An organization may create service accounts for different purposes, such as automated processes, integrations, etc. However, as the number of systems and applications grows, manually tracking these accounts becomes complex and error-prone. Thus, having service account management software will help you overcome these challenges. This article will explore the top service account management solutions that can benefit your business.
A service account management tool provides a centralized platform for creating, managing, and monitoring service accounts. As an IT manager, you can use this tool to automate the provisioning and deprovisioning of service accounts. This ensures that access is granted only to authorized users and systems.
By implementing a service account management tool, you can streamline your operations, reduce the risk of security breaches, and improve overall efficiency. Moreover, with better visibility and control over service accounts, you can mitigate risks, ensure regulatory compliance, and focus your resources on strategic initiatives rather than facing issues related to account management.
In addition, with features like automated provisioning workflows, role-based access control, and password rotation policies, these tools enable you to enforce security best practices consistently across all service accounts.
Let’s explore the features to look for in a service account management solution.
Key Features to Look For in a Service Account Management Tool
As an IT manager, selecting the right service account management tool is crucial for maintaining security and efficiency within your organization. Here are some essential features to consider when evaluating different options:
Role-based Access Control (RBAC): Look for a tool that offers granular control over user permissions based on their roles and responsibilities. RBAC helps ensure that only authorized individuals can access sensitive service accounts, reducing the risk of unauthorized access and data breaches.
Password Rotation and Management: An effective service account management tool should automate the process of regularly rotating passwords for service accounts. This helps mitigate the risk of credential theft and ensures that compromised passwords are quickly invalidated.
Audit Trails and Reporting: Comprehensive audit trails and reporting capabilities are essential for maintaining visibility into account activities. Choose a tool that logs all account actions and provides detailed reports, enabling you to track changes, troubleshoot issues, and demonstrate compliance with regulatory requirements.
Integration Capabilities: Look for a tool that seamlessly integrates with your existing IT infrastructure. This includes directory services, identity management solutions, and other security tools. Integration ensures smooth deployment and enables centralized management of service accounts across your organization.
Automated Provisioning and Deprovisioning: Streamline the process of access provisioning and deprovisioning service accounts with automation capabilities.. An efficient tool should allow you to create templates for account configurations, automate account provisioning based on predefined rules, and promptly deactivate accounts when they are no longer needed.
Credential Vaulting and Encryption: Ensure that the tool provides secure storage for service account credentials, utilizing encryption to protect sensitive information. Vaulting credentials reduces the risk of exposure and unauthorized access, especially in environments where multiple administrators manage service accounts.
Compliance and Certification: Choose a tool that adheres to industry standards and regulatory requirements relevant to your organization, such as PCI DSS, HIPAA, or GDPR. Verify that the tool offers service account governance that has undergone independent audits and certifications to validate its security and compliance posture.
Now, we will explore the various service account management tools along with its features. But, before discussing the tools, let us introduce Zluri, who we are and what we do.
0. Zluri: Gain control over access to service accounts effectively
Managing service accounts efficiently is important for ensuring security and compliance. Zluri offers a comprehensive solution tailored to streamline service account management, using nine discovery methods to identify these critical accounts across your infrastructure.
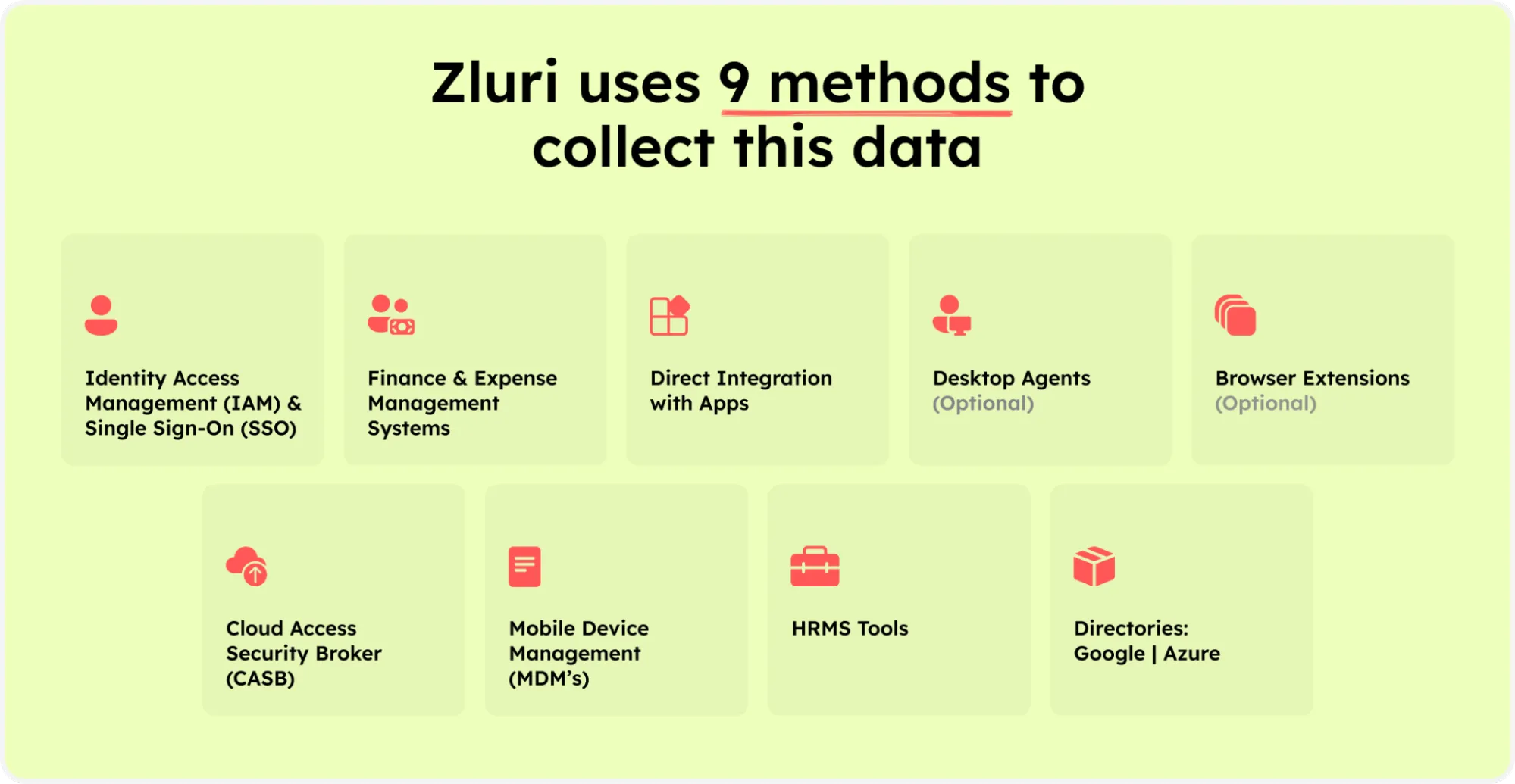
Zluri’s nine discovery methods
Through meticulous discovery processes, Zluri eliminates the manual effort typically associated with identifying them. Whether through Active Directory scans, cloud platform integrations, or API integrations, Zluri helps you locate these essential accountsOnce identified, Zluri's access review solution facilitates robust governance over service account access. With Zluri, you gain granular control over access permissions, ensuring that each service account only has the necessary privileges to fulfill its designated tasks.
By providing visibility into account activities and access levels, Zluri effectively empowers IT teams to enforce least privilege principles.
Further, Zluri's access review solution offers actionable insights into access patterns and usage trends associated with service accounts. You can easily track and monitor account activity through intuitive dashboards and customizable reports. These insights identify any deviations or suspicious behavior that may indicate a security threat.
Moreover, Zluri simplifies the access review process through automation, reducing the burden on your team and minimizing the risk of human error. Zluri ensures compliance with security policies while optimizing operational efficiency by automating routine tasks such as access approvals and revocations.
8 Service Account Management Tools
Let’s delve into the 8 service account management tools.
1. ManageEngine
ManageEngine offers a free service account management solution. The tool is tailored to streamline the intricate process of overseeing service accounts across the enterprise. With ManageEngine, you can gain a comprehensive suite of capabilities designed to simplify account lifecycle management, enhance security posture, and optimize operational efficiency.
Key Features
- Centralized Account Repository: ManageEngine offers a centralized repository for storing and managing service accounts. It provides you with a single pane of glass view of their account ecosystem. This consolidated approach simplifies account administration and ensures visibility across the organization.
- Automated Provisioning and Deprovisioning: With ManageEngine, you can automate the provisioning and deprovisioning of service accounts. It reduces manual overhead and minimizes the risk of human error. This automation accelerates the onboarding process for new services and enhances security by promptly revoking access when necessary.
- Role-Based Access Control (RBAC): ManageEngine enables the implementing of role-based access control (RBAC) policies. By assigning roles and privileges based on job functions, organizations can enforce least privilege principles and mitigate the risk of unauthorized access.
- Comprehensive Auditing and Reporting: ManageEngine facilitates comprehensive auditing and reporting capabilities, allowing you to track account activities, monitor changes, and generate compliance-ready reports.
- Password Management and Rotation: ManageEngine offers robust password management and rotation features to ensure the integrity of service account credentials. You can enforce password policies, schedule automatic password rotations, and integrate with enterprise password vaults to safeguard sensitive credentials from unauthorized access.
- Integration with Identity Providers: ManageEngine effectively facilitates smooth interoperability within the IT ecosystem by seamlessly integrating with existing identity providers and directory services. Whether leveraging LDAP, Active Directory, or other authentication protocols, you can extend the benefits of service account management across the organization without disruption.
Customer Rating
- G2: 4.2/5
2. Delinea
Delinea offers service account management software. Delinea simplifies the complex task of securing service accounts. This provides you with a comprehensive platform to effectively oversee and control service accounts, ensuring enhanced security and operational efficiency.
Moreover, integrate Delinea with your existing IT infrastructure and third-party applications. Whether Active Directory, LDAP, or cloud platforms, Delinea offers flexible integration options to ensure interoperability and maximize efficiency.
Key Features
- Centralized Management: With Delinea, you can centrally manage all service accounts from a single interface. Delinea provides a unified dashboard where you can effortlessly view, organize, and monitor all service accounts.
- Role-Based Access Control: Implement granular access controls with Delinea's role-based permissions. Define specific roles and responsibilities for each user, ensuring that only authorized personnel have access to sensitive service accounts. This enhances security by minimizing the risk of unauthorized access.
- Automated Provisioning and Deprovisioning: Delinea's automated provisioning and deprovisioning capabilities simplify account lifecycle management. They streamline the process of creating, updating, and removing service accounts, saving valuable time and reducing the likelihood of human error.
- Comprehensive Auditing and Reporting: Gain insights into service account activity with Delinea's robust auditing and reporting functionalities. Track changes, monitor access attempts, and generate comprehensive reports to ensure compliance with regulatory requirements and internal policies.
- Password Rotation and Policy Enforcement: Enhance security posture with Delinea's password rotation and policy enforcement features. Set password expiration policies, enforce strong password requirements, and automate the rotation of credentials to mitigate the risk of unauthorized access and credential-based attacks.
Customer Rating
- G2: 4.4/5
3. Okta Identity Cloud
Okta Identity Cloud offers a comprehensive solution tailored to streamline service account management. It provides the capabilities you need to maintain control and enhance security measures.
Okta Identity Cloud seamlessly integrates with various applications, directories, and identity management systems. This integration flexibility enables you to leverage existing infrastructure investments while extending the benefits of centralized service account management across the organization.
Key Features
- Centralized Management: Okta Identity Cloud provides a centralized platform to oversee and administer service accounts across various applications and systems. This centralized approach simplifies management tasks and allows for efficient provisioning, deprovisioning, and access control.
- Automated Lifecycle Management: With Okta's automation capabilities, you can automate the lifecycle of service accounts, from creation to retirement. This automation reduces manual intervention, minimizes errors, and ensures compliance with security policies throughout the account lifecycle.
- Granular Access Controls: Okta Identity Cloud offers granular access controls, enabling you to define and enforce access policies based on roles, responsibilities, and business needs. By implementing least privilege access principles, organizations can mitigate the risk of unauthorized access and data breaches.
- Auditing and Reporting: Okta provides robust auditing and reporting functionalities, allowing you to track and monitor service account activities in real-time. With detailed audit logs and customizable reports, your organization can gain insights into user behavior, detect anomalies, and maintain regulatory compliance.
Customer Rating
- G2: 4.5/5
4. Active Directory Pro
Active Directory Pro, a notable service account management software, offers a comprehensive solution to streamline and fortify your service account management processes. This tool empowers your organization by simplifying the complexities inherent in service account management within the Active Directory environment.
Key Features
- Effortless Service Account Creation and Delegation: Active Directory Pro facilitates the seamless creation and delegation of service accounts, enabling you to swiftly establish and allocate necessary permissions without hassle.
- Granular Access Control and Permission Management: Active Directory Pro offers granular access control mechanisms, allowing you to fine-tune permissions for service accounts with precision and ease. Whether restricting access to sensitive resources or granting specific privileges, administrators can exercise full control over service account permissions with confidence.
- Automated Service Account Lifecycle Management: Active Directory Pro automates the entire lifecycle management of service accounts, from creation to retirement. You can ensure that service accounts are provisioned, updated, and decommissioned in accordance with organizational policies, minimizing the risk of security breaches and operational disruptions.
- Comprehensive Auditing and Reporting Capabilities: Active Directory Pro provides comprehensive auditing and reporting functionalities, allowing you to precisely track all changes and activities related to service accounts.
- Seamless Integration with Existing IT Infrastructure: Active Directory Pro seamlessly integrates with your IT infrastructure, ensuring compatibility with Microsoft Active Directory environments and third-party solutions. Whether you're running on-premises, in the cloud, or hybrid deployments, this versatile tool adapts to your unique setup, providing a cohesive service account management experience without disruption.
5. CheckPoint
CheckPoint Service Account Management is a robust solution designed to streamline and fortify your organization's service account ecosystem. With CheckPoint, you can effortlessly oversee and safeguard service accounts, ensuring seamless operations and fortified defenses against potential security breaches.
Key Features
- Comprehensive Visibility: You will gain comprehensive visibility into all service accounts across your IT infrastructure, empowering you to identify and track every account with precision.
- Automated Provisioning and Deprovisioning: Simplify the provisioning and deprovisioning process with CheckPoint's automated capabilities, reducing manual errors and enhancing operational efficiency.
- Granular Access Controls: Implement granular access controls to regulate access permissions for service accounts, minimizing the risk of unauthorized access and potential security vulnerabilities.
- Centralized Policy Management: Centrally manage security policies for service accounts, ensuring consistency and compliance with organizational security standards across the board.
- Real-time Monitoring and Alerts: Monitor service account activities in real-time and receive instant alerts for any suspicious or anomalous behavior, enabling proactive threat mitigation and incident response.
- Audit Trail and Reporting: Maintain a detailed audit trail of all service account activities and generate comprehensive reports for compliance audits and regulatory requirements, fostering organizational transparency and accountability.
Customer Rating
- G2: 4.6/5
6. CyberArk
CyberArk offers a comprehensive solution tailored for service account management (SAM), empowering you with robust tools to effectively protect and control access to critical assets.
CyberArk seamlessly integrates with existing IT infrastructure and third-party applications, enabling you to extend SAM functionalities across the enterprise. Whether integrating with identity management systems or leveraging APIs for custom integrations, CyberArk ensures interoperability and flexibility.
Key Features
- Centralized Account Repository: CyberArk provides a centralized platform for securely storing and managing service account credentials. You can consolidate all service account passwords and keys within a single, highly secured vault, streamlining access management and enhancing overall security posture.
- Automated Credential Rotation: With CyberArk's automated credential rotation capabilities, you can eliminate manual tasks and ensure service account passwords are regularly updated. This proactive approach eliminates the risk of unauthorized access and enhances compliance with industry regulations.
- Granular Access Controls: CyberArk enables you to define granular access controls for service accounts, ensuring that only authorized personnel can access sensitive credentials. Organizations can reduce the attack surface by implementing least privilege principles and preventing potential security breaches.
- Audit and Compliance Reporting: CyberArk offers robust audit and compliance reporting functionalities, allowing you to track and monitor all activities related to service account management. With comprehensive audit trails and real-time alerts, organizations can demonstrate compliance with regulatory requirements and internal policies.
Customer Rating
- G2: 4.5/5
7. StrongDM
StrongDM offers comprehensive privileged access management software. This helps streamline the process of granting and revoking access to various service accounts across your infrastructure.
StrongDM utilizes encrypted connections and secure protocols to ensure that access to your resources is always protected. This helps safeguard sensitive data from interception and unauthorized access.
Key Features
- Centralized Access Control: With StrongDM, you gain centralized control over service account access, allowing you to manage permissions from a single interface. This simplifies the process of granting and revoking access, reducing the risk of unauthorized entry.
- Granular Permissions: StrongDM enables granular control over permissions, ensuring that users only have access to the required resources. This helps minimize the risk of privilege escalation and insider threats.
- Audit Trail: StrongDM provides a detailed audit trail of all access attempts and actions, giving you full visibility into who accessed what and when. This feature is invaluable for compliance purposes and investigating security incidents.
- Multi-Platform Support: StrongDM supports a wide range of platforms and services, including databases, servers, and cloud infrastructure. Whether your resources are hosted on-premises or in the cloud, StrongDM ensures consistent access management across your entire environment.
Customer Rating
- G2: 4.7/5
8. Netwrix
Netwrix offers a comprehensive privileged access management platform providing streamlined service account management to ensure security, compliance, and operational efficiency.
Netwrix seamlessly integrates with existing IT infrastructure, including Active Directory, IAM solutions, and SIEM platforms, ensuring compatibility and ease of deployment. You can leverage Netwrix alongside their existing tools and workflows, maximizing operational efficiency and ROI.
Key Features
- Centralized Visibility and Control: Netwrix provides a centralized platform to gain complete visibility into all service accounts across the IT infrastructure. Administrators can easily monitor, track, and manage service accounts through a unified dashboard, ensuring a holistic approach to security and compliance.
- Automated Service Account Lifecycle Management: With Netwrix, the tedious task of managing service account lifecycles is simplified through automation. You can define policies and workflows to automate service account provisioning, modification, and decommissioning, reducing manual errors and improving operational efficiency.
- Risk Mitigation and Compliance Assurance: Netwrix helps you eliminate security risks and maintain compliance with regulatory requirements by continuously auditing service account activities. Real-time alerts and reports enable proactive identification of suspicious behavior, ensuring swift action to mitigate potential threats and maintain regulatory compliance.
- Granular Access Control and Least Privilege Enforcement: Netwrix empowers you with granular access control capabilities, allowing them to enforce the principle of least privilege for service accounts. By restricting access to only essential resources and privileges, you can reduce the risk of unauthorized access and data breaches.
Customer Rating
- G2: 4.4/5
Elevate Your Service Account Management with Efficient Tools
With an array of service account management tools, you can streamline operations and enhance security and productivity across your organization. These top eight tools offer comprehensive solutions to meet the diverse needs of modern enterprises.
From robust access control mechanisms to seamless integration capabilities, each tool offers a unique set of features. Whether you prioritize user-friendly interfaces, stringent compliance measures, or scalable architecture, there's a solution tailored to your requirements. By harnessing the power of these tools, you can optimize resource allocation, mitigate risk, and empower your team to achieve peak performance.
Furthermore, the landscape of service account management is constantly evolving, with new challenges and technologies advancing. Investing in adaptable solutions is essential to staying ahead of the curve. With continuous updates and proactive support, these tools prepare you to overcome the challenges that service accounts may throw your way.
FAQs
1: What is an example of a service account?
For instance, programs like Exchange, SharePoint, SQL Server, and Internet Information Services (IIS) use service accounts. These accounts set the rules for how the programs can access files and networks and decide what they can do with them.
2: What is the difference between a service account vs. a user account?
Service Account vs. User Account:
A service account is like an ID card for a computer program, while a user account is for people. User accounts usually have names like \"John Smith,\" but service accounts have names like \"NetworkService\" or even no name at all. This helps keep track of which programs are running on computers, separate from the people using them.
3: What are managed service accounts?
A standalone Managed Service Account (sMSA) is like a super organized account that handles passwords automatically, makes managing service names easier, and allows other admins to help out.
4: What is a vertical privilege escalation?
Vertical privilege escalation, also called privilege elevation, happens when someone with lower access somehow gets into areas or uses features meant for higher-level users. For example, regular Internet banking customers suddenly gain access to site admin tools or bypass a smartphone's password.









.svg)














