identity governance for files, account management, access request management, password management, and role management.
2. Identity Governance & Administration
- Oracle enables your IT team to efficiently manage identities across both cloud and on-premises environments with a comprehensive and user-friendly access catalog. This catalog further helps simplify granting, modifying, and revoking access requests by leveraging role and entitlement suggestions.
How does Oracle help your IT team discover and mitigate compliance risks effectively?
Well, Oracle assists your IT team in discovering common access patterns within peer groups through intelligent role mining. Oracle Identity Role Intelligence automates role publishing to Oracle Identity Governance (OIG) by analysing organizational structure, user attributes, and business activities. This advanced solution continuously optimizes role-based access control using cutting-edge data mining, AI, and ML technologies.
Also, address compliance objectives effectively with granular entitlement management. This helps streamline compliance processes through customizable certification campaigns, focusing on user, role, application, or entitlement.
To keep track of the compliance process, it conducts audit-driven assessments that target high-risk entitlements or meet regulatory requirements such as SOX and GDPR. Continuously scan the business landscape to identify and remediate policy violations related to the segregation of duties. - Meanwhile, with SailPoint, your IT team can seamlessly enhance your organization's data security, streamline auditing procedures, and boost operational efficiencies. It safeguards your valuable information by automating access controls and benefits from the power of AI and machine learning through IdentityNow, a multi-tenant SaaS solution.
Furthermore, it offers a seamless deployment process for enterprise-grade Identity Security services directly from the cloud. Plus, the solution ensures rapid implementation and requires zero maintenance, allowing your team to focus on other core business objectives.
How does SailPoints help your IT team grant, modify, and revoke timely access?
With SailPoint, your IT team gains centralized control over SaaS apps and data access by efficiently discovering, managing, and securing all identity access. This further provides deeper visibility and helps your team mitigate potential security and compliance risks.
Also, your IT team can easily manage user access as they join, move, or depart from your organization while ensuring the right access permissions are granted to the required apps.
Moreover, with SailPoint, your employees can access the necessary resources remotely while maintaining security measures. It conducts detailed audits and generates reports to ensure transparency and compliance with regulations, enhancing trust and accountability.
Additionally, it streamlines certification processes with increased visibility, enabling faster and more accurate verification of user entitlements.
3. Securely Managing Provisioning & Deprovisioning
- Oracle offers user lifecycle management capabilities and robust access entitlement controls. It further supports microservices, enabling the discovery of common access patterns and the optimization of role-based access control.
How does Oracle expedite provisioning and deprovisioning processes?
Oracle oversees user provisioning and deprovisioning, ensuring a smooth and efficient user onboarding and offboarding experience. Its highly flexible and customizable workflow allows your team to grant and revoke access to apps quickly upon onboarding and offboarding of users. It also provides valuable identity intelligence that helps your IT team quickly address high-risk user entitlements, minimizing potential security issues.
Oracle offers self-service and managing access policies capabilities
- Through its self-service portal, your employees get the flexibility to request access to required SaaS apps and data.
- Not only that, but to maintain a secure access environment, your IT team can customize access policies. This helps ensure existing employees have access to those SaaS apps and data that aligns with their job role.
- Whereas, with SailPoint, your IT team can streamline the onboarding and offboarding processes with automation, providing your employees with the appropriate access on day one. It enables your team to quickly grant, modify, or revoke access, ensuring compliance, boosting productivity, and reducing costs by simplifying processes through automation.
This further helps accelerate the productivity of new hires from the day of their joining, eliminating human errors, and improving the efficiency of your employees and the IT team. Also, it minimizes the risk of over-provisioning or unauthorized access by former employees, enhancing security measures.
How does SailPoint streamline the onboarding and onboarding process? - It simplifies the provisioning process by automatically adjusting user access as changes occur.
- Validate access through audit, reporting, and metrics to ensure compliance with regulations.
- Improve efficiency by automating worker access, eliminating time-consuming manual processes, and maximizing productivity.
It also empowers your employees to work-from-anywhere, providing them with seamless and secure access to essential applications, systems, and data.
Additionally, it ensures the separation of duties by implementing role-based provisioning policies and aligning access privileges with organizational hierarchies.
Moreover, It manages worker accounts effectively to reduce risk, ensuring that former employees no longer have access to resources while current workers have only the access they need for their roles and responsibilities.
4. Maintaining Compliance
- Oracle is dedicated to assisting your IT team in navigating the challenges related to compliance and, accordingly, meeting the demands of complex regulatory environments.
How does Oracle address compliance issues?
Oracle provides effective solutions for addressing compliance objectives. With granular entitlement management, you can streamline compliance processes. This includes customizing certification campaigns that focus on specific aspects such as users, roles, applications, or entitlements. This targeted approach allows for more efficient compliance management and ensures that your organization meets the necessary requirements.
However, before implementing Oracle, it is highly recommended that customers conduct a formal analysis of their cloud strategy. This analysis should assess the suitability of Oracle cloud services based on their legal and regulatory compliance obligations. - On the other hand, SailPoint provides comprehensive capabilities to govern access, track usage, and enforce policies for all users, applications, and data. By automating regulatory enforcement and demonstrating compliance, your team can more effectively navigate the complex landscape of compliance requirements.
Further, your team can gain visibility and control over potential access risks by leveraging SailPoint. Also, it improves your compliance posture with automated reporting, enabling your team to quickly prove compliance when required. Reduce complexity and human error by implementing consistent organizational controls and policies.
Additionally, SailPoint helps you comply with global regulations such as CCPA, FISMA, GDPR, HIPAA, PCPD, PDPA, POPI, PPC, and SOX.
How does SailPoint make your team audit ready?
- Certify user access reviews with ease using AI-driven recommendations, ensuring fast, accurate, and simplified certification processes. Maintain a comprehensive audit trail of accounts, entitlements, policies, and actions, supporting thorough auditing requirements.
- Enforce policies and privileges continuously and organization-wide. Identify and address compliance gaps proactively, ensuring appropriate access across your entire organization. Simplify access certifications, eliminating guesswork and providing clear access maintenance or revocation recommendations. By doing so, your team can always be audit ready.
5. Zero-Trust Security
- Oracle allows your IT team to manage secure access by providing controlled and time-limited access to crucial SaaS apps and data. Furthermore, it simplifies certificate management by allowing easy creation, deployment, and management of SSL/TLS certificates for secure communication.
Also, it centrally manages encryption keys and secret credentials with Oracle Cloud Infrastructure Vault, enabling your IT team to maintain control and security over data. Providing an extra layer of data security enables your team to enforce security policies using a rich library of predefined policies and best practices. It also assesses and monitors vulnerabilities with Oracle Cloud Infrastructure Vulnerability Scanning Service, providing visibility into virtual and bare metal cloud hosts and assisting in the remediation of open ports and unsafe packages.
Additionally, adhere to regulatory compliance requirements with Oracle Cloud Compliance, participating in various programs that audit Oracle Cloud and assist customers in meeting global, regional, and industry-specific certifications. - However, SailPoint provides your IT team a 360-degree view of all user types and associated access privileges. By leveraging SailPoint, your team can effortlessly manage access throughout the user lifecycle, including provisioning, mid-life cycle transitions, and deprovisioning, thanks to its automated granting, modification, and revocation capabilities.
Furthermore, SailPoint's advanced capabilities allow your team to detect and prevent unauthorized access and proactively safeguard critical data. Enabling preventive measures ensures that potential security risks are identified and addressed promptly.
Apart from that, SailPoint consolidates access to decision-making through a unified and reliable source of truth. This centralized approach streamlines the process, facilitating accurate and efficient access management.
After closely comparing Oracle and SailPoint, you might have better understood which tool will fit your IT team's needs perfectly. However, you should not restrict yourself to two tools. That's because there are other efficient platforms available in the market. One such platform is Zluri which offers excellent functionalities to effectively manage identity governance and can be a better alternative to Oracle and SailPoint.
So, What is Zluri? What unique features does it offer? Here's a quick brief.
Zluri Identity Governance and Administration: Streamline Access Control & Compliance with Ease
Are you tired of your IT team's complexities and challenges in managing access permissions and ensuring compliance? Look no further, as Zluri presents the ultimate solution to your problems. Introducing Zluri's modern identity governance and administration (IGA) solution, designed to streamline user lifecycle management, access request processes, and access certification workflows. With a strong emphasis on efficiency, compliance, and data security, Zluri's IGA Solution empowers your IT team to seamlessly manage user identities, access privileges, and certifications.
But how does Zluri make it all possible? Below are a few remarkable capabilities that Zluri offers, enabling your IT team to handle access while meeting all compliance requirements effortlessly.
1. Gaining Clear Insights into User Access With Zluri's Data Discovery Engine
Zluri helps your IT team to analyze and discover all the SaaS app and users related data seamlessly with its 9 discovery methods, i.e., MDMs, IDPs & SSO, direct integration with apps, finance & expense management systems, CASBs, HRMS, directories, desktop agents (optional), and browser extension (optional).
With the help of these methods, your team can easily identify who has access to which applications, which are active users, what permission is granted to them, whether the employee accessing the apps falls under critical users, and more.

Zluri’s nine discovery methods
With access to this detailed contextual data, your IT team can easily conduct access reviews, improving efficiency, reducing the risk of oversight, and ensuring that access privileges align with user roles and comply with regulatory requirements.
2. Streamline Onboarding to Offboarding with Zluri's Powerful Automation Engine
Zluri empowers your IT team to efficiently manage employee access throughout their journey in the organization. It enables accurate access provisioning, smooth access modifications for changing requirements, and effortless access revocation when needed with its intelligent user lifecycle platform. Let's explore how Zluri achieves this seamless access management process.
- Seamlessly Grant Access Upon Provisioning
So what Zluri does is, it ties user profiles with their digital identity during onboarding. Further when your IT team verifies user identity to grant them access during the provisioning process, they can simply cross check the details from a centralized dashboard. Thus, this integration allows your IT teams to accurately assign the user access that aligns with their job role.
But it doesn't stop there, Zluri automates the entire provisioning process, granting new employees access with just a few clicks. By automating the process your team can ensure the right access is granted to the right employees with the right level of permissions to necessary apps. That further boosts employees productivity by enabling them to start working from day one.
You must be wondering how Zluri automates the provisioning process? Well, your IT team can create onboarding workflows. All they need to do is, select users, whom they want to grant access to or onboard and apps (you can even choose from recommended apps option), which all apps they want the users to have access to.
Then, your team can take necessary actions easily by clicking on \"add an action.\" Here, they can schedule the workflow, and more.
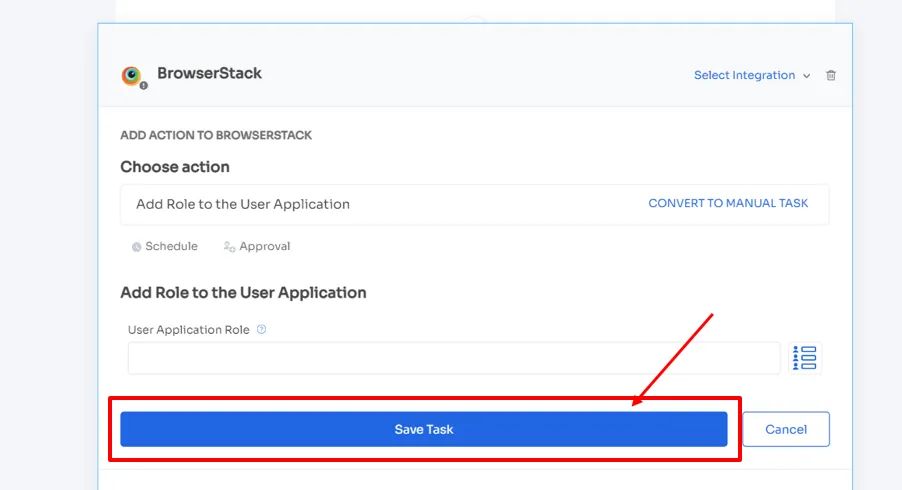
Zluri even provides in-app suggestions, allowing your team to add employees to different channels, groups, or projects or send automated welcome messages.
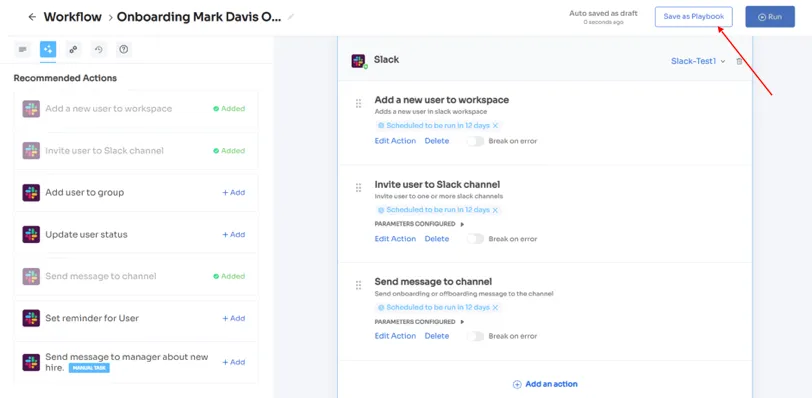
The actions can vary for different applications and are mentioned under recommended actions. Once all the actions are set, you can directly run the workflow or save it as a playbook for future use.
For added efficiency, Zluri offers automated playbooks (i.e. collections of recommended applications for automation) that can be customized for different roles, departments, and designations. This feature streamlines the onboarding of new employees, making it as easy as a few clicks to set up their access.

Note- Apart from that; your team can set automation actions, such as by triggering if and but conditions, they can grant Kissflow access to all the finance department employees.
- Ticketless Access Management
Now comes a critical phase where the risk of access mismanagement arises. As employees transition to new roles, departments, or require access to certain apps for specific tasks, their access requirements keep on changing. Generally, they have to wait for days to get their app access request approved, since the manual method involves multiple steps. So what Zluri does is it eliminates the time-consuming manual access request process through automation. Let’s see what it does.
In order to stay updated with the changes Zluri integrates with HRSM. With the help of this integration, Zluri automatically retrieves and displays updated employee data on a centralized dashboard. By leveraging this integration, your IT team can easily access and verify employee details without manual effort.
This streamlined process ensures that access permissions align with current employee roles and responsibilities. Whether granting or revoking access, your team can efficiently manage user privileges based on the most up-to-date information available.

It doesn't stop there, Zluri takes a step further to streamline the access request process by making it ticketless. It offers an Employee App Store (EAS), a self-serve model, which is a collection of applications pre-approved by your IT team. With this self-serve model, employees enjoy the flexibility of choosing any application from the app store and gaining quick access in no time.

All they need to do is raise a request, and the IT team will verify and review their identity before providing access to the requested application. If approved, employees gain access right away. If access is declined, they receive prompt notifications along with reasons for the decision, any modifications made, or suggested alternatives for the application, all viewable in the \"Changelogs.\"
So, no more back-and-forth emails or delays in granting access.
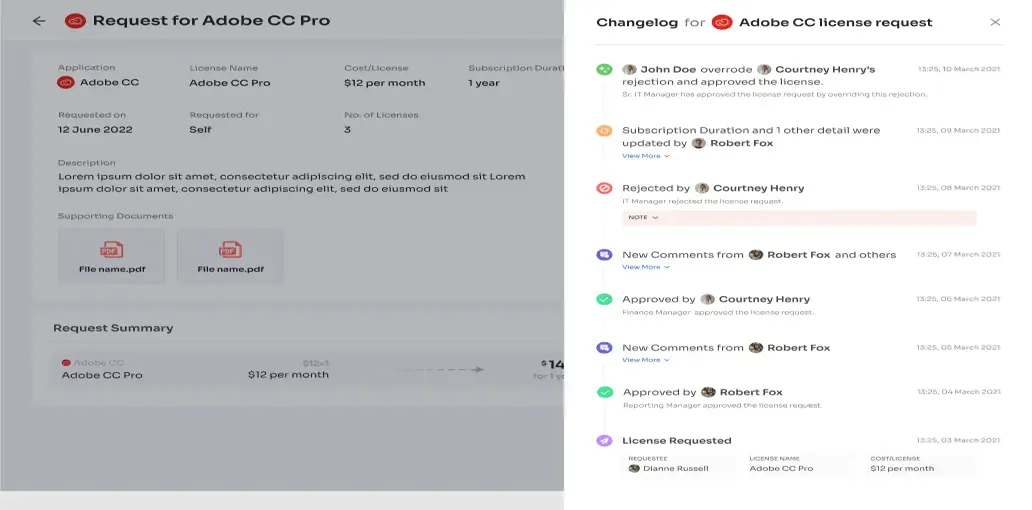
- Revoke Access From The Employees Upon Departure
Revoking access from departing employees or those who no longer require certain application access is a critical task for IT teams. Even a single oversight in this process can potentially lead to security breaches, jeopardizing data security.
Zluri recognizes this concern and provides a solution by automating the deprovisioning process. With just a few clicks, your IT team can effortlessly revoke required or all access from employees without missing any crucial steps. This automation ensures timely and thorough revocation, safeguarding SaaS app data from potential security breaches such as unauthorized attempts.
Furthermore, to automate the process, your team can simply create an offboarding workflow. All they need to do is select the users from whom they want to revoke app access and then they will come across a list of recommended actions (such as signing out users, removing them from org units, and more).
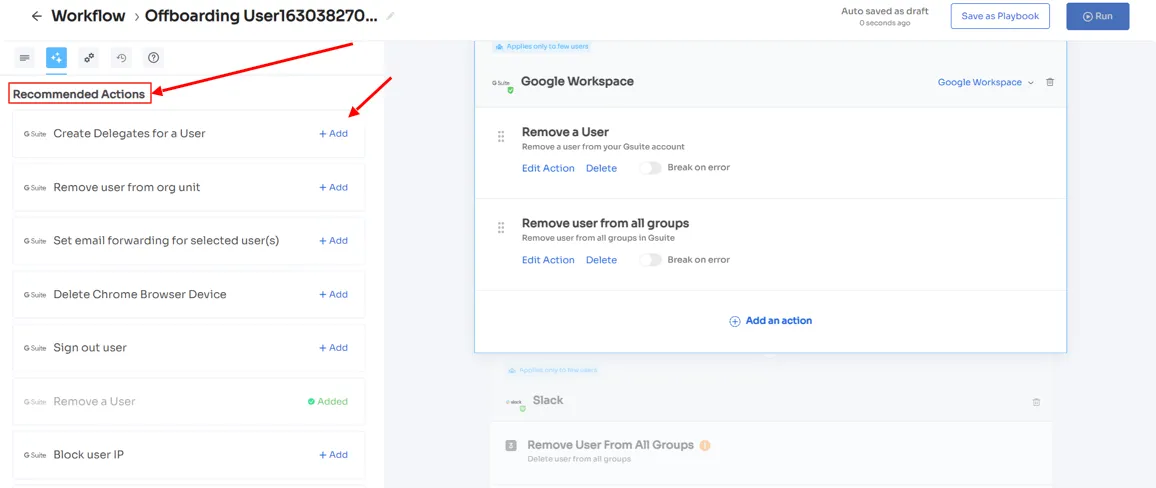
Your team can choose one or multiple actions at once from the list, a point to note is that these actions will be executed post the deprovisioning process. Once all desired actions are added, your team can run the workflow instantly or save it as a playbook for future use.
3. Be Audit Ready By Streamlining Access Certification
Compliance is a top priority for every organization, and Zluri understands that. That's why Zluri's IGA Solution streamlines the access certification process, providing a structured and automated approach to review and validate user entitlements. It is backed by Kuppingercole's report, that Zluri’s IGA ensures access privileges are regularly audited, unauthorized access is detected, and compliance requirements are met.
For example, the IT team has granted access to Kissflow to the finance team to complete a project within 8 months. However, the finance team finished the assigned tasks within 4 months. So the manager or any set reviewers can review the access and revoke the assigned access. Or else, after a compilation of 8 months, Zluri will automatically revoke the access with/without reviewers' intervention.
This was just an overview, Zluri is not only restricted to these few access review capabilities, it has more to offer, which is exclusive and sets it apart from the competitors. So, let’s explore them one by one.
- Unified Access Review
Zluri's unified access review feature allows your IT team to easily determine which users have access to various SaaS apps and data. It gathers these valuable insights from its centralized access directory, where all user access-related data is stored.
With these insights, including user roles (admins or regular users), department information, and more, your IT team can thoroughly review access privileges and ensure they align appropriately with each user's role and responsibilities.
Additionally, Zluri’s activity & alerts capabilities come into play to keep things running smoothly. This feature provides real-time information about the last activities users performed and notifies IT teams about any new logins. With the help of these insights, reviewers can make quick and informed decisions during access reviews, ensuring the right people have the right access at all times.
- Automated Access Review
Zluri simplifies access reviews by fully automating the process. Just log in to Zluri, create a certification, and choose the apps and users you wish to review. From there, the reviewers will conduct the review and update you on the results via email.
By automating this process, you can achieve results that are 10 times better than manual methods and save your IT team's efforts by 70%. Let's explore how this automation works in detail.
- After accessing contextual data through Zluri's unified access feature, your team can take it a step further by establishing access rules based on these insights. For instance, if an individual holds an admin role on Salesforce, you can effortlessly create a review policy designed specifically for that situation.
- Following that, the schedule certification feature comes into play, enabling your team to generate certifications based on the gathered information. This empowers you to take actions aligned with the insights you've obtained. For instance, you can utilize data such as last login, departments, user status (active or inactive), and more to make well-informed decisions during the review process. These decisions may include determining whether the user's current access should be maintained or if any modifications are required. With Zluri's context-rich information, your team can confidently take actions that align with your access management policies. This intelligent and efficient approach ensures that the right users have the appropriate access, all while maintaining data security.
- Secure access orchestration/auto-remediation
After completing the access review, necessary changes will take place as per the set actions during certification creation, so all these actions, like access modification or removal, are part of secure access orchestration. It's the seamless process that ensures access is managed securely and efficiently, safeguarding your organization's data and resources.
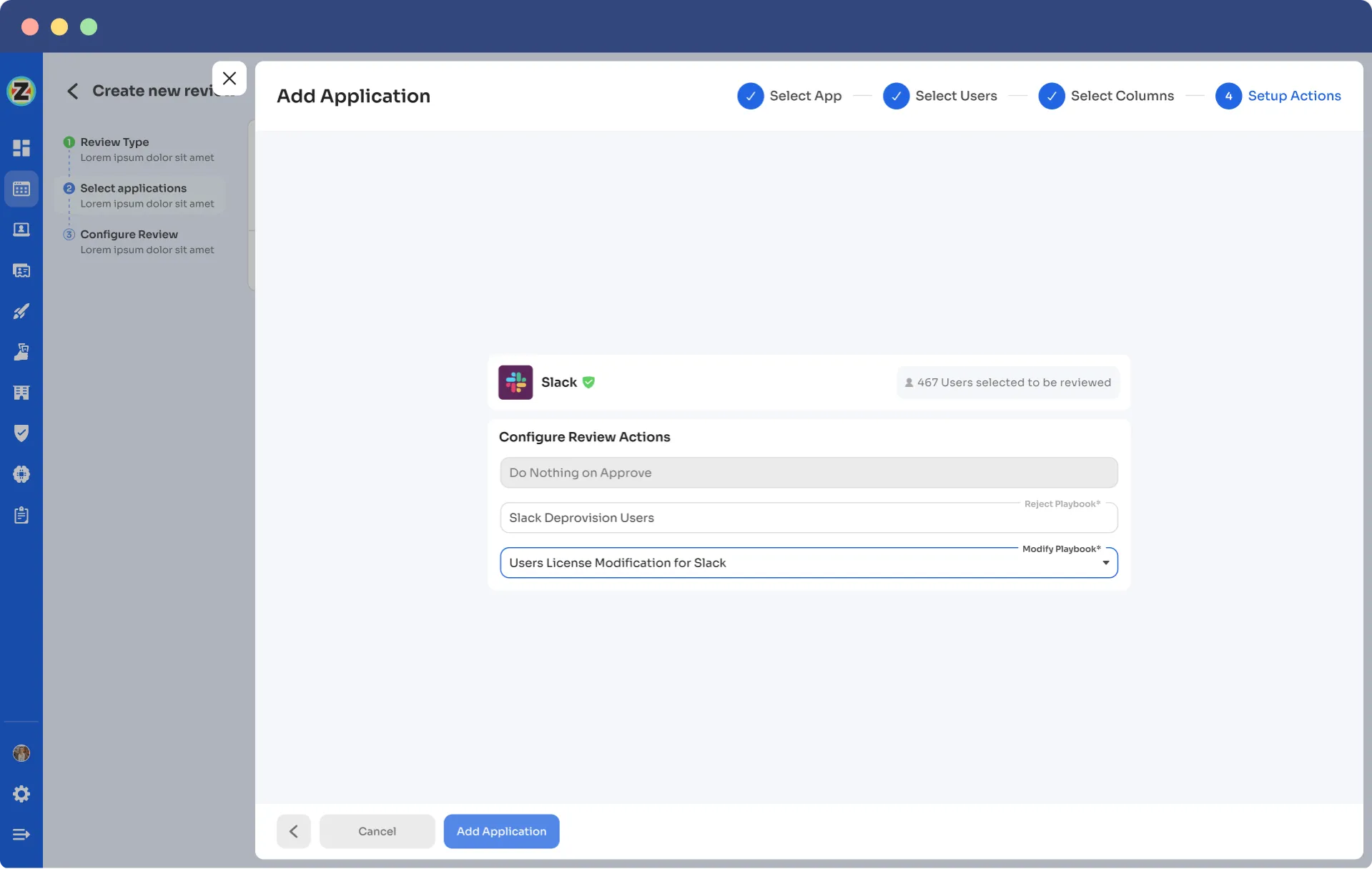
For example, while creating a new certification in Zluri, your team will come across configuration action under which they need to create deprovisioning playbooks and modification playbooks. If the reviewers decline the access permissions, then automatically, the deprovisioning playbook will run, and the same goes for the modification playbook. Also, for both scenarios, the reviewers need to provide relevant reasons stating why the access permission is declined or modified.
Point to note-These actions will take place automatically post the review; that's why this process is also known as the auto-remediation process.
Furthermore, Zluri also offers integration features that are quite beneficial at the time of gathering access data. By leveraging these integrations, Zluri enhances the access review process and improves the overall security posture of the organization.
For instance, when reviewing critical components like the Identity System and core applications, Zluri seamlessly integrates with platforms such as Salesforce, Okta, Azure, and others. These integrations play a vital role in gathering crucial data from the identity system and SaaS apps, providing valuable insights, and streamlining the review process.
Also, Zluri generates reports that are commonly associated with audit logs or audit trails. These audit reports serve as valuable documentation to share with auditors or keep as a reference for future reviews. And, audit trails act as roadmaps, showcasing the changes made during previous reviews.
For instance, if an employee's access level was downgraded from admin to user, it becomes crucial to review and ensure that the access remains appropriate, or if there were any subsequent changes back to admin. Understanding the reasons behind such upgrades is essential for maintaining proper access control.
So Zluri automatically generates reports on such changes, which further helps in the reviewing process.
So what are you waiting for? Book a demo now and check yourself how Zluri can be a game-changing solution for you.







.png)

.svg)














