Are you confident that your organization’s IT general controls can withstand security threats and compliance checks? With evolving threats and stricter regulations, even minor gaps in IT general controls can leave your organization exposed. An ITGC audit checklist simplifies this process, helping you find vulnerabilities, enforce controls, and ensure compliance- before issues escalate.
Think about this- your organization’s IT systems store sensitive data and run critical processes. Now, imagine what could happen if the controls protecting this data are weak or missing. Scary, right? That’s exactly why ITGC audits are so important.
But here’s the catch—how do you make sure your audit process covers everything it should? That’s where an ITGC audit checklist comes in. Whether you manage audits manually or use automation tools, a checklist keeps you on track and helps you avoid costly mistakes.
Picture this: your company stores customer financial data, and one day, an employee- who shouldn’t even have access- manages to view and leak that information. Suddenly, you’re dealing with a data breach, regulatory fines, and reputational damage. Sounds like a nightmare, doesn’t it?
Now, imagine you had an ITGC audit checklist in place. It would’ve flagged gaps in access management, caught weak controls early, and ensured compliance with security policies—saving you from all the trouble.
In this blog, we’ll walk you through exactly what an ITGC audit checklist should include and how to use it effectively.
ITGC Audit Checklist: 6 Key Details to Consider During the Audit
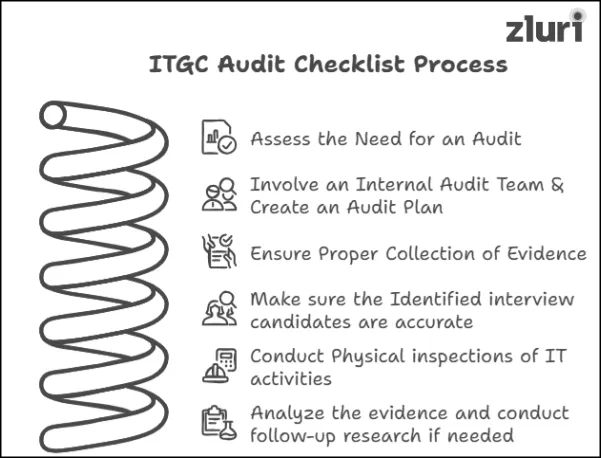
Conducting an ITGC audit requires careful planning, execution, and analysis. Whether your goal is to meet regulatory requirements, strengthen IT governance, or mitigate security risks, following a structured checklist can simplify the process.
This step-by-step ITGC audit checklist will guide you through every critical stage- from assessing the need for an audit to analyzing findings and presenting actionable insights.
1. Assess the Need for an ITGC Audit
Why do you need an ITGC audit in the first place? Before jumping into the process, step back and identify what’s driving the need for the audit (a crucial part of the ITGC audit checklist). Is it a regulatory requirement? Are there gaps in your security standards? Or maybe you’re facing risks that could threaten your IT systems.
Start by evaluating these triggers and discussing them with your management team. Highlight how the audit can address compliance issues, mitigate risks, and strengthen your organization’s IT governance. Clear communication at this stage ensures everyone is aligned and understands the audit’s purpose.
Once there’s an agreement, make it official- seek formal approval. This step in the ITGC audit checklist not only locks in leadership support but also helps you allocate resources and set expectations upfront. With everyone on board, you can move forward confidently, knowing the audit has the backing it needs to succeed.
Now that you have secured management’s approval, the next step is to build an internal audit team and create a clear roadmap for the process. Let’s dive into how to assemble the right team and structure the audit plan.
2. Involve an Internal Audit Team & Create an Audit Plan
With management's approval in hand, it's time to build your internal audit team—one of the most important steps in the ITGC audit checklist. Bring together the right people, such as IT experts, compliance specialists, and auditors. This mix of perspectives ensures you cover all critical areas and strengthens the audit's accuracy and credibility.
Once your team is in place, the first task is to identify the ITGC controls you need to audit. Focus on areas directly tied to the audit's purpose—whether it's access control, system lifecycle management, or IT operations. Prioritize controls that protect sensitive data, reduce vulnerabilities, and ensure compliance.
Note: Map out the controls based on organizational priorities and known risks to address what matters most.
Next, create an audit plan. Clearly outline the audit's objectives, scope, and timeline. Include steps for testing controls and evaluating their effectiveness. A well-structured audit plan keeps your team organized and builds transparency with stakeholders and management.
By aligning your audit plan with business goals and focusing on critical controls, you’ll set the stage for a smooth and effective ITGC audit.
With the audit plan in place, the next step (in the ITGC audit checklist) is to collect evidence demonstrating whether the controls are working as intended. Let’s look at how you can gather and organize this evidence effectively.
3. Ensure Proper Collection of Evidence for Examination
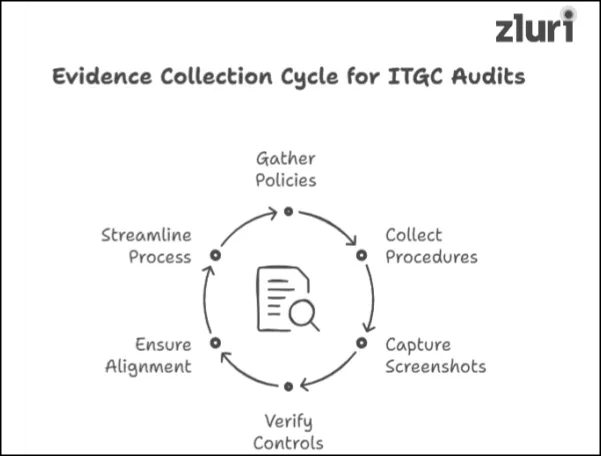
How do you prove your IT controls are actually working? That’s where collecting the right evidence comes in—a key step in the ITGC audit checklist. Start by gathering policies, procedures, and screenshots that demonstrate how controls are applied within your organization. These documents and visuals are essential to verifying that your controls are in place and functioning as expected.
Note: Gathering accurate evidence builds trust in the audit findings and avoids gaps that could lead to compliance issues.
Ensure the evidence directly supports the controls being audited. For instance, policies should align with compliance goals, and screenshots should provide proof of real-world practices.
You can collect evidence manually or with the help of automated tools. The manual collection involves reviewing documents and capturing screenshots. While effective, automation streamlines the process, reduces human errors, and ensures no critical detail is overlooked.
You set a solid foundation for accurate audit findings and actionable insights by carefully gathering and examining evidence.
Now that you have gathered evidence, the next step is to interview the right candidates to gain insight into how these controls are implemented and managed.
4. Make sure the Identified interview candidates are accurate
How do you ensure the right information about your IT controls is collected? It starts with identifying the right people to interview candidates—a critical part of the ITGC audit checklist. Focus on selecting individuals who are directly involved in managing the controls being audited. Their insights will help verify whether the controls are implemented and functioning as intended.
Note: Choosing the right candidates saves time and ensures productive discussions during the process.
Once the candidates are identified, schedule interviews at convenient times and share a clear agenda in advance. This gives them time to prepare, ensuring productive and focused conversations.
During the interviews, ask questions that assess their knowledge and responsibilities related to the controls, such as:

- What is your role in managing this specific control?
- How is this control implemented and monitored?
- Have there been any challenges or incidents related to this control?
- Are there any areas for improvement in the current process?
By conducting well-structured interviews, you will gather valuable insights into how controls are managed and identify gaps that need attention.
While interviews provide insights into how controls are managed, physical inspections offer a hands-on approach to verifying their implementation and effectiveness. Let’s now look at how conducting physical inspections (a critical part of the ITGC audit checklist) can further validate your IT activities.
5. Conduct Physical inspections of your IT activities
What’s the best way to confirm that IT controls are working as described? Sometimes, seeing is believing- that’s why physical inspections are an important step in the ITGC audit checklist. For example, conducting a data-centric walkthrough (if applicable) can give you first-hand insights into how controls are implemented and maintained.
Note: Preparing in advance ensures inspections cover all critical areas and focus on audit objectives.
Before starting, review the controls you’ll be inspecting and create a checklist of key areas to examine, such as:
- Access controls: Check badge or biometric access logs to verify who can access restricted areas.
- Equipment security: Review maintenance records and observe workflows to confirm proper practices.
- Environmental safeguards: Assess physical protection, such as fire suppression systems and temperature controls.
While on-site, run tests to confirm whether these controls are working as intended. For example, test access restrictions to see if unauthorized entry is blocked or review maintenance logs to check for gaps.
By observing physical setups and processes, you can validate whether documented policies align with real-world practices and uncover any gaps that need to be addressed.
With the inspection complete, it’s time to analyze the evidence (the final part of the ITGC audit checklist) you have gathered and examine your findings more closely.
Also Read: If you want to know more about access controls, consider reading 4 types of access controls.
6. Analyze the evidence and conduct follow-up research if needed
How do you turn collected data into meaningful results? This is where analyzing evidence becomes a key step in the ITGC audit checklist. It’s about carefully reviewing the information to assess whether controls are effective or if there are any gaps or inconsistencies that need attention.
Note: Conducting follow-up research ensures that any unclear areas are resolved, giving you complete and accurate results.
Start by organizing the evidence and looking for patterns or issues indicating weaknesses. If something seems unclear, dig deeper- this may mean asking follow-up questions or gathering additional information to validate your findings.
Once the analysis is completed, document your findings in a structured report. Make sure to:
- Highlight areas where controls are effective
- Point out weaknesses and provide clear recommendations for improvement.
- Summarize risks and potential impacts in simple terms.
Tip: Use visuals like charts and graphs to make the report easier to read and present.
Finally, share the report with management and walk them through the key findings. This will ensure they understand the results and the net steps needed to strengthen IT governance.
By analyzing evidence thoroughly and presenting actionable recommendations, you turn audit findings into real improvements that add value to your organization.
By following this ITGC audit checklist step-by-step, you ensure the organization is well-prepared to evaluate IT controls, address weaknesses, and maintain compliance. With a solid foundation, your organization can continually improve governance and security in an ever-evolving IT landscape.
Transform Your ITGC Audit Process—From Manual to Automated Compliance
Managing IT general controls (ITGC) audits can often feel overwhelming- especially when performed manually. From tracking user access to generating compliance reports, the process is time-consuming, error-prone, and resource-intensive.
For example, reviewing user access across multiple systems might involve sorting through dozens of spreadsheets, logs, and permissions lists. This manual approach increases the risk of human error and creates compliance gaps that could lead to audit failures.
Role of Automation in Simplifying ITGC Audits
Automation offers a more efficient and reliable alternative to manual processes. Instead of spending countless hours verifying user permissions, an automated solution like Zluri can stream access reviews, quickly identify compliance issues, and reduce oversight risks.
Let’s break it down further:
1: Centralized Access Management
Tracking user access manually becomes complicated, especially in organizations using hundreds of SaaS apps and cloud services. Without centralized visibility, it’s easy to lose track of who has access to what.
How Zluri Helps?
- Provides a single dashboard to monitor all user permissions across platforms and tools.
- Detects inactive and orphaned accounts that could pose security and compliance risks.
- Automated real-time updates for role-based access control to ensure permissions align with job roles.
For example, imagine an IT administrator who left the company but still has active credentials in your Cloud storage and financial systems. Zluri automatically flags these accounts, helping you revoke access instantly and preventing unauthorized activity.
Also Read: Compliance Risk Management: An In-Depth Guide
2: Continuous Monitoring & Risk Alerts
Compliance isn’t just about preparing for audits- it’s about maintaining security year-round. Continuous monitoring ensures that compliance gaps are identified and resolved promptly before they escalate into major issues.
How Zluri Helps?
- Tracks change in user roles and permissions in real-time.
- Sends alerts for policy violations, such as over-permissive access or failed login attempts.
- Integrates with identity providers to enforce consistent access rules across systems.
For example, suppose a contractor was granted temporary access to sensitive financial records. Zluri can set alerts to track when the contractor logs in and ensure access is revoked immediately after the contract ends.
Also Read: Temporary Elevated Access for SaaS Apps
3: Automated Access Reviews
Conducting periodic access reviews manually can be tedious, often requiring hours of data compilation and validation. With automation, reviews are faster, more accurate, and easier to manage.
How Zluri Helps?
- Schedules and automates recurring access reviews to ensure compliance with ITGC standards.
- Provide customizable templates for access certifications, simplifying the review process for managers.
- Flags exceptions automatically, reducing the need for manual oversight.
For example, consider a scenario where a department head needs to review permissions for 50 employees. Instead of manually verifying each access level, Zluri generates a pre-filled report highlighting mismatches or risky permissions- cutting review time by 70%
4: Audit-Ready Reporting & Evidence Collection
Audit preparation often involves collecting and organizing evidence to provide compliance. Manually compiling these reports can lead to missing data or inconsistencies.
How Zluri Helps?
- Generates audit-ready reports that summarize access control activities and policy enforcement.
- Logs all changes and actions related to user access, creating a clear audit trail.
- Provides exportable reports for external audits, ensuring compliance with frameworks like SOX, ISO 27001, and SOC 2.
Also Read: 8-Step SOC 2 Audit Checklist
For example, when undergoing a SOC 2 audit, organizations often struggle to produce evidence for periodic user access reviews. Zluri automatically compiles detailed reports, showcasing review timelines, remediation actions, and approvals- simplifying audit submission.
Thus, it wouldn’t be wrong to say that manually doing ITGC audits is no longer sustainable for modern organizations. Therefore, if you’re ready to transform your ITGC audit process, schedule a personalized demo with Zluri today and make compliance management effortless.
Now, let’s take Intune as an example to see how you can automate access review in Zluri.
Also Read: If you’re looking to streamline your access review process with Zluri, consider reading the case study of Assured Allies.
Frequently Asked Questions (FAQs)
1. What are the examples of logical access controls?
A few examples of logical access controls include passwords and PINs, multi-factor authentication (MFA), role-based access control (RBAC), and security tokens. These will ensure that only authorized persons have access to certain digital resources.
2. What is the ITGC audit scope?
ITGC audits gauge the effectiveness and security level of an organization's information systems and technology infrastructure. These may include auditing system controls, data integrity, cybersecurity provisions, and IT governance processes within their scope.
3. Who are the external auditors?
The external auditor will examine the internal process to confirm that they are aligned with the required compliance standards (relevant rules and regulations governing your organization). They may make suggestions for improvements to enhance compliance. Further, a poor compliance record can become a barrier for potential investors or acquirers.
4. What is involved in a compliance audit process?
Conducting a compliance audit process involves the following:
- Planning
- Risk assessment
- Creating an audit program
- Reviewing documentation
- Conducting interviews and testing controls
- Analyzing findings
- Reporting results, and recommending corrective actions









.svg)














