Access gaps necessitates robust identity management and access management to ensure both security and operational efficiency. While often used interchangeably, it's vital to distinguish between "identity management" and "access management." This guide explores the key differences between the two concepts, offering clarity in navigating their distinct roles.
Identity management and access management are commonly confused terms, but they represent distinct aspects of cybersecurity. In essence, identity management involves the administration of user attributes, while access management is concerned with controlling user access based on these attributes.
To simplify, identity management verifies a user's identity through authentication, while access management authorized users for specific actions. The confusion often arises in distinguishing between authentication and authorization, where authentication establishes 'who' a person is during login, and authorization grants permission to access applications or resources.
In large organizations, managing these processes can be intricate. Implementing effective identity and access management streamlines authentication and authorization complexities, ensuring vigilant oversight of digital identities and their associated access privileges. This brief overview provides foundational information on identity management vs access management, but a deeper understanding can be gained by delving into their individual meanings.
What Is Identity Management?
Identity management is the process of managing and overseeing your employees digital identity. When employees become a part of an organization they are assigned a digital identity which includes various attributes or details. These attributes can be their job title, department, and role which further contribute to an employee's distinct identity within the organization and are typically managed by the IT and HR teams.
So by implementing identity management your IT teams can create, maintain, and verify/authenticate these digital identities and associated attributes of the employees. Also, it enables your team to manage changes in an employee's details over time, such as promotions, department change, or geo shift.
Furthermore, by implementing identity management, your IT team can ensure that individuals have the appropriate access levels at the right times. The accuracy of identity management is paramount for a company, as it directly influences access to the organization's resources and data.
How Does Identity Management Work?
Identity management primarily focuses on delivering secure and convenient authentication for extensive user groups, such as a company's workforce (employees, customers, or both). It commonly incorporates tools and technologies to establish a reliable identity management framework for verifying the identities of individuals accessing digital systems or services. These tools and technologies include:
- Single Sign-On (SSO): Identity management often incorporates SSO functionality, allowing users to access multiple systems or applications with a single set of login credentials. This enhances convenience for users while reducing the need to remember multiple usernames and passwords.
- Robust Identity Verification: it implements robust identity verification/authentication methods to enhance login security. This may include multi-factor authentication, biometrics, facial recognition, or other secure authentication measures. The goal is to ensure that only authorized individuals gain access to the system.
- One-Time Passwords (OTPs): It utilize one-time passwords as an additional layer of security during the authentication process. These temporary codes, generated for each login attempt, add an extra level of protection against unauthorized access.
- Centralized Platform: Identity management provides a centralized platform for user authentication and automated account management. This centralization streamlines the process of creating, modifying, and deleting user accounts. It offers a convenient way for administrators to manage user identities efficiently.
What Is Access Management?
Access management is a comprehensive process that involves granting, modifying, or revoking a user permission to access specific organization data or resources. The decision to either grant or remove access is influenced and determined by the user's attributes. During the authentication process, users provide their attributes, which are then examined for access authorization. To authorize a resource, one must first authenticate user identity. It is important to note that authentication identifies the user, while authorization determines whether the user is entitled to access the resource.
Moreover, within a company, individuals are typically assigned varying access levels based on their positions, roles, and responsibilities which can be challenging to keep track of and also there are multiple access points. By implementing access management, you can mitigate these challenges and empower your IT teams to effectively regulate and limit authorization for company resources according to an employee's digital/electronic identity.
How Does Access Management Work?
Access management uses specialized software to control and regulate access permissions for various systems within an organization. These tools are designed to make access adjustments and manage access to systems like active directory (used by Microsoft), file servers (compatible with Windows, Linux, SAN/NAS systems), and collaboration platforms such as Exchange or SharePoint. Also these tools provide other functionalities to streamline and simplify the authorization process, which includes:
- Permission Reporting: These tools provide a clear overview of permissions associated with different systems. For example, they can show who has access to what resources, helping your IT team understand and manage employee permissions more effectively.
- Cleanup of Chaotic Permissions: Access management tools can be particularly beneficial for organizations with chaotic or disorganized permission structures. By offering detailed reports and insights, these tools assist companies in identifying and addressing unnecessary or outdated access permissions.
Now that you are familiar with what are identity management and access management and how they work, let’s proceed further and understand their key differences.
Identity Management Vs Access Management: Comparison Based On Different Parameters
Below we’ve differentiated identity management vs access management based on different parameters. This comparison analysis will help you thoroughly understand these two critical concepts differences:
1. Scope Of Operation
Identity management vs access management have distinct scope of operations such as:
- Identity management primarily focuses on establishing and overseeing digital identities. This includes individuals, systems, or entities within a digital environment.
For instance, identity management involves managing user profiles/accounts lifecycle, encompassing their creation, modification, and deletion. As the employee progresses in their role, the system is updated to reflect changes in responsibilities or job titles. It ensures that accurate and secure information is associated with each identity throughout its existence. When an employee leaves the organization, identity management ensures the secure deletion of their user profile, minimizing the risk associated with inactive accounts. - Access management, on the other hand, is dedicated to precisely controlling and regulating permissions and privileges linked to established digital identities. It involves specifying who has access to particular data or functionalities within a system.
Robust access management involves controlling which users or roles can view, modify, or delete specific files or utilize particular features within an application. It ensures that the right individuals can access digital resources, preventing unauthorized use and maintaining a secure digital environment.
For instance, in an IT infrastructure, access management helps your IT team govern which members can access critical system configurations and network settings. It ensures that only authorized personnel, such as system admins, have the necessary permissions to modify sensitive configurations.
This granular control minimizes the risk of unauthorized access to crucial IT infrastructure elements, protecting the integrity and security of the organization's digital assets and systems.
2. The Granularity Of Control
In identity and access management, granularity of access control refers to the detail and specificity level in regulating user permissions. This parameter is pivotal to consider in order to understand the differences between identity management vs access management.
- Identity management involves broader controls, dealing with user profiles, roles, and groups. For instance, an organization might define overarching roles such as "Administrator" or "Employee" within its identity management system. These roles encompass a range of responsibilities and access rights, providing a generalized framework for user categorization.
The "Administrator" role may encompass extensive access rights across various systems and functionalities, while the "Employee" role might have more limited access. - Whereas, access management takes a more detailed and specific approach to control. It involves specifying precise permissions and access restrictions for individual users or groups based on their roles and responsibilities. For example, within the "Employee" role established by identity management, access management may further dictate specific data access rights for individual employees based on their job functions.
This could mean restricting financial data access to the finance team while allowing the marketing team access only to relevant marketing databases. Access management tailors permissions with finer granularity, ensuring that individuals have precisely the access they need for their specific tasks.
Thus, identity management sets broad categories and roles, while access management refines and fine-tunes these roles to match the exact requirements of each user's responsibilities within the organization. This approach enhances security and optimizes operational efficiency by providing individuals with the right access levels needed for their specific roles.
3. User-Focused & Resource-Focused Approaches
Identity management vs access management have different approaches, such as-
- Identity management takes a user-centric approach by establishing and maintaining accurate digital profiles of users. Imagine a scenario where an organization employs identity management to manage different employee profiles.
It would ensure that each employee's personal and professional information, such as their role, department, e-mail address, and contact details, is accurately represented in the system. This guarantees that the right information is associated with the right person throughout their tenure within the organization. - Meanwhile, access Management adopts a user as well as resource-centric approach, emphasizing the assurance that the right individuals (users) possess the right access to the right resources. Consider a database containing sensitive customer information.
Moreover, access management helps IT teams determine who, among the organization's employees, has the authority to access this database. It ensures that only users with the requisite permissions, such as customer service representatives or analysts, can retrieve, modify, or update the information within, safeguarding both the data and the organization's overall security.
Also, access management focuses on controlling and monitoring users’ access to various resources to prevent unauthorized use or any potential security breaches.
4. Authentication & Authorization
- Identity Management strives to create a robust and precise digital profile for each user within a system. The overarching goal is to maintain a comprehensive and accurate user database that securely captures essential information about individuals.
For example, in a corporate setting, Identity Management ensures that employee profiles accurately reflect their roles, responsibilities, and access requirements, contributing to a well-maintained and secure digital identity ecosystem.
This results in streamlined and secure user authentication processes, reduced instances of identity errors, and an enhanced overall user experience within the digital ecosystem. - On the other hand, the primary goal of access management is to guarantee that authorized users have tailored access to the resources they need, minimizing security gaps and preserving data integrity.
Consider a scenario where an organization utilizes access management to regulate access to confidential financial data. It ensures that only finance department personnel with appropriate roles can access sensitive financial information, preventing unauthorized use and maintaining the integrity and confidentiality of critical data.
The outcome is a controlled and monitored access landscape where authorized users can seamlessly access specific or additional resources, and unauthorized access attempts are thwarted. This leads to improved data security, reduced risks of data breaches, and the preservation of data integrity, contributing to a more secure and compliant digital infrastructure.
5. Tools & Technologies
Effective identity and access management relies on a suite of tools and technologies designed to streamline processes, enhance security, and ensure compliance. Here's an elaboration on the tools and technologies used in identity management vs access management:
- Tools and Technologies Used In Identity Management
- Single Sign-On (SSO) Solutions: Single Sign-On tools allow users to access multiple applications with a single set of login credentials.
Example: Okta and Microsoft Azure Active Directory provide SSO solutions, streamlining user authentication across various platforms. - Identity Verification Platforms: Identity vefircation software employs multi-factor authentication methods to verify the legitimacy of user identities.
Example: Auth0 and Duo Security offer identity verification solutions through multi-factor authentication, ensuring robust user authentication. - User Provisioning Systems: Systems that automate the process of granting or revoking access to enterprise resources based on predefined roles and policies.
For example, SailPoint and Oracle Identity Manager automate user provisioning, ensuring efficient onboarding and offboarding processes. - Tools and Technologies Use In Access Management
- Role-Based Access Control (RBAC) Systems: Systems that assign access rights and permissions to users based on their roles within an organization.
For example, AWS Identity and Access Management (IAM) uses RBAC principles to control access to AWS services based on user roles. - Privileged Access Management (PAM) Solutions: Access management tools that manage and monitor privilege access to critical systems and data, especially for privileged users.
For example, CyberArk and Beyond Trust offer PAM solutions to secure and monitor access to privileged accounts. - Access Governance Platforms: Platforms that ensure access policies align with business objectives and regulatory standards/requirements.
For example, RSA Identity Governance and Lifecycle provides access governance capabilities, helping organizations maintain compliance and control.
Also Read: To choose a suitable tool, consider reading How to choose a suitable IAM solution for your organization
By leveraging these tools and technologies, organizations can establish a robust framework for access management vs identity management (iam vs idm), enhancing overall security posture, compliance, and efficiency in their digital environments.
Comparison Table: Identity Management Vs Access Management
To provide you with a complete overview here’s a quick comparison table of identity management vs access management (IdM vs IAM)-
But how will you come to know whether an identity management solution aligns with your needs or access management solution? Well there are various factors that you need to consider. To provide you with better understanding, let’s dive deeper.
Choosing Between Identity Management & Access Management
Choosing the right solution for your organization depends on the unique needs of your IT setup. Factors like the size of your company, the number of accounts, and the complexity of your access structure play a crucial role in this decision.
If you're a small organization dealing with a limited number of accounts but facing challenges with a large volume of data and a complex access structure, considering an access management solution or a data governance tool might be the best fit. These tools are designed to provide strong control over user access, ensuring secure and efficient management of data resources.
On the other hand, if your organization deals with a large number of accounts and doesn't require intricate permission adjustments among different user groups, a straightforward identity management solution could be sufficient. This type of solution is designed for simplicity, offering an easy way to manage user accounts without the complexities of fine-tuning permissions for diverse user groups.
In short, the software and features your organization needs should be aligned with a clear understanding of your operational requirements. Whether it's implementing advanced access management solutions for complex access structures or opting for identity management tools to handle numerous accounts efficiently, aligning your choices with your organizational needs ensures an optimal IT setup.
However, you also might be wondering what if we combine and use them together. Can they work together? Let’s find out.
How Identity Management & Access Management Work Together?
Authentication is a crucial element of identity management, ensuring that a user or entity is verified when attempting to access a system. On the other hand, access management relies on authorization to determine whether the authenticated entity has the appropriate access rights to the requested IT resource. We know that they have their own specific focuses, but can they work together? Yes identity management and access management can work together. Here's how these components work in tandem:
- When a user or entity attempts to access a system, it undergoes authentication to confirm its claimed identity. If the authentication is successful, it means they can proceed to the next step.
- Once authenticated, the authorization process comes into play to grant, modify, and remove necessary access to the user based on their predefined attributes.
For instance, consider a scenario where a member of the accounting team wishes to log in. Upon providing their credentials or completing multi-factor authentication (MFA), they go through the authentication process. When they attempt to use the accounting software, the authorization process verifies their role within the organization and grants access to the application.
However, if the same user tries to access the company's HR database or the CEO's mailbox, the authorization process will deny the request. This denial occurs because the user's role or permissions may not align with the necessary access rights for these particular resources.
Thus, the collaboration between identity management and access management ensures that only authenticated entities with the appropriate permissions gain access to relevant corporate resources, maintaining security and data integrity.
After going through the authentication and authorization process you may have realized how challenging they can be to manage without a proper solution. Fortunately, the market offers solutions that are designed to simplify both identity management and access management. One such solution that stands out from the rest is Zluri. What is Zluri? How does it work? Here’s a quick read-through.
How Zluri Helps Effectively Manage User Identities & Their Access Permissions?
Zluri is an advanced access management solution that is designed to streamline and simplify identity and access management processes, such as managing user accounts, granting, modifying, and revoking access, enforcing policies, adhering to stringent compliance regulations, and more. This helps ensure only the right user has access to the right application or other organizational resources at the right time which further helps in maintaining a secure access environment.
Let’s have a quick look at how it works and the benefits it offers:
Seamlessly Assigning Digital Identity
Zluri’s access management enables your IT team to assign new employees their digital identity upon onboarding. How does it do that? Zluri’s access management fetches all the data associated with the new employees profile which helps the IT team to assign them identities based on different attributes. Also, it updates the data on HRMS through integration. This integration ensures that all the information is up-to-date which further helps in the access management process.

Authenticates The Identity Before Granting Access
Once your IT team has assigned new employees digital identity, with Zluri’s access management they further create accounts for the new employees. So, at the time of granting them access, your IT team quickly cross checks their digital identities before granting them required access.
Effectively Manages Employee’s Access
After authenticating employees' identities, Zluri’s access management seamlessly grants the employees the required access to SaaS apps, data, and systems. This helps ensure new employees hit the ground running from day one.
Also, upon employees mid-lifecycle change, Zluri’ access management enables your IT team to adjust or modify their access. How do they even come to know if there is a change in an employee's role? Well, Zluri integrates with the HR system so all the updated information is notified to the IT team so that they can take necessary actions without any delays.
Lastly, when the employees depart from the organization, your IT team can promptly revoke all the access from the employee. This reduces the risk of data breaches associated with lingering access rights
Enforces Access Policies
Zluri’s access management enables you to enforce segregation of duty policy (SoD), role-based access control (RBAC), the principle of least privilege (PoLP), and just-in-time access. These security policies help ensure only authorized users have access to organization resources.
- Enforcingthe SoD policy enables you to ensure no two individuals are responsible for completing one task.
- Implementing role-based access control enables you to ensure the access permissions align with the user's roles and responsibilities.
- Enforcing the least privilege principle enables you to ensure minimum access permissions should be granted to employees. This allows you to avoid over-provisioning or granting excessive privilege.
- Enforcing just-in-time access enables you to grant employees temporary or just-in-time access to required apps for a specific duration. This way, you can reduce the attack surface caused by standing privileges.
Thoroughly Monitor Access Activities
Zluri’s access management enables your IT team to monitor all access activities within your organization. Including which user has access to which applications, their status as active or inactive, what permission level they hold, and more.
Your IT team can understand access patterns and user behavior by keeping track of user's access activities. This will help your team ensure that only authorized users access sensitive SaaS application data. This way, your team can establish a well-governed and secure environment.
In fact, Zluri has been named in the Gartner® Report: Reduce Your IAM Attack Surface Using Visibility, Observability, and Remediation. Download now!
Gartner, Reduce Your IAM Attack Surface Using Visibility, Observability, and Remediation, Rebecca Archambault, 8 October 2025
Gartner is a trademark of Gartner, Inc. and/or its affiliates.
Gartner does not endorse any company, vendor, product or service depicted in its publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner publications consist of the opinions of Gartner’s business and technology insights organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this publication, including any warranties of merchantability or fitness for a particular purpose.
Performs Periodic Access Review
Zluri’s access management assists your IT team in conducting routine access review. These reviews involve evaluating users' existing access permissions to determine whether they should continue having the access permissions. By reviewing the user access rights, your IT team can easily detect if any user holds unauthorized or excessive user access rights. Accordingly, your team can right-size their permissions or restrict access to critical applications.
Also, it's highlighted in Kuppingercole's research and analysis report that with Zluri, your team can record the user access review audits. These records can be presented as evidence of compliance by demonstrating that access permissions align with these updated compliance regulations. This way, you can avoid paying hefty fines and being non-compliant.
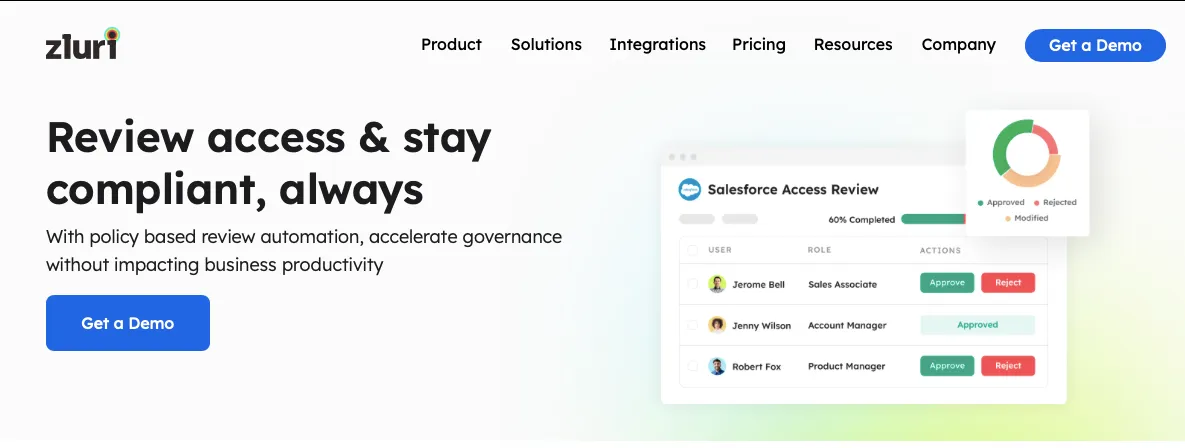
Generates Curated Reports
It also generates curated reports that play a pivotal role in identity and access management (IAM). These reports provide visibility into who has access to what systems and data. This visibility is essential for maintaining a clear understanding of user privileges and prevent potential security risks.
So now that you are familiar with Zluri’s access management capabilities, why not book a demo now? And experience it firsthand. You never know this solution can be a perfect fit for your organization.
FAQs
What Is Access Control & Identity Management?
Access control and Identity management involve the management of access to organizational resources to ensure the security of systems and data. Serving as a fundamental aspect of your security framework, these practices aid in authenticating users' identities, ensuring that they are granted the appropriate level of access to workplace systems and information.
What Is The Difference Between Identity And Access Management And IGA?
IAM systems commonly consist of tools for authentication, authorization, and administration, offering a structure for managing identities and access across an organization during their life cycle. On the other hand, identity governance and administration (IGA) is a broader concept that not only includes IAM but also expands to encompass governance and compliance requirements.
What Is The Difference Between Access Management And Governance?
Access management provides technical tools to control who has access to what. On the other hand, access governance ensures that access control adheres to your organizational objectives and regulatory mandates.
What Is The Difference Between Identity And Access Management IAM basic?
The basic difference between identity and access management is that identity management focuses on user accounts, while access management deals with permissions and privileges. Identity management handles who the users are, while access management controls what they are allowed to do or access.
What Is The Difference Between Identity Management and Credential Management?
Identity management is about managing and securing digital identities, while credential management specifically deals with the secure handling of authentication credentials such as passwords or biometric data.
What Is The Difference Between Active Directory And Identity And Access Management?
Identity and access management focuses on managing identities and controlling access to an organization's systems, applications, and data. On the other hand, Active Directory serves as a centralized directory service specifically storing and managing information about users and assets in a network, including their roles and associated network privileges.









.svg)














