Role-based access control (RBAC) and Relationship-Based Access Control (ReBAC) are two well-known access control models widely used in various organizations. As an IT manager, you might be pondering which option is the right fit for your organization.
While RBAC offers a structured approach with assigned roles and permissions, it lacks the dynamic behavior and flexibility required for more complex scenarios. On the other hand, ReBAC introduces a fine-grained control mechanism by establishing relationships between users and objects, but it may not be as easy to manage permissions as RBAC.
This article compares these two authorization models, exploring their strengths, limitations, and ideal use cases.
When users log into your organization's SaaS apps, ensuring they have the right level of access becomes a crucial and challenging task. Granting insufficient access can hinder productivity and limit their capabilities, while excessive access can lead to potential security risks and data breaches. To strike the right balance, authorization plays a pivotal role. It involves confirming the user's identity (authentication) and determining whether they have the correct access to specific resources for the appropriate duration (authorization).
Among the various authorization methods, two widely adopted models are role-based access control (RBAC) and relationship-based access control (ReBAC). These approaches provide distinct approaches to managing user access and permissions, each with its strengths and considerations.
RBAC is a common approach to access control, where permissions are grouped into roles like admin, editor, or viewer and then assigned to users. However, the need for more precise controls arises as applications become more intricate. This is where ReBAC enters.
Instead of directly assigning permissions to users or groups, ReBAC establishes relationships between users and specific objects, such as projects, lists, or folders, at different levels of the resource hierarchy. These relationships are then used to determine access rights, resulting in a more nuanced and granular access control model.
RBAC vs. ReBAC: Choosing The Right Access Control Model
Access control is critical to information security, ensuring that the right users have appropriate access to resources in a system. Both RBAC and ReBAC models are helpful, but understanding their strengths and weaknesses is essential for selecting the most suitable approach for specific use cases and scenarios.
RBAC: Use Cases & Scenarios
RBAC is a widely adopted access control model, particularly in organizations with well-defined roles and responsibilities. It is well-suited for scenarios where user access can be categorized into distinct roles and where the roles have consistent and stable permissions.
Some typical use cases for RBAC include:
- Enterprise Applications:
RBAC is widely used in large-scale enterprise applications to manage access control efficiently. In such systems, users have different roles based on their job functions, such as administrators, managers, employees, or customers. RBAC allows organizations to define roles and associate them with specific sets of permissions, ensuring that users only have access to the functionalities and data relevant to their roles.
- Cloud Services and SaaS Platforms:
RBAC is valuable in cloud computing environments and Software-as-a-Service (SaaS) platforms. These platforms often cater to multiple clients with varying access requirements. By employing RBAC, administrators can easily control access for each client based on predefined roles, preventing unauthorized access to critical resources.
- E-commerce Platforms:
RBAC is utilized in e-commerce websites to manage user access and privileges. Roles like customers, administrators, and support staff are established, each with tailored permissions. RBAC ensures that customers can access their accounts while administrators have the necessary tools to manage the platform and assist users.
- Financial Services:
Financial institutions deal with vast amounts of sensitive financial data. RBAC allows them to establish strict access controls based on job functions, departmental roles, and regulatory compliance requirements. Roles like tellers, managers, and auditors are granted specific permissions, enabling efficient and secure financial data management.
Overall, RBAC offers a scalable and efficient access control solution for a wide range of applications and industries. It simplifies user management, enhances security, and ensures users can access the resources they need based on their designated roles and responsibilities.
ReBAC: Use Cases & Scenarios
ReBAC, conversely, is more suitable for complex and dynamic access control environments, where access decisions depend on intricate relationships between users, resources, and other entities.
Some typical use cases for ReBAC include:
- Collaborative Environments:
ReBAC can be applied in collaborative platforms or document management systems where access to shared resources depends on dynamic group memberships, project roles, and collaborative relationships. Users may have varying access rights based on their involvement in specific projects or their membership in certain collaborative groups.
- Research Data Repositories:
In research or academic environments, ReBAC can be utilized to manage access to research data repositories. Access rights can be governed by complex relationships such as data ownership, authorship, institutional affiliations, and collaboration structures. Researchers may be granted different levels of access to datasets based on their contributions or roles within the research project.
- Organizational Workflows:
ReBAC can be beneficial in scenarios where organizational roles and reporting structures determine access to files and resources. For instance, employees in managerial positions may automatically gain access to files created by their subordinates due to their hierarchical relationship within the organization.
- Supply Chain Management:
In supply chain management systems, ReBAC can help regulate access to sensitive supply chain data based on the relationships between suppliers, manufacturers, distributors, and other stakeholders. Different participants in the supply chain may have distinct access rights depending on their role and position in the chain.
- Multi-Tenant SaaS Platforms:
In multi-tenant Software-as-a-Service (SaaS) environments, ReBAC can be employed to handle access control across different tenants. The relationships between tenants, administrators, and users can influence access rights, ensuring that each tenant's data and resources are appropriately secured and isolated.
It's important to note that the specific implementation and features of ReBAC would depend on how the hypothetical model is designed and structured.
Quick Glance at Key Differences & Similarities
- Relationship Model: The primary distinction between RBAC and ReBAC lies in their access control models. RBAC (Role-Based Access Control) focuses on role-based permissions, where users are assigned to predefined roles, and each role has associated permissions. On the other hand, ReBAC (Relationship-based Access Control) incorporates complex relationships between users, resources, and other entities as the basis for access control decisions. These relationships can involve ownership, group memberships, hierarchies, or other custom associations that govern resource access.
- Complexity: RBAC is generally simpler and easier to implement compared to ReBAC. RBAC's straightforward role-to-permission mapping makes it suitable for straightforward access control scenarios, especially in environments with clear and stable role definitions. It is often the preferred choice when access control requirements are relatively straightforward, and roles can be clearly defined. On the contrary, ReBAC's consideration of complex relationships introduces a higher level of complexity. It becomes more appropriate in environments where access control requirements are dynamic, and access decisions depend on intricate relationships between users and resources.
- Flexibility: ReBAC offers greater flexibility in defining access rules compared to RBAC. RBAC's rigid role-based approach may have limited flexibility in handling complex access scenarios where relationships play a crucial role. ReBAC's relationship-driven approach allows for more nuanced and context-aware access decisions. It provides the ability to tailor access control based on various factors, such as ownership, project participation, or hierarchical structures, enabling a more adaptable and fine-grained access control mechanism.
- Auditability: Both RBAC and ReBAC provide good auditability of access control decisions. RBAC's role-based mapping often results in straightforward and easily traceable audit logs, as access decisions are directly tied to predefined roles. In contrast, ReBAC's relationship-driven model may require more comprehensive logging to capture the intricate relationships influencing access decisions. While ReBAC's audit logs might be more complex, they offer valuable insights into how access rights are determined based on relationships, helping to maintain accountability and security.
The choice between RBAC and ReBAC depends on the nature of the access control requirements in a given system. RBAC is ideal for straightforward scenarios with clear role definitions, while ReBAC is better suited for environments where complex relationships govern resource access.
Each model has its strengths and weaknesses, and the decision should be based on the specific access control needs and the complexity of relationships between users and resources within the system.
Factors to Consider When Choosing Between RBAC and ReBAC
When choosing between RBAC and ReBAC, there are several factors to consider:
1.Nature of your organization's IT Infrastructure
The organization's IT infrastructure plays a crucial role in determining the most suitable access control model. If the infrastructure is relatively straightforward, with clearly defined roles and permissions, RBAC might be the better choice. On the other hand, if the IT environment is complex, involving dynamic relationships between users, resources, and other entities, ReBAC might provide a more flexible and adaptable solution.
2.Complexity of Access Control Requirements
The complexity of access control requirements is a significant factor in selecting the appropriate model. RBAC is generally more straightforward and easier to implement, making it a suitable option for organizations with relatively simple access control needs. However, if access control decisions depend on intricate relationships, such as ownership, project involvement, or hierarchical structures, ReBAC can better accommodate these complex scenarios.
3. Granularity of Access Control
The level of granularity required for access control is an essential consideration. RBAC typically provides a coarser level of access control, where permissions are associated with roles rather than individual users. For scenarios demanding fine-grained access control, where access decisions need to consider specific relationships between users and resources, ReBAC offers the capability to define more nuanced access rules.
4. Flexibility & Scalability
Flexibility and scalability are crucial factors for access control models, especially in dynamic and growing organizations. ReBAC's relationship-driven approach offers greater flexibility in defining access rules, allowing for more context-aware access decisions. It can adapt to changes in the organization's structure and access control requirements more seamlessly. On the other hand, RBAC might be sufficient for static or less complex environments, but it may face limitations when trying to accommodate evolving access needs.
To sum up, each model has its strengths, and the right choice will depend on the specific characteristics and demands of the organization's access control environment.
If you're searching for a platform that simplifies the task, look no further than Zluri. This innovative solution goes above and beyond traditional approaches by seamlessly combining the strengths of both models, resulting in a unique and comprehensive access control solution.
Let's explore how.
Zluri's IGA: Pioneering Access Governance in the New Tech Era
Many access control approaches lack granular insights into individual actions, proving ineffective in today's complex business and regulatory environments. With organizations relying on multiple systems, applications, and users accessing them from diverse devices and locations, access governance has become intricate, posing security challenges.
Zluri introduces an advanced Identity Governance and Administration (IGA) platform, offering real-time visibility into user activities and access details, including who has access to what, when, and from where.

Zluri's IGA solution empowers your IT teams with a wealth of user access data, contextual access control, fine-grained authorization, robust security controls, and comprehensive auditing capabilities. By breaking the barriers of conventional systems, Zluri grants IT teams unparalleled control and security over user permissions. With Zluri, you can streamline IT audits, ensure regulatory compliance, and effectively take charge of access control with confidence.
The IGA platform revolutionizes access governance through flexible features that customize permissions based on roles, departments, and specific needs, ensuring every employee has the appropriate access. It allows fine-grained access policies based on various attributes and conditions, granting access only to authorized users under specific circumstances.

The tool streamlines access requests, approvals, and access reviews through workflow automation, ensuring efficiency. It empowers IT teams with control over authentication, authorization, data protection, and compliance, making IT audits effortless and user access reviews simplified. With Zluri, security risks are reduced, and sensitive data and resources are protected.
Explore Zluri's unmatched features that distinguish it from other IGA tools, demonstrating its unparalleled capabilities.

- Take your access governance to new heights with Zluri's top-notch discovery engine
The first crucial task in creating a strong access governance policy involves discovering and mapping the relationships between identities, users and resources. Zluri offers your IT admin a clear overview of authorized actions associated with each identity across all organizational assets.
Zluri equips your IT team with effortless analysis and discovery of all SaaS applications and user-related data, utilizing its 9 effective discovery methods. These methods encompass MDMs, IDPs & SSO, direct integration with apps, finance & expense management systems, CASBs, HRMS, directories, desktop agents (optional), and browser extension (optional).
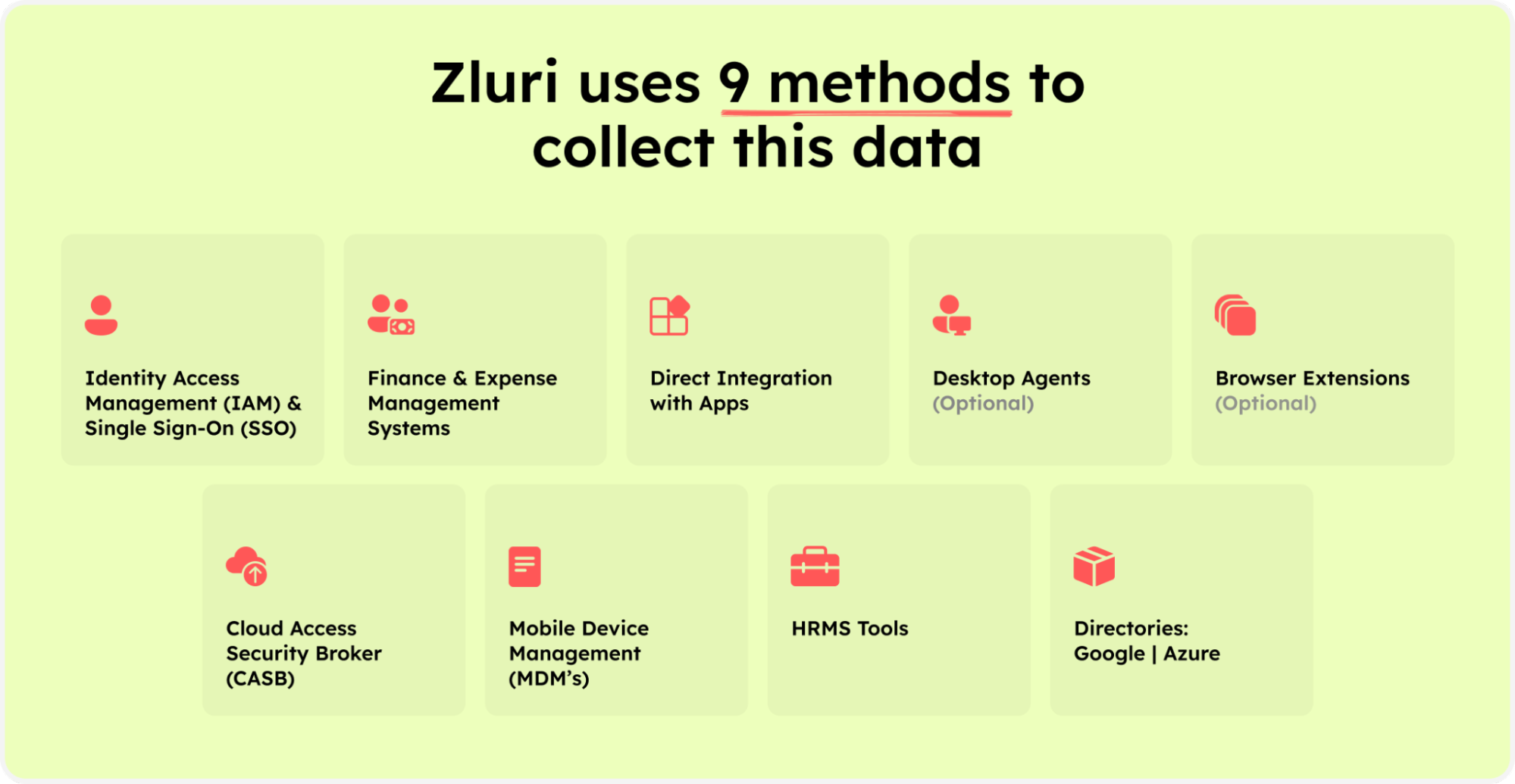
Zluri’s nine discovery methods
As per KuppingerCole’s report, Zluri provides a single source-of-truth for all SaaS apps in your organization.
By employing these discovery methods, your team can easily discover application access, active users, granted permissions, critical user categorization, and more. Zluri streamlines the process, providing clear insights into your organization's application usage and access patterns.
Zluri seamlessly integrates with popular identity systems and core applications, ensuring smooth authentication processes for a seamless user experience. With access to over 300 SaaS apps, Zluri delivers real-time data, insights, and AI-powered alerts, offering 100% visibility through API-based integration. As a result, it strengthens your security measures, providing complete control and visibility to safeguard against potential breaches, thereby bolstering overall security.
Moreover, Zluri boasts an extensive library of over 240,000 apps, enabling granular-level access data that grants comprehensive insights into user permissions within your SaaS ecosystem. IT teams leverage Zluri's robust integration capabilities for enhanced productivity and seamless data flow, empowering your organization to thrive.
- Zluri's Automation Engine: Self-Operating Access Workflows With Defined Rules & Policies
Zluri's Automation Engine drives both security and efficiency by adeptly handling access workflows, guaranteeing strict compliance with policies. Through the establishment of automation rules and triggers, it facilitates personalized and autonomous access and review workflows. It showcases self-operating access workflows, ensuring that data is automatically consumed.

With the Data, Discovery, and Automation engines working together, it provides us with better granularity and contextual insights, enabling streamlined review automation and a well-defined rule and policy engine. This results in streamlined administrative processes and maximized IT management capabilities.
Discovering the Core Capabilities of Zluri's Identity Governance and Administration (IGA):

Ensuring Appropriate Access for Designated Individuals through ULM Solution
Zluri's user lifecycle management (ULM) solution simplifies identity governance and administration by seamlessly bridging access provisioning, ad-hoc access requests, and access revocation. This ensures smooth and efficient management of user access privileges, enhancing security and compliance for IT teams. The ULM system automates access provisioning based on predefined roles, reducing errors and administrative workload.

Similarly, it streamlines deprovisioning, revoking access rights when users leave or change roles, thus minimizing unauthorized access risks and data breaches. Zluri's approach maintains robust security measures and aligns with identity governance and administration best practices.
Zluri presents a proficient user access lifecycle management with 3 distinctive attributes:
- Customizable Workflows: Zluri's adaptable pre-defined workflows facilitate predefined configurations tailored to suit your organization's specific requirements, streamlining the process of manual access authorization and removal. Its user-friendly interface facilitates the creation of custom workflows aligned with user roles, departments, and seniority levels, ensuring a seamless and efficient approach to access management.

Onboarding workflow

Offboarding workflow
- Leveraging user profiles, departments, seniority levels, and contextual cues, the platform offers intelligent app recommendations and in-app suggestions. This simplifies the process of selecting applications for provisioning, aiding your team in effortlessly identifying the most fitting choices.

- Furthermore, Zluri enhances user productivity by delivering in-app suggestions that provide timely recommendations for optimizing task execution. These suggestions extend to IT teams, guiding them to efficiently add users to multiple Slack profiles and craft welcome messages.
- Zluri's reusable automation playbooks save and store onboarding and offboarding workflows as preconfigured templates, eliminating the requirement for repetitive recreations. This streamlined approach significantly boosts operational efficiency, resulting in a smoother and more effective process.

Onboarding Playbooks

Offboarding Playbooks
Effortless Ad-hoc Access Request Management: Ticketless Solution
Zluri's Employee App Store (EAS) revolutionizes access request management by streamlining ad-hoc requests when roles change. Through EAS, IT teams exert complete authority in assigning access according to job roles and permissions, ensuring a tailored and personalized experience.

Zluri's tailored SaaS workflows eliminate the complexities of managing numerous requisitions, approvals, and revocations. The platform employs a transparent approval hierarchy comprising three tiers: app owners, reporting managers, and IT administrators. This structured system allows higher-level authorities to supersede decisions made at lower levels, ensuring efficient decision-making and thwarting unauthorized access.

Moreover, the inclusion of the \"changelog\" feature enables employees to monitor request statuses and receive updates, fostering transparency and accountability within the access management process.
Stay Compliant with robust access control & thorough Access Certifications.
As SaaS decentralization makes it easier to provide employees with privileged access, it also introduces novel challenges in managing and overseeing these privileges. Zluri's IGA solution steps in to simplify user access reviews and permission management, providing a centralized platform for your IT teams and auditors to conduct comprehensive reviews and generate access reports.

The platform's automated access certification evaluates user access privileges using predefined rules, simplifying the review process and minimizing errors in contrast to manual approaches. Swift auto-remediation features promptly tackle access violations, heightening security measures and guaranteeing compliance adherence.

Zluri enables IT teams to efficiently revoke access for terminated or obsolete privileges, effectively reducing the risk of unauthorized data breaches. Furthermore, its extensive range of reports provides valuable insights into access trends, vulnerabilities, and compliance status, thereby supporting compliance efforts and well-informed access management choices.
Zluri distinguishes itself through ongoing access reviews, offering regular certifications to consistently validate permissions. The scheduled certifications guarantee timely assessments, addressing crucial access concerns and reinforcing overall security measures.

Leveraging its AI-driven compliance solution, Zluri enhances data security while simplifying compliance endeavors. Real-time access reviews meticulously analyze patterns and user activities, swiftly identifying anomalies to proactively counter threats. Persistent monitoring delivers immediate visibility into access privileges, enabling swift responses to potential concerns. Zluri's AI-driven compliance features provide astute insights, aligning access controls with industry regulations to curtail compliance risks.
Furthermore, Zluri provides industry-standard certificate templates that streamline the certification process, furnishing comprehensive, precise, and guideline-adherent documents.
Embrace the next era of access governance with Zluri today and open the doors to unmatched data protection. Schedule a demo today to see it in action!









.svg)



.svg)
.svg)
.svg)
.svg)

.svg)

.svg)

.svg)
















.webp)







.webp)
.webp)





.webp)