Outdated. Incomplete. Unreliable. If that describes your current review reports, it's not just a reporting issue—it's a risk issue.
Whether you're preparing for SOX 404, PCI DSS, SOC, HIPAA, or GDPR audits, one thing is non-negotiable – your access review reports must prove that your internal controls and security practices are working as intended.
Most organizations try to get their reports right the first time. But, despite their best efforts, many still fall short, not because of negligence, but because they rely on a traditional approach to generate review reports.
Reviewers are stuck juggling spreadsheets, tracking:
- Which apps are they reviewing?
- Which identity’s access permissions are they checking?
- What actions have they taken?
All while trying to meet deadlines.
This opens the door to human error, such as entering incorrect usernames, assigning wrong roles, missing permissions, or undocumented remediation actions. In a fast-moving SaaS environment, where users and applications are constantly changing, manual reporting only adds complexity.
The solution? Next-gen IGA platforms that automate identity governance reporting and deliver audit-ready reports – without the chaos. Let’s explore how.
Identity Governance Reporting Features That Help Generate an Audit-Ready Report
Here's the breakdown of the core identity governance reporting features that will help you generate reliable, audit-ready reports – without any manual hassle or risk of oversight.
%202.png)
Note: We’ll use Zluri’s next-gen IGA platform as a real-world example to show what modern reporting capabilities look like in action.
1. Auto-Generates User Access Review Reports
Once a user access review cycle is complete, next-gen IGA solutions like Zluri step in to take the reporting burden off your team’s shoulders.
Instead of spending hours collecting scattered data across systems, Zluri automatically generates a detailed, audit-ready user access review report that covers everything reviewers care about:
- Which applications were reviewed
- The list of users whose access permissions were evaluated
- Key user attributes considered during review (like job title, department, account type, employment status, and more)
- The remediation actions (approve, revoke, modify access) marked by the reviewer
- The completion status of each remediation action (which acts as proof that necessary measures were taken to close access gaps)
What’s even better is that Zluri gives you the flexibility to customize the columns and data points in your review reports.
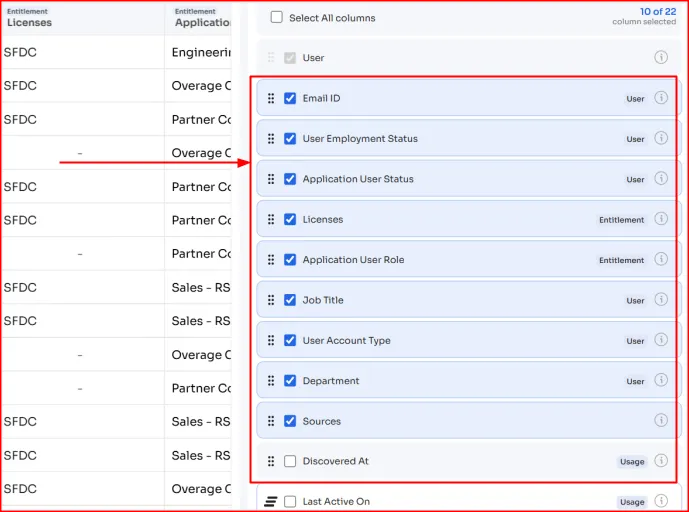
Want to add a specific attribute or highlight only certain insights? Go ahead. Once done, Zluri will show those selected columns in your user access review report.
Zluri lets you present a curated view of accurate, complete, and up-to-date data that is relevant for auditors and easy to understand (in the right format) – no clutter, no fluff.
2. Restricts Unauthorized Users From Making Changes To The Review Reports
Zluri auto-generates user access review reports in a read-only format, making them tamper-proof once finalized.
No one, not even reviewers, can alter data post-report generation.
This ensures that what auditors see is a true, unmodified record of your review campaign.
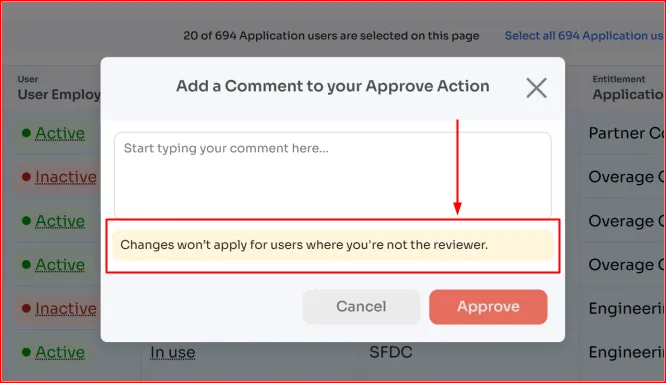
Zluri also safeguards the integrity of reviews during the campaign. Each reviewer is restricted to their assigned scope. They can only act on the users they're responsible for.
- For example, the marketing head can review access for marketing users only, while the finance head is limited to finance users. These role-based controls ensure that reviewers can't interfere with each other's assignments, whether intentionally or unintentionally.
The result?
- Your final report reflects clean, unbiased, and traceable data, giving auditors full confidence in the integrity of your review process.
3. Provides Pre-Review Reports to Strengthen Audit Evidence
Zluri doesn’t just generate the ‘user access review report’ – it also generates ‘supplementary reports’ that you can use as supporting evidence to enhance the credibility of your review report.
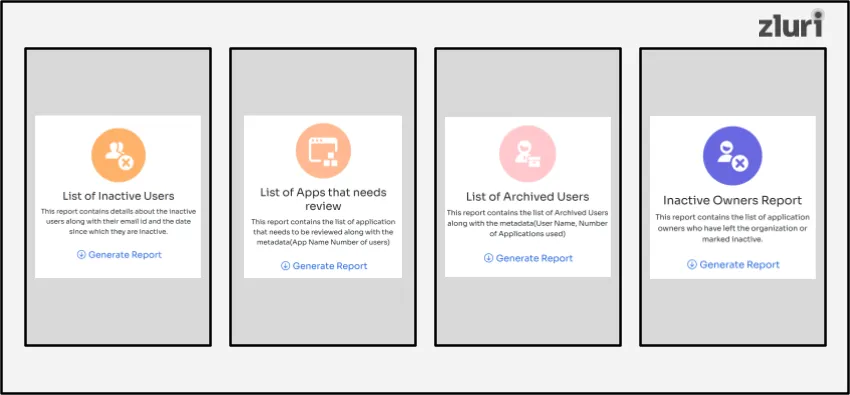
But what type of supplementary reports does Zluri generate? It generates the following reports that you attach alongside your access review reports:
- List of inactive users report
- List of apps that need a review report
- List of archived users report
- Inactive owners report
How is this going to help? These baseline reports will act as your “before” snapshot – a clear view of irregularities or access gaps that exist before the actual review is conducted.
Note: You have to generate the supplementary reports before conducting the review.
After that, once the review is complete, you generate a user access review report that highlights the actions taken – such as revoking access for inactive users, removing orphaned accounts, or modifying permissions for archived users.
Now, by combining the pre-snapshot and post-review reports, you can present a comprehensive picture of your governance efforts. It will clearly show that you didn’t just review the permissions — you identified access misalignments and took corrective action. This kind of evidence-backed reporting helps gain the trust of compliance auditors.
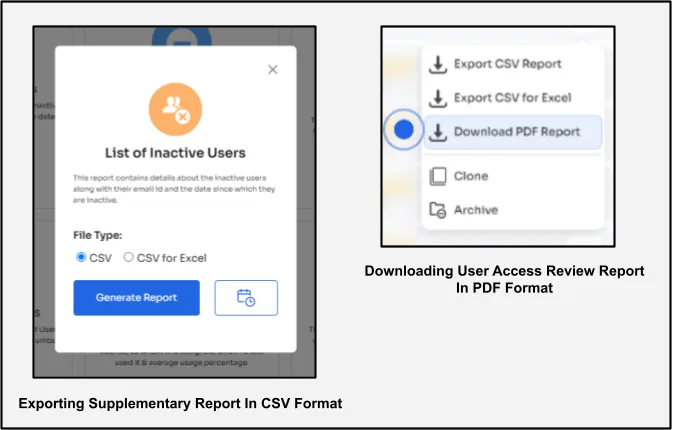
4. Exports Reports In Multiple Auditor-Friendly Formats
Zluri allows you to export supplementary reports in CSV or Excel format and enables you to download user access review reports in PDF format, making it easier to share with compliance auditors.
Customer testimonials
“With Zluri, you can instantly download reports in PDF or CSV that clearly show what access was reviewed, who approved, who modified, and when.”
Generate Reports That Prove Your Controls Work
Restricting who can modify reports or enabling auto-generation isn’t enough. To truly satisfy auditors, your reports must demonstrate that your access controls are not only in place but also working effectively.
If you’ve enforced strict access policies and conducted proper reviews, that should be evident in the report. It should clearly show that access anomalies were detected, remediated, and that your internal controls are reducing risk – not just ticking boxes.
Because at the end of the day, auditors don’t just want to see effort. They want evidence that your governance program is doing what it claims to do.
Also Read: IT Compliance Audit









.svg)














