As an IT manager, ensuring the security of sensitive information and maintaining the integrity of business processes is paramount. One effective way to achieve these objectives is by implementing a robust system of Separation of Duties Policy.
Implementing a robust Separation of Duties policy is crucial for fortifying organizational integrity and compliance. By adhering to SoD principles, IT managers can proactively address regulatory requirements, enhance operational efficiency, and bolster defenses against potential risks.
This guide aims to equip IT managers with the necessary knowledge and insights to navigate the complexities of SoD policy, thereby establishing a resilient and secure organizational framework.
What is Separation of Duties?
Separation of Duties (SoD) or Segregation of Duties stands as a vital internal control mechanism crucial for organizations to combat errors and fraud effectively. Its significance is particularly pronounced in regulatory compliance scenarios such as adherence to the US Sarbanes-Oxley Act of 2002 (SOC).
SoD ensures that critical business processes involve the participation of multiple individuals, thereby minimizing the likelihood of errors or fraudulent activities.
Within any organization, employees holding multiple functional roles possess the potential to misuse their authority and knowledge. Thus, integrating SoD into risk management strategies becomes imperative for enterprises seeking robust protection against such risks.
The SoD policy is a set of guidelines and procedures implemented within an organization to ensure that no single individual has complete control over a particular process or task from beginning to end. The core principle of the SoD policy is to distribute responsibilities among multiple individuals or teams to prevent conflicts of interest, errors, and fraud.
For example, while one individual may initiate an order with a supplier, another individual must handle the recording of the transaction. This systematic approach significantly mitigates the risk of fraud by thwarting scenarios where individuals may unlawfully initiate orders and then manipulate transaction records, either by omission or through misrepresentation of values.
Components of Separation of Duties Policy
Key components of a Separation of Duties policy typically include:
- Identification of Critical Processes: Identifying the key business processes and tasks that are critical to the organization's operations, security, and financial integrity.
- Assignment of Roles and Responsibilities: Clearly defining roles and responsibilities for each employee involved in the identified processes. This involves specifying who can initiate, approve, execute, and review various tasks.
- Segregation of Duties: Ensuring that no single individual has the authority to complete an entire process independently. Tasks are divided in such a way that different individuals or teams handle distinct stages of a process to create checks and balances.
- Rotation of Duties: Implementing periodic rotation of job responsibilities among employees to mitigate the risk of collusion and fraud. This prevents individuals from becoming too familiar with a specific area and potentially exploiting it for personal gain.
- Monitoring and Enforcement: Regularly monitoring compliance with the SoD policy and enforcing consequences for violations. This may involve audits, reviews, and controls to ensure adherence to the established guidelines.
- Documentation and Training: Documenting the SoD policy and providing training to employees to ensure they understand their roles and responsibilities. Clear communication is essential to foster awareness and compliance across the organization.
Few Examples of Organizational Roles that Require SoD
Here are examples of a few organizational roles that require SoD policy.
- Record-Keeping Roles: Individuals in this role are responsible for creating and maintaining financial reporting that documents all the transactions within the organization. It is important to ensure that these individuals are different from those who issue or hold responsibility over transactions. This separation ensures a checks-and-balances system and reduces the risk of fraud or errors.
- Authorization Roles: Individuals in authorization roles are responsible for evaluating and recording transactions. It is important that these individuals are segregated from the record-keeping process and from reconciling or review of transactions. This segregation of duties can help prevent conflicts of interest and enhances the accuracy and integrity of financial reporting.
- Asset Manager Role: The individual in this role manages or has access to physical assets like inventory or cash. They in no way should be responsible for recording inventory, reconciling bank accounts, or approving transactions. separating these responsibilities reduces the risk of mishandling assets and maintains proper control.
- Reconciliation Roles: This role is responsible for verifying the accuracy and completeness of transactions. It should be segregated from roles involved in requesting or approving transactions. This separation of duties can guarantee an independent review process, reducing the chances of errors or fraudulent activities going unnoticed.
Let's explore the various examples of Separation of Duties policy that will ensure a secure and transparent environment.
7 Essential Separation of Duties Policy Examples
Here are the 7 separation of duties policy examples:
Example 1: Optimized User Access Management
Within your organization, a meticulous Segregation of Duties policy is rigorously enforced by the IT department to uphold a secure access management.
Access Provisioning Team: Operating within this framework, two distinct teams oversee user access management: the access provisioning team and the access review team. The access provisioning team is tasked with the seamless onboarding of new users, tailoring permissions to align precisely with their roles and responsibilities. This ensures swift and efficient access to the requisite SaaS applications.
For instance, upon a new employee's arrival, whether they belong to the sales department or another division, the access provisioning team diligently configures their access privileges. This could involve granting Customer Relationship Management (CRM) access to sales personnel for customer data management and sales tracking, among other necessary permissions.
Access Review Team: Conversely, the access review team assumes a crucial role in regularly auditing user access rights to preempt potential security vulnerabilities. Their mandate includes conducting periodic user access reviews to validate that user permissions remain aligned with job roles and responsibilities. Prompt action is taken to revoke unnecessary access for employees who change roles or depart the organization.
Consider, for example, an employee transitioning from a sales position to project management. The access review team promptly ensures the removal of CRM access, aligning permissions with the employee's new responsibilities. This proactive approach effectively mitigates the risks associated with unauthorized access, thereby reducing the likelihood of data breaches or misuse.
Example 2: Enhanced Data Backup and Recovery
Imagine an IT department in a large organization responsible for crucial data backup and recovery. Traditionally, these tasks are overseen by a single individual, the IT admin, who manages everything from backups to data retrieval.
Challenges of Centralized Control: However, this setup poses risks. What if the IT admin accidentally deletes important files or is unavailable during a system failure? This is another separation of duties policy example that could prevent severe data loss and significant downtime.
To address these risks, the IT manager implements Separation of Duties policy. This means splitting backup and recovery tasks among different roles to prevent one person from having complete control.
New Role Assignments: Under this revised setup, distinct responsibilities are assigned to different individuals:
- Backup Administration: A dedicated backup administrator is tasked with initiating and overseeing the backup process. Their primary focus includes ensuring regular backups of critical data, maintaining functional backup systems, and adhering to back up schedules.
- Monitoring and Verification: Another team member assumes the role of monitoring and verification. Their major duties encompass overseeing backup systems, validating backup data integrity and completeness, and conducting routine test restores to verify backup recoverability. They also remain vigilant for any potential errors or anomalies during backup operations.
- Data Recovery Expertise: A specialized individual is entrusted with data recovery responsibilities. Their expertise comes into play during data loss incidents or when data retrieval from backups is necessary. They excel in swift and efficient data recovery, minimizing downtime and swiftly restoring critical systems and data.
By integrating SoD policy into the data backup and recovery process, the organization significantly mitigates the risk of inadvertent data loss, enhances system availability, and fortifies overall data protection measures.
Moreover, it establishes a robust system of checks and balances, ensuring no single individual holds the power to compromise the integrity or reliability of backup and recovery operations.
Example 3: Enhanced Vendor Management
As an IT manager overseeing vendor management in your organization, your role is pivotal in ensuring efficient procurement of IT assets and services from external suppliers. However, relying solely on one individual to handle all vendor-related activities can expose the organization to various concentrations of risk, including fraud, errors, and strained vendor relationships.
To mitigate these risks and optimize vendor management processes, it's imperative to implement robust Segregation of Duties policy and procedures.
This separation of duties policy example in vendor management involves distributing tasks and responsibilities among multiple individuals to establish checks and balances. Let's delve into an example to elucidate this concept further:
Initially, all vendor management responsibilities, from vendor selection to payment approval, are consolidated under the purview of the procurement manager. While this setup may appear convenient, it presents inherent vulnerabilities and lacks oversight.
To address these concerns, your organization adopts SoD principles within the vendor management framework, dividing tasks into distinct roles:
- Vendor Selection: Assigned to research and identify potential vendors based on requirements and budget constraints.
- Contract Negotiation: Responsible for negotiating SaaS contracts to ensure alignment with organizational needs and legal standards.
- Payment Approval: Handles financial transaction process, verifying invoices and authorizing payments within budget limits.
- Vendor Performance Evaluation: Assesses vendor performance, monitoring quality and addressing issues promptly.
In this way, each employee involved has a distinct role, reducing the risk of fraud, errors, or bias. It ensures that no single individual has excessive control over the entire vendor management process, enhancing transparency, accountability, and efficiency.
Example 4: Enhanced Risk Management
In an organization leveraging a cloud-based project management SaaS application, effective risk mitigation is paramount. Implementing Segregation of Duties policy measures within the IT team can bolster security and preempt potential issues.
User Access Management: Segregating duties related to user access management in the SaaS app is crucial. For instance, one team member can focus on creating user accounts, while another oversees access permissions and role assignments. This division ensures separate activities for account creation and privilege allocation, mitigating unauthorized access risks.
Configuration and Monitoring: Similarly, segregating duties concerning configuration and monitoring of the SaaS app is essential. One team member configures settings and defines security controls, while another monitors system logs for anomalies. This separation reduces the likelihood of errors or security breaches, preserving data integrity and confidentiality.
Data Backup and Recovery: To safeguard critical data, SoD can be implemented for data backup and recovery processes. One team member schedules and performs regular backups, while another validates and tests the restoration process. This ensures diligent and independent backup procedures, minimizing the risk of data loss or corruption.
By employing SoD measures across these areas, the organization strengthens its risk management framework, fortifying security and safeguarding critical data against potential threats.
Example 5: Network Administration
In the IT department, network administration involves managing the organization's computer networks, including hardware, software, and security measures. Here's how IT separation of duties can be implemented:
Network Configuration: One team or individual is responsible for configuring network devices such as routers, switches, and firewalls to ensure optimal performance and security. This includes setting up network protocols, IP addresses, and access control lists (ACLs) to restrict unauthorized access.
System Administration: Another team or individual is responsible for managing servers, including installing operating systems, configuring user accounts, and monitoring system performance. This separation ensures that changes to network infrastructure do not compromise server stability or security.
Security Monitoring: A dedicated team or individual monitors network traffic for suspicious activity, identifies security threats, and implements measures to protect against cyber attacks. This division ensures that security monitoring is conducted independently of network and system administration, reducing the risk of insider threats or oversight.
By implementing this separation of duties measures, the IT department can enhance network security, minimize the risk of unauthorized access or data breaches, and ensure the reliability and availability of critical IT services.
Example 6: Human Resources Management
In the human resources department, the separation of duties policy helps protect sensitive employee information and ensures compliance with employment laws and regulations. Here's how it can be applied:
Recruitment and Hiring: Separate individuals or teams should be responsible for different stages of the recruitment and hiring process, including posting job vacancies, screening resumes, conducting interviews, and making job offers. This segregation helps prevent bias or favoritism in hiring decisions and ensures that candidates are evaluated fairly based on their qualifications.
Payroll Processing: The payroll function, including calculating employee wages, processing payroll taxes, and issuing paychecks, should be segregated from other HR functions such as benefits administration or employee relations. This division helps prevent unauthorized changes to employee compensation or fraudulent payroll activities.
Employee Records Management: Individuals responsible for maintaining employee records, including personal information, employment history, and performance evaluations, should be separate from those responsible for making personnel decisions or handling disciplinary actions. This segregation ensures compliance with regulations and protects sensitive employee data security and privacy.
Example 7: Improving IT Asset Management with SoD
In context of IT asset management, Segregation of Duties policy plays a pivotal role in ensuring robust security and operational integrity. Let's delve into a hypothetical scenario to illustrate SoD's application in a company utilizing multiple SaaS applications.
Dividing Responsibilities: The IT team tasked with managing these assets undertakes various critical functions, including user access provisioning, application configuration, data backups, and system maintenance. SoD necessitates distributing these responsibilities among different team members to mitigate SoD risks such as fraud, risk of errors, or unauthorized or inappropriate actions.
For instance:
- User Access Administration: One team member assumes the role of user access administrator, overseeing access provisioning and revocation for SaaS applications.
- Application Configuration: Another team member focuses on application configuration, ensuring alignment with organizational requirements and optimizing software features.
- Data Backup Management: A separate team member is responsible for conducting regular data backups to safeguard against potential loss or corruption.
Ensuring Compliance and Efficiency: By delineating these responsibilities, each individual serves as a check and balance for others, reducing the likelihood of misuse or errors that could compromise asset integrity.
To effectively implement SoD, clear policies and procedures must be established, detailing the roles and responsibilities of each team member. Comprehensive documentation and communication are essential to prevent confusion and ensure seamless coordination.
Addressing Challenges: While SoD offers significant benefits, challenges such as balancing access and internal control activities must be addressed. Striking the right equilibrium between granting employees access to necessary resources and maintaining requisite checks and balances can be intricate.
Addressing these challenges demands a sophisticated approach to access management and comprehensive visibility into user interactions with SaaS applications. Yet, relying on outdated software and isolated Identity Governance and Administration (IGA) tools often prove insufficient in offering the requisite visibility across your SaaS landscape. This is precisely where Zluri’s IGA excels.
How Zluri’s IGA Solution Helps in Implementing Segregation of Duties Policy
Zluri's IGA platform simplifies SoD policy implementation for SaaS and AI environments. Govern access seamlessly with user provisioning, automated reviews, and self-service requests. Ensure compliance and security with 100% SaaS visibility and 300+ app integrations.
Discover & Govern Access with the Discovery Engine:
- Zluri simplifies data analysis and discovery for your IT team with nine robust methods: MDMs, IDPs & SSO, direct integration with apps, finance & expense management systems, CASBs, HRMS, directories, desktop agents (optional), and browser extension (optional).
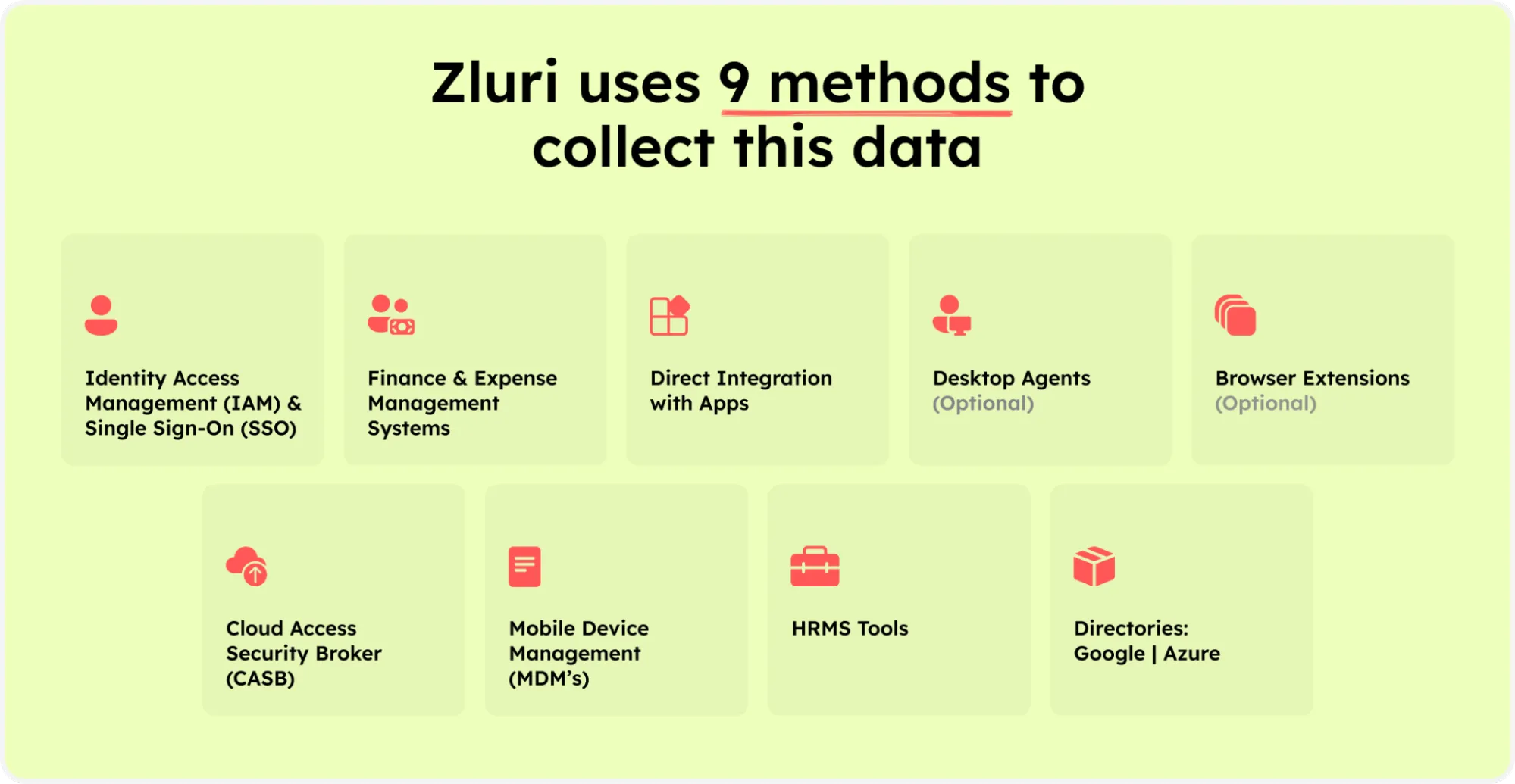
Zluri’s nine discovery methods
Zluri offers detailed access data for a comprehensive understanding of user permissions.
In fact, Zluri has been named in the Gartner® Report: Reduce Your IAM Attack Surface Using Visibility, Observability, and Remediation. Download now!
Gartner, Reduce Your IAM Attack Surface Using Visibility, Observability, and Remediation, Rebecca Archambault, 8 October 2025
Gartner is a trademark of Gartner, Inc. and/or its affiliates.
Gartner does not endorse any company, vendor, product or service depicted in its publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner publications consist of the opinions of Gartner’s business and technology insights organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this publication, including any warranties of merchantability or fitness for a particular purpose.
Streamlined Lifecycle Management with Automation Engine:
Zluri's automation engine functions as your organization's self-driving system, effortlessly managing access workflows with thorough reviews and adherence to policies.
Key Features:
- Lifecycle Management: Zluri's user lifecycle management (ULM) solution simplifies onboarding and offboarding processes, ensuring new employees have the right access from day one and minimizing security risks upon departure.
Onboarding
Offboarding
2. Customizable Workflows: Tailor workflows to meet SoD requirements, automating access management tasks based on user roles, departments, and seniority levels to maintain compliance.
App Recommendations & In-App Suggestions:Zluri offers contextual app recommendations and in-app suggestions, enhancing productivity while ensuring that access assignments align with SoD principles.
4. Reusable Playbooks: Predefined workflows, or \"playbooks,\" can be saved and reused to standardize access management processes, promoting efficiency and consistency in SoD compliance efforts.With Zluri's automation capabilities, your organization can efficiently manage access workflows while maintaining security and compliance.
Customizable Workflow & Access Request Management:
Zluri streamlines user access management during role transitions through its Employee App Store (EAS) self-serve model, empowering IT teams to oversee employees' access to vital tools and applications.

Key Features:
- Transparent Approval Process: The approval system, involving app owners, reporting managers, and IT admins, ensures transparency and accountability in access approval, a crucial aspect of SoD compliance.
- Hierarchy in Decision-Making: With different levels of authority, higher-level admins can override decisions made by lower-level managers, ensuring adherence to organizational SoD policies.
- Reasoning and Modification: Decision-makers can provide explanations for rejections and modify requests as needed, maintaining clarity and flexibility within the SoD framework.
- Changelog for Transparency: The changelog feature tracks updates related to access requests, including approvals, rejections, and comments, enhancing transparency and user awareness in SoD-compliant access management.
With Zluri's Access Request Management, organizations can efficiently govern access and safeguard sensitive information while empowering employees to request access aligned with their needs.
Continuous Access Reviews:
Zluri simplifies user access review and permission management through its centralized platform, facilitating easy parameter setting, reviewer selection, and campaign scheduling.
Key Features:
- Intelligent Automation: Zluri automates user access rights assessment based on predefined SoD rules, reducing errors and saving time compared to manual reviews.
- Auto-Remediation: Offers auto-remediation capabilities for SoD violations, taking immediate corrective actions to enhance security and ensure SoD compliance.
- Comprehensive Reporting: Generates detailed reports on access patterns, vulnerabilities, and SoD compliance status, facilitating demonstration to auditors and informed decision-making within the context of SoD requirements.
Unique Approaches:
- Continuous Access Reviews: Enables recurring and scheduled certifications to ensure consistent validation of access permissions and timely identification of SoD-related security weaknesses.
- Real-time Access Reviews:Leverages AI for real-time access reviews within the SoD framework, identifying unusual activities and potential security threats, allowing proactive mitigation to protect sensitive data within the confines of SoD principles.
- AI Compliance Capabilities: Provides intelligent insights and recommendations to align access controls with SoD requirements and industry regulations, simplifying SoD compliance processes.
Zluri's innovative approach to access reviews ensures continuous monitoring, real-time visibility, and streamlined compliance with SoD principles, helping organizations effectively meet regulatory requirements in this critical area of security and governance.
FAQS:
1. Why is SoD policy important in financial management?
SoD policy is crucial in financial management to ensure that no single user account has control over all aspects of financial statements. This helps mitigate the risk of fraud and ensures the accuracy and integrity of financial records.
2. What role does Role-Based Access Control (RBAC) play in SoD?
Role-Based Access Control is a method of restricting system access based on the roles of individual users within an organization. In the context of SoD, RBAC helps enforce the principle by limiting access to financial systems and data to only those individuals who require it to perform their designated duties, thereby reducing the risk of unauthorized access or misuse.
3. How does SoD address Financial Processes within an organization?
SoD plays a crucial role in financial processes by separating duties such as authorization, custody, and recording of financial transactions. This prevents any individual employee from having complete control over financial activities, reducing the risk of fraud or errors.
4. How does SoD relate to Employee Records?
SoD ensures that access to employee records, including sensitive information such as personal details and performance evaluations, is appropriately segregated. This helps prevent unauthorized access and ensures data privacy and compliance with regulations such as GDPR.







.png)

.svg)














