As an IT manager, you constantly strive to strengthen your organization's identity governance and administration (IGA) practices. To achieve this, selecting the most suitable solution becomes crucial. It entails finding an IGA platform that bolsters security measures, optimizes user provisioning processes, and guarantees compliance adherence.
Explore the top 9 Oracle IGA alternatives that can empower your IT team in their quest for robust IGA capabilities.
Oracle identity governance simplifies user access management and governance in your organization. It automates access provisioning and deprovisioning processes, ensuring compliance by following predefined rules and guidelines. The platform can promptly identify and address any suspicious activity in real time by analyzing user behavior and access requests. Therefore, it effectively mitigates any security risks associated with access management.
However, despite its numerous features and functionalities, the solution has a few drawbacks that can impede your team's ability to effectively manage user access and safeguard your critical assets.
Drawbacks Of Oracle IGA
There are various limitations that your IT teams may encounter while using the Oracle IGA solution. It may include functionality, implementation, integration, or cost-effectiveness challenges. Below are a few potential limitations to consider:
- This may not be the ideal choice if you are looking for an easy-to-use solution. While it offers a comprehensive set of features, learning them can be challenging and requires a substantial time investment from your team to utilize its capabilities fully.
- The tool lacks a user-friendly interface, as navigating through numerous applications to obtain desired results can be cumbersome, making it difficult for your team to simplify access management and governance processes.
- The tool's intricate installation process can be complex and time-consuming, posing challenges and potential delays for your team. Resolving technical hurdles and dependencies is necessary to ensure the tool is fully installed and functional. Consequently, this hinders your team's ability to implement and utilize the tool effectively.
- Additionally, updating patches can be complex and burdensome, further complicating the effective management of the tool. These challenges can impact the user experience and require additional effort from your IT team to ensure smooth operation and maintenance.Considering the above scenarios, this article presents a curated list of top-notch IGA alternatives, offering comprehensive features and functionalities that empower you to elevate your IGA practices to new heights.
List Of Top 9 Oracle IGA Alternatives
Whether you're looking for cost-effective solutions, enhanced user experiences, or additional functionalities, these alternatives provide viable IGA tools that are worth considering for your IT team. Let's take a closer look at them:
1. Zluri
Imagine a medium-sized organization with numerous employees and a wide range of applications. Each employee has different access needs based on their role, department, and seniority level. Over time, as employees join, change roles, or leave the company, managing their access becomes increasingly complex and prone to errors.
Further, manual access provisioning and deprovisioning processes are time-consuming and cumbersome, leading to delayed access for new employees and potential security risks from outdated permissions for former employees. Maintaining a clear overview of who has access to what becomes challenging, making it difficult to ensure compliance with internal policies and industry regulations.
To overcome this, Zluri offers an intelligent and advanced identity governance and administration platform designed to empower your IT team in efficiently managing and monitoring user access. It simplifies regular IGA tasks, offering a comprehensive solution that ensures compliance, enhances productivity, and bolsters security.
The platform incorporates workflow automation to efficiently handle user access requests and access reviews. It prioritizes crucial IT functions, including authentication, authorization, data protection, and regulatory compliance. With Zluri, your IT team gains complete control and clear visibility over user access management.
The platform offers customizable access permissions based on roles, departments, and seniority levels. It ensures that each employee has the appropriate access to necessary tools with the required level of approval for their success.
Key Distinctive Capabilities of Zluri's IGA:

SaaS Discovery Engine: Real-Time User Data at Your Fingertips
Zluri's discovery engine incorporates nine discovery methods: MDMs, IDPs & SSO, direct integration with apps, finance & expense management systems, CASBs, HRMS, directories, desktop agents (optional), and browser extension (optional). These methods enable in-depth analysis, unveiling valuable user data and providing crucial insights into your SaaS applications, setting Zluri apart.

Zluri’s nine discovery methods
Recognizing the vulnerability of identity systems to access theft and breaches, Zluri ensures assured integration, granting complete control and visibility. Embracing Zluri's integration fortifies your defenses against potential breaches, ensuring heightened security and peace of mind.
Zluri's robust integration capabilities seamlessly integrate with popular identity systems and core applications, achieving an impressive 50% scope coverage. This facilitates unified access and streamlines authentication processes, enhancing the user experience.
The extensive integration ensures a smooth and efficient user experience, facilitating seamless data flow and maximizing productivity. With integration across 300+ SaaS apps, Zluri delivers real-time data, insights, and AI-powered alerts. API-based integration ensures deep data discovery across all apps, providing 100% visibility.
Elevating Efficiency & Access Control: Zluri’s Automation Engine
Zluri's automation engine features self-operating access workflows, ensuring efficient and automated reviews. With a defined rule and policy engine, Zluri sets up workflows to automatically consume data, providing better granularity and contextual insights from the Data, Discovery, and Automation engines.
Zluri's IGA platform puts you in control, effortlessly strengthening security. IT teams can leverage features like user provisioning, automated access reviews, and self-service access requests to efficiently manage and enhance your organization's security.
Curious about how Zluri transforms identity governance & administration to empower your access management?
Our robust IGA platform comprises 3 critical components that drive its effectiveness:

User Lifecycle Management
Zluri streamlines the complete user lifecycle control from onboarding to offboarding. It streamlines access management by automating the process of granting and revoking access, making it easier and more efficient. How does it do that? Zluri offers automated provisioning and deprovisioning solutions that enable efficient management of user access in the cloud environment. It enables secure access to sensitive data by assigning permissions based on user roles and monitoring all IT activities.

Zluri empowers your IT teams to create personalized onboarding and offboarding workflows (playbooks) for effortless provisioning and deprovisioning. With a few clicks, you can assign customized permissions based on roles, departments, and seniority levels, ensuring that each employee receives appropriate access to the necessary tools approved at the right level.

As a comprehensive user lifecycle management platform, it has 3 valuable USPs to ensure proper access management:
- Customizable workflows: Zluri distinguishes itself with its highly customizable workflows, offering the flexibility to set up pre-defined workflows that perfectly align with your organization's specific needs. This eliminates the cumbersome manual process of granting and revoking access permissions. The user-friendly interface empowers you to create custom workflows based on user roles, departments, and seniority levels, ensuring efficient and effective access management.

Onboarding workflow

Offboarding workflow
- Intelligent App Recommendations & In-App Suggestions: Zluri provides powerful contextual-based app recommendations, considering user profiles, departments, seniority levels, and other factors. This streamlines the process of selecting the most suitable apps for provisioning, making it convenient for your team to make informed decisions.

Moreover, Zluri boosts user productivity by offering in-app suggestions, and guiding users with recommended actions for more efficient task performance.

- Automation Playbooks: With Zluri, onboarding, and offboarding workflows are saved as predefined \"playbooks,\" removing the need to recreate them for each user. This streamlined approach boosts operational efficiency, making the process more seamless and productive.

Onboarding Playbooks

Offboarding Playbooks
Ad-hoc Access Request Management (Ticketless Solution)
Zluri provides the Employee App Store (EAS), a self-serve model that revolutionizes access request management. This innovative platform simplifies ad-hoc access requests, especially during role changes, empowering your IT team with full control over granting access based on job roles and permissions. Your IT team can customize the content and visibility of apps for each employee, ensuring a personalized and relevant experience.

By leveraging the EAS, your team can focus on strategic initiatives instead of repetitive approval tasks. It eliminates the burden of handling numerous requisitions, approvals, and revocations. Your IT admins and designated approvers can efficiently review and approve access requests, ensuring alignment with job responsibilities. Higher-level authorities can override decisions by lower-level admins or managers, enabling efficient decision-making and tight access control.
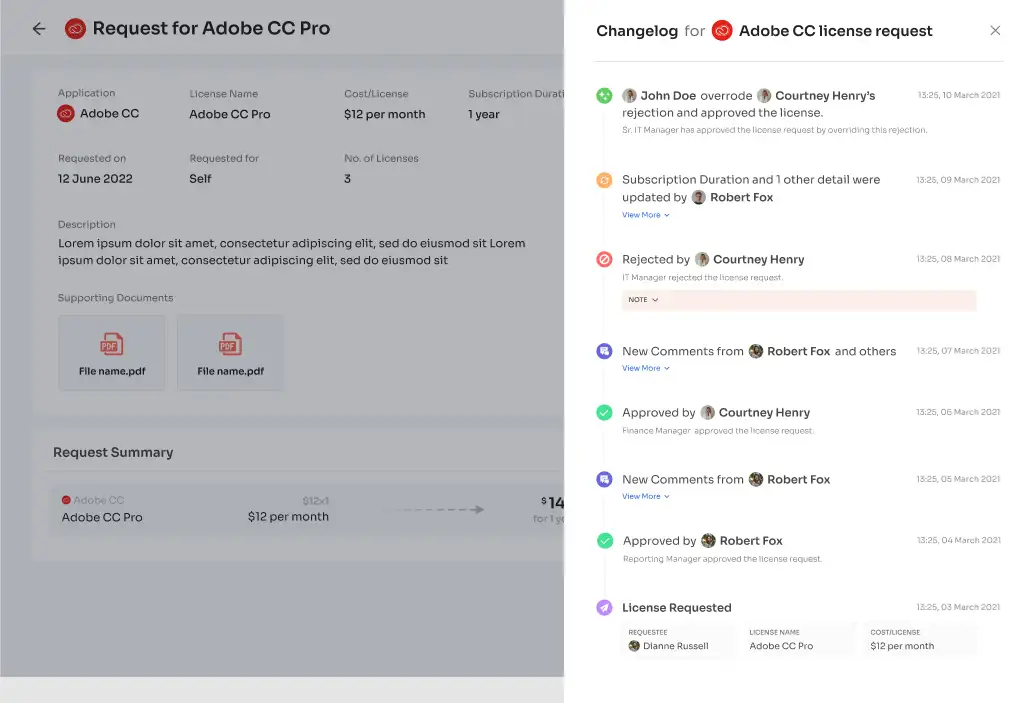
Moreover, its \"changelog\" feature allows employees to track request status and updates. It provides deep insights into approvals, rejections, changes in requested license tiers, and admin comments, ensuring visibility and accountability throughout the access management process.
Robust Access Certification Helps You Stay Compliant & Secure
Zluri recognizes the utmost importance of compliance for your organization. To achieve this, it streamlines the access certification process, offering a well-organized and automated approach to review and authenticate user access and entitlements.

Zluri's IGA platform provides a centralized platform for your IT teams and auditors to efficiently review and report on users' access. Conducting regular access certifications allows you to validate and evaluate user access privileges, ensuring compliance with industry regulations and internal security policies.

Zluri's access review feature offers two key benefits for your IT teams:
- Intelligent Automation: Effortlessly set review parameters, select reviewers, and schedule campaigns through intelligent automation.
- Rule-Based Assessment: Evaluate user access rights based on predefined rules, saving time and reducing errors compared to manual spreadsheet reviews.
Let's delve into the distinctive features step by step:
- Complete Access Control with Continuous Reviews:
Zluri's innovative approach to access reviews offers continuous certifications, ensuring precise control over access privileges. Regularly auditing and validating access permissions reduces the risks of unauthorized entries and potential data breaches. Recurring certifications swiftly identify and resolve security vulnerabilities, assuring robust access controls to safeguard sensitive information.
- Strategic Access Reviews through Scheduled Certifications:
Zluri's scheduled certifications allow you to strategically plan and conduct access reviews at predetermined intervals, minimizing the risk of overlooking critical access issues.

Industry-standard certificate templates further streamline the certification process, ensuring a comprehensive, accurate, and compliant review aligned with recognized guidelines.
- Enhanced Data Security with Real-Time Access Reviews:

Zluri's AI-driven real-time access reviews analyze access patterns, user behavior, and system logs to swiftly identify unusual or risky activities. Prompt detection and alerts enable you to proactively mitigate security threats and protect sensitive data. Continuous monitoring provides real-time visibility into access privileges, allowing swift resolution of potential access-related concerns.
- Unlocking the Power of Intelligent AI Compliance: Zluri's AI compliance capabilities offer invaluable insights and recommendations, ensuring seamless alignment with industry regulations and standards.

Leveraging Zluri's AI technology streamlines the compliance process, making it easier for your organization to meet regulatory requirements while minimizing the risk of compliance violations. Integrating AI-driven intelligence empowers your organization with the tools needed to proactively maintain a compliant and secure environment.
- Auto-Remediation Capability:
Zluri goes beyond reviews with its auto-remediation capabilities. Swift corrective actions are taken when access violations are detected, enhancing security and ensuring compliance. Revoking access for terminated employees or those with outdated privileges mitigates the risk of unauthorized data breaches, ensuring data integrity.
With Zluri's powerful IGA platform, you can rest assured that your organization's access management is efficient, compliant, and secure.
Unlock the full potential of Zluri's Identity Governance by scheduling a personalized demo today and experience it firsthand!
Pros
- Zluri differentiates itself from traditional IGA tools by providing a hassle-free implementation process. Its user-friendly interface makes it easy for your IT teams to quickly adopt and navigate the platform, reducing the learning curve and increasing productivity.
- It prioritizes user satisfaction with its responsive customer support. The dedicated support team is readily available to address any concerns or issues that may arise during platform usage. This ensures a smooth and efficient experience, instilling confidence in relying on Zluri for your IGA needs.
- Zluri's seamless integration with common Single Sign-On (SSO) tools simplifies employee login with a single set of credentials, improving convenience and enhancing security by centralizing access control and reducing password-related vulnerabilities.
Customer Rating
- G2: 4.8/5
- Capterra: 4.9/5
2. Imprivata Identity Governance
Imprivata Identity Governance is a specialized solution designed to automate the entire user lifecycle, simplify auditing processes, and provide on-demand analytics for swift threat evaluation and remediation.
With Imprivata Identity Governance, organizations can ensure that the right individuals are granted access while preventing unauthorized access. The tool automates the management of user lifecycles, enabling secure and role-based access from day one. This streamlined approach enhances security and reduces the risk of unauthorized access incidents.
The platform also offers streamlined auditing and analytics capabilities, providing organizations complete visibility into user behavior. By combining rights and usage data into a single analysis report, organizations can gain valuable insights and promptly detect any suspicious activities or anomalies. This enables proactive threat mitigation and enhances overall security posture.
Pros
- The tool enables convenient remote sign-in for your team, allowing them to authenticate and access secure networks with just a click on their cell phone. It eliminates the wait for verification texts, saving time and enhancing productivity with faster connectivity.
- Its Intuitive Admin console serves as a powerful tool for your IT team, providing seamless management of admin activities with minimal assistance. This user-friendly console lets your team gain insights into login patterns from different endpoints, empowering them to anticipate and address potential security breaches proactively.
Cons
- Imprivata has limited customization of reports, providing a fixed set of reports. This restricts the ability of admins and end users to create customized reports based on their specific needs. The lack of flexibility in tailoring reports can limit the depth and specificity of insights, impacting decision-making and analysis.
- Customizing or implementing new developments or customizations in the tool can be time-consuming. It requires coordination and collaboration with Imprivata's support team, which can delay deploying new features and hinder your team's agility in adapting to evolving business requirements.
Customer Rating
- G2: 4.5/5
- Capterra: 4.7/5
3. CyberArk Privileged Access Manager
CyberArk Privileged Access Manager acts as an IGA platform and provides centralized visibility and control to minimize the risk of unauthorized access, excessive privileges, and accumulation of access rights. The tool enables your IT team to gain a clear understanding of user access and authorizations across a wide range of resources, including highly privileged accounts.
With CyberArk Privileged Access Manager, organizations can continuously review and assess user access, enforcing the principle of least privilege. By making informed decisions about user permissions, you can ensure that users only have the necessary access required to perform their job responsibilities, reducing the risk of unauthorized actions and potential security breaches.
Furthermore, Leveraging intelligent analytics, the tool proactively detects risks and identifies areas of non-compliance. Thus, you can make critical remediation decisions and take necessary actions to maintain compliance with even the most stringent regulations. By leveraging these capabilities, you can enhance your organizational security posture, mitigate potential threats, and maintain compliance with regulatory requirements.
Pros
- If you operate in the payment card industry, CyberArk is an ideal choice. It specifically caters to compliance requirements like the PCI-DSS and provides the necessary tools to meet them. By implementing CyberArk, your IT team can align their access management practices with PCI-DSS guidelines, ensuring the security and protection of users’ data.
- The tool’s SSO integration with MFA offers a seamless and user-friendly experience. Your team can access all their daily applications from a single dashboard with one click, saving time and improving productivity.
Cons
- Implementing the tool necessitates using virtual machines (VMs), which can increase the complexity of the deployment process. This added complexity may present challenges for you and your team in terms of the time and effort required for successful implementation.
- If your organization has many users who need access to privileged accounts, this tool can be costly. The license model operates on a per-user basis, which means that larger organizations may incur higher expenses due to the increased number of users requiring access.
Customer Rating
- G2: 4.2/5
- Capterra: 4.3/5
4. Brainwave GRC
Brainwave GRC is an Identity and Access Management (IAM) system primarily focused on managing access rights. Its identity Analytics provides advanced capabilities that enable you to analyze and evaluate access rights in-depth. It offers robust functionalities for conducting comprehensive access reviews, detecting excessive or inappropriate access privileges, and ensuring adherence to regulatory requirements and industry best practices.
By integrating Identity Analytics into your IAM environment, you can harness its powerful features to gain complete control over your access rights and effortlessly achieve compliance.
By utilizing Identity Analytics alongside your IAM system, you can extend the capabilities of your access management processes. This combination allows you to manage access rights effectively, gain valuable insights into access-related risks, and make data-driven decisions to strengthen your security posture and compliance efforts.
Pros
- The tool can be customized to support any Identity and Access Management (IAM) data type. Whether you have a specific IAM system in place or a unique data structure, the tool can be tailored to handle and analyze your specific data requirements.
- The platform incorporates implemented controls that are designed to be clear and user-friendly. This means that your team and end users can easily understand and navigate the system without requiring extensive assistance or training, reducing the need for constant hand-holding or support from you.
Cons
- Configuring new campaigns can be complex, requiring expert knowledge and hands-on experience. It involves understanding intricate configuration settings, mapping data structures, defining rules, and establishing workflows. This complexity can be challenging for your IT team.
- Due to technical limitations or system constraints, the tool may experience delays in processing requests and providing timely responses. This delay can impact the overall efficiency of data retrieval and analysis, potentially causing frustration for your team, who require real-time or quick access to GL information.
Customer Rating
- G2: no reviews
- Capterra: no reviews
5. Lumos IGA
Lumos IGA is an innovative tool that revolutionizes compliance management and empowers your team for strong identity governance and administration (IGA). With its comprehensive feature set, Lumos IGA simplifies compliance complexities and facilitates regulatory navigation.
The tool's primary focus is on authentication, ensuring secure and accurate user identification before granting access to resources. It offers robust authorization capabilities, enabling granular access controls aligned with organizational policies and regulatory requirements.
Lumos IGA excels in regulatory compliance, assisting your team in monitoring, documenting, and enforcing compliance with regulations and industry standards. It provides valuable insights into compliance requirements and streamlines compliance-related processes, reducing the burden on your team and minimizing the risk of non-compliance. Thus, your team can confidently navigate compliance challenges, emphasizing critical aspects of identity governance and administration.
Pros
- The tool's user-friendly interface prioritizes ease of use, enabling team members to effortlessly navigate and operate the tool. The intuitive design and clear navigation make it simple for team members to access the desired features and functionalities, saving valuable time and effort.
- It offers an auto-provisioning feature that automates the user provisioning process, eliminating the need for manual setup and configuration. This saves time and ensures consistent and accurate provisioning across your systems and applications.
Cons
- The platform lacks transparent pricing information, such as clear details about its plans and pricing tiers, on its website. This lack of transparency can create confusion and make it challenging to compare Lumos with other tools available in the market.
Customer Rating
- G2: 4.8/5
- Capterra: no review
6. IBM Security Verify Governance
IBM Security Verify Governance is a robust identity governance and administration solution that retrieves and manages data from multiple sources. With its modular design, directory integrator, and database capabilities, this solution offers a comprehensive approach to governing and administering identities within an organization.
This appliance-based platform provides a wide range of capabilities to manage user identities throughout their lifecycle effectively. From provisioning to auditing and reporting, IBM Security Verify Governance offers robust features that ensure proper access and activity monitoring. Its comprehensive features cover lifecycle management, compliance, and analytics, making it suitable for both on-premises and cloud-based environments.
Moreover, with its SoD controls, including for SAP, the platform enables risk and compliance managers to identify violations and make appropriate access decisions quickly.
Pros
- The platform provides robust security measures that facilitate efficient user access management and conduct comprehensive risk-based authentication analysis before granting system or application connectivity.
- With its versatility, this tool brings the convenience of seamless operation to your team, allowing for smooth functionality in various scenarios. Whether your team works in cloud environments or offline on workstations, this tool ensures they can perform their tasks without interruption.
Cons
- This solution may not be the most suitable choice if you prioritize affordability due to its pricing model. The pricing is determined by the number of features included, which means that utilizing specific functionalities (considered as add-ons) may lead to additional costs.
- The password policies may be too basic and fail to enforce vital password requirements. Without robust password policies, there is a higher risk of users selecting weak or easily guessable passwords, leaving the accounts vulnerable to unauthorized access and potential security breaches in your organization.
Customer Rating
- G2: 4.3/5
- Capterra: no reviews
7. SailPoint Identity
The SailPoint Identity Platform offers a comprehensive solution for managing identities across your organization. By centralizing user provisioning, deprovisioning, and lifecycle management, this platform gives your team complete visibility and control over user access.
With SailPoint Identity, you can implement granular access controls, ensuring that users have the precise level of access required for their job functions. By leveraging role-based access controls (RBAC) and attribute-based access controls (ABAC), your IT admins can define and enforce access policies based on user roles, responsibilities, and other contextual factors.
This advanced approach empowers your organization with enhanced security measures and minimizes the risk of unauthorized access. By aligning user access with organizational needs and policies, the SailPoint Identity Platform strengthens your overall security posture and facilitates compliance with regulatory requirements.
Pros
- This solution offers a seamless access governance experience, allowing your team to integrate with your current systems effortlessly. By integrating with your existing infrastructure, it allows you and your team to have a comprehensive view of your entire access management process
- The tool provides an improved access management solution, allowing your team to easily oversee and control each user access in your organization. This level of visibility empowers them to effectively monitor and regulate user access, leading to efficient tracking, governance, and auditing processes.
Cons
- The tool demands a significant time investment from your team to fully grasp and utilize its capabilities. This can limit their ability to concentrate on crucial tasks, such as risk prevention and compliance maintenance.
- If you require a highly flexible and customizable solution, this tool may not be the most suitable choice. Its limitations in terms of customization options can present significant constraints when attempting to tailor the tool to meet your organization's specific requirements.
Customer Rating
- G2: 4.4/5
- Capterra: 4.2/5
8. ForgeRock IGA
ForgeRock Identity Governance leverages the capabilities of the ForgeRock Identity Cloud, coupled with advanced AI and machine learning, to establish robust identity governance practices within your organization. By harnessing this powerful combination, ForgeRock Identity Governance ensures that every identity is granted only the necessary level of access.
One of the key strengths of ForgeRock Identity Governance is its ability to automate various identity management processes. It streamlines account and entitlement provisioning, enabling efficient workflows for access requests. With the automation of these tasks, your IT team can reduce their workload and focus on more critical activities.
Furthermore, ForgeRock Identity Governance offers comprehensive features for ongoing access certification. This allows you to regularly review and validate users' access privileges, ensuring that they continue to have appropriate access rights.
Pros
- It offers an intuitive and user-friendly interface, enabling your team to manage access permissions and enhance overall security effortlessly. Thus, it simplifies granting and revoking access, promoting efficient access management practices within your organization.
- The platform offers seamless integration capabilities and smooth connectivity with various systems and applications. With easy integration, your IT team can quickly incorporate the tool into its existing infrastructure without significant disruptions or complex configurations.
Cons
- The tool does not support integration with certain systems, such as Unix-based systems. This limitation can hinder your team's ability to effectively manage access to these systems and potentially introduce security risks to your organization.
- The platform's limited reporting capabilities can hinder your team's ability to effectively monitor and assess various access permissions, making identifying gaps during audits challenging. This limitation can impact your organization's compliance with regulatory requirements and increase the risk of security breaches.
Customer Rating
- G2: 4.4/5
- Capterra: 4.8/
9. RSA Identity Governance and Lifecycle
RSA Governance & Lifecycle is a robust Identity Governance and Administration (IGA) tool designed to empower IT teams with comprehensive capabilities for managing identities and user access. One of the key features of RSA Governance & Lifecycle is its ability to facilitate access certification processes. This feature streamlines identity governance by automating the certification of user access rights. It enables your IT team to efficiently review and validate user access, ensuring that only authorized individuals have the appropriate level of access to resources.
The tool helps your IT team manage the entire lifecycle of user identities, from provisioning to deprovisioning. It supports centralized user administration, role-based access controls, and automated workflows, enabling your team to enforce consistent access policies and reduce the risk of unauthorized access.
Additionally, RSA Governance & Lifecycle offers comprehensive reporting and analytics capabilities. It provides insights into access patterns, usage trends, and compliance status, giving your team valuable insights regarding access rights and identity governance.
Pros
- It boasts a straightforward and easy configuration process, enabling your team to quickly set up and customize the tool to their specific needs. This simplifies the implementation process and saves valuable time and effort for your IT team, allowing them to focus on other critical tasks.
- The platform is designed with user-friendliness in mind, providing dedicated versions for iPhones and iPads. This ensures a seamless and intuitive user experience for your team members accessing the software on these devices.
Cons
- Its collection-based architecture necessitates a scheduled process for provisioning groups. This means that user provisioning cannot occur in real time since the tool requires the collection of account information from end targets before provisioning the groups. As a result, there may be delays in user access provisioning, which could potentially impact operational efficiency and agility.
- If you are considering migrating from one IGA tool to another, this may not be the most suitable option due to its initial complexity. Thus, it can be a bit complicated for your team to use initially, which may require additional time and effort to learn and utilize effectively.
Customer Rating
- G2: 4.7/5
Capterra: 4.6/5









.svg)



.svg)
.svg)
.svg)
.svg)

.svg)

.svg)

.svg)
















.webp)







.webp)
.webp)





.webp)