Lately, the news has been flooded with headlines about high-profile cyberattacks like ransomware, zero-day exploits, and DDoS attacks. This proves that organizations leave security blind-spots unchecked, allowing attackers to exploit them. However, if you don't want to become a victim, it is necessary to uncover every gap in your security setup. How can that be done? Perform a cybersecurity audit. In this article, we'll explore it in detail.
In March 2017, Equifax, a prominent credit card reporting agency, was the victim of a security incident in which attackers stole approximately 147 million people's PII (personally identifying data). Can you guess how much this breach cost the company? They incurred over $700 million in settlement costs, legal fees, and customer compensation.
After hearing the cost, you might wonder, 'What caused this disaster?'
After investigation, it was found that Equifax had known about an issue in its Apache Struts (developers used it to build the company's consumer complaint web portal) but delayed patching it. The attacker took the chance, exploited the vulnerability, and gained unauthorized access to the complaint portal. After that, they moved from the web portal to other servers and got hold of usernames and passwords stored in plaintext. They further used those usernames and passwords to access other internal systems and applications. But here's where things took a turn for the worse — they remained undetected for over a month, which gave them enough time to steal terabytes of sensitive data.
Where did they go wrong? First, they missed patching the vulnerability — a simple step that could've blocked the attackers in their tracks. Second, they didn't catch the suspicious activity lurking in their system — which, unbelievably, went unnoticed for over a month.
What could they have done? The entire incident could have been avoided, if they had conducted a cybersecurity audit on time.
What Is Cybersecurity Audit?
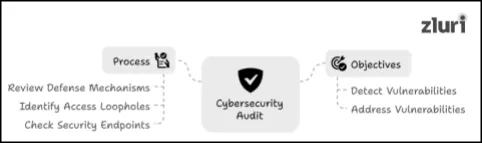
A cybersecurity audit (360-degree security audit) is a formal procedure of reviewing how effective an organization’s cybersecurity defense mechanism is, such as whether it can prevent or withstand potential breaches. Typically, the main objective behind performing such audits is to detect vulnerabilities (such as access loopholes or unpatched security endpoints) and address them before malicious actors get the opportunity to exploit them.
Note that the cybersecurity audit procedure is carried out either by the organization's in-house audit team or external auditors, depending on the scenario.

- Let's say you’re aiming to obtain a compliance certification (which can be SOX, PCI DSS, GDPR, or HIPAA certification), and then you need to bring in a certified external auditor to perform this audit. Meanwhile, if your sole objective is to get an idea of whether your security controls can effectively prevent and mitigate breaches, then you can have your internal team take charge of the audit.
Also Read: Compliance Audit: Definition, Types, & How to Conduct It
- However, if your in-house team lacks the necessary expertise to carry out this audit process, then you need to appoint an external auditor.
Also Read: If you are uncertain about which external auditor to bring in, you can check out this blog— how to choose an auditor
Now, you might probably have a question — ‘What exactly is examined? What areas or aspects are evaluated during a cybersecurity audit?’
Outlined below are the 5 areas that are assessed during this audit.
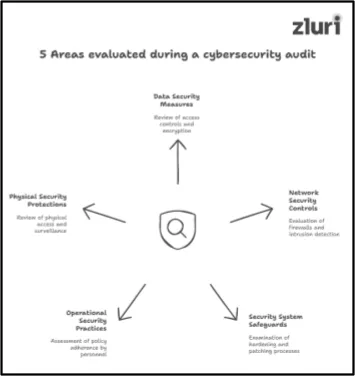
- Area 1# Data Security Measures — During the audit, the audit team reviews implemented access controls, encryption use, and measures taken to protect data at rest and transmission.
- Area 2# Network Security Controls — The team evaluates every access point, anti-virus configurations, security monitoring capabilities, implemented firewalls, and intrusion detection systems.
- Area 3# Security System Safeguards — The team thoroughly examines the hardening process (e.g., rules that organizations have put in place to maintain the security of systems, applications, and endpoints) and patching process.
- Area 4# Operational Security Practises — The team assesses whether security policies and procedures are followed by each individual (employees, admins, freelancers, contractors, and others) within the organization or not.
- Area 5# Physical Security Protections — The team reviews on-premises physical security controls such as who has access to server rooms and data centers, physical devices protection setup (e.g., locked doors, screen locks, and disk encryption), alarm systems, and surveillance setup.
Breakdown Of Cybersecurity Audit Stages
Below, we’ve explained what stages are involved in a cybersecurity audit process.
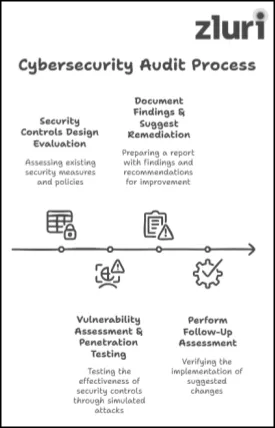
Stage 1: Security Controls Design Evaluation
During this stage, the audit team checks which security controls, policies, procedures, and measures (covering all areas outlined earlier above) the organization has implemented. They also verify whether the implemented controls align with the CIA triad principle (CIA stands for confidentiality, integrity, and availability).
Note: The effectiveness of the controls isn't being tested just yet—this stage is all about what's in place, not how well it works.
Stage 2: Performs Vulnerability Assessment & Penetration Testing (VAPT)
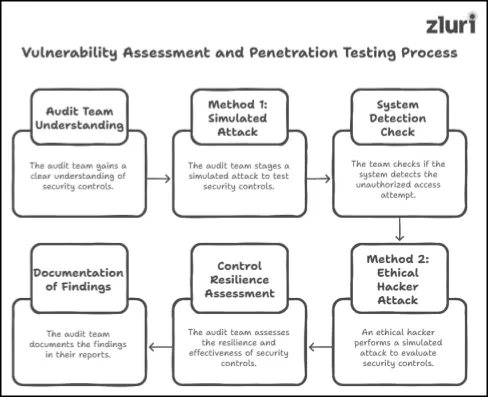
Once the audit team gains a clear understanding of the security control design, they further evaluate the effectiveness of those controls by performing vulnerability assessment and penetration tests (VAPT). This test is typically carried out in two ways –
- Method 1# The audit team runs a check on their own (hands-on approach). They stage a simulated attack; for instance, they impersonate an unauthorized user and attempt to log in to the system or application. After that, they check whether the security controls, such as the organization's SIEM system, can proactively detect this unauthorized access attempt and trigger an alert to notify the IT/security teams.
Note: If the system successfully identifies such instances and raises a timely/instant alert, the audit team will write in their report that the security controls are functioning as intended. However, in case the system fails to perform (which indicates a flaw in the controls), the audit team further records the information under the 'need-remediation' section.
- Method 2# The audit team brings in an ethical hacker to perform a simulated attack. Note that, this isn't an average security test — these attacks are just like real-world breaches (don't worry; no data or systems are harmed in this process).
For instance, these ethical hackers combine multiple systems, applications, and endpoints simultaneously, just like a real-world cybercriminal would. As the attack unfolds (while the hacker works their way through), the audit team closely evaluates how well the security controls withstand the attacks, assessing their resilience and effectiveness. Also, they examine how fast the defense system and IT/security team respond (i.e., how quickly they can identify and neutralize the breach). Once the control's effectiveness is assessed, the audit team carefully documents the findings in their reports.
Stage 3: Document The Findings & Suggest Remediation Measures
After evaluating the effectiveness of cybersecurity controls, the audit team prepares a formal audit report in which they specify the methodologies they used during VAPT, what type of stimulated attack they performed, and which particular open port allowed the attack to go undetected. They also provide suggestions regarding how the flaws or identified weaknesses in security controls can be fixed.
Note: A separate dedicated team should be assembled to implement the corrective actions suggested by the audit team.
Stage 4: Perform Follow-Up Assessment
Once the suggested changes have been made, the audit team will perform a follow-up cybersecurity audit to verify if they are properly executed.
Note: If your organization is undergoing a compliance audit, the external certified auditors will perform a follow-up cybersecurity assessment to verify if the suggested changes have been made properly. If the auditors find that these changes were applied correctly and that the IT controls function as required, they will issue a compliance certification.
Now you might ask – 'What benefits will an organization even get by undergoing a cybersecurity audit? What would one go through all the hassle – invest time, resources, and money?' Here's why.
Cybersecurity Audit Benefits
Listed below are two main benefits of cybersecurity audit.
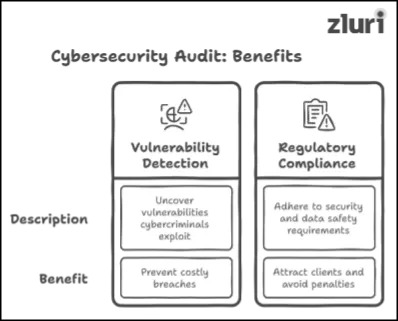
1: Helps Uncover Vulnerabilities That Cybercriminal Exploits
By undergoing a cybersecurity audit, you as an organization can gain complete visibility into lurking vulnerabilities or weak points (like — outdated software, unauthorized access points, or inadequate encryption protocol, basically any gaps that can leave your systems exposed to potential threats) that often go unnoticed during regular security assessments.
Note: These routine assessments usually lack the depth needed to spot the more elusive cyber risks hidden beneath the surface.
Once you have this visibility, it becomes much easier to take spot-on corrective measures (such as patching security endpoints or reconfiguring security controls to make them effective) and close those security loopholes before malicious actors can exploit them and comprise sensitive data. This way, you can prevent costly security breaches and reputational damage that comes with security failures.
2: Helps Adhere To Regulatory Compliance
To comply with regulatory compliance (such as ISO 27001, SOC 2, CCPA, GLBA, or any other security compliances), you, as an organization, need to meet the stringent security and data safety requirements set forth by them without fail.
But the real question is, 'How will one demonstrate that they have implemented the necessary measures outlined in the compliance regulations?' Here's where a cybersecurity audit comes into play.
By undergoing this audit, you can get your hands on a formal, detailed report (issued by an in-house team or external auditors) that serves as proof of evidence that you have put necessary measures in place and that they are effective enough to safeguard sensitive data (be it—PII, PHI, legal record, financial statement). You can submit this report to the certified auditors. The auditor will then carefully assess the report and check if your controls align with the compliance requirements or not. If all checks out, they'll issue the compliance certification!
Even better, once you've secured the compliance certification, you can display it on your organization's official website, marketing your commitment to maintaining data security. This way, you will attract the interest of potential clients, partners, and stakeholders (who value trust and credibility) and open doors to investment opportunities and business growth. That's not all; by having compliance certification in hand, you can even avoid incurring costly non-compliance penalties. (you can check this blog to get an idea about what non-compliance typically costs – Penalties For SOX Violation)
Now that you are familiar with the benefits, let's quickly address two important questions that most organizations frequently ask: 'How often should we perform cybersecurity audits? And when should we actually perform them?'
How Often & When To Perform Cybersecurity Audit?
Below, we’ve addressed the question in two sections for better understanding.
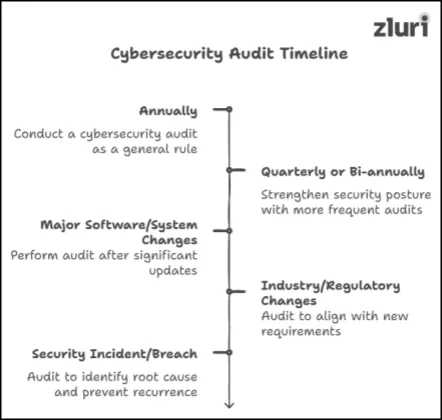
- How Often Should You Perform A Cybersecurity Audit?
Conducting a cybersecurity audit at least once a year is considered a general rule of thumb. However, if your budget permits, you can strengthen your security posture by performing it quarterly or bi-annually.
- When To Perform Cybersecurity Audit?
- Whenever your organization undergoes major software or system changes or upgrades, it’s crucial to perform a cybersecurity audit (it doesn’t matter if you’ve already performed it twice prior to the changes).
This is because, at times, the new systems or updates may introduce new gaps or vulnerabilities. Therefore, to detect such possibilities (before they cause any major issues) and troubleshoot them, you need to perform this audit on time.
- Likewise, when industry standards or regulatory requirements are changed or updated (don’t worry, this incident happens rarely), you will again need to perform this audit to assess whether your security measures remain in line with these new requirements.
- Lastly, when your organization encounters an unexpected security incident or breach, you need to perform a cybersecurity audit to identify the root cause of the issue and assess the damage. This will allow you to fine-tune your security defense and prevent similar incidents from happening in the near future.
Detect The Gaps Before Hackers Do With Cybersecurity Audit
You need to understand that — cybercriminals are becoming more sophisticated and evolving every moment. They’re always looking for the slightest vulnerabilities in an organization’s security infrastructure (what’s worse is, these gaps aren’t always obvious; they hide in often overlooked places). And this is the exact reason why performing a cybersecurity audit is non-negotiable. It helps uncover and address these loopholes before attackers even get a chance to exploit them. It is a must-perform practice to outsmart attackers and protect what matters most—your data and reputation.
But the real issue is that performing a cybersecurity audit can be a little expensive [e.g., you have to either pay for training an in-house audit team (if they lack the knowledge) or hire an external auditor (which is quite expensive)].
Fortunately, there is a way to cut the audit cost. Instead of bearing the cost of an external auditor (which you must incur every time you perform the audit), you can opt for automated solutions. These solutions do the job at a fraction of the cost and deliver faster, more accurate audit results (as human involvement is eliminated).
But which automated solution should you use? You can either use a risk management solution or an access review solution like Zluri (or both if needed). How is it helpful?
For example, Zluri’s access review solution offers discovery and auto-remediation features that simplify the access reviewing process. Here’s how it works: First, it automatically discovers all the users who are accessing applications (by integrating with the app). After that, it compiles the list of users, along with their data (such as role, status, designation, and more), in a centralized dashboard, making it easier for reviewers/auditors to evaluate whether the app access is relevant for them or not.
If any access misalignments are found (which depict access controls not functioning as intended), the reviewer can perform an on-spot action and revoke or modify the user access rights. Later, they can request the IT or security team to re-configure the access controls to fix their functioning. Moreover, if reviewers detect misalignment in large numbers (such as a large volume of inactive users who have app access), they can remediate them all with a single click with the help of Zluri’s bulk remediation action. Lastly, it generates a detailed UAR report outlining what has been reviewed and what actions have been performed. The best part is that you can also use these reports for direct compliance purposes.
In short, with solutions like this, you can not only test the effectiveness of your controls but also fix any anomalies on the spot — all without wasting extra time or effort.








.svg)














