Saviynt offers an identity governance and administration (IGA) platform that empowers IT teams to efficiently manage user identities, access controls, and compliance requirements. However, as an IT manager, exploring alternative IGA platforms is crucial for you to make informed decisions aligning with the IT team's needs.
Saviynt's IGA offers comprehensive features to streamline your organization's identity and access management processes. The platform allows your IT teams to govern user identities efficiently, assign appropriate access privileges, and enforce organizational compliance policies.
Moreover, Saviynt's IGA platform is known for its robust automation capabilities, reducing manual efforts and enhancing operational efficiency. Additionally, it provides detailed audit logs and reporting functionalities to facilitate compliance audits and maintain a secure environment.
However, a few drawbacks fail to make this platform to be an ideal choice for your organization.
Drawbacks of Saviynt IGA
Below listed are a few drawbacks.
- The platform has challenges with certain workflows, as they just work initially and break down, creating difficulties for your IT team in efficiently creating workflows to streamline their regular tasks like provisioning and deprovisioning and consuming valuable time
- The tool falls short in reissuing new entitlement and just removes the existing one, leaving the user without the necessary entitlement that is required to access the applications based on their new roles, ultimately hampering productivity
- The tool’s reporting and analytics capabilities might not meet your expectations, which could hinder your ability to effectively monitor access and identify potential gaps. This could pose challenges in streamlining processes and ensuring compliance within your organization
Customer rating
- G2: 3.5/5
- Capterra: 4.5/5
This post will help you deep dive into the alternatives of Saviynt’s IGA solution and make an ideal choice for your organization.
9 Saviynt Alternatives
Let’s explore the various alternatives to Saviynt’s IGA solution.
1. Zluri

Zluri offers an identity governance and administration (IGA) platform for organizations looking to regain control over their SaaS applications. This powerful platform offers a unified approach to access management, streamlining the complex web of access permissions and ensuring top-notch security.
With Zluri's IGA platform, your IT teams can monitor and manage user access effortlessly. They can grant appropriate permissions while blocking unauthorized access and safeguarding sensitive information from potential threats.
Let's explore how Zluri meets your identity governance and administration needs, from managing user access and handling access requests to ensuring access certifications.
Gain Access Insights with Zluri’s Discovery Engine
Zluri uses 9 discovery methods to gain complete visibility into your organization's SaaS landscape. These methods include browser agents, IDPs & SSO, direct integrations, desktop agents, active directories, HRMS platforms, MDM platforms, finance systems, and CASB platforms. This empowers your team to identify and manage SaaS applications effectively.

But that's not all - Zluri goes above and beyond with its integration capabilities, integrating with over 300 SaaS applications. You'll receive real-time data, valuable insights, and AI-powered alerts to stay informed.
Through API-based integrations, Zluri ensures a thorough data discovery process across all your SaaS applications, leaving no stone unturned. With 100% visibility, you can trust Zluri to provide a complete picture of your SaaS environment.
Notably, Zluri boasts the most extensive library with over 240,000 apps and excels in delivering granular-level access data. Dive into the details and comprehensively understand user permissions and access levels within your SaaS ecosystem. Rest assured; no important aspect will go unnoticed with Zluri by your side.
Streamline your access management with Zluri’s robust automation engine
Zluri's automation engine is like a self-driving system for your organization. It takes care of access workflows effortlessly, ensures smooth and efficient automation with thorough reviews, and follows a clear set of rules and policies.
Now, let’s explore Zluri’s automation capabilities.
Lifecycle Management
Zluri simplifies the process of granting and revoking user access, ensuring efficient access management in your organization. With Zluri, your team can customize permissions based on roles, departments, and seniority levels, ensuring that each employee has appropriate access to the tools they need, approved at the right level, for their success.
- Making sure users have the right access to tools through automation
To give secure access to the new employees using Zluri's user-friendly interface, follow these simple steps:
Step 1: Go to the workflow module within Zluri's platform. From the drop-down menu, select the onboarding option. Click on \"New Workflow\" to proceed to the next step.

Step 2: Now, your team can choose the user(s) that are required to grant access to the right tools. Your team can use the search bar to locate a specific employee or browse through the list quickly. Once they select the employee(s), click \"Continue\" to move forward.

Step 3: Zluri provides contextual-based app recommendations based on factors such as the user's role, department, and even seniority level. Select the apps from the recommended list.

Step 4: Zluri assists your team by providing in-app suggestions. These suggestions help them automate additional tasks, such as adding users to relevant channels or sending them welcome messages in apps like Slack.

Step 5: Adding actions is easy too. Just click on \"Edit Action,\" enter the required information, and save the task. Your team can even schedule actions to execute the workflow on the onboarding day.
If you want to add more actions, click on \"Add an action,\" choose from the available options, provide the necessary details, and save the task.

Step 6: Further, with Zluri, your team can save workflows as \"playbooks'' for future use or click on “run” to run the workflow. This eliminates the security risks when onboarding employees with similar designations, user roles, permission levels, etc.
Note: These onboarding playbooks help you to ensure the right access to the right users at the right time, securing your sensitive information and increasing the overall productivity.

- Seamless workflows to remove user access and ensure security
Zluri provides a convenient solution for automating user deprovisioning. This feature ensures that the user’s accesses are revoked when they leave your organization, maintaining data security and compliance. Here's how you can use this feature:
Step 1: Access Zluri's main interface and navigate to the workflow module. Select \" offboarding \" from the drop-down and click \"New Workflow.\"
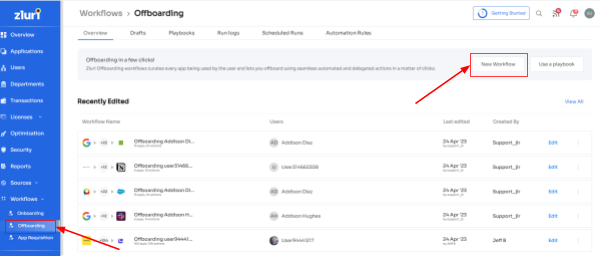
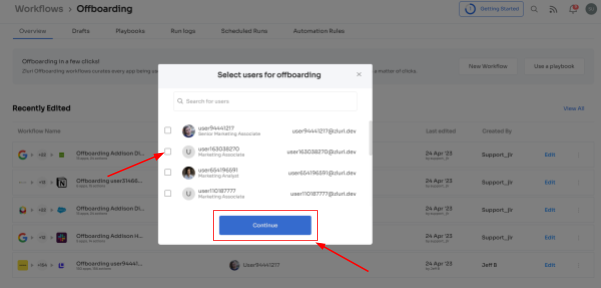
Step 2: Your team will find a dedicated offboarding user box within the platform. Here, your team can locate the employee(s) you want to offboard. They can either scroll through the list or use the search bar to find them. After selecting the users to offboard, click on \"Continue\" to proceed.
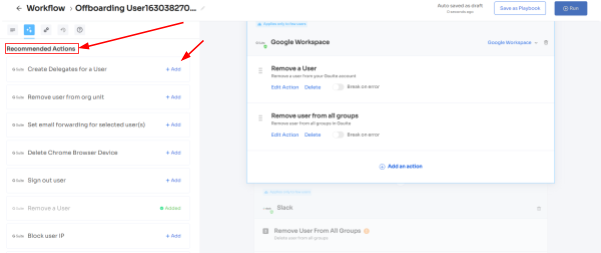
Step 3: Next, your team can review all the applications that the offboarded employee had access to. Also, they can click on each application to see the suggested actions under \"recommended actions.\"
Choose and execute the necessary actions based on the recommendations for the applications.
Step 4: Save the workflow as a \"playbook\" for future use. This allows your team to use the same playbook to deprovision users in the future.
Note: These offboarding playbooks help ensure that ex-employees cannot access your organization's data, leading to improved security and compliance with necessary regulations.

Access Requests Management
When new employees join or leave a company, managing their access to different systems is relatively straightforward. The real challenge arises during the mid-lifecycle transition when employees require access to new applications.
In the past, this process involved submitting access requests and waiting for approvals, which could take a long time. But now, Zluri has come up with a more efficient solution. Zluri has introduced a streamlined method that eliminates the need for tickets, reducing unnecessary delays and saving valuable time for your employees.
Zluri offers an Employee App Store (EAS), a self-serve platform, that contains a collection of pre-approved and verified SaaS applications, all curated by IT admins. This empowers employees by giving them the flexibility to choose from the EAS and quickly gain access to the applications they need.

Further, the EAS empowers your IT team to have control over what access your employees have to the required tools. For example, your team or approver can approve the access request only if the permission level requested by the employees is suitable to their job role. This helps you govern the access and prevent the access to sensitive information in your organization.

Zluri provides a clear approval system with three levels: app owners, reporting managers, and IT admins. When it comes to decision-making, higher authorities have the power to override the decisions made by admins or managers at lower levels.
Moreover, if an app request is rejected, decision-makers can include comments to explain why a request was rejected, to maintain transparency in the access request process.
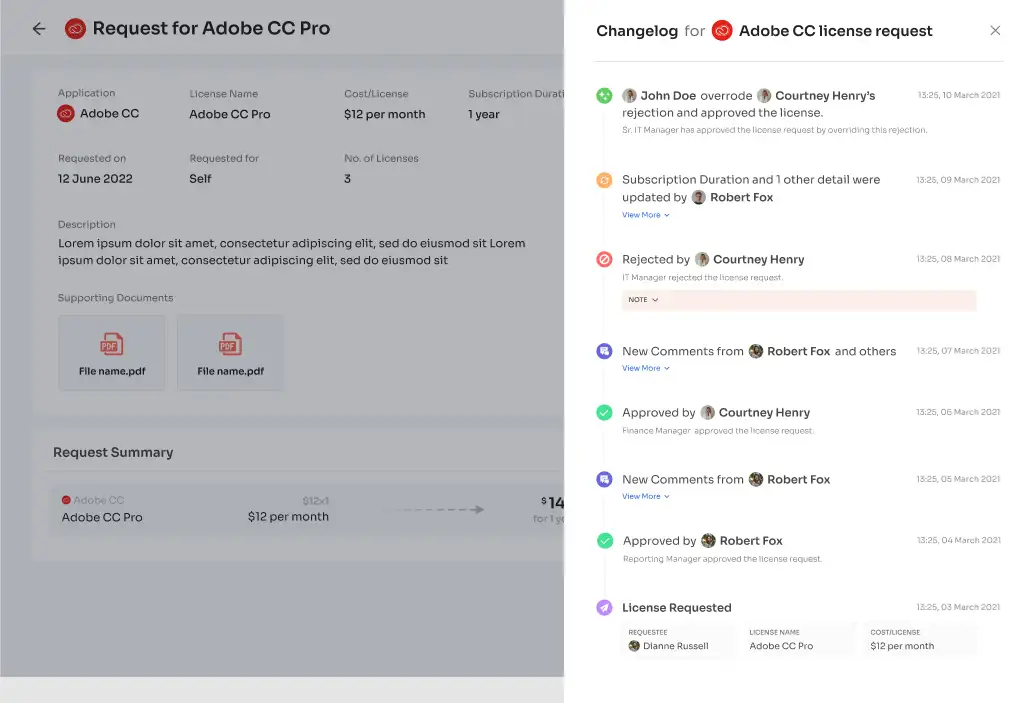
Approvers also have the ability to modify specific requests. For instance, if an employee requested a \"Microsoft Enterprise\" license, the approvers can change it to \"Microsoft Business\" if needed during the approval process.
The users can view the updates in the “changelog” on all the requests made. For example, approval or rejection of requests, changes in the duration or tier of licenses, and the comments added by any admin.
Access Certifications
Due to work decentralization, managing employee access has become both easier and more challenging. It's easier for your employees to get the necessary access they need, but harder for you to control and keep track of all those privileges.
To ensure a secure and compliant environment, it's crucial to grant the right level of permissions to the right users. That's where Zluri's IGA solution comes in to simplify the users’ access review process.
Zluri provides a centralized platform for your IT, security, GRC (Governance, Risk, and Compliance) teams, and auditors to review and report on users' access. With Zluri, you can easily set review parameters, choose reviewers, and schedule access review campaigns.

Through intelligent automation, Zluri assesses user access rights based on predefined rules, which saves time and reduces errors compared to manual spreadsheet reviews.
Moreover, Zluri doesn't just stop at reviews. It also offers auto-remediation capabilities. If any access violations are detected, Zluri takes immediate corrective actions, enhancing your organization's security and ensuring compliance.
One of the key benefits of Zluri is its ability to promptly revoke access for terminated employees or those with outdated privileges. By doing so, Zluri helps mitigate the risk of unauthorized data breaches and keeps sensitive information secure.
Zluri goes further by generating comprehensive reports that offer valuable insights into access patterns, vulnerabilities, and compliance status. These reports are auto-generated, making it easy to demonstrate compliance to auditors and enabling you to make informed decisions about access management.

Let's dive deeper into how it works.
Continuous Access Reviews
Continuous access reviews are essential for ensuring that only the right people have the necessary permissions, reducing the risk of unauthorized access and data breaches. Zluri offers a unique approach to access reviews that sets it apart from other IGA tools.
With Zluri's access review solution, you can maintain control over access privileges through two key features: recurring certifications and scheduled certifications.
Recurring certifications mean that access permissions are regularly and consistently reviewed and validated. This helps quickly identify and address any potential security weaknesses, keeping your system secure.

Scheduled certifications allow you to plan and conduct access reviews at specific intervals. Following a scheduled approach ensures that access permissions are consistently and timely evaluated, minimizing the chances of missing critical access issues.
To further streamline the certification process, Zluri provides industry-standard certificate templates. These templates offer a standardized approach, making it easier for you and your team to conduct certifications efficiently. Using these templates ensures that the certification process is comprehensive, accurate, and aligned with recognized guidelines.
Real-time Access Reviews
Zluri’s access review solution is powered by artificial intelligence (AI) to boost data security and simplify compliance procedures.

By leveraging AI, Zluri performs real-time access reviews by analyzing access patterns, user behavior, and system logs. This allows it to spot unusual or potentially risky activities, giving you early alerts to proactively address security threats and safeguard sensitive data.
Zluri's access reviews also support continuous monitoring, giving you a live view of access privileges. This means you can keep track of any changes or possible issues related to access rights in real-time. With this visibility, you can quickly resolve access-related concerns, reducing the chances of unauthorized access or misuse.

Moreover, Zluri's AI compliance capabilities offer intelligent insights and recommendations. It helps align your access controls with industry regulations and standards, reducing the risk of compliance violations. With the help of AI, Zluri streamlines the compliance process, making it simpler for your organization to meet regulatory requirements.
Here are the steps to automate the access review process.
- Step 1: Open Zluri's main interface, go to the \"Access Certification\" module.
- Step 2: Now to create an access certification, click on \"Create a New Certification.\" Now, add a suitable name for the certification and assign a responsive owner.
- Step 3: Under the set up certification, choose how you want to review users' access: either by Application, or Users.
For example, if you select to review access by Application, add the application to audit users' access.
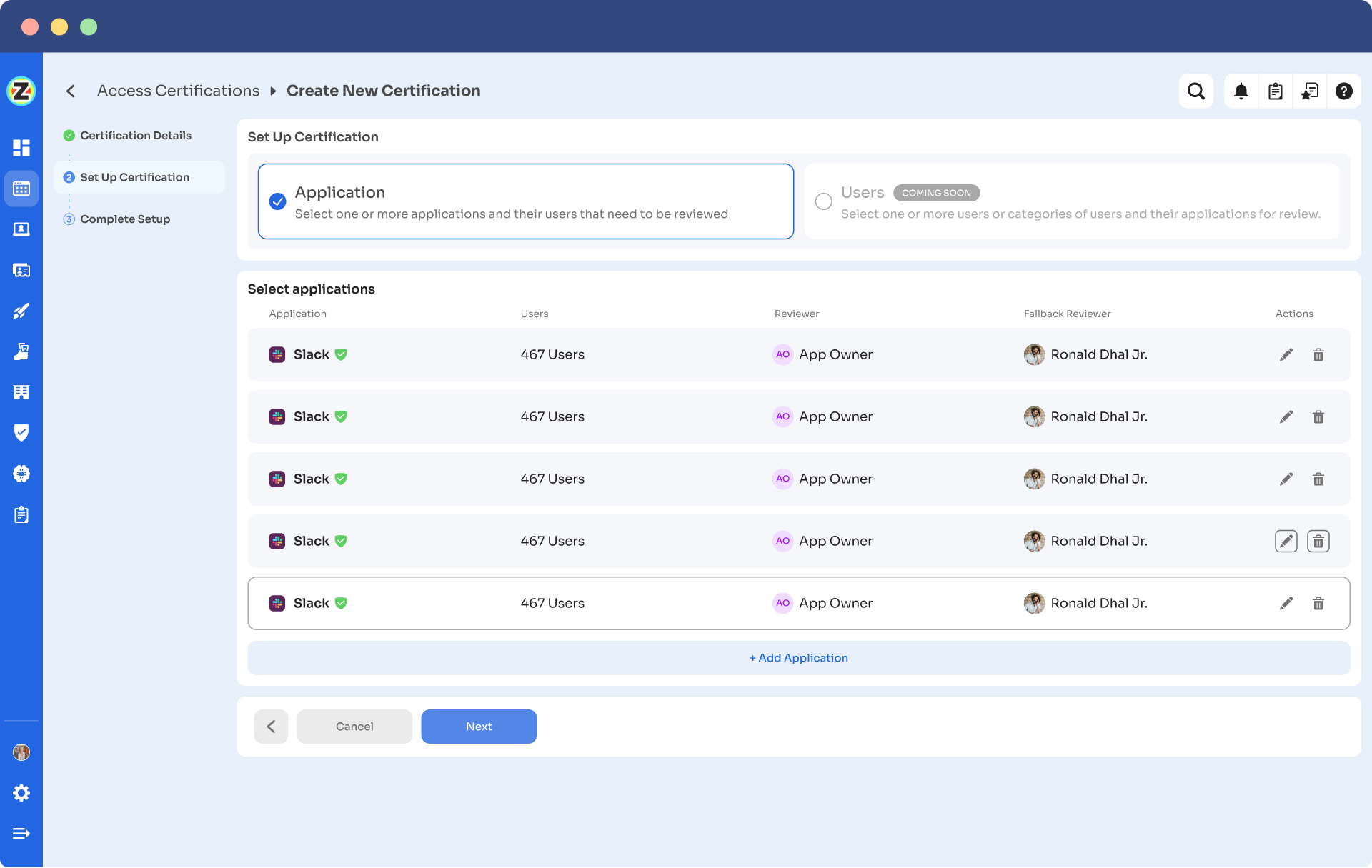
- Step 4: Then choose a primary reviewer and a fallback reviewer from the drop-down menu. Once you are done selecting the reviewers, you can click on “Next”.
Note: Generally the primary reviewers are app owners. Also, choose the fallback reviewer carefully whom you think is responsible.
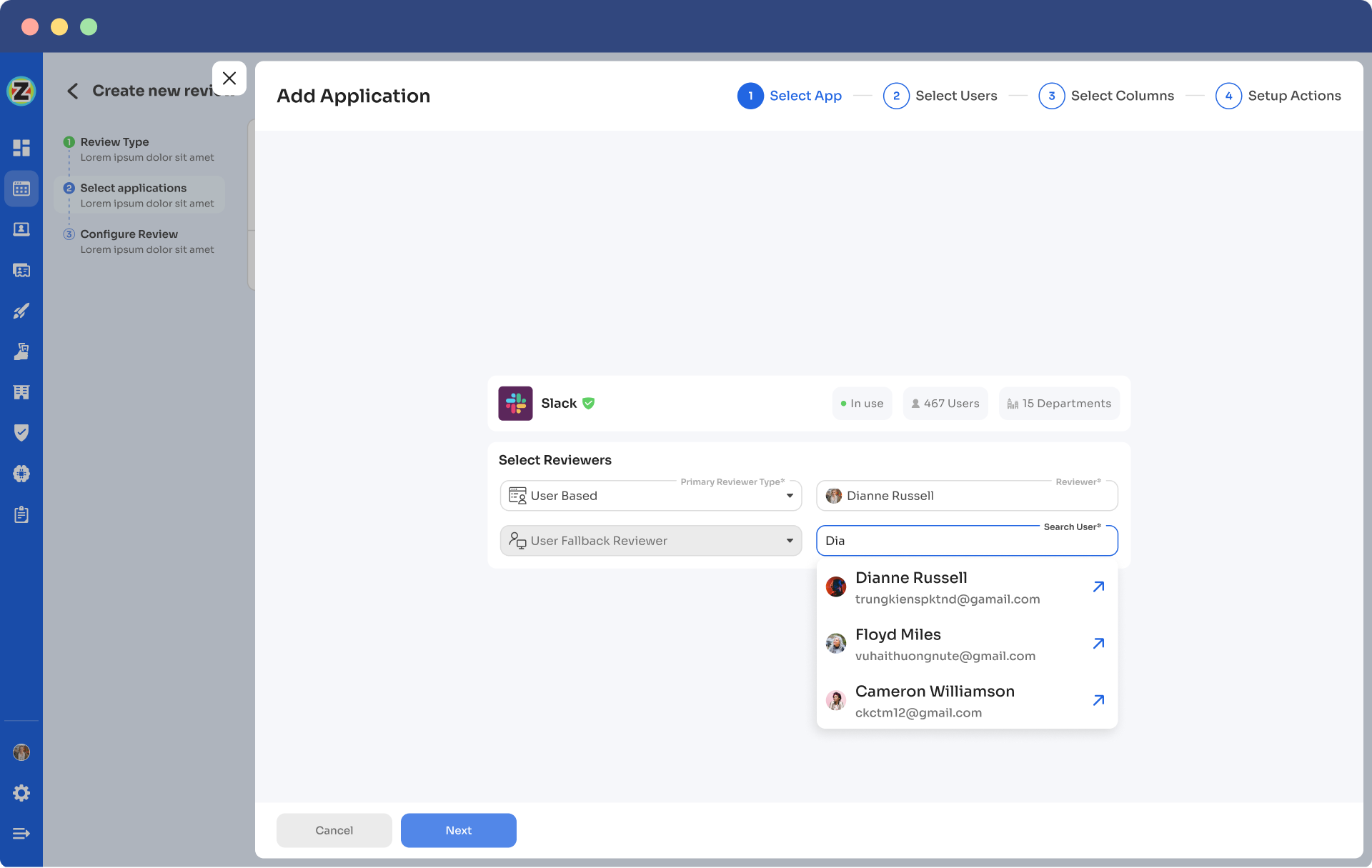
- Step 5: Choose the specific users to include in the certification process. You can also filter the data points such as user department, job title, usage, and more, as per your certification requirements. Then, click on \"Next.\"
Note: Select those relevant data points only that you wish your reviewers to see while reviewing the access. By filtering the criteria appropriately, you enable your reviewers to make swift and well-informed decisions, streamlining the review process and ensuring efficiency.
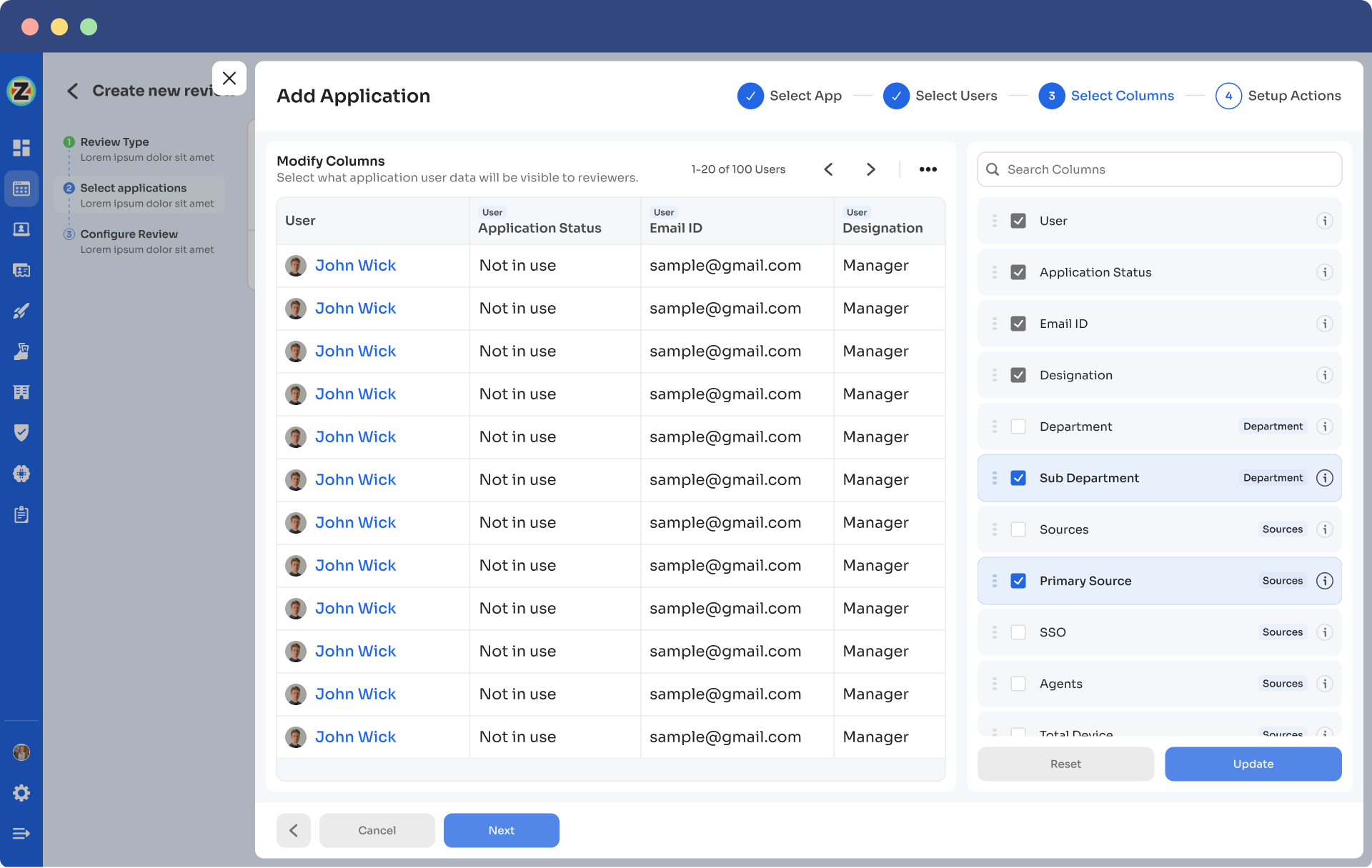
- Step 6: Now configure actions based on your needs and choose from the drop-down options.
For example, for rejection action you can select the respective deprovisioning playbook to revoke the unnecessary access of the users.
Once you set-up the action, you can click on “add applications”.
Note: You can add multiple applications for the same certification.

- Step 7: Set the start and end dates for the certification process, depending on within what time span you want the review to be completed.
Note: You can also click on \"Save Template\" to save it for future use.
- Step 8: Lastly you can keep track of the automated access review process by clicking on the ‘Review Status’ and view whether the review is still pending, modified, declined, or approved.
Finally, you can easily track the entire review process on a chart. Once the review is complete and the assigned reviewer approves it, you can simply click 'conclude' to instantly send the reports to their email.
For further information on how Zluri meets your identity governance needs, Book a demo today!
Pros
- Zluri's SSO capabilities allow employees to use a single set of credentials to log in, streamlining the login process and increasing security.
- Zluri sends alert notifications in the event of unauthorized access, helping your ITteam to ensure that sensitive data is kept secure.
- With Zluri, your team can customize actions to restrict or remove access to critical apps and users, ensuring your organization's data remains secure.
- Zluri allows customization to fit the specific needs of your IT team.
Customer rating
- G2: 4.8/5
- Capterra: 4.9/5
2. Okta’s Identity Governance

Okta's Identity Governance provides a platform to manage user access across multiple systems and applications. By centralizing access controls, your team can streamline the process of granting or revoking access to resources, reducing administrative overhead, increasing productivity, and minimizing the risk of unauthorized access.
Okta's Identity Governance provides better security by offering robust auditing and reporting capabilities. With a centralized view of access permissions and policy enforcement, your team can easily monitor and track user activities, generate detailed reports, and comply during audits.
Pros
- The tool uses a six-digit passcode for user authentication, making it easy for your IT admin to grant authorized access and prevent security risks such as unauthorized entry
- The platform offers a centralized location for streamlined app management and access, providing complete control in a simple, efficient manner
Cons
- The solution can make it difficult for your team to connect with your existing systems, leading to inefficiencies when it comes to managing user access across multiple necessary systems based on their role
- The tool delays in sending push notifications with users' requests, requiring your team to manually retrieve the passcodes for granting access to the requested applications
Customer rating
- G2: 4.5/5
- Capterra: 4.7/5
3. Omada Identity

Omada Identity offers a centralized identity governance platform that allows your team to manage user identities and access controls from a single, unified console. This centralized approach gives you a comprehensive view of user access, enabling your team to enforce consistent policies and quickly respond to access requests.
With Omada Identity, you gain granular visibility and control over user privileges, improving security and minimizing the risk of unauthorized access.
Moreover, the platform simplifies compliance management by providing a range of features to support audit and regulatory requirements. With built-in reporting capabilities, you can easily generate detailed reports on user access and permissions, demonstrating compliance during audits.
Pros
- The tool offers seamless integration with your entire IT infrastructure, empowering your IT team to effectively manage access and enhance security measures
- For your IT admin seeking absolute control over account management, this tool is a perfect fit. It simplifies the management of accounts and enables easy access for your organization's identities, ensuring a seamless user experience
Cons
- If you're seeking a tool that can be quickly implemented, this might not be the ideal choice. The initial setup of this tool takes time, which can cause delays in efficiently managing user access
Customer rating
- G2: 3.8/5
4. Oracle Identity Governance

Oracle Identity Governance automates user provisioning and deprovisioning, simplifying the process of granting and revoking access. The platform's automated workflows and policy enforcement ensure consistent adherence to regulatory guidelines, mitigating the risk of non-compliance and associated penalties.
The solution leverages advanced analytics and intelligent algorithms to detect and mitigate security risks. The platform identifies anomalies and potential threats by analyzing user behavior patterns and access requests in real-time.
This proactive approach allows your team to respond swiftly to security incidents, reducing the likelihood of data breaches and unauthorized access. With Oracle's identity governance, you can strengthen your organization's overall security posture and protect critical assets effectively.
Pros
- If you're in search of a scalable IGA tool to meet the security requirements of your expanding user provisioning process, look no further. This solution is perfectly suited for your needs, as it can effortlessly handle multiple workflows within the provisioning process
Cons
- The tool's user interface is overly complicated with multiple applications to manage, creating significant challenges for your team in streamlining access management
- The tool gives one password to access all the apps, hampering your ability to effectively maintain the security of your organization's data
Customer rating
- G2: 3.7/5
- Capterra: 4.4/5
5. One Identity Manager

One Identity Manager offers a range of features to help your team efficiently manage user identities. This allows your team to easily onboard new employees, provision access rights based on their roles, and automate user lifecycle processes, such as user provisioning, access requests, and deprovisioning.
Additionally, the solution offers granular access controls, allowing your IT admin to define and enforce least privilege principles, ensuring that users only have access to the resources they truly need.
Also, the solution provides detailed audit trails and reporting capabilities, allowing your team to monitor and track user activity, access requests, and changes to permissions. This visibility helps your team demonstrate compliance with industry regulations and internal policies, while also facilitating quicker and more accurate audits.
Pros
- The tool promises flexibility for your IT team to create and implement role management policies, simplifying access management based on user roles and ensuring regulatory compliance
- If you are seeking for an easy implementation, this tool provides you with quick implementation, making it smooth to use the tool at its full potential
Cons
- While the tool offers a web interface for access management, it unfortunately falls short in providing all the necessary functionalities. As a result, users are restricted in their ability to effectively manage and control access through the web interface
- Its customization options are limited, leading to potential inefficiencies in access management and data security maintenance for your organization
Customer rating
- G2: 3/5
- Capterra: 5/5
6. RSA Identity Governance and Lifecycle

With RSA Identity Governance and Lifecycle, your team gains a centralized platform to manage user identities, roles, and access privileges across your organization's IT infrastructure. It provides a unified view of user access, enabling you to create and enforce consistent access policies, regardless of the systems or applications involved.
The tool helps your team identify and address access risks and compliance violations by analyzing user entitlements and access patterns. This enables your team to detect and mitigate potential security threats, such as excessive access rights.
The solution also provides auditing and reporting capabilities, enabling you to generate detailed compliance reports, track access requests and approvals, and demonstrate adherence to regulatory requirements during audits.
Pros
- With its ability to adapt to your organization's access requirements, the tool provides unparalleled flexibility, positioning it as the optimal solution for managing and maintaining full control over system access.
Cons
- The tool lacks in providing sufficient training materials, resulting in your team to give in extra effort and invest time in learning the tool efficiently. This leads to delay in managing users’ access to required tools efficiently
Customer rating
- G2: 4.7/5
7. Symantec IGA

Symantec IGA is a comprehensive solution that helps your IT team to streamline and enhance the management of user identities within the organization. With Symantec IGA, you can efficiently govern and administer user access rights across various systems, applications, and data repositories.
One of the key features of Symantec IGA is its powerful identity governance capabilities. Your IT admin can establish and enforce policies to control user access throughout the organization. This enables them to prevent unauthorized access, reduce the risk of data breaches, and maintain compliance with industry regulations.
Symantec IGA also provides advanced administration features to simplify user lifecycle management. Furthermore, it offers a self-service portal, empowering end-users to manage their own access requests and password resets. The self-service portal includes built-in approvals and workflows, ensuring that access requests go through the appropriate channels for review and authorization.
Pros
- With its powerful auditing capabilities, this tool becomes an invaluable asset in your quest for compliance and ensures that your organization operates within the boundaries of the required regulations
- The tool empowers your team with enhanced access management capabilities, enabling precise control over user permissions based on roles, departments, and more.
Cons
- The tool faces challenges when it comes to customizing the different app approvals needed for users to access them, limiting your team's ability to create a tailored approval process and ultimately hindering productivity
- The solution makes it complicated for your team to integrate with your existing system, resulting in inefficiencies to manage users’ access to the different systems necessary for the user's role
Customer rating
- G2: 3.4/5
- Capterra: 4/5
8. ForgeRock Identity Governance

ForgeRock Identity Governance helps you streamline and enhance your organization's identity and access management processes, ensuring security, compliance, and efficiency. With ForgeRock Identity Governance, your team can take control of user access rights, minimize risks, and maintain a strong governance framework.
It enables your team to efficiently handle user onboarding, changes, and offboarding, ensuring that the right individuals have access to the right resources at the right time.
In addition, the tool also provides comprehensive compliance reporting and auditing functionalities. With this, your IT team can generate detailed reports on user access, permissions, and activities, which are crucial for regulatory compliance and audits. These reports help you demonstrate compliance with industry standards and regulations and assist you in addressing any potential compliance gaps.
Pros
- The tool offers extensive customization options for authentication and authorization, empowering your IT team to effectively manage access and proactively mitigate any unauthorized entry
- The tool provides an intuitive and user-friendly interface, enabling your team to effortlessly navigate and utilize its powerful features
Cons
- The tool has limitations in integrating with systems like Unix-based systems, restricting your team from managing access to these systems, and can bring security risks to your organization
Customer rating
- G2: 4.4/5
9. IBM Security Verify

IBM Security Verify offers a comprehensive suite of identity and access management capabilities, empowering you to enhance security, enforce compliance, and streamline your organization's operations. With IBM Security Verify, your team can effectively manage user access, mitigate risks, and ensure a strong governance framework.
It allows you to define and enforce policies for managing user identities, access rights, and entitlements. With centralized identity management, your team can easily monitor and control user access across your organization, ensuring compliance with regulatory requirements and industry standards.
IBM Security Verify also simplifies user provisioning and deprovisioning processes. It enables your team to automate user onboarding, updates, and offboarding, reducing administrative burdens and eliminating the risk of manual errors.
In addition, the solution provides detailed logs and reports on user activities, access requests, and system events, helping you easily meet regulatory compliance requirements and pass audits. This provides you with valuable insights into user behavior and potential security threats, enabling proactive risk management.
Pros
- If you have a large-sized organization and are facing challenges in maintaining security when it comes to system access, then this solution is perfect for you. It simplifies access management, covering everything from passwords to configuring access to your systems, making it highly efficient
- The tool provides powerful security measures that helps your team effectively manage user access and assess the risk associated with visitors before granting them access to the system or applications
Cons
- By supporting simple and easy password policies, this tool opens the door to unauthorized access to your organization's sensitive data, posing significant security risks such as data breaches
- It has a steep learning curve, requiring you and your team to invest more time to learn and use the tool at its full potential
Customer rating
- G2: 4.3/5
- Capterra: 4.3/5









.svg)



.svg)
.svg)
.svg)
.svg)

.svg)

.svg)

.svg)
















.webp)







.webp)
.webp)





.webp)