Segregation of duties (SoD) policy has become pivotal in upholding data security, ensuring compliance, and safeguarding operational resilience. As an IT manager, your position plays a central role in orchestrating the seamless management of SoD policies.
The management of a separation of duties (SoD) policy holds significant importance due to its pivotal role in ensuring security and compliance. This policy serves as a crucial mechanism that carefully harmonizes the need for streamlined operations with the imperative of mitigating risks.
Doing so creates a resilient framework wherein the possibilities of misuse or unauthorized activities are methodically reduced.
The adherence to the principles of SoD goes beyond being a mere good practice; it transforms into a strategic necessity. This imperative particularly resonates with organizations aiming to navigate the intricate interplay between various responsibilities, control mechanisms, and regulatory mandates.
By upholding the core tenets of SoD, you and your teams are better equipped to bolster their overall security posture and maintain alignment with evolving compliance standards.
Let’s take a look at the top strategies to elevate SoD policy management in your organization:
Top 7 Strategic Approaches to Elevate SoD Policy Management
Here are seven strategic approaches tailored to IT managers that can elevate your SoD policy management framework:
1. Dynamic review of your organization’s risks & SoD rulesets
As your organization introduces new applications and undergoes transformational changes, the risk landscape evolves accordingly. The approach of dynamic review plays a pivotal role in consistently assessing how these shifts impact your business processes. By seamlessly aligning SoD rulesets with this evolving structure, you ensure that your policies remain relevant and effective.
Further, while vendor-provided SoD rulesets lay a strong foundation, they might not encompass the intricacies of your organization's unique processes and customizations. You can customize these rulesets through the dynamic review process, seamlessly integrating them with your specific workflows. This precise alignment greatly heightens the accuracy and efficacy of your policy framework.
Integral to this strategy is the active engagement of stakeholders. Collaborating closely with key process owners through structured training sessions facilitates a profound comprehension of high-level risk definitions. This inclusive approach effectively identifies gaps or distinctive risks that hold relevance for your organization.
The engagement of stakeholders ensures that your SoD policies are astutely informed and closely aligned with the tangible risks at hand, thus amplifying the overall effectiveness of your policy management. This strategic embrace of dynamic review streamlines resource allocation during risk mitigation and facilitates the identification of cross-application risks.
Additionally, by leveraging the insights of risk management professionals or consultants, you tap into specialized expertise that expedites risk identification and augments the overall impact of the review process.
2. Empower business ownership & accountability
Optimizing SoD policies demands a strategic shift toward inclusive collaboration. Engaging business units in the design and upkeep of SoD policies ensures precision and contextual relevance. By forging a partnership between IT and business stakeholders, accuracy in rule formulation is heightened, cultivating a sense of ownership that amplifies compliance adherence.
This synergy elevates security and fosters holistic risk management, proactively enabling your teams to address evolving challenges. To implement this collaborative paradigm effectively, foster open communication channels between IT and business representatives.
Encourage regular interactions to align policy designs with specific operational intricacies. By harnessing collective insights, your team can identify and resolve issues swiftly, bolstering security measures and fortifying your organization's compliance landscape.
3. Agile remediation for SoD violation
Agile remediation entails the implementation of dynamic and adaptable processes that facilitate the rapid identification, assessment, and resolution of SoD violations.
One pivotal component of agile remediation is the deployment of automated workflows and case management systems. These technologies play a crucial role in expediting incident response. By automating the initial stages of identification and assessment, you can significantly reduce the manual effort and time required to pinpoint and understand the nature of SoD violations.
Implementing agile remediation processes has tangible benefits for IT management and the organization as a whole. Rapid incident response helps minimize the potential impact of violations on your business operations, ensuring smoother continuity.
Moreover, these measures enhance regulatory compliance by demonstrating a proactive commitment to managing and resolving SoD concerns.
4. Integration of identity risk analytics into workflows
Enhance your organization's cybersecurity stance by seamlessly integrating identity risk analytics into your workflows. This strategic approach provides invaluable insights into user behavior, access patterns, and risk indicators, enabling real-time monitoring and instant alerts for suspicious activities.
By adopting this data-driven methodology, your IT team gains the upper hand in proactive risk mitigation and strengthens the effectiveness of SoD policies. This integration offers granular user insights, customizable alert mechanisms, and efficient resource allocation, optimizing your security protocols and decision-making processes.
Incorporating identity risk analytics amplifies your security strategy. Through continuous real-time monitoring and proactive risk management, your IT team becomes empowered to swiftly detect anomalies, ensuring regulatory compliance and promptly preventing potential breaches.
By embedding analytics seamlessly into your workflows, you bolster the efficiency of your operational processes while fortifying your system's resilience against evolving threats.
5. Ongoing education & training for SoD awareness
The significance of regular training programs in propagating SoD awareness cannot be overstated. By illuminating the rationale underpinning SoD protocols, employees gain a comprehensive grasp of how these policies safeguard critical processes and sensitive data.
Furthermore, employees become attuned to the potential ramifications of policy violations, including their role in potentially compromising the organization's security posture and regulatory standing.
A well-informed workforce is inherently more inclined to align with SoD guidelines. With an intricate understanding of the value that SoD brings to your organization, employees are equipped to make informed decisions and conduct their duties in a manner that is congruent with compliance imperatives.
This proactive approach significantly mitigates inadvertent policy violation occurrences, reducing overall organizational risk profile.
As IT managers, the strategic deployment of ongoing education and training endeavors is pivotal. By offering periodic workshops, seminars, and e-learning modules, you empower your team to continually refresh their knowledge, keeping pace with the evolving threat landscape and regulatory changes.
These initiatives foster a culture of vigilance and responsibility, where each employee becomes a sentinel of security, contributing to the overall integrity of the organization's operations.
6. Consistent policy review & adaptation
Regular reviews facilitate the identification of potential gaps or discrepancies that may arise as roles and responsibilities evolve. By proactively assessing the alignment of SoD policies with current operational practices, you can mitigate risks associated with unauthorized access, fraud, or errors.
Incorporating a collaborative approach with different business units is vital for the success of SoD policies. Establishing open lines of communication and cooperation ensures that policies are reflective of the organization's broader goals and objectives. You can actively engage with department heads, process owners, and key stakeholders to gain insights into operational changes that could impact SoD requirements.
Your organization frequently experiences transformative events, such as mergers, acquisitions, or the introduction of new business processes. These changes often necessitate adjustments to existing SoD policies. You should remain agile in responding to such shifts by promptly reviewing and modifying policies to accommodate the evolving landscape.
This proactive stance guarantees that SoD protocols remain effective in safeguarding against risks even amid organizational transformations.
By consistently reviewing and adapting SoD policies, you ensure that they remain relevant, robust, and aligned with the evolving nature of the organization. This strategic approach not only upholds security and compliance standards but also reinforces the overall resilience of the IT infrastructure.
7. Implementing a modern IGA platform
Strategic adoption of identity governance and administration (IGA) platforms emerges as a potent tool for fortified governance strategies. These platforms offer a streamlined approach to managing the intricacies of SoD policies, catering to your specific needs.
At the forefront, role-based access controls (RBAC) take center stage. Modern IGA solutions empower your teams to institute precise access privileges based on distinct job roles and responsibilities. By implementing RBAC, the risks associated with unauthorized access are substantially reduced.
You can allocate access rights with accuracy, thereby mitigating the potential pitfalls of excessive permissions and enhancing the security landscape.
Furthermore, the automation of policy enforcement stands out as a pivotal feature of modern IGA platforms. Automated policies and rules consistently monitor access and enforce controls, minimizing the need for manual intervention. This automation ensures prompt action in the face of access violations and optimizes operational efficiency.
Lastly, the overarching benefit of enhanced visibility, control, and compliance comes to the fore. The integration of role-based controls, automated enforcement, and centralized identity management empowers you with comprehensive insights into user behaviors, compliance adherence, and potential risks. Zluri is one such platform that is a leading innovator in the IGA landscape.
Ensuring SoD Policy Management with Zluri’s Advanced IGA Solution
Zluri presents a cutting-edge IGA solution that redefines how you manage SoD policies. This powerful IGA platform gives you the upper hand in governing access within your SaaS landscape while seamlessly orchestrating user lifecycles. This fortifies your security measures and ensures impeccable compliance with prevailing regulatory requisites.
Unlock a comprehensive suite of features within Zluri's IGA platform, designed to place you firmly in control of user access management. Acting as the central hub, it empowers you to master user identities, roles, and permissions across a spectrum of SaaS applications.
By seamlessly integrating with multiple SaaS platforms, Zluri simplifies the provisioning and deprovisioning of user access, effectively eradicating manual errors and guaranteeing timely, precise access control. Embark on an exploration of Zluri's revolutionary IGA solution, tailored to elevate your SoD policy management to unprecedented levels:
Harnessing proactive insights with Zluri’s data discovery engine
Zluri's IGA solution is at the forefront of redefining SoD policy management, introducing a paradigm shift in how organizations maintain a robust separation of duties while harnessing the full potential of their SaaS applications and user landscape.
Central to this transformation is Zluri's 9 discovery methods to gain complete visibility into your organization's SaaS landscape. These methods include browser agents, IDPs & SSO, direct integrations, desktop agents, active directories, HRMS platforms, MDM platforms, finance systems, and CASB platforms. This empowers your team to identify and manage SaaS applications effectively.

A strategic embrace of SoD principles
Incorporating the principles of separation of duties, Zluri elevates its commitment to the next level. By meticulously segregating data access and analysis roles, the platform sets new benchmarks in security enhancement. This meticulous approach ensures that individuals authorized for data access remain distinct from those entrusted with its in-depth analysis and interpretation.
This strategic division significantly reduces the risk of unauthorized tampering, safeguarding the integrity of your insights and strengthening compliance endeavors.
Pioneering beyond SoD: Unveiling a seamless integration landscape
Zluri's innovation doesn't culminate in SoD policy compliance. The platform seamlessly integrates with an expansive array of over 300+ SaaS applications, embodying its dedication to real-time data delivery, invaluable insights, and AI-driven alerts.
Leveraging the power of API-based integrations, Zluri conducts comprehensive data discovery across all SaaS applications, ensuring no corner goes unexplored. Furthermore, Zluri's vast library, encompassing a rich repository of more than 240,000 applications, underscores its profound understanding of the intricacies within your SaaS ecosystem.
This profound insight provides meticulous access data, affording comprehensive insights into user permissions and access hierarchies. In this role, Zluri emerges not merely as a solution but as an indispensable partner in your organization's journey toward effective SoD policy management.
Powering SoD policy management with Zluri's automation engine
Say goodbye to manual access management complexities and usher in a new era of streamlined processes that enhance efficiency and fortify security measures. Zluri's automation engine goes beyond mere user access management, seamlessly optimizing the entire user lifecycle.
From granting well-suited access to dynamically adapting permissions as roles evolve, and securely revoking access when needed – Zluri handles it all seamlessly. By entrusting these pivotal responsibilities to Zluri, your IT team can ensure impeccable operations while safeguarding your organization's invaluable SaaS app data. Embrace a future where access management is both hassle-free and secure, thanks to Zluri's automation.
By dynamically tailoring permissions in response to role changes, Zluri guarantees that individuals possess access only to the resources and features pertinent to their specific responsibilities. This heightens security by minimizing unauthorized actions and harmonizes with regulatory mandates, bolstering compliance endeavors.
The synergy between SoD and access control becomes strikingly evident during the processes like onboarding and offboarding. In the onboarding phase, Zluri facilitates the precise provisioning of access rights, meticulously aligned with each new employee's role. This proactive approach prevents the accumulation of unnecessary privileges, eradicating potential security weak points.
Similarly, during offboarding, it promptly revokes access, mitigating the risk of former employees retaining entry to sensitive systems and data.
Streamline onboarding: Zluri's groundbreaking solution for effortless access provisioning
Transform user access provisioning into a SoD-compliant, efficient, and secure process through Zluri's visionary platform. The days of manual provisioning and the associated risks are behind you, thanks to Zluri's automation, ensuring meticulous alignment with separation of duties principles.
Zluri's platform acts as a guardian against errors and over-provisioning, offering your IT team a streamlined process that's tailored to SoD mandates. Through an intuitive interface, your team gains the power to craft onboarding workflows that align precisely with job entitlements, roles, positions, and departments. This alignment ensures access privileges are set according to responsibilities, minimizing security risks and enforcing SoD compliance.
With Zluri, your IT team becomes the architect of secure and efficient access provisioning. Say farewell to manual complexities as you configure access privileges based on job roles and duties with simplicity. The result? Enhanced efficiency, elevated employee productivity, and fortified security for both users and sensitive SaaS app data—all in harmony with the tenets of SoD.
To streamline the Onboarding process using Zluri, follow these straightforward steps:
Step 1: Access Zluri's workflow module and select "Onboarding" from the dropdown menu. Begin creating your onboarding workflow by clicking on "New Workflow."
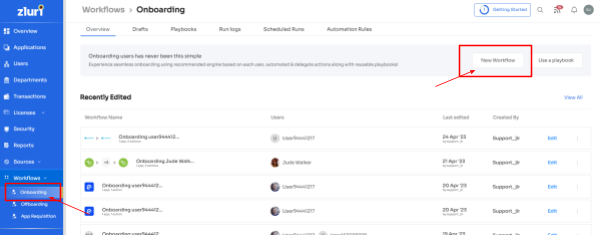
Step 2: Select a user for onboarding; easily choose the user(s) you wish to onboard. You can manually select them or utilize the search bar to find specific employees. Simply click "Continue" to proceed.
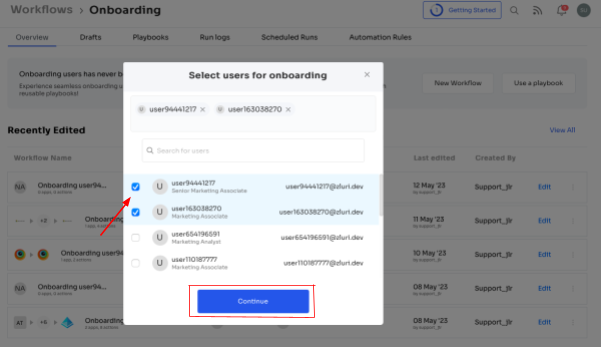
Step 3: On the left side, explore the recommended apps and select the necessary ones for the user. Define the desired actions for each application to tailor the onboarding process.
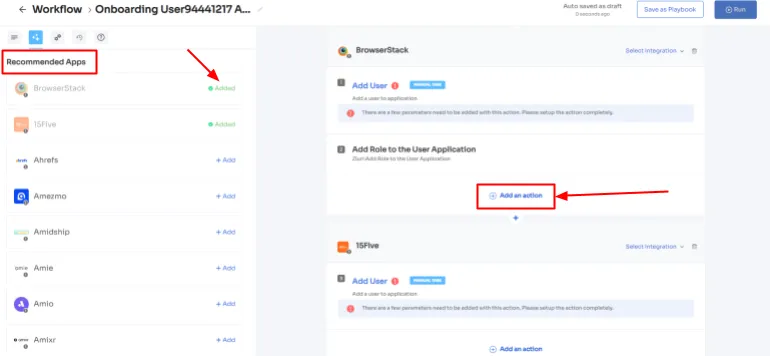
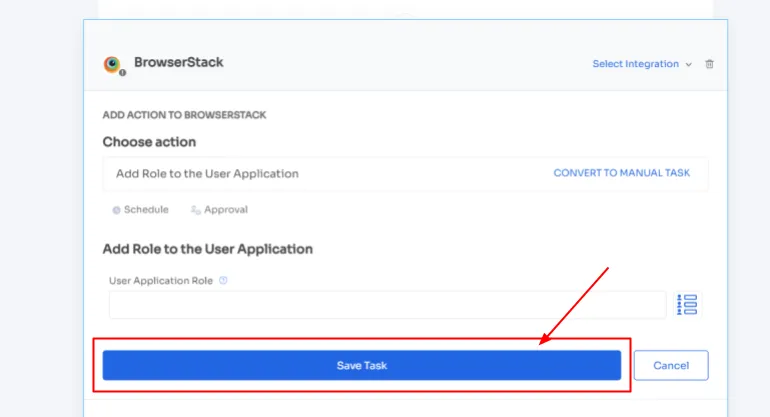
Step 4: Customize actions further by selecting "Edit Action" and providing the required details. If needed, schedule these actions to execute on the day of onboarding. Once finalized, save the actions by clicking on "Save Task."
Step 5: To preserve the workflow for future use, select "Save as Playbook." Name your playbook in the prompted dialogue box and click "Save Playbook." Your onboarding workflow is now ready to be utilized.
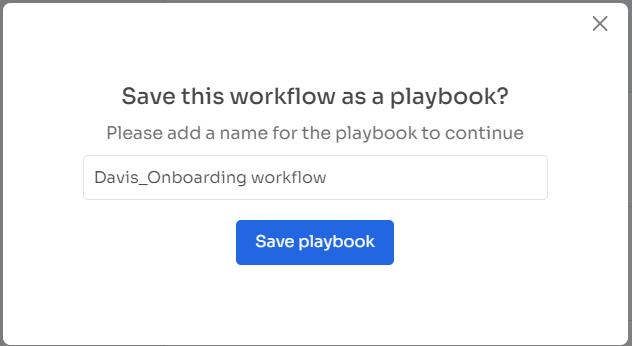
Note: Zluri's solution brings exceptional reusability and adaptability to playbooks. Effortlessly refresh these playbooks as needed, guaranteeing uninterrupted efficiency throughout your onboarding process.
Embracing Zluri's user-friendly approach, managing and adjusting your playbooks evolve into a frictionless endeavor, enabling you to progressively refine and enhance your onboarding protocols.
Streamline offboarding: Zluri's groundbreaking solution for effortless access deprovisioning
When an employee exits the organization, Zluri seamlessly revokes their access rights, effectively thwarting any unauthorized entry to critical resources. This powerful functionality ensures that former employees are unable to compromise sensitive data, drastically mitigating the risks associated with data breaches and security breaches.
Moreover, Zluri goes beyond access revocation. It seamlessly orchestrates data backup and facilitates smooth data transfer to designated successors, eradicating the possibility of critical information loss during the deprovisioning procedure. This guarantees that vital data finds its way securely to the right personnel, facilitating a seamless transition post-employee departure.
Zluri also simplifies the process of revoking employee licenses and terminating their single sign-on privileges. This proactive measure effectively bars former employees from leveraging organizational applications, proactively ensuring data security and preempting potential misuse of company assets.
By adopting Zluri's intuitive approach to managing employee departures, your organization can achieve a uniform and secure offboarding process for all outgoing personnel. This heightened efficiency and security empower both HR and IT teams to manage departures effortlessly and confidently, alleviating the administrative load and instilling assurance during potentially delicate scenarios.
Now, to streamline the Offboarding process using Zluri, follow these straightforward steps:
Step 1: Access Zluri's main interface and navigate to the workflow module. Select the offboarding option from the drop-down list and click "New Workflow."
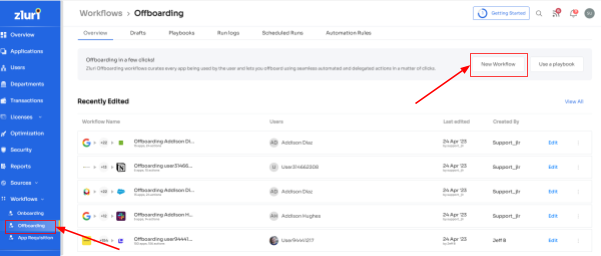
Step 2: Choose the user(s) you wish to offboard by selecting "Select the user for offboarding." Once you've made your selection, click "Continue."
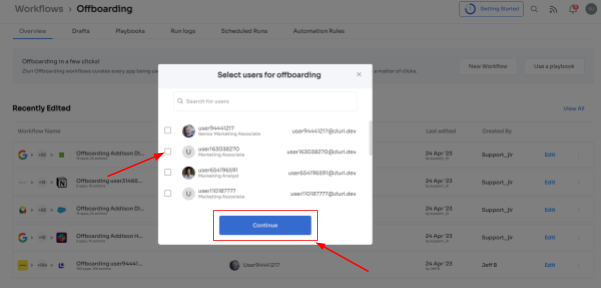
Step 3: Zluri provides recommended actions tailored to specific apps. Effortlessly choose from a range of suggested actions and execute them across the selected applications.
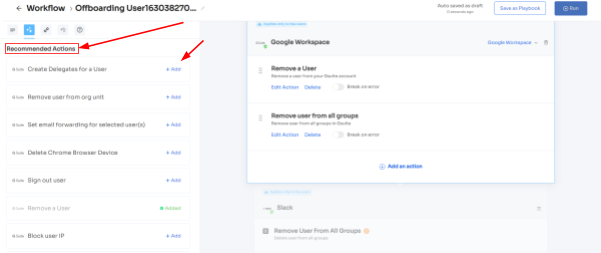
Step 4: To include additional actions, click "Add an Action." Fill in the necessary details and save the task by clicking "Save Task.".
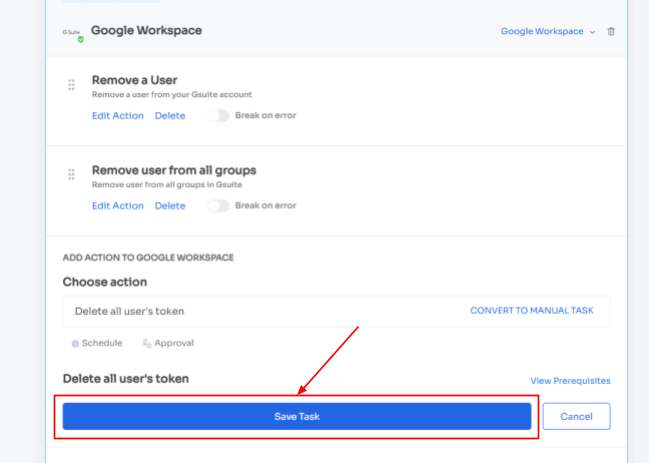
Step 5: Finalize the workflow by saving it as a playbook. Provide a name, and click "Save Playbook," your offboarding workflow is now set and ready to go.

Note: These playbooks empower you to craft workflows and define actions in response to specific triggers and conditions. This level of customization enables you to finely calibrate automation according to your organization's unique needs and workflows.
The possibilities are limitless. With automation, the deprovisioning processes are elevated, guaranteeing swift and accurate access revocation.
Enhancing SoD policy management & empowering operational efficiency through Zluri's self-service approach
Experience streamlined management of SoD policies through Zluri's innovative self-serve model. It empowers you to navigate access request processes with ease, ensuring precise access controls and adherence to regulatory standards. Introducing the employee app store (EAS), a game-changing self-serve model from Zluri that redefines user access management during role transitions.

By embracing EAS, your IT team can seamlessly handle access requests while retaining a firm grip on employees' access privileges to critical applications.
Within EAS, your team or assigned approver can meticulously review and authorize access requests, aligning them with individual job responsibilities. This approach ensures that permissions granted are in perfect harmony with specific operational necessities, fostering efficient access governance and fortifying the security of sensitive data.

Zluri introduces a transparent, multi-tiered approval framework, encompassing app owners, reporting managers, and IT admins. This hierarchy empowers senior stakeholders to make well-informed decisions, enabling them to supersede choices made by lower-tier administrators or managers. The transparent approval system promotes transparency and responsibility throughout the access request process.
In scenarios where access requests are declined, decision-makers can provide comprehensive explanations clarifying the rationale behind their verdicts. This transparent communication mechanism facilitates understanding between requestors and approvers, nurturing an environment of open discourse.
Moreover, approvers possess the flexibility to adjust specific access requests as necessitated, facilitating a dynamic and adaptable strategy towards access control.
Zluri introduces a valuable "changelog" component within its IGA solution, serving as an information hub for users. This tool empowers users to track real-time updates pertaining to their access requests. These updates encompass approval or rejection statuses, license duration or tiers alterations, and administrators' annotations.
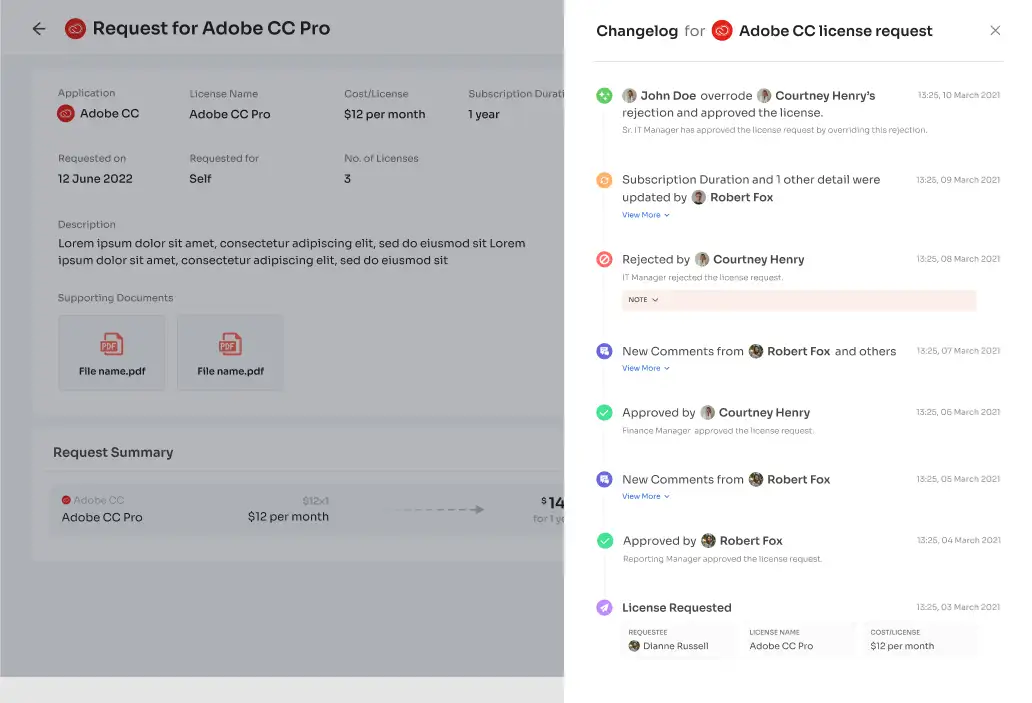
By harnessing the changelog feature, employees remain informed and engaged, gaining insights into any alterations or determinations impacting their application access.
Empower your SoD policy management with Zluri's access reviews
Zluri offers a unified gateway for access management and automated review mechanisms, providing your teams with the tools to fortify security measures, significantly reduce the risk of data breaches, and expertly manage user access rights.

With Zluri's robust features, the IGA solution accelerates SoD assessments by a factor of ten while diminishing effort by an impressive 70%. This empowerment paves the way for streamlining access management processes, translating into heightened resources and time dedicated to propelling growth and nurturing innovation within your organizational realm.
1. Automated access reviews
Through Zluri's intuitive platform, configuring access review parameters, designating reviewers, and orchestrating review campaigns becomes a breeze. This intelligent automation not only expedites the process but also eradicates the need for time-consuming manual assessments. This optimization not only saves valuable time but also minimizes the potential for inaccuracies.

Incorporating traditional access review functionalities, Zluri takes a step further by introducing auto-remediation capabilities. Detected access violations trigger automatic corrective actions, promptly addressing security concerns. This proactive stance reinforces your organization's security posture, effectively mitigating risks and ensuring adherence to compliance standards. Zluri's rapid response mechanism acts as a deterrent against security breaches and unauthorized access attempts.
Zluri's IGA system excels in swiftly revoking access for departing employees or individuals with outdated privileges. Automated access disablement by Zluri drastically reduces the exposure of sensitive information, thereby significantly lowering the risk of unauthorized data breaches. By preserving the integrity of your organization's assets, Zluri exemplifies its commitment to robust security practices.
Zluri provides auto-generated reports that offer concise summaries of access reviews to bolster decision-making and accountability. These reports shed light on access patterns, potential vulnerabilities, and compliance status. Leveraging these insightful reports empowers your teams to seamlessly demonstrate compliance to auditors and regulatory bodies, effectively showcasing your organization's commitment to maintaining airtight security measures.
2. Agile access reviews
Within Zluri's IGA framework, the focus shifts to maintaining rigorous control over access privileges by implementing agile and recurrent certifications. These certifications are fundamental in ensuring access privileges undergo consistent and systematic reviews.
By fostering a continuous evaluation process of access rights, you can promptly detect and rectify potential security gaps that might emerge. This proactive approach becomes instrumental in fortifying security measures and effectively mitigating the inherent risks associated with unauthorized access.
One of the key strengths of Zluri's IGA solution lies in its capability to facilitate well-planned and scheduled certifications carried out at predefined intervals. This structured methodology guarantees access privileges are subject to regular and timely assessments. This adherence to a predetermined schedule significantly reduces the probability of overlooking critical access-related concerns, enabling swift responses to security vulnerabilities.

Furthermore, Zluri's IGA platform presents a set of certificate templates meticulously designed to align with both industry best practices and regulatory standards. This strategic inclusion streamlines the certification process, making it more efficient and effective.
Leveraging these preconfigured templates empowers your team to conduct thorough and precise certification procedures that are in complete harmony with prevailing industry norms.
3. Real-time access reviews
By leveraging advanced AI capabilities, Zluri elevates data security measures and offers real-time access intelligence, ensuring your organization's adherence to SoD policies while maintaining robust security.
Using AI-driven anomaly detection algorithms, Zluri employs continuous analysis of real-time access patterns, user behavior, and system logs. This proactive approach facilitates the swift identification of unusual or potentially high-risk activities, empowering you to promptly detect potential violations of SoD policies and take immediate corrective actions to safeguard critical data.
This vigilance reinforces your SoD compliance strategy, mitigating the potential impact of policy breaches.
Through Zluri's platform, access reviews transcend the realm of sporadic assessments. The solution facilitates ongoing monitoring and evaluations, providing you with real-time insights into access privileges. You're constantly informed about any alterations or potential access-related concerns, enabling you to address issues in real-time and proactively minimize the risks associated with unauthorized access or policy non-compliance.
Zluri's AI-driven compliance capabilities offer intelligent recommendations and insights, supporting your organization in aligning access controls with industry regulations and standards. By integrating relevant requirements into your access management processes, Zluri significantly reduces the likelihood of SoD policy violations.
Incorporating AI technology streamlines the compliance journey, simplifying the fulfillment of regulatory obligations for your organization.

Wondering how to automate user access reviews? Zluri’s comprehensive ‘Access certification’ module has got you covered:
- Step 1: To automate access reviews, access Zluri's main interface and navigate to the "Access certification" module. Within the module, select the option to create a ‘new certification.’
- Step 2: Assign a name to the certification and designate an owner who will oversee the automated access reviews.
- Step 3: Choose the preferred method of reviewing user access by exploring the options: Application, Users, and Groups.
- Step 4: Opt for the "Application" review method if desired and add the relevant application(s) to be audited for users' access.

- Step 5: Select a primary reviewer and a fallback reviewer from the dropdown menu for the automated access reviews.
- Step 6: Select the users to be included in the automated access reviews process and apply data filtering to refine the user selection based on certification requirements.

- Step 7: Proceed to the next step and configure the actions to be performed during the automated access reviews, choosing from the provided dropdown list of actions.
Note: If there are multiple applications to be included in the same certification, repeat the process of adding applications as needed.

- Step 8: Specify the start and end dates for the automated access certification process, ensuring they align with recurring or scheduled certifications.
- Step 9: Save the configuration as a template for future use by clicking on the "Save Template" option.
- Step 10: Monitor the progress and updates of the automated access review process for the specific certification by regularly checking the "Review Stage" section.Unlock the power of Zluri's cutting-edge IGA solution for streamlined SoD policy management. Seamlessly oversee user access, ensure regulatory adherence, and fortify critical data security. This translates to enhanced operational efficiency and a heightened sense of assurance amidst the intricate terrain of the digital realm. Ready to experience the transformation? Book a demo now!









.svg)



.svg)
.svg)
.svg)
.svg)

.svg)

.svg)

.svg)
















.webp)







.webp)
.webp)





.webp)