Saviynt enables your IT teams to ensure your employees have seamless access to SaaS apps and data without compromising on security and compliance. Meanwhile, ForgeRock assists your IT team in enforcing access controls and separation of duties policies to protect the SaaS app data from unauthorized users.
However, both tools offer other distinct functionalities that you, as an IT Manager, can carefully evaluate before deciding which IGA platform to choose.
To determine the most suitable IGA platform, it's crucial to thoroughly analyze each tool's capabilities and how well they align with your IT team's requirements.
This was just a gist of how a tool's features can greatly influence your decision-making process. However, relying solely on one particular functionality is not enough while determining the ideal platform; you need to evaluate and consider the distinctive features of each tool thoroughly.
Let’s assume an organization requires an IGA platform that offers zero trust capabilities focusing more on adaptive access policies. So which IGA tool will be more suitable for this scenario, Saviynt or Forgerock?
In this situation, Saviynt will be a better choice as its zero trust features center around identity governance, continuous monitoring, and adaptive policies. It utilizes pre-built access roles to provide precise access that expires automatically, enhancing security and ensuring least privilege access.
Whereas, ForgeRock’s zero trust capabilities focus on secure access management and dynamic risk assessments, enabling your IT team to promptly discover and mitigate potential threats. Also, it allows your employees to authenticate/verify themselves seamlessly and can gain quick access to required applications.
So, let's move ahead and compare both tools based on different parameters to help you decide which IGA solution will best meet the requirements of your IT team.
Comparison Based On Different Parameters: Which IGA Tool Is A Perfect Fit?
Below, we have differentiated the tools' functionalities in detail that will assist you in selecting the ideal platform for streamlining identity governance and administration management.
1. Identity Governance And Administration
While both Saviynt and ForgeRock share the common objective of assisting IT teams in streamlining identity governance, they follow different approaches. So let's see how they make it all possible.
- Experience simplified Identity Governance with Saviynt
Saviynt ensures seamless access to SaaS apps and data while maintaining compliance. Saviynt simplifies the complexities of identity governance and administration (IGA) by leveraging automation and intuitive workflows.
Saviynt utilizes a single control panel for privileged access management across clouds, applications, and infrastructure so that your IT team can view risks in real-time and take immediate measures. Also, your IT team can establish a Zero Trust framework i,e., an approach that enables a strict security posture by granting access based on continuous verification and contextual awareness.
Furthermore, it offers unique key capabilities, such as role-appropriate access in which your team enforces access roles to reduce standing privilege and converged PAM+IGA, which allows you to make smarter decisions to mitigate governance-driven risk and privileged access data.
Additionally, it meets evolving regulations with ISO, SOC, and FedRAMP-authorized platforms.
- Govern Every Identity With ForgeRock
On the other hand, with ForgeRock, your IT team is designed to meet the needs of large enterprises. It enables processing millions of entitlements across thousands of applications in just minutes. This exceptional scale sets ForgeRock apart from other governance solutions that cannot match its level of performance.
Furthermore, ForgeRock Identity Cloud streamlines tasks such as application onboarding, access request reviews, and periodic certification, eliminating the need for lengthy deployments and reducing operational costs.
Additionally, it ensures a seamless onboarding experience by granting new joiner access to the applications they need on day one. Also, it provides your IT team with complete situational awareness of your workforce identity management, access management, and identity governance requirements.
It also leverages AI and machine learning to automate low-risk access request approvals and certifications, ensuring efficient and compliant processes.
Moreover, ForgeRock provides segregation-of-duties policy checks and proactive scanning to identify rogue accounts and inappropriate user access, preventing access violations.
2. Seamless Authentication Procedure
- Saviynt strengthens your Zero Trust strategy by providing comprehensive capabilities across various areas, such as offering privileged access management capabilities, and allowing your IT team to grant just-in-time access and permissions for a limited duration.
Further, Saviynt enables your IT team to ensure elevated privileges align with the least privilege policies. This includes privilege clipping using usage and outlier analysis. Additionally, it offers credentialless access, password obfuscation, and password rotation after use.
Besides that, it offers a data access governance feature that helps your IT team identify data access across diverse IT ecosystems and automates data access risk analysis. It provides access risk insights, continuous monitoring, and automated review triggers to protect your data effectively.
Also, Saviynt enables your team to build a comprehensive risk profile by sharing risk data across various security and GRC platforms, including SIEM, UEBA, and network and endpoint security tools. It offers pre-built controls aligned with HIPAA, PCI, NERC/CIP, COBIT, and CIS, simplifying compliance across platforms. - Meanwhile, ForgeRock enables your IT team to implement passwordless authentication across a wide range of SaaS apps, devices, and platforms, including mobile authenticators, smart cards, biometric devices, digital certificates, browsers, and applications. Also, your team can customize passwordless authentication journeys effortlessly using ForgeRock's no-code orchestration and tailor the process to meet your unique security and user experience requirements, ensuring a seamless and secure authentication flow.
But that's not all. By eliminating the vulnerabilities associated with passwords, ForgeRock's passwordless authentication strengthens your organization's security posture. Passwords are often easy targets for hackers, making your systems and sensitive information vulnerable. With ForgeRock, you can safeguard against unauthorized access and protect your valuable SaaS app data.
Additionally, to enhance security, ForgeRock prioritizes the user experience. By removing the friction of passwords from the login process, your IT team can create a seamless and hassle-free authentication experience for your users. This not only increases user satisfaction but also boosts productivity and engagement.
Also, you no longer need to invest in expensive backend password recovery and synchronization tools. With ForgeRock's passwordless authentication, you can significantly reduce help desk calls related to forgotten passwords and account lockouts.
3. Securely Granting Access Upon Onboarding
- Saviynt simplifies onboarding, allowing your IT team to quickly and seamlessly onboard new employees. Automating this process allows your employees to be onboarded with minimal effort, reducing your team's burdens and improving productivity.
It further helps your team ensure that the new employees can access required SaaS apps right from the start. Also, your team can minimize manual errors by automating the onboarding process.
With Saviynt, during onboarding, your employees are assigned access based on their roles and responsibilities, ensuring access rights align with job requirements and minimizing the risk of excessive privileges.
It seamlessly integrates with various applications, systems, and platforms, enabling smooth data exchange during onboarding. This integration capability simplifies the onboarding experience, minimizes disruptions to existing workflows, and enhances overall efficiency. - Whereas, ForgeRock's centralized identity management platform provides a comprehensive solution for managing user identities, roles, and entitlements. By serving as a single source of truth, it becomes the authoritative system that holds and governs user-related information across the organization. This centralized approach brings several benefits to streamline the provisioning process and support your IT team's efforts.
Furthermore, it lets your IT team completely view user identities, roles, and entitlements. They can manage and maintain this information in one place.
When it comes to provisioning new employees, ForgeRock offers capabilities for bulk provisioning. This means that your team can provision multiple user accounts simultaneously, significantly saving time and effort compared to manual provisioning. By leveraging automation, your team can efficiently assign the appropriate level of access permissions to the required applications and data to new employees. This ensures that employees have the necessary access to perform their job functions effectively from day one.
4. Mitigating Security Risks
- With Saviynt's advanced data protection solutions, your IT team can safeguard SaaS app data from anywhere, anytime. It ensures that your information remains secure and inaccessible to unauthorized users. How does it do all that? It allows your IT team to easily locate sensitive files, whether they are stored on-premises or in the cloud. With powerful discovery tools, your team can quickly identify and assess the risk associated with each file.
Once the data is discovered, it enables your team to lock it down to prevent unauthorized access; they can also determine who can access the data. Further, by eliminating access obtained through sharing links, your team can reduce the risk of data exposure.
Additionally, its automation capabilities allow your team to enforce least-privilege access. This means that only authorized individuals can access specific data, reducing the potential for data breaches.
Apart from that, your team can inspect and classify files containing sensitive information, such as personally identifiable information (PII), payment card industry (PCI) data, protected health information (PHI), and data governed by the General Data Protection Regulation (GDPR). This classification enables your team to prioritize protection efforts and allocate resources effectively.
Also, Saviynt's data protection solutions provide complete visibility, allowing your team to monitor user behavior and analyze access patterns. With this insight, they can proactively detect and respond to potential security risks, mitigating the impact of insider threats and unauthorized access attempts. - However, ForgeRock's Partner Authenticators, integrated with ForgeRock Intelligent Access, offer diverse, robust authentication options to address various use cases. Whether your IT team requires one-time passcodes, optical codes, or biometrics for user authentication, its authentication partners provide the capabilities your team needs, ensuring secure access for your users.
Furthermore, ForgeRock fraud and risk management partners are at the forefront of identifying and remediating risks, regardless of their origin. Also, its behavioral biometrics partners use cutting-edge technologies to create biometric profiles based on user behavior, combating bots, synthetic identities, and account takeovers. With the latest behavioral biometrics capabilities, its partners transparently identify individuals based on their unconscious actions, minimizing friction.
Additionally, they help identify non-human entities and emulators that may pose threats to your websites and applications. When integrated with ForgeRock Intelligent Access and our powerful authorization engine, behavioral biometrics partners add an invisible layer of security that protects your users while delivering exceptional experiences.
Also, ForgeRock identity proofing and enrichment partners are crucial in verifying user identities, ensuring they are genuine and associated with the claimed identity. These partners also identify potential risks associated with users.
After thoroughly comparing Saviynt and ForgeRock, you might have better understood which tool will be an ideal solution for your IT team's specific needs. However, it's crucial to note that other platforms are also available and worth exploring. One such exceptional platform is Zluri, which offers remarkable features that help your IT team streamline the identity governance process.
So, let's have a quick look at how Zluri is a better alternative to Saviynt and ForgeRock.
Zluri: A Better Identity Governance & Administration Alternative
Managing access permissions requires your IT team's constant attention to maintain a secure and compliant environment for your employees' identities and SaaS apps. However, managing these responsibilities can be challenging. If your IT team faces these difficulties, Zluri is the perfect modern IGA solution. It provides your team with exquisite features like access requests, access certification, lifecycle management, and other unique capabilities. That further helps your IT team govern access effectively and maintain a secure environment for SaaS app data.
So let’s see how each feature helps your IT team streamline identity governance and administration process.
1. Discover User Access Data Like Never Before With Zluri Data Discovery Engine
Zluri is better than competitors at discovering data since it is primarily a SaaS management platform. This background has given Zluri a distinct advantage, making it highly effective and proficient in identifying SaaS app data. One area where this expertise proves exceptionally valuable is in the area of user access data identification.
According to KuppingerCole's research, Zluri offers a single source of truth for all SaaS applications within an organization. With Zluri’s five discovery methods, i.e., SSO or IDP, finance systems, direct integrations, browser extensions (optional), and desktop agents (optional), your IT team gains the ability to explore and unveil essential details. They can seamlessly identify which users have access to particular SaaS apps, what all access rights are granted to them, identify the user status (active or inactive), and more.
These insights are a game-changer for user access management and SaaS app data security. Armed with such granular knowledge, your IT team finds it easier to conduct access reviews. Also, the process becomes streamlined, efficient, and less prone to oversight, ensuring access privileges align with user role and compliance requirements.

2. Automate The Manual Processes From Onboarding To Offboarding With Zluri’s Automation Engine
With Zluri’s user lifecycle management platform, your IT team can ensure the right level of access is granted to employees, modify access when there is a change in the employee's access requirement, and revoke access seamlessly. How does Zluri do that? Here’s a quick read-through.
- Enabling your IT team to streamline provisioning and deprovisioning through automation
Zluri enables your team to efficiently manage the user lifecycle by automating the provisioning and deprovisioning processes, ensuring your employees have secure access to SaaS applications throughout their employment.
Zluri simplifies the process of onboarding new employees by enabling your team to create customized onboarding workflows. These workflows allow your team to grant the necessary access to required SaaS apps so that the employees can start being productive from day one of joining. This eliminates the manual effort involved in provisioning access and reduces the chances of errors.
Similarly, when offboarding employees, your team can create offboarding workflows and revoke all access privileges associated with the departing employees. This helps in maintaining a secure environment and minimizing potential risks.
By automating the provisioning and deprovisioning processes, Zluri improves accuracy and consistency, reducing the likelihood of access-related errors and ensuring compliance with access management policies.
How can your IT team create an onboarding workflow?
Below are the steps that your team needs to follow to create an onboarding workflow:
- Step 1: From Zluri's main interface, click on the workflow module and select the onboarding option from the drop-down list. Proceed by clicking on New Workflow.
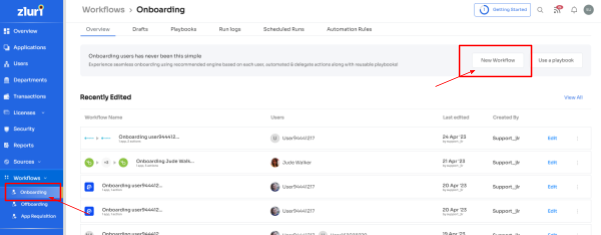
- Step 2: Select the user for the onboarding box will appear; from there, select the employee(s) whom you want to onboard. Also, you can search for a particular employee in the search bar. Once you are done selecting the employee, click on continue.
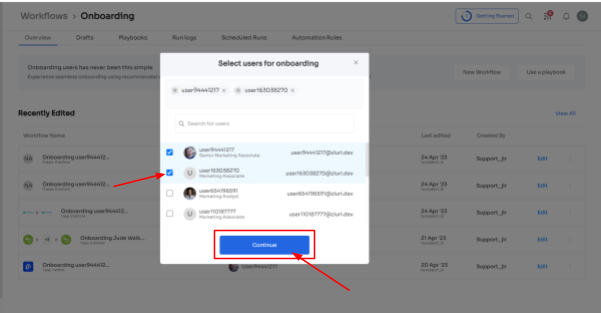
Note: You can even select multiple employees; this helps onboard multiple new employees in one go
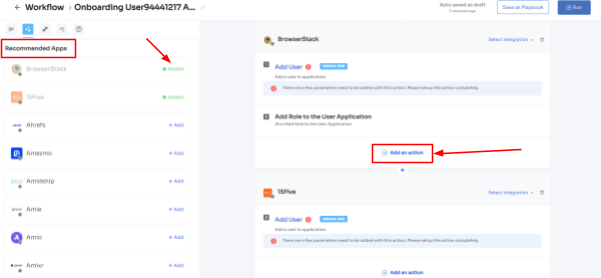
- Step 3: With its intelligent feature, Zluri would suggest some apps under recommended apps based on the employee's department, role, and seniority. Choose any of those, then execute the required action for the selected applications.
- Step 4: To execute certain actions, you need to Click on Edit Task and enter the required details. Your team can schedule the actions to execute the workflow on the day of onboarding. In order to save the actions, click on Save Task, and the actions will automatically be saved.
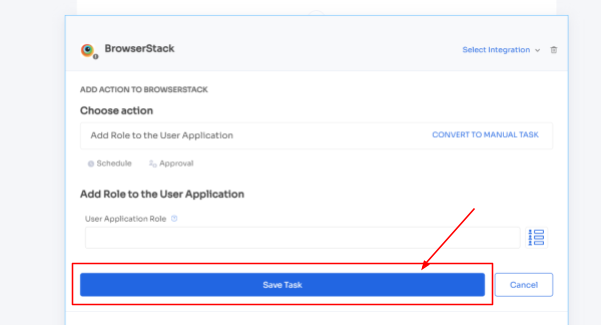
Also, your team can add your employees to channels or send an automated welcome greeting using Zluri's in-app suggestions. The actions can vary for different applications and are mentioned under recommended actions.
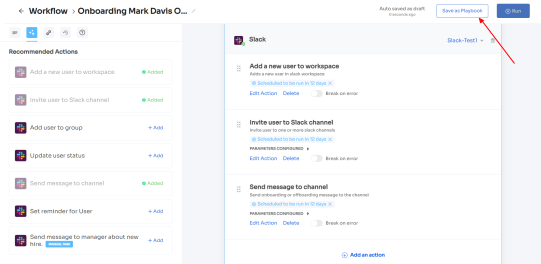
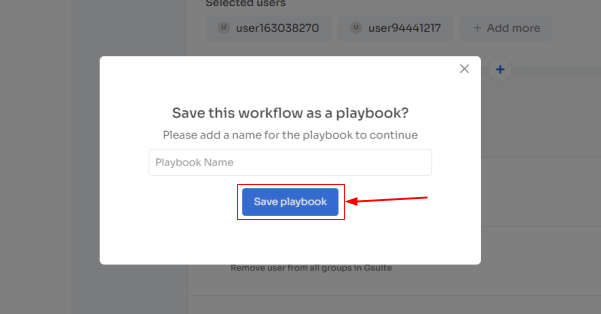
- Step 5: Finally, click on Save as Playbook to save the workflow. Then, you'll get a dialogue box with instructions to name the playbook. Add a name, proceed further by clicking on Save Playbook, and the onboarding workflow is ready.
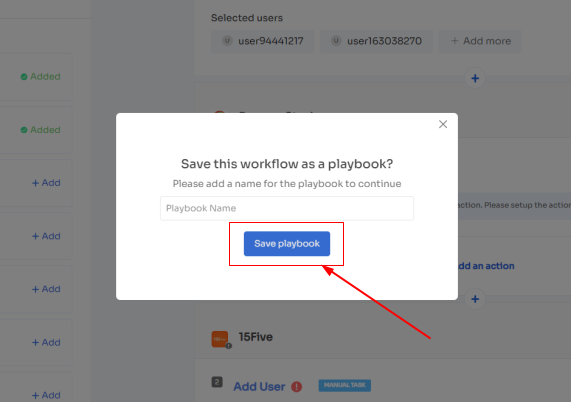
For added efficiency, Zluri offers automated playbooks (i.e., collections of recommended applications for automation) that can be customized for different roles, departments, and designations. This feature streamlines the onboarding of new employees, making it as easy as a few clicks to set up their access.
Note- Apart from that, your team can set automation actions, such as by triggering if and but conditions, they can grant Kissflow access to all the finance department employees.
How can your team create an offboarding workflow?
Here’re the steps your team needs to follow to create an offboarding workflow:
- Step 1: From Zluri's main interface, click on the workflow module and select the offboarding option from the drop-down list. Proceed by clicking on New Workflow.
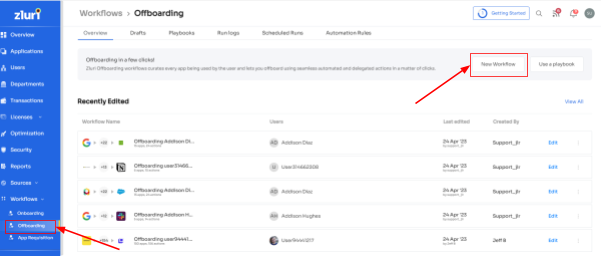
- Step 2: A popup labeled 'Select the user for offboarding' will appear. Select the employee(s) you want to offboard, or you can look for them in the 'search box. Click on continue after selecting the employee.
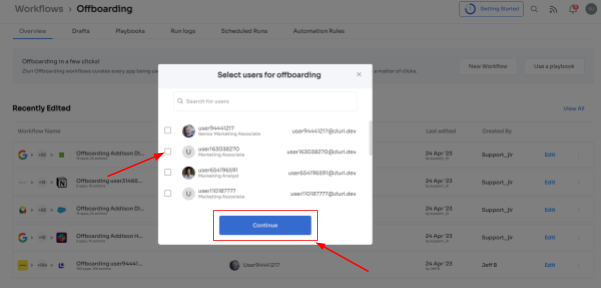
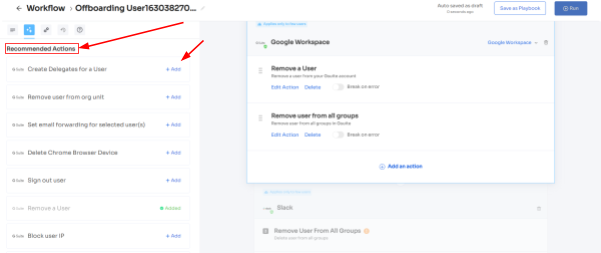
- Step 3: Your team will be able to view all the applications your employee can access. Now when you click on the app, Zluri will display some suggested actions under recommended actions. Select any of those or multiple actions, and then execute the required action for your chosen applications.
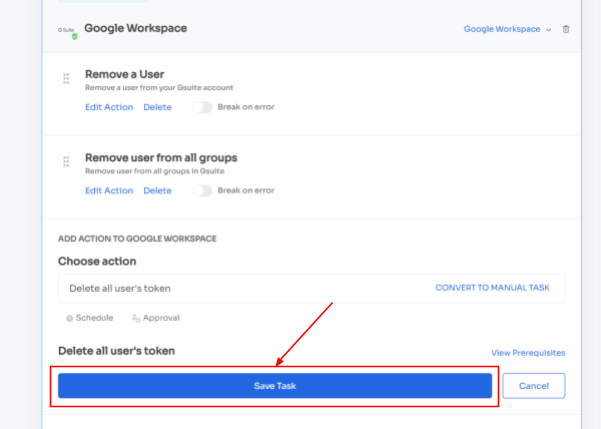
- Step 4: To add other actions, click Add an Action, fill in the required details, and proceed by clicking on Save Task; the actions will be saved.
- Step 5: Save the workflow by clicking Save as Playbook. A dialogue box will appear, instructing to name the playbook.
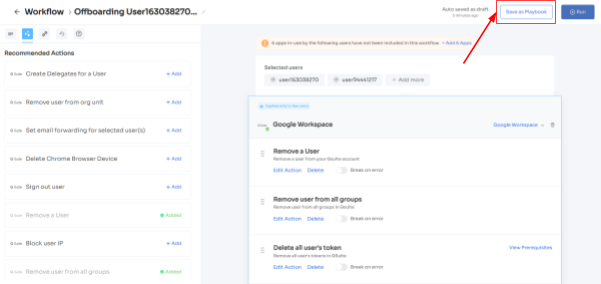
Add a name, click Save Playbook, and the offboarding workflow is ready.
- Ticketless Access Approval Process With Zluri’s EAS
Zluri takes a step further by simplifying the access request and approval process by offering your employee an Employee App Store (EAS), a self-serve model, a collection of SaaS applications approved and verified by IT admins. This empowers employees with the flexibility to choose from the EAS and gain quick access to their required applications.

But you might be wondering how your team can stay informed about changes in employee roles. Zluri offers a convenient solution to address this concern. Through seamless integration with your organization's HR system, Zluri automatically retrieves and displays updated employee data on a centralized dashboard.
By leveraging this integration, your IT team can easily access and verify employee details without manual effort. This streamlined process ensures access permissions align with current employee roles and responsibilities. Whether granting or removing access, your team can efficiently manage user privileges based on the most up-to-date information available.

This improves your IT team’s productivity and enhances your employee’s overall experience.
How can your employee raise access requests?
Your employees can raise requests by following the given below steps:
- Step 1: Your employees will receive an icon on the Zluri main interface's upper right corner; click on that, and a drop-down menu will appear; From there, click Switch to Employee View.
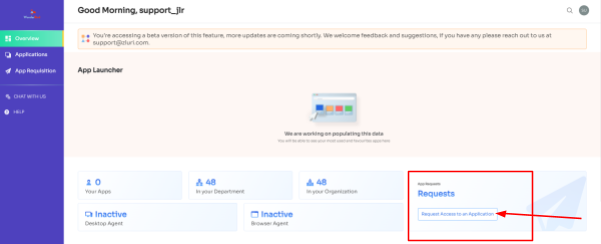
- Step 2: Overview dashboard will appear by default; now click on 'Request Access to an Application
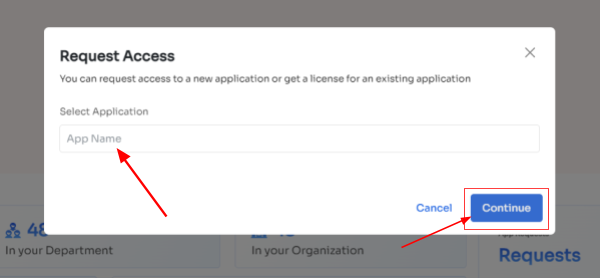
- Step 3: Your employees will see a dialogue box where they need to enter the application name they require access to. Then, click on Continue.
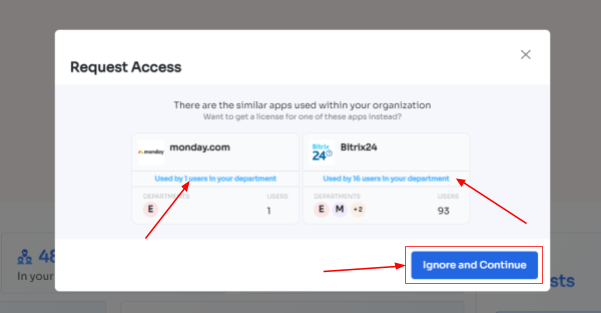
- Step 4: Some applications will not be used in the organization. However, your employees can still request that application. Click on continue, and another dialogue box will appear, showing similar applications that are being used in the organization.
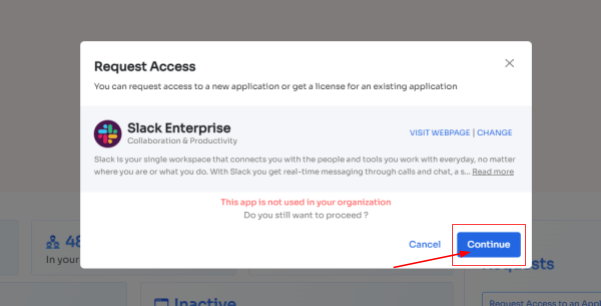
- If your employees want to opt for a similar application, they can simply click on the application or click on Ignore and Continue to proceed forward with your request.
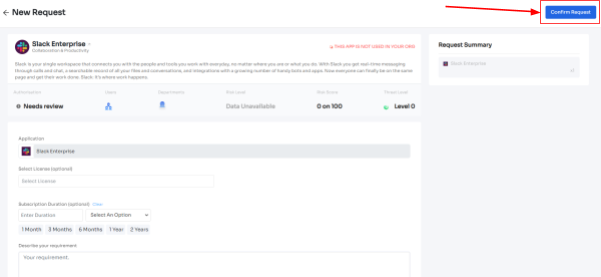
- Step 5: Further, they have to fill in the required details like selecting the license plan, subscription duration, and description of why they need the application and attach supporting documents. Once filled, click on Confirm request.
Note: Additionally, if the request has been modified in any way or if one of the approvers suggests any substitutes for the application, your employee can check it in the "Changelogs."

And that's it. The app access request has been submitted.
3. Strengthen security and compliance by simplifying access certification
Now comes the most critical aspect of access management: access reviewing. Ensuring that each user has the appropriate level of access permissions to apps and data is quite important to maintain data safety. Manual access reviewing can be time-consuming and inefficient, requiring IT teams to gather user lists, user statuses, access patterns, and all the apps to which users have access.
For instance, a user previously had admin-level access to a specific application, but their access permissions were revoked by your IT team two months ago, since they no longer required such high privileges. To ensure that user access remains appropriate, your team needs to review their permissions periodically and check if they still have the right level of access or have been granted admin-level permissions again. If they have been granted admin-level access again, what is the reason? Manually handling this process would be a significant waste of time.
To streamline access reviewing, Zluri comes to the rescue with automated solutions. Zluri automates the entire access review process, gathering all user access-related data in a centralized place. This simplifies the reviewing process for your team/reviewers, eliminating the hassle and making it more efficient.
This was just an overview. Zluri is not only restricted to these few access review capabilities, it has more to offer, which is exclusive and sets it apart from the competitors. So, let’s explore them one by one.
- Unified Access Review
Zluri’s unified access review feature provides your IT team with the ability to identify which users have access to all SaaS apps and data. Where does Zluri get all these insights from? Well, it has an access directory where all the user access-related data is stored in one central place.
Further, with the help of these insights, including whether the users are admins, regular users, which departments they belong to, and more, your IT team can examine users' access privileges and ensure their access aligns with the roles.
Additionally, Zluri’s activity & alerts capabilities come into play to keep things running smoothly. This feature provides real-time information about the last activities users performed and notifies IT teams about any new logins. With the help of these insights, reviewers can make quick and informed decisions during access reviews, ensuring the right people have the right access at all times.
- Automated Access Review
No more manual headaches with spreadsheets and JSONs! Zluri takes the hassle out of access reviews by automating the entire process. Just head to Zluri, create a certification, select the apps and users you want to review, and rest the reviewers will review and update you about the compilation via email.
So, by automating this process, you get 10 x better results than manual methods and save your IT team's efforts by 70%. Now let’s move ahead and see how it works.
- Once you gain access to contextual data through Zluri’s unified access feature, you can create access rules around these insights. For example, if someone is an admin on Salesforce, you can easily set up a review policy specifically tailored to that scenario.
- Next comes the schedule certification feature, where you can create certifications based on the gathered information. This allows you to take actions based on the insights you've gained. For instance, you can use data like last login, departments, user status (active or inactive), and more to make informed decisions during the review process, such as whether the user can continue with the existing access or need any modification.
With Zluri's context-rich information, your team can confidently take actions that align with your access management policies. It's a smarter, more efficient way to ensure the right access for the right users, all while keeping your data secure. Zluri's automated access reviews and access rules are the key to simplifying your access governance process.
- Secure access orchestration/auto-remediation
After completing the access review, necessary changes will take place as per the set actions during certification creation, so all these actions, like access modification or removal, are part of secure access orchestration. The seamless process ensures access is managed securely and efficiently, safeguarding your organization's data and resources.
For example, while creating a new certification in Zluri, your team will come across configuration action under which they need to create deprovisioning playbooks and modification playbooks. If the reviewers decline the access permissions, then automatically the deprovisioning playbook will run, and the same goes for the modification playbook. Also, for both scenarios, the reviewers need to provide relevant reasons, stating why the access permission is declined or modified.
Point to note: These actions will take place automatically post the review; that's why this process is also known as the auto-remediation process.

Apart from that, Zluri also offers integration features that are quite beneficial at the time of gathering access data. Though Zluri already has data within its platform, integration allows it to gather even more valuable insights. Leveraging these integrations further enhances your access review process and strengthens the organization's overall security posture.
For example, the top priority for the company is to review the Identity System and core applications, as they pose the highest risk. The Identity System stores crucial employee data and requires timely and thorough reviews to ensure security. So what Zluri does is it integrates with Salesforce, Okta, Azure, and other applications. Further, these integrations are crucial in gathering identity system and SaaS app data, providing valuable insights and streamlining the review process.
Additionally, Zluri generates reports that are commonly associated with audit logs or audit trails. These audit reports serve as valuable documentation to share with auditors or keep as a reference for future reviews. And audit trails act as roadmaps, showcasing the changes made during previous reviews.
For instance, if an employee's admin-level permissions were changed to user-level, it becomes essential to review and ensure that the access remains appropriate or if there were further changes back to admin. Understanding the reasons behind any upgrades is crucial for maintaining proper access control.
So Zluri automatically generates reports on such changes,, which further helps in the reviewing process.
So what are you waiting for? Book a demo now and check yourself how Zluri can be a game-changing solution for you.









.svg)



.svg)
.svg)
.svg)
.svg)

.svg)

.svg)

.svg)
















.webp)







.webp)
.webp)





.webp)