Segregation of Duties (SoD) is crucial for mitigating risks that arise from concentrated authority and access to critical resources. In this article, we will explore various software solutions with SoD capabilities.
Ensuring proper segregation of duties (SoD) within your organization can be challenging. Without the right tools, it’s easy for conflicts to arise, leading to potential security breaches and compliance issues.
Managing SoD manually or with inadequate software increases the risk of fraud, errors, and audit failures. You might find yourself struggling to maintain clear and secure role definitions, which can compromise your organization’s security and compliance standing. To address these challenges, utilizing dedicated SoD software is essential.
Here will introduce you to the top 10 software with SoD, helping you enhance security, ensure compliance, and streamline your role management processes. With the right tools, you can achieve better control and oversight in your organization.
Key Features of Software with SoD Capabilities
Let's explore the key features that make the software an indispensable asset for your organization’s SoD requirements:
- Access Control & Authorization Management: The software with SoD abilities empowers you to define and enforce strict access controls for different roles within your organization. By assigning specific duties and permissions to individual employees, the software ensures that no single person has excessive access rights.
- Real-time Compliance Monitoring: These tools help you track and analyze user activities, ensuring adherence to industry regulations and internal policies. The software provides comprehensive insights to aid in compliance audits, be it GDPR, HIPAA, or any other relevant standard.
- Segregation of Sensitive Operations: With the software with SoD capabilities, you can effortlessly segregate critical operations and ensure that no single user possesses all the necessary permissions to execute high-risk tasks. This segregation fosters a robust security posture and reduces the chances of security breaches caused by human errors or malicious intent.
- Audit Trail and Reporting: You can rely on this software's comprehensive audit trail and reporting features to monitor user actions effectively. The software keeps a detailed log of every user's activities, giving you a transparent view of who did what and when. This feature helps in identifying and investigating any suspicious or unusual activities promptly.
- Automated Rule Enforcement: This software streamlines security by automating the enforcement of access control rules. By setting predefined access restrictions, the software minimizes the need for manual oversight, reducing the risk of accidental policy violations and ensuring consistent adherence to security protocols.
- Incident Response and Alerting: Promptly address potential security incidents with real-time alerts and notifications. The software with SoD features proactively alerts you about any unusual behavior or policy violations, enabling them to take immediate action and prevent security breaches before they escalate.
In this post, we will discuss the various SoD tools available in the market to help you choose the suitable one for your organization.
10 Software with Segregation of Duties Capabilities
Let’s explore the list of SoD software that can meet your requirements.
1. Zluri
Zluri offers a robust identity governance and administration (IGA) platform designed to meet your SoD requirements. This allows you to govern access to your entire SaaS landscape throughout the user lifecycle.
With Zluri's IGA platform, you can easily maintain control and enhance security through features such as user provisioning, deprovisioning, automated access reviews, and self-service access requests.
The platform empowers you to ensure that every user's access is properly managed and aligned with your organization's policies. This strengthens security and helps you comply with the required regulations.
Let's explore how Zluri stands out from other IGA tools by offering unique SoD capabilities.
Enhance your SoD capabilities with Zluri’s discovery engine
Zluri makes it easy for your IT team to analyze and uncover valuable data about your SaaS applications and users. We offer nine discovery methods to identify this information: MDMs, IDPs & SSO, direct integration with apps, finance & expense management systems, CASBs, HRMS, directories, desktop agents (optional), and browser extension (optional).
As per KuppingerCole’s research, Zluri provides a single source-of-truth of all SaaS apps in your organization.
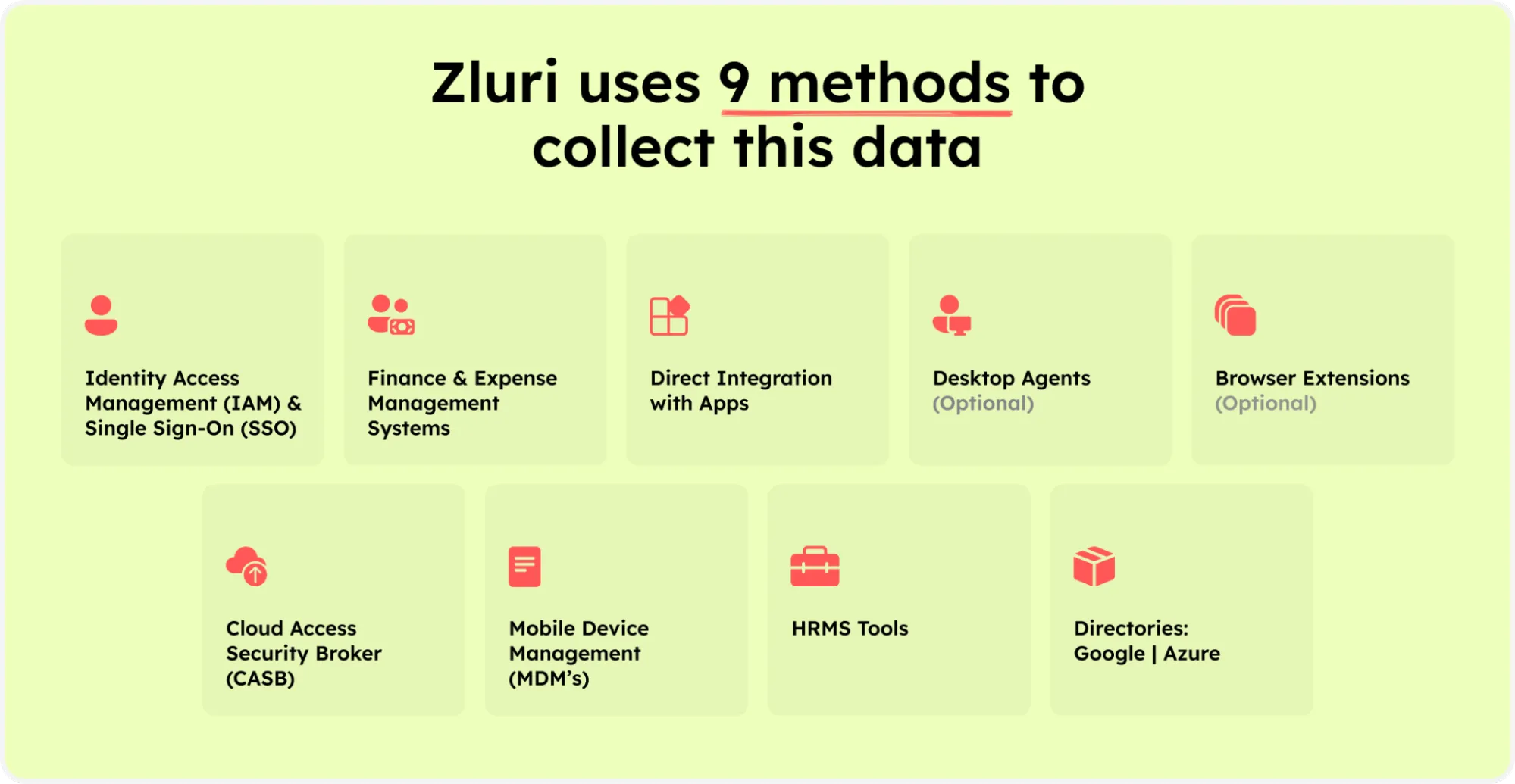
Zluri’s nine discovery methods
But Zluri doesn't stop at discovery. The platform goes above and beyond by integrating with over 300 SaaS applications. You get real-time data, valuable insights, and AI-powered alerts to stay informed.
With API-based integrations, Zluri ensures in-depth data discovery across all your SaaS applications, leaving no information hidden. You can trust that Zluri provides 100% visibility into your SaaS environment.
Let’s see how this feature helps in separating duties.
Imagine you're in a company where different groups look after various software tasks. The finance folks handle expenses, the IT team manages API connections, and the security team takes care of SSO. Zluri makes things easy. Each team can find the info they need without getting in the way of others. This keeps everyone focused on their own jobs and makes everything run smoothly.
Gain access control with Zluri’s automation engine
Zluri's automation engine acts like a smart driving system for your company. It makes it simple to control who can access different things, ensuring everything runs really smoothly. It's like having a set of rules that it always obeys to keep things fair.
With Zluri's automation engine, your IT teams can effortlessly ensure the correct people have the proper permissions. This boosts security and follows the idea of dividing tasks so that no one has too much control simultaneously.
Now, let’s explore Zluri’s IGA capabilities.
- Lifecycle Management
Zluri's IGA solution simplifies and secures user access for your organization. With this platform, you can easily manage user accounts from the moment they join to when they leave, all while keeping things very secure.
Zluri's IGA makes it super easy when someone new joins your team. They can quickly get into the apps and stuff they need, all thanks to automatic processes that work smoothly with HR systems. Your IT team can create accounts for many apps in one place, meaning fewer mistakes and less work for them. Also, new employees get the right access right from the start.
And it doesn't stop there. When someone leaves the company, Zluri's automatic systems help your IT team remove their access to all the apps. This stops old accounts from hanging around and causing problems. It's like ensuring people have access to what they need for their job and nothing extra.
Let’s consider your IT department like an intricate web, with different people handling different tasks - one ensuring the network's safety, another taking care of software setup. This sharing of duties is vital to keep a good balance between control and access.
With Zluri's IGA, you ensure that no one in your IT team has too much power. It's like giving each member exactly the right permissions for their specific roles and having strong control over who can access what in the organization.
In addition, Zluri offers key unique features that differentiate it from others, ensuring effective access management:
Customizable workflows: With Zluri, you can set up pre-defined workflows tailored to your organization's specific requirements, eliminating the need for manual granting and revoking access permissions. The intuitive interface allows you to customize workflows based on user roles, departments, and seniority levels.
Onboarding

Offboarding
Powerful app recommendations & in-app suggestions: Zluri also provides contextual-based app recommendations based on user profiles, department, seniority level, etc., making it convenient for your team to choose the appropriate apps for provisioning.

Moreover, it offers in-app suggestions to enhance user productivity by recommending required actions for efficient task performance.
Reusable Playbooks: By saving these workflows as predefined “playbooks”, Zluri eliminates the need to recreate workflows for each user, further streamlining the process and increasing operational efficiency.

But what happens when a user’s role changes during the mid-lifecycle transitions?
- Access request management
Zluri simplifies the process of managing user access during role transitions with its self-serve model, the Employee App Store (EAS). This powerful feature empowers your IT team to maintain control over employees' access to essential tools and applications.

Using the EAS, your team or designated approver can review and approve access requests based on the employees' job roles and responsibilities. This ensures that permissions granted align with their specific needs, allowing you to govern access and protect sensitive information within your organization.
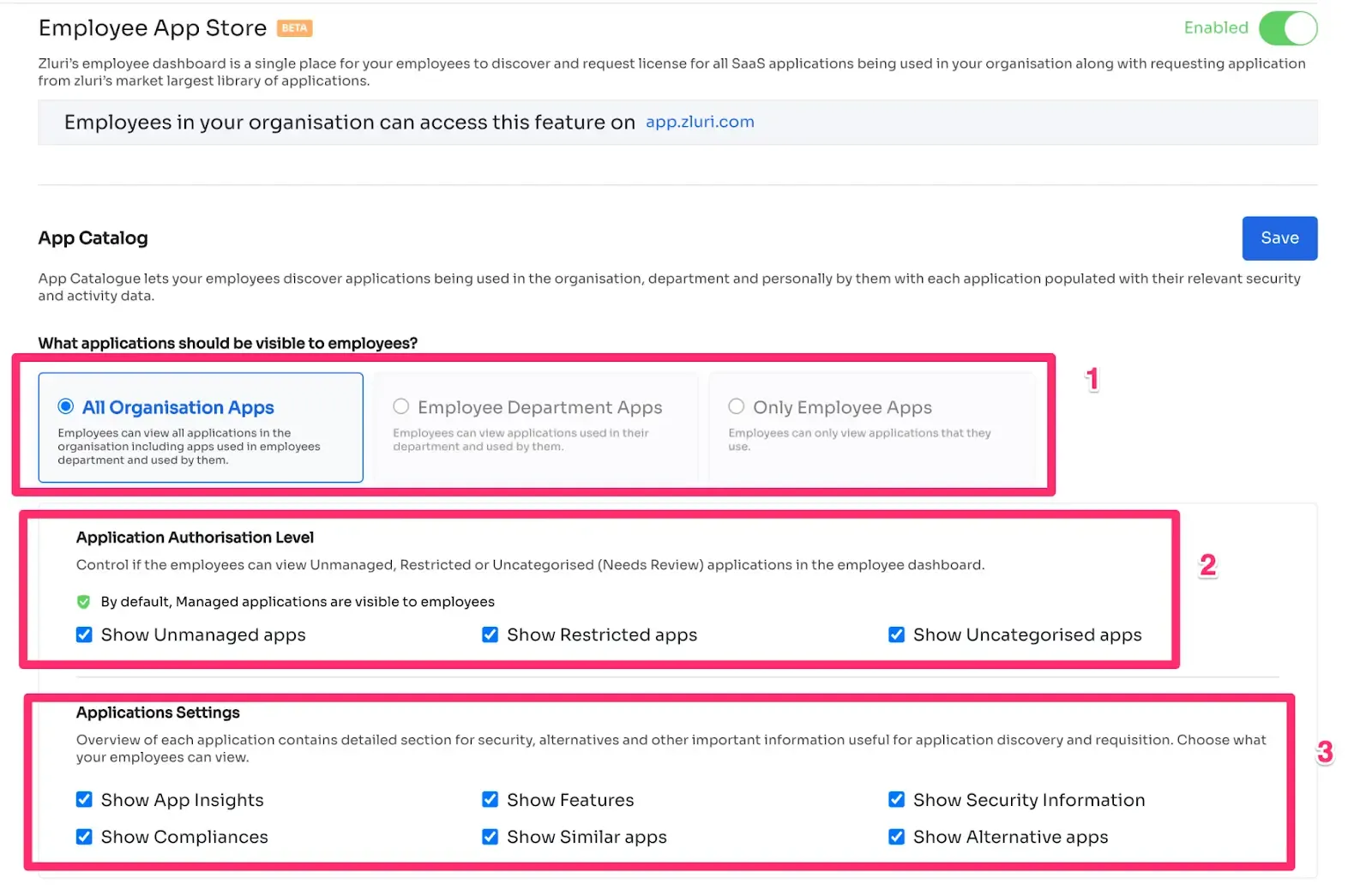
Zluri's transparent approval system consists of three levels: app owners, reporting managers, and IT admins. Higher-level authorities have the decision-making authority, enabling them to override decisions made by lower-level admins or managers.
In the event of an access request being rejected, decision-makers can provide comments explaining the reasons behind the rejection, ensuring transparency and clarity in the access request process. Approvers also have the ability to modify specific requests as needed.
Let’s see how Zluri’s EAS helps you meet your SoD requirements.
Let's say your IT department handles different tasks like looking after servers, managing databases, and supporting applications. Each of these jobs requires different levels of access to tools and systems. Without a proper setup, someone responsible for server upkeep might accidentally get access to sensitive customer info stored in databases, creating a security problem.
With Zluri's EAS, when roles change, or new employees in the IT team join, it clearly lays out what access they need based on their specific job—whether it's taking care of servers, handling databases, or supporting applications.
The IT manager or whoever's in charge can review and approve these access requests following the rules we've already set. This stops any one person from having too much access, which could cause a breach. We keep everything balanced, so no one's juggling conflicting tasks or has too much power over important systems.
Additionally, to keep users well-informed, Zluri provides a \"changelog\" feature where users can track updates related to their access requests. This includes information such as the approval or rejection of requests, changes in license duration or tier, and comments added by any admin. This helps users stay updated and aware of any changes or decisions made regarding their access to applications.
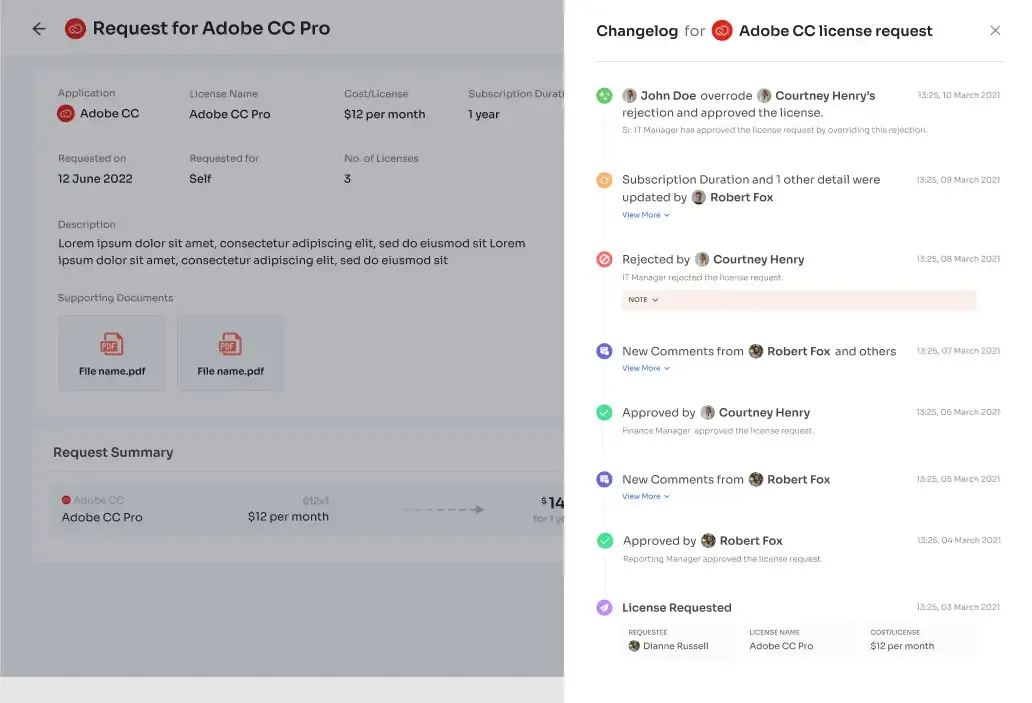
Access certification
Zluri's IGA solution simplifies user access review and permission management. It provides a centralized platform for your team and relevant teams, like security, GRC, auditors, etc., to review and report on user access. With Zluri, you can easily set review parameters, choose reviewers, and schedule campaigns.
Through intelligent automation, Zluri assesses user access rights based on predefined rules, saving time and reducing errors compared to manual spreadsheet reviews.
Zluri also takes security to the next level by offering auto-remediation capabilities. In case of any access violations detected, Zluri takes immediate corrective actions. This ensures your organization's security is strengthened and compliance with SoD capabilities is maintained. It helps prevent unauthorized data breaches by promptly revoking access for terminated employees or those with outdated privileges.
Zluri generates comprehensive reports that provide valuable insights into access patterns, vulnerabilities, and compliance status. These reports make it easy to demonstrate compliance to auditors and make informed decisions about access management.
Zluri's unique approach to access reviews sets it apart from other IGA tools. Let’s see how.
Continuous Access Reviews: It enables you to maintain control over access privileges through recurring and scheduled certifications. Recurring certifications ensure consistent review and validation of access permissions, quickly identifying and addressing security weaknesses.
Further, scheduled certifications offer planned and timely evaluations, reducing the risk of overlooking critical access issues. This proactive approach ensures that access privileges remain up-to-date and help you maintain SoD across the organization.
Zluri provides industry-standard certificate templates to simplify the certification process. These templates offer a standardized approach, making certifications efficient, comprehensive, accurate, and aligned with recognized guidelines.
Real-time Access Reviews: Zluri leverages the power of artificial intelligence (AI) to enhance data security and streamline compliance processes. By conducting real-time access reviews and analyzing access patterns, user behavior, and system logs, Zluri identifies unusual or potentially risky activities, allowing proactive mitigation of security threats and the protection of sensitive data.
Zluri's access reviews support continuous monitoring, providing real-time visibility into access privileges. This enables you to promptly address access-related issues, reducing the risk of unauthorized access or misuse.

One of Zluri's key strengths is its AI compliance capabilities. It provides intelligent insights and recommendations to ensure your access controls align with industry regulations and standards. By leveraging AI technology, Zluri simplifies the compliance process, making it easier for your organization to meet regulatory requirements, particularly when it comes to SoD capabilities.
Customer rating
- G2: 4.8/5
- Capterra: 4.9/5
2. SecurEnds
SecurEnds offers a platform designed specifically to address the challenges of SoD effectively. With its user-friendly interface and powerful features, SecurEnds empowers you to streamline SoD processes and bolster your organization's overall security posture.
Through the tool's intuitive policy management feature, you can define rule sets and access restrictions, ensuring that potential conflicts are mitigated, and SoD guidelines are consistently followed across the organization.
Key Features
Role-Based Access Control (RBAC) Management: With this feature, you can easily segregate duties based on job functions and responsibilities. You can create and modify roles through a centralized dashboard, ensuring that employees can access only the resources and data essential for their specific tasks, prevent unauthorized access, and minimize potential risks.
Risk Identification and Mitigation: The tool's sophisticated algorithms analyze user permissions and access patterns to detect potential conflicts that may lead to fraud or data breaches. By proactively identifying these risks, you can take timely action to rectify the issues and ensure compliance with regulatory requirements.
Real-time Monitoring and Alerts: SecurEnds empowers you with real-time monitoring capabilities, allowing you to track user activities and permissions changes as they happen. This continuous monitoring ensures that any deviations from SoD policies are promptly flagged, enabling you to address potential threats swiftly.
Additionally, the tool sends automated alerts to relevant stakeholders, keeping them informed about critical changes and facilitating timely corrective measures.
Simplified Access Review Process: Periodic access reviews are essential to maintain a secure SoD environment. SecurEnds streamlines this process with automated access review campaigns. The tool generates review tasks, prompting responsible parties to regularly validate users' access rights.
This simplification saves time and effort while ensuring that SoD remains intact and adheres to the organization's policies.
Customer rating
- Capterra: 4.8/5
3. SailPoint Identity Security Platform

SailPoint Identity Security Platform emerges as a powerful solution, offering robust SoD features that help you enhance security and streamline compliance processes.
SailPoint understands the significance of segregating duties to prevent conflicts of interest and potential security breaches. The Identity Security Platform comes equipped with advanced SoD capabilities, which allow you to define and enforce logical access controls across their organization's systems and applications.
With SailPoint's SoD, you can establish rules restricting certain combinations of permissions to ensure that no single user has excessive access rights, reducing the risk of insider threats and data breaches.
Key Features
Role-Based Access Control (RBAC): SailPoint enables you to create granular roles for different job functions within the organization. Each role has a specific set of permissions and access privileges tailored to the role's responsibilities.
This ensures that users are granted only the permissions required to perform their duties, eliminating the potential for unauthorized access to critical systems.
Policy-Based Governance: The platform offers customizable policy rules that align with industry regulations and best practices. You can define policies that identify and flag potential SoD conflicts automatically.
When SailPoint detects a violation, it can trigger alerts, notifications, or even automated actions, allowing you to swiftly address and rectify the issue.
Access Request and Approval Workflows: SailPoint offers streamlined access request workflows with built-in approval processes. Users can initiate a request through the platform when they need access to specific resources.
The request is then routed through predefined approval chains, ensuring that appropriate authorities review and authorize the access request before granting permissions. This controlled process minimizes the risk of granting unauthorized access to sensitive information.
Customer rating
- G2: 4.4/5
4. Okta Identity Governance
Okta Identity Governance is a solution designed to streamline the process of segregation of duties (SoD) within your organization. With a focus on simplicity and effectiveness, this tool empowers you to proactively prevent conflicts of interest and unauthorized access, thereby fortifying your company's digital perimeter.
Okta Identity Governance offers a centralized platform to manage user access and permissions across all applications, systems, and devices. You can define and enforce SoD policies tailored to your organization's unique requirements through a single, intuitive dashboard. This minimizes the complexity of handling multiple user repositories, ensuring a seamless and cohesive approach to access control.
Key Features
Automated SoD Policy Enforcement: The tool uses advanced automation to continuously monitor and enforce the segregation of duties policies. The system identifies potential conflicts in user roles, preventing users from acquiring conflicting privileges that could lead to unauthorized access or data breaches.
Real-time Risk Detection: The tool constantly evaluates user activities and access patterns, promptly flagging suspicious behavior that might indicate a violation. By proactively identifying potential security risks, you can take swift action to prevent security breaches and ensure compliance with industry regulations.
Streamlined Compliance Reporting: The tool simplifies the process of generating compliance reports. You can effortlessly demonstrate adherence to SoD policies during audits through comprehensive and customizable reporting features. This feature empowers you to save valuable time and resources while showcasing your organization's data security and governance commitment.
Role Lifecycle Management: Okta's role lifecycle management capabilities automate role assignments, updates, and revocations based on user responsibilities or job role changes. This ensures access rights align with employees' current positions, reducing the risk of outdated permissions causing SoD issues.
Customer rating
- G2: 4.5/5
- Capterra: 4.7/5
5. ForgeRock Identity Governance
ForgeRock Identity Governance is a solution that provides robust Segregation of Duties (SoD) capabilities. SoD is a critical aspect of access management, preventing conflicts of interest and unauthorized actions by ensuring that no single user possesses too much control within the system.
With ForgeRock's SoD policy management, you can effortlessly define and enforce segregation rules. This enables you to identify potential conflicts between roles and restrict users from having conflicting permissions. You enhance your organization's security posture and maintain regulatory compliance by mitigating the risk of misuse, unauthorized access, or fraud.
Key Features
Role-Based Access Control: The tool adopts a role-based access control approach, allowing you to define specific roles and their associated responsibilities within your organization. By assigning roles to users based on their job functions, you can ensure that individuals are granted only the necessary access rights required to perform their duties and nothing more.
Real-time Monitoring and Alerts: The solution continuously monitors user activities and real-time access patterns. This proactive approach lets you promptly detect unauthorized attempts to bypass SoD controls. The system can generate alerts or notifications to administrators when suspicious activities are identified, ensuring immediate action can be taken to mitigate potential risks.
Entitlement Reviews: ForgeRock Identity Governance streamlines the entitlement reviews process by automating it, which helps ensure that user access rights are periodically reviewed, adjusted, or revoked based on changing roles or job responsibilities. This feature ensures that you meet the SoD needs and also facilitates compliance with regulatory requirements.
Separation of Duties Conflict Resolution: The tool offers conflict resolution mechanisms when conflicts between roles arise. These mechanisms give administrators the necessary insights to make informed decisions and resolve conflicts effectively. This capability allows you to maintain an efficient workflow while upholding SoD principles across the organization.
Customer rating
- G2: 4.4/5
6. One Identity Manager
One Identity Manager emerges as a reliable solution, empowering you to efficiently handle SoD challenges while fostering a secure and compliant work environment. One Identity Manager simplifies complex access control processes by providing a comprehensive set of features tailored to address SoD concerns, ensuring your organization's data and assets are in safe hands.
The solution facilitates the easy creation and enforcement of SoD policies tailored to your organization's specific requirements. You can define rules restricting the combination of conflicting roles to prevent employees from holding conflicting duties. The solution also automates the enforcement of these policies, flagging and alerting administrators when potential SoD violations are detected.
Key Features
Role-Based Access Control (RBAC): The tool adopts an RBAC approach, allowing you to define user roles and assign appropriate permissions based on job responsibilities. It ensures that users have access only to the necessary functions and data required to perform their tasks, preventing unauthorized access to sensitive information. This granular control minimizes the risk of conflicts of interest and potential fraud.
Real-Time Monitoring and Reporting: The solution provides real-time monitoring and reporting capabilities to maintain a proactive security stance. You can gain insights into user activities, access patterns, and attempted violations of SoD policies. Further, timely alerts enable swift responses to potential threats, ensuring quick remediation and enhancing overall IT security.
Access Certification and Reviews: The platform streamlines the access certification process, allowing you to conduct regular reviews of user access rights. This feature helps identify access discrepancies and allows managers to make informed decisions on access modifications, reducing the risk of unauthorized actions.
Workflow Automation: The platform offers workflow automation capabilities to simplify access request and approval processes. You can also establish custom workflows to obtain appropriate authorizations before granting access to sensitive resources. Automating these procedures reduces manual errors and ensures compliance with SoD principles throughout the access lifecycle.
Customer rating
- G2: 3/5
- Capterra: 5/5
7. RSA Governance and Lifecycle
The RSA Governance & Lifecycle solution is a platform designed to streamline and fortify your security operations, specifically focusing on SoD. This powerful solution addresses the critical challenge of preventing conflicts of interest and minimizing potential risks in your organization's access control landscape.
Recognizing that each organization has unique operational requirements, the RSA Governance & Lifecycle Solution allows for flexible customization of SoD rules. You can tailor the rules based on your organization's specific business processes and compliance needs. This adaptability ensures that the platform aligns precisely with your security policies, reducing potential gaps in SoD coverage.
Key Features
Role-Based Access Control (RBAC) Framework: With RBAC, you can easily assign specific roles to employees based on their job responsibilities, ensuring they have access only to the necessary resources for their respective roles. This feature drastically reduces the risk of unauthorized access, making it easier to maintain SoD compliance.
Automated SoD Violation Detection and Remediation: RSA's solution has advanced automated detection mechanisms that proactively identify potential conflicts and violations across your systems. Upon detecting a violation, the platform triggers immediate notifications to relevant stakeholders, enabling swift and targeted remediation actions.
Real-Time Compliance Monitoring and Reporting: Maintaining SoD compliance is an ongoing process, and the RSA solution facilitates real-time monitoring and reporting of access activities. You gain complete visibility into user access and SoD compliance status. Comprehensive reports provide actionable insights, allowing you to easily demonstrate compliance to auditors and other stakeholders.
Seamless Integration and User-Friendly Interface: The solution seamlessly integrates with your existing infrastructure, making deployment quick and straightforward. Additionally, the user-friendly interface ensures that even non-technical users can efficiently manage access controls, reducing the burden on your IT team.
Customer rating
- G2: 4.7/5
8. Hyperproof

Hyperproof provides a centralized platform to manage all aspects of SoD compliance efficiently. With a user-friendly interface, you can easily access and monitor all compliance-related activities, ensuring nothing falls through the cracks. This streamlines the process of assigning, tracking, and documenting responsibilities within your organization.
Key Features
Role-Based Access Controls (RBAC): With Hyperproof's RBAC, you can customize permissions for each user, aligning with their specific roles and responsibilities. This feature helps maintain a clear separation of duties, reducing the likelihood of insider threats and unauthorized access to critical systems.
Real-time Risk Assessments: Hyperproof offers real-time risk assessments that allow you to continually stay on top of compliance status. The system evaluates SoD compliance across the organization, generating insightful reports and dashboards for effortless monitoring and decision-making.
Policy and Procedure Management: The tool facilitates seamless policy management, enabling you to maintain a current repository of policies, procedures, and control measures. It also assists in ensuring that all employees are aware of the guidelines they need to follow.
Auditing and Reporting Capabilities: The solution generates detailed compliance reports, offering a comprehensive overview of your organization's SoD practices. This not only streamlines audit processes but also helps you identify areas for improvement.
Customer rating
- G2: 4.6/5
- Capterra: 4.7/5
9. Omada Identity
Omada Identity offers an IGA solution with features tailored specifically for bolstering SoD within your organization. Omada's user-friendly interface lets you easily map out your organization's processes and define access rules that align with best practices.
The platform automatically detects and alerts you to potential conflicts, helping you proactively address them before they escalate. This safeguards your systems and data and promotes a culture of accountability and transparency.
Moreover, the solution ensures compliance with industry regulations and standards, such as SOX, GDPR, and HIPAA, providing your organization with a reliable foundation for meeting the necessary requirements. This, in turn, helps you avoid hefty fines and legal consequences while maintaining the trust of your customers and partners.
Key Features
Role-based Access Control System: With this feature, you can define distinct roles and assign appropriate permissions to individuals based on their job responsibilities. By clearly segregating roles, you minimize the risk of conflicts of interest and prevent unauthorized access to sensitive information.
Automated Provisioning and Deprovisioning: When employees join or leave your organization, this feature ensures that their access rights are granted or revoked promptly and accurately. This streamlines your IT processes and reduces the potential for errors and unauthorized access points.
Continuous Monitoring and Analysis: The solution also excels in monitoring and analyzing access rights through its user activity tracking feature. This real-time monitoring allows you to detect any suspicious activities promptly and take appropriate actions, thus safeguarding your systems from potential insider threats or malicious activities.
Advanced Analytics and Reporting: This allows you to gain valuable insights into user access patterns, potential SoD violations, and areas that require further attention. With this knowledge, you can proactively address any vulnerabilities and maintain a strong SoD posture.
Customer rating
- G2: 3.8/5
10. Saviynt IGA

Saviynt IGA is an identity governance and administration (IGA) platform focusing on SoD management. Its primary goal is to prevent conflicts of interest within your organization by enforcing a clear division of duties among employees, thereby mitigating the risk of fraud and compliance violations.
Moreover, Saviynt IGA streamlines the user lifecycle management process, ensuring that permissions are correctly assigned, modified, or revoked based on employees' roles and responsibilities. This minimizes the risk of lingering access rights after employee departures and reduces potential security gaps.
Key Features
Role-Based Access Control (RBAC): Saviynt IGA offers a powerful RBAC feature that allows you to create and manage roles within your organization. Each role is associated with specific access permissions, ensuring that employees only have access to the resources necessary for their job functions. This granular control significantly reduces the risk of unauthorized access and accidental data exposure.
Customizable Policies: The platform allows you to define custom SoD policies tailored to your organization's unique needs. You can set up rules that prevent certain combinations of roles from being assigned to the same individual, ensuring strict adherence to SoD principles.
Real-time Monitoring and Alerts: Saviynt IGA offers real-time monitoring of user activities and access permissions. Any potential violation of SoD policies triggers instant alerts, enabling your IT team to take immediate action to rectify the situation. This proactive approach helps prevent security breaches and swiftly responds to potential threats.
Audit Trails and Reporting: The platform generates detailed audit trails and comprehensive reports to provide a transparent view of all user actions and access changes. These reports are invaluable for compliance audits and demonstrating regulatory adherence. With Saviynt IGA, your organization can easily meet the requirements of various industry standards.
Customer rating
- G2: 3.5/5
- Capterra: 4.5/5







.png)

.svg)














