By implementing robust security practices, such as separation of privilege, IT managers can proactively defend against potential attacks and mitigate the impact of security breaches on their organizations.
The Separation of Privilege (SoP) principle is a fundamental concept in information security that focuses on dividing system privileges or access rights among multiple entities. The principle aims to reduce the risk of unauthorized access and limit the potential damage caused by compromised credentials or insider threats. By implementing SoP, you can enforce strict access controls, prevent privilege escalation, and enhance overall system security.
The SoP principle involves the division of system privileges or access rights to ensure that no single entity possesses all the necessary permissions to compromise the security of a system or access critical resources. It emphasizes the importance of granting privileges on a need-to-know and need-to-access basis, limiting access to only what is essential for performing specific tasks.
For instance, consider a company's file-sharing platform. To apply the SoP principle, the system is structured so that employees have different levels of access based on their roles and tasks.
- Regular Employee: Employees can upload and access files within their department folders. They can't delete files or access files from other departments.
- Department Manager: Department managers have the ability to delete and modify files within their own department folders. However, they can't view or modify files in other department folders.
- System Administrator: System admins can manage user accounts, configure security settings, and perform system-wide maintenance. However, they don't have direct access to the content of individual files unless explicitly granted.
By enforcing this separation of privileges, you can rest assured that employees can only access the files necessary for their tasks, reducing the risk of unauthorized access or data leakage. Even if an employee's account is compromised, the potential damage is limited due to the restricted access imposed by the SoP principle.
Examples of Separation of Privilege Enhancing Security & Efficiency
Here are a few examples showing how the separation of privilege boosts security and efficiency.
1. Role-based access control (RBAC) implementation and its benefits: RBAC is a widely used approach to implementing separation of privilege. By assigning roles to users and defining their permissions based on those roles, your team can ensure that individuals have access only to the resources necessary for their job function. RBAC simplifies access management, improves security, and enhances efficiency by eliminating the need for individual access control lists.
2. Use of virtualization and sandboxing to isolate systems and applications: Virtualization and sandboxing technologies provide a way to separate systems and applications from each other, limiting the potential impact of a compromised system or application. By isolating resources, you can enhance security and efficiency by preventing unauthorized access or actions that could disrupt critical services or compromise sensitive data.
3. Real-world scenarios showcasing the advantages of separation of privilege: Consider an e-commerce platform where customer support representatives need access to customer order information, not financial data or administrative settings. By implementing separation of privilege, your IT team can ensure customer support representatives have access to fulfill their duties without exposing sensitive financial data or risking accidental changes to administrative settings.
4. Comparisons with organizations lacking privilege separation and its impact: Organizations that lack separation of privilege often face higher security risks and operational inefficiencies. Without well-defined access controls, there is a greater likelihood of unauthorized access, data breaches, and misuse of privileges.
Additionally, managing access becomes more complex, leading to administrative overhead and potential delays in granting access to authorized users.
Benefits of Separation of Privilege
The SoP principle offers several benefits to your organization that can be implemented as part of its security strategy.
1. Enhanced security through restricted access & reduced risk of breaches
Enhanced security is crucial, and restricted access plays a key role. By limiting individual account and system privileges, you can reduce the attack surface and make it harder for malicious actors to exploit vulnerabilities.
In the event of a compromised account or system, restricted access helps contain the damage. Even if one account is breached, it doesn't grant access to other sensitive resources, minimizing the impact of a breach and preventing unauthorized access.
Restricted access ensures that only authorized individuals or processes can perform specific actions, preventing unauthorized users from infiltrating systems or causing security incidents. It adds an extra layer of protection for sensitive information.
Real-world case studies, such as the principle of least privilege, show the benefits of restricted access. Granting minimum privileges necessary for tasks reduces the risk of compromised accounts causing extensive damage, enhancing security and protecting your organization’s sensitive information.
2. Improved efficiency through fine-grained access control
Fine-grained access control enables precise customization of access permissions, ensuring that users only have access to resources essential to their roles. This tailored approach empowers employees to focus on core tasks, slashing wasted time and skyrocketing efficiency.
But the benefits don't stop there. Fine-grained access control fortifies data integrity and shields sensitive information from unauthorized eyes by significantly reducing the risk of errors and accidental data exposure.
Say goodbye to the tangled web of individual access controls. With the brilliance of separation of privilege, access management becomes a breeze. Complexity fades away by grouping permissions based on roles or departments, freeing up your IT admin to tackle strategic initiatives and drive productivity.
And that's not all! Approval processes become streamlined with automated workflows, granting access based on predefined roles and responsibilities. No more manual approval bottlenecks—employees swiftly access the resources they need, propelling operational agility and giving your organization a competitive edge.
Potential Challenges of Separation of Privilege
When implementing the separation of privilege principle in an organization, several potential challenges need to be considered. These include:
- Administrative overhead and complexity in managing privileges: Implementing separation of privilege requires establishing and managing different access levels for various organizational personnel or roles. This can result in increased administrative overhead and complexity, as it involves setting up and maintaining access control mechanisms, monitoring access rights, and responding to access requests.
- Dependencies on specific personnel or roles: Separation of privilege often relies on specific individuals or roles having unique access to critical systems or information. This dependency can become a limitation if these individuals are unavailable or their roles change. Establishing contingency plans and mechanisms to address such situations is crucial.
- Potential conflicts and difficulties in determining appropriate access levels: Determining the appropriate access levels for different personnel or roles can be challenging. Striking a balance between granting sufficient privileges to enable job functions and minimizing the risk of unauthorized access requires careful consideration and ongoing evaluation.
- Balancing user convenience with security measures: Strict separation of privilege can sometimes impede user convenience by introducing additional steps or restrictions in accessing certain resources. Finding the right balance between user convenience and security measures is essential to ensure the smooth operation of business processes while maintaining adequate security.
Addressing potential issues of Separation of Privilege
To mitigate the potential issues associated with the separation of privilege, organizations can implement the following strategies:
- Developing contingency plans for key personnel absence: You should have contingency plans in place to address the absence of key personnel. This can involve identifying backup roles or personnel who can temporarily assume critical access privileges to ensure continuity of operations.
- Implementing backup roles and cross-training employees: Cross-training employees and establishing backup roles can help mitigate the risk associated with dependencies on specific individuals. You can reduce the impact of personnel changes or unavailability by ensuring that multiple personnel can perform critical tasks.
- Automating access management processes to reduce dependencies: Automation can help minimize dependencies on specific personnel by streamlining access management processes. Implementing automated systems for granting, revoking, and monitoring access can reduce administrative overhead and enhance efficiency while ensuring proper privilege separation.
- Regularly reviewing and updating privilege separation policies: It is essential to regularly review and update privilege separation policies to reflect changes in personnel, roles, or technology. Conducting periodic audits and assessments can help identify gaps or inconsistencies in access controls and enable organizations to take corrective actions.
Effective Approaches for Successful Implementation of Separation of Privilege
Balancing security requirements with operational efficiency and user experience is crucial for successfully implementing separation of privilege. Here are some approaches you can adopt:
- Collaborative efforts between security and operational teams: Close collaboration between security and operational teams is vital to strike a balance between security requirements and operational efficiency. By involving all stakeholders in the decision-making process, you can ensure that security measures do not overly impede operational effectiveness.
- Conducting risk assessments to determine the level of separation needed: Performing regular risk assessments helps you identify and prioritize areas where separation of privilege is most critical. This enables them to allocate resources effectively and implement appropriate access controls based on the risk level associated with different systems or information.
- User education and awareness programs to promote understanding of security measures: Educating users about the importance of security measures and the rationale behind privilege separation can help foster a culture of security within the organization. Training programs and awareness campaigns can promote user compliance and facilitate the acceptance of security measures without significant resistance.
- Implementing user-friendly access control mechanisms to minimize friction: User experience should not be sacrificed for the sake of security. You should strive to implement user-friendly access control mechanisms that minimize friction while still maintaining effective separation of privilege. This can include techniques such as single sign-on, contextual authentication, or adaptive access controls that adapt to user behavior.
Overall, an identity governance and administration (IGA) platform can provide a unified solution for managing user identities, access privileges, and ensuring compliance with the separation of privilege principle. It helps you enhance security, streamline access control, and maintain efficient governance over user access, mitigating risks and ensuring adherence to security best practices. One such platform is Zluri.
Enhancing Separation of Privilege Security Principle with Zluri's IGA Capabilities
Zluri's IGA capabilities elevate the effectiveness of the separation of privilege security principle by providing a comprehensive and AI-powered solution to manage access privileges across the organization. Through advanced AI algorithms and anomaly detection mechanisms, Zluri identifies and addresses potential security risks related to access control in real-time.
With Zluri, access reviews, and evaluations go beyond simple periodic assessments. The platform enables continuous monitoring of access patterns, user behavior, and system logs, allowing for immediate detection of any unusual or suspicious activities. This proactive approach ensures that any deviations from established access norms are quickly flagged, helping your team take swift action to mitigate risks.
By leveraging Zluri's AI-driven insights and recommendations, your team can make well-informed decisions about access controls. This ensures that each user or role has precisely the privileges they require to fulfill their responsibilities and no more. The principle of least privilege is effectively enforced, reducing the attack surface and potential impact of security breaches.
Furthermore, Zluri streamlines the compliance process by aligning access controls with relevant industry regulations and standards. This helps meet organizational compliance requirements and strengthens their security posture. The AI-driven capabilities provide continuous monitoring and automated reporting, simplifying the auditing process and promptly identifying and addressing compliance gaps. Let’s explore this in detail:
Discover the power of Zluri's cutting-edge discovery engine
Zluri uses 9 discovery methods to gain complete visibility into your organization's SaaS landscape. These methods include browser agents, IDPs & SSO, direct integrations, desktop agents, active directories, HRMS platforms, MDM platforms, finance systems, and CASB platforms. This empowers your team to identify and manage SaaS applications effectively.

Zluri’s nine discovery methods
What sets Zluri apart is its commitment to going above and beyond. Seamlessly integrating with over 300 SaaS applications, the platform delivers real-time data, invaluable insights, and AI-powered alerts to keep you well-informed. The API-based integrations guarantee comprehensive data discovery across all your SaaS applications, ensuring no valuable information remains hidden.
Notably, Zluri has extensive app library allowing for in-depth exploration of user permissions and access levels within your SaaS ecosystem. This level of detail comprehensively understands the intricacies of your SaaS environment, providing a powerful tool for your organization.
Unlock efficiency & strengthen security with Zluri's advanced automation engine
Zluri’s automation engine frees your teams from the tedious burden of manual access management, enabling them to embrace streamlined processes that boost efficiency and strengthen security measures.
Zluri's automation engine goes beyond traditional user access management. It takes on the multifaceted task of optimizing the entire user lifecycle. All these tasks are seamlessly handled, from granting appropriate access to dynamically adjusting permissions based on evolving roles and securely revoking access when needed.
By entrusting these critical aspects to Zluri's automation engine, your IT team can maintain flawless operations while ensuring the utmost protection of your organization's invaluable SaaS app data. Welcome a new hassle-free and secure access management era with Zluri's cutting-edge automation engine.
Streamlining onboarding with Zluri’s IGA solution
Zluri understands the importance of a seamless onboarding process that benefits the organization and creates a positive experience for new employees. With intelligent lifecycle management capabilities, you can say goodbye to the hassles of manual onboarding and hello to increased productivity and efficiency.
One of the standout features of Zluri is its ability to create customizable onboarding workflows, which act as playbooks for specific roles or departments. These workflows can be reused whenever needed, saving you valuable time and effort. Zluri's exceptional reusability and flexibility through playbooks empower you to create a streamlined onboarding process that fosters consistency across your entire organization. By harnessing Zluri's playbooks, you establish a strong foundation for effective onboarding, fostering a sense of belonging and engagement among new employees from day one.
Never again worry about last-minute rushes with Zluri's scheduled task management. You can plan and schedule tasks in advance, ensuring everything is set up and ready for the new employee's first day. This proactive approach eliminates unnecessary stress and ensures a smooth onboarding experience.
Zluri's 'contextual app recommendations' and in-app suggestion feature taking your onboarding process to the next level. Even before a new employee joins, Zluri suggests relevant applications based on their department and role. With this foresight, you can prepare for their needs in advance, allowing for a seamless transition from day one.
Streamlining offboarding with Zluri’s IGA solution
One of the standout benefits of using Zluri is its automatic revocation of access to all devices, apps, and systems when an employee departs. Zluri promptly disables their access, preventing any unauthorized entry to sensitive information. This proactive approach ensures that former employees cannot access company resources, significantly reducing the risk of data breaches or security incidents.
Zluri also takes care of data backup and transfer to a new owner, mitigating the risk of essential data being lost during the deprovisioning process. This feature ensures that critical information is securely handed over to the appropriate personnel, facilitating a smooth transition even after an employee's departure.
In addition to data protection, Zluri simplifies employee license revocation and eliminates single sign-on (SSO) access. By doing so, the platform effectively blocks the ex-employees usage of any organization's applications, further ensuring data security and preventing potential misuse of company resources.
By adopting Zluri's straightforward approach to employee offboarding, your teams can ensure consistent and secure deprovisioning for all departing employees. This level of efficiency and security allows HR and IT teams to handle departures with ease and confidence, reducing the burden of administrative tasks and providing peace of mind during potentially sensitive situations.
Streamlined access request management with Zluri's self-serve model
Simplifying access permissions during employee transitions is a critical challenge for organizations. Balancing the need for employees to have appropriate access for their roles while safeguarding sensitive data from unauthorized use requires a robust solution. Thankfully, Zluri's groundbreaking self-serve model, the Employee App Store (EAS), is here to revolutionize access request management, ensuring efficiency and security.

Bid farewell to manual processes for managing permissions. Zluri's EAS empowers both team members and approvers to seamlessly review and approve access requests tailored to specific job roles. This level of granularity ensures employees have precisely the right access they need, preventing unnecessary exposure to sensitive information.
With Zluri, you gain unmatched control over access privileges, establishing a secure environment within your organization's boundaries. The cutting-edge technology allows you to effortlessly safeguard critical data, mitigating the risk of unauthorized access while retaining full control over accessible tools and resources.

The EAS employs a robust approval system with three distinct levels: app owners, reporting managers, and IT admins. This multi-tiered approach enables higher authorities to override decisions made by lower-level admins or managers, facilitating swift and decisive action when needed. Access request approvals and rejections come with explanations and comments, promoting collaboration and clarity within the organization's access management process.
But that's not all! Zluri's intelligent solutions enable approvers to modify specific access requests, precisely tailoring permissions to the organization's unique requirements. To keep stakeholders informed, Zluri's IGA solutions offer a comprehensive "changelog" feature. This allows users to track updates, from approvals and rejections to license duration or tier changes.
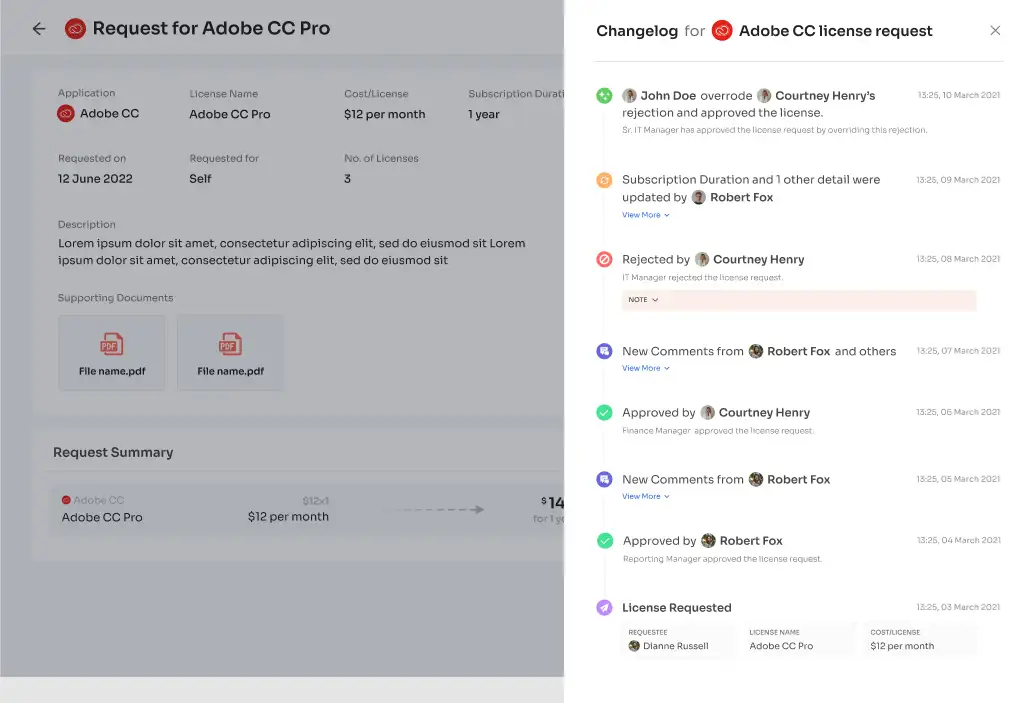
The changelog captures valuable insights, including comments added by any admin, fostering a collaborative and well-informed approach to access management. With Zluri's EAS, managing access requests has never been more efficient, transparent, and secure, empowering your team to navigate employee transitions with confidence.
Revolutionize access certifications with Zluri's IGA
Zluri's IGA solution transforms access reviews by embracing automation, saving valuable time. What was once a burdensome and time-consuming process is now seamlessly streamlined, empowering admins to focus on essential tasks that drive your company's mission.
With Zluri's IGA solution leading the review process, you'll experience an astonishing tenfold increase in review efficiency, eliminating the need for laborious manual reviews and ushering in lightning-fast access assessments.

Harness the power of Zluri's IGA to achieve unparalleled review efficiency, bidding farewell to manual reviews and welcoming swift access assessments. This transformation allows your team to dedicate more time and resources to your company's core objectives, enhancing productivity and overall success.
Not just that, Zluri offers unified access and automated review mechanisms that strengthen security, minimize the likelihood of data breaches, and effectively handle user access privileges. Their powerful features expedite access reviews tenfold and reduce effort by 70%, enabling you to streamline access management processes. This translates to more resources and time to drive growth and foster innovation within your organization. Let's explore how Zluri revolutionizes the process of access reviews.
1. Automated access reviews
Zluri provides a seamless and efficient process for evaluating user access rights. Zluri’s intelligent automation evaluates by defining specific review parameters, selecting reviewers, and scheduling campaigns, eliminating the need for manual reviews. This not only saves time but also reduces the risk of errors.

Beyond traditional access reviews, Zluri goes the extra mile by incorporating auto-remediation capabilities. The system automatically takes corrective actions for immediate resolution whenever access violations are detected. This proactive approach enhances the organization's security posture, effectively addressing potential risks and ensuring compliance. Zluri's swift actions help prevent security breaches and unauthorized access attempts.
Zluri's IGA system also includes a robust mechanism to promptly revoke access for terminated employees or individuals with outdated privileges. By automatically disabling access, Zluri reduces the likelihood of sensitive information falling into the wrong hands, mitigating the risk of unauthorized data breaches and safeguarding the organization's valuable assets.
Moreover, Zluri facilitates the generation of auto-generated reports that offer clear and concise overviews of access reviews. These reports provide valuable insights into access patterns, potential vulnerabilities, and compliance status. Leveraging these auto-generated reports allows organizations to easily demonstrate compliance to auditors and regulatory bodies.
2. Agile access reviews
Agile access reviews play a crucial role in minimizing the possibility of unauthorized access and potential data breaches. Zluri's IGA presents a unique method for access reviews that enhances both security and compliance. Let's explore how this system reinforces security measures through agile access reviews.
With Zluri's IGA, you can maintain control over access privileges through recurring certifications. These certifications ensure that access privileges undergo consistent and frequent evaluations. By continuously assessing access rights, you can quickly identify and address any potential security gaps that may arise. This proactive approach significantly strengthens security measures and reduces the risk of unauthorized access.
Zluri's IGA solution also facilitates planned and scheduled certifications at predefined intervals. This systematic approach ensures that access privileges receive consistent and timely evaluations. Adhering to this schedule minimizes the likelihood of overlooking critical access issues, and security vulnerabilities can be promptly addressed.

Furthermore, Zluri offers certificate templates that align with industry best practices and regulatory standards. This streamlines the certification process, making it easier for you and your team to carry out certifications efficiently. Utilizing these templates ensures a thorough and accurate certification process that aligns with industry standards.
3. Real-time access reviews
Zluri's IGA distinguishes itself through the integration of artificial intelligence (AI) to revolutionize access reviews and simplify compliance procedures. By harnessing advanced AI features, Zluri enhances data security and delivers real-time access insights, ensuring your organization remains protected and compliant.
Through the utilization of AI-driven anomaly detection algorithms, Zluri continuously examines real-time access patterns, user behavior, and system logs. This proactive approach allows for the swift detection of unusual or potentially risky activities, empowering you to identify security threats promptly and take immediate action to safeguard sensitive data. This vigilant approach fortifies your security posture, minimizing the impact of potential breaches.
With Zluri, access reviews transcend periodic assessments, as the platform supports continuous monitoring and evaluations, providing real-time visibility into access privileges. You can stay informed about any changes or potential access-related issues, enabling you to address concerns promptly and proactively reduce the risk of unauthorized access or misuse.
Zluri's AI compliance capabilities offer intelligent insights and recommendations, aiding in adherence to industry regulations and standards. By aligning access controls with relevant requirements, Zluri helps decrease the risk of compliance violations. Leveraging the power of AI technology, Zluri streamlines the compliance process, simplifying your organization's ability to meet regulatory obligations.

Wondering how to automate user access reviews? Zluri’s comprehensive ‘Access certification’ module has got you covered:
- Step 1: To automate access reviews, access Zluri's main interface and navigate to the "Access certification" module. Within the module, select the option to create a ‘new certification.’
- Step 2: Assign a name to the certification and designate an owner who will oversee the automated access reviews.
- Step 3: Choose the preferred method of reviewing user access by exploring the options: Application, Users, and Groups.
- Step 4: Opt for the "Application" review method if desired and add the relevant application(s) to be audited for users' access.
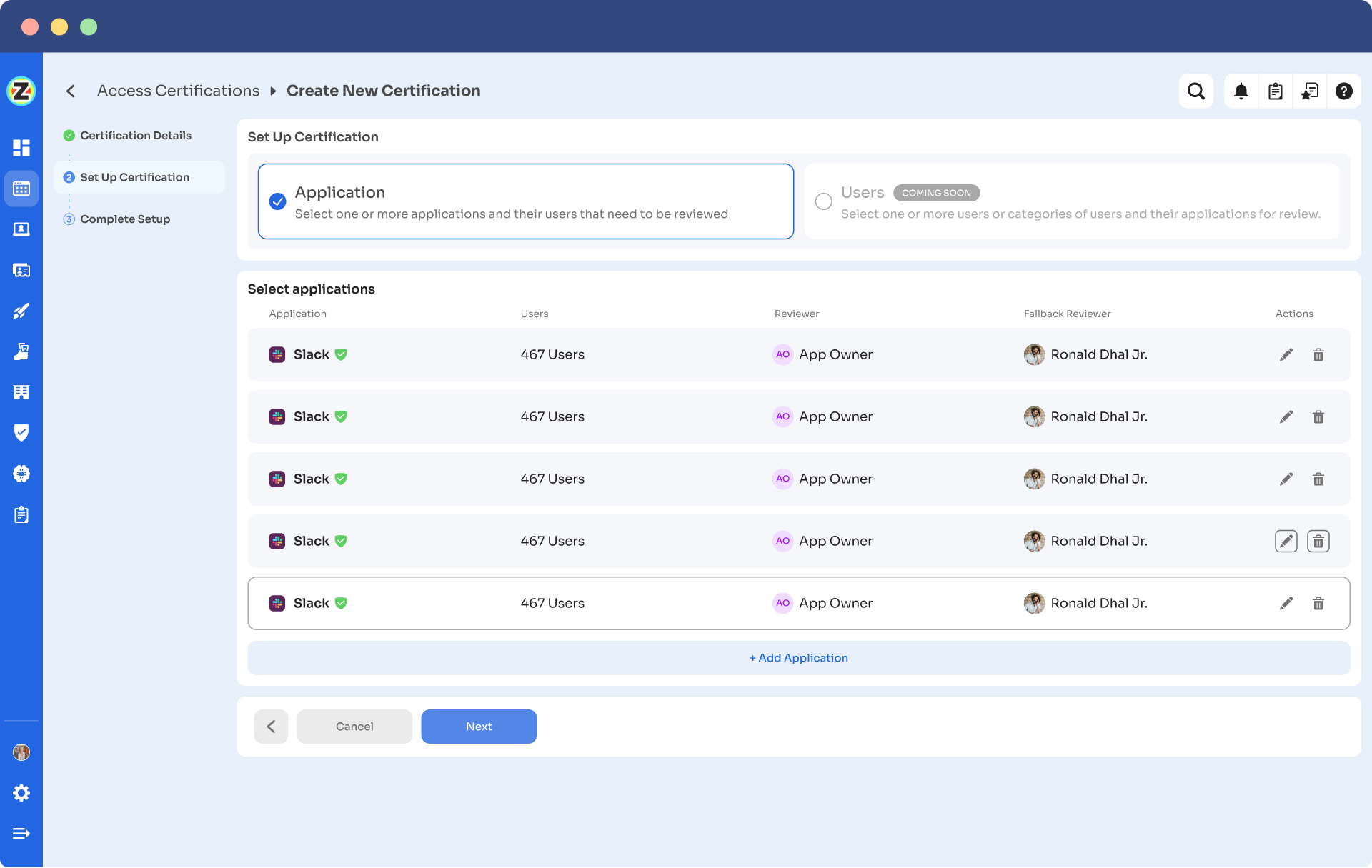
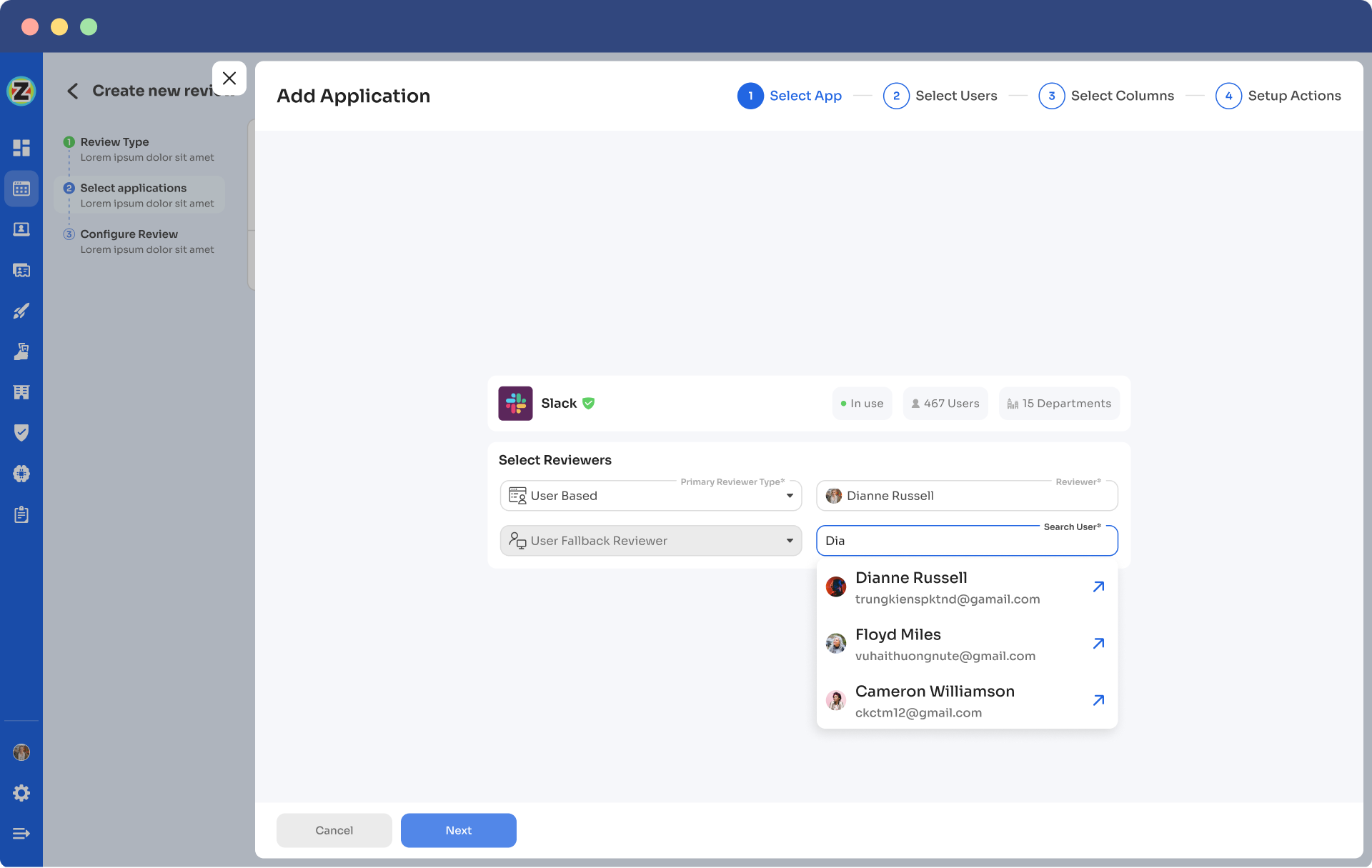
- Step 5: Select a primary reviewer and a fallback reviewer from the dropdown menu for the automated access reviews.
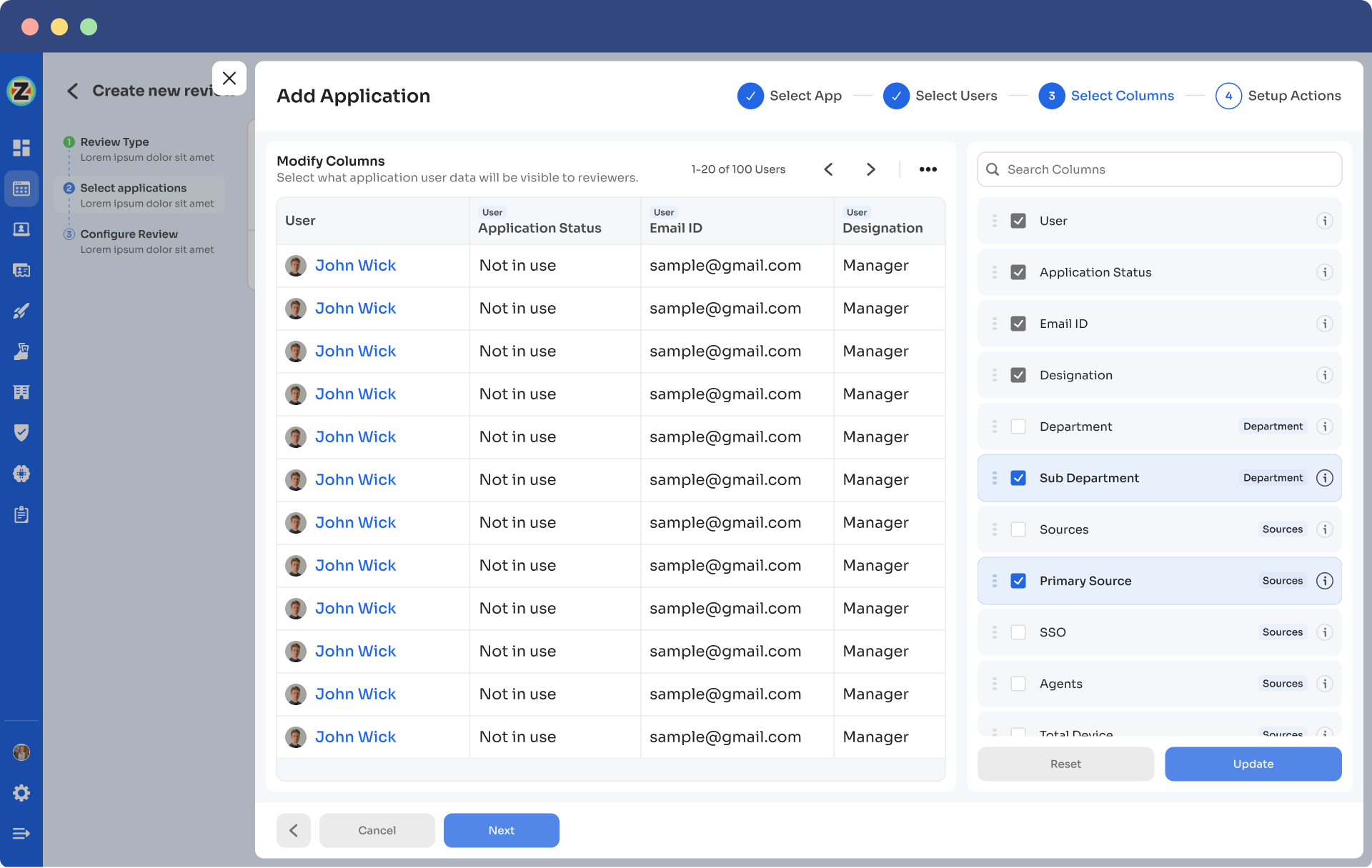
- Step 6: Select the users to be included in the automated access reviews process and apply data filtering to refine the user selection based on certification requirements.
- Step 7: Proceed to the next step and configure the actions to be performed during the automated access reviews, choosing from the provided dropdown list of actions.Note: If there are multiple applications to be included in the same certification, repeat the process of adding applications as needed.
- Step 8: Specify the start and end dates for the automated access certification process, ensuring they align with recurring or scheduled certifications.
- Step 9: Save the configuration as a template for future use by clicking on the "Save Template" option.
- Step 10: Monitor the progress and updates of the automated access review process for the specific certification by regularly checking the "Review Stage" section.
Unlock the power of Zluri's IGA solution to efficiently handle user access, ensure compliance, and safeguard sensitive data, leading to overall success and tranquility in today's intricate digital environment. Don't hesitate any longer – schedule a demo now and embark on the path to enhanced security and peace of mind!









.svg)



.svg)
.svg)
.svg)
.svg)

.svg)

.svg)

.svg)
















.webp)







.webp)
.webp)





.webp)