Triple-A identity access management standards are a set of rules that guide you on how to carry out or execute verification, authorization, and reviewing processes. In this article, we’ll discuss which specific guidelines are outlined under identity access management standards.
Before discussing the guidelines included in each identity access management standard, let’s first address a common question — ‘Why is it so important to follow triple A identity access management standards?’
Managing identity and their access is not as simple as it seems. Behind every login attempt and permission granted lies an intricate setup that requires careful coordination. What’s worse is that a slight oversight or one misstep can cause serious repercussions (such as leaving your data vulnerable to threats and disrupting the entire flow of business operations). Considering the risk and complexity involved in the process, the Identity Management Institute (IMI) introduced triple-A identity access management standards for guidance.
Now that you have the answer, let’s explore it further to gain a deeper understanding of triple-A identity access management standards.
Breakdown Of Triple-A Identity Access Management Standards
Below, we've explained what each 'A' in triple identity access management standards stands for and which specific guidelines they cover.
1: Authentication Standard
Authentication identity access management standards are a set of guidelines designed to securely authenticate an organization's digital identities (validating whether the digital identities are indeed who they claim to be). Basically, such standards aim to ensure only authorized personnel are given the 'entry pass' to access an organization's systems and apps while keeping intruders locked out for good.
Now you may ask — 'What specific guidelines are outlined in authentication identity access management standards?' Below, we've mentioned the 3 main guidelines that authentication standards cover.
Guideline 1: Assign A Unique Identifier To Every User Present Within Your Organization
To ensure your authentication process is free from inaccuracies and runs smoothly, you must assign a unique identifier (it can be anything, such as an employee ID, name, or email address, basically info that distinguishes one user from another) to every user working within your organization. But how is this actually helping?
When you assign unique identifiers to each user, you’re straightway adding distinct information about users in your database/active directories (that clearly differentiate one user from another).
Now, during the authentication process, your authentication system (identity provider aka IdP) can directly use this set of information (i.e., unique identifier) to quickly verify user identity. In fact, this eliminates the need for IdP to go through multiple databases to collect information and match the bits against each other to determine how one identity is different from another and whom to actually give permission to enter.
- Let’s suppose you have two employees named Alex, one from the sales department and the other from marketing. Now, without a unique identifier, your IdP might get totally confused while determining who is who and may grant the wrong Alex permission to access the marketing tools (we have assumed Alex from sales has mistakenly requested access to marketing tools).
You need to understand that the IdP is just a tool, not a human. It doesn’t have the ability to distinguish users based on different factors (until and unless it is configured to do so). It only goes through databases to improve its understanding (make sense of the information in records). Therefore, you cannot expect it to perform something so complex.
Rather, you can focus on eliminating the confusion by assigning each user a unique identifier. This way, your IdP won’t get confused and can accurately validate identities.
Guideline 2: Choose An Identity Provider That Can Seamlessly Integrate With Your Existing Applications & Directories
In the past, manual authentication was the norm, the go-to method for verifying identity. IT teams would collect user information, verify their information by asking each user questions (pre-set security questions), review their official documents, and then give them permission to log into the requested applications. However, with time, organizations realized that this approach was time-intensive and susceptible to errors, and even users had to wait for days to get their requests approved.
Realizing the inefficiencies of the manual approach, organizations switched to third-party identity providers to authenticate their users. Why did they switch? IdPs basically eliminate human involvement completely by integrating with organizations' existing applications and automatically collecting, reviewing, and validating users' identities. This not only speeds up the authentication process but also brings a level of accuracy that manual methods simply cannot match.
However, there have been incidents where organizations found their IdP was not performing as per their expectations. Why did this happen? Organizations have a common misconception: They believe any IdP will seamlessly work in their setup. That’s where they go wrong.
Various third-party IdPs are available in the market — Okta, AuthO, OpenID-Connect, and a few more- but not all will suit your setup. Why? Below, we’ve listed a few reasons:
- An IdP needs to connect with your app to validate users and allow them to log into the app. But if you have an application that the IdP doesn’t integrate with, then there won’t be any connection to support the authentication process (in simple words, verification of user identity won’t happen, and users won’t be able to log in to the apps).
- IdPs use different authentication protocols like SAML, Kerberos, OIDC, and a few more to communicate with service providers (applications). Now, if your application (SP) doesn’t support the protocols the IdP uses, then it won’t be able to receive the assertions (authentication token) sent by IdP. As a result, again, the IdP will fail to authenticate identities.
Also Read: What are the Generic Steps to Setup SAML?
Therefore, before selecting a third-party identity provider, you as an organization have to do a compatibility check — check if your preferred IdP integrates with your existing applications and directories and the protocol compatibility. This way, you will have an IdP that truly meets your expectations by helping streamline your authentication process.
Guideline 3: Leverage Multi-Factor Authentication or 2-Factor Authentication Mechanism
You need to understand that – cyber threats have leveled up. Malicious actors leverage advanced techniques to exploit user identities, steal them, and infiltrate secure systems. Therefore, simply relying on single-factor authentication methods wouldn't be sufficient to keep these attackers at bay. Why? Suppose an attacker successfully gets their hands on that single authentication factor, like the password of the user's account. In that case, they can gain access to your systems and apps straightaway without having to put much effort into them.
So, to counter such attacks, identity access management standards established guidelines that mandate organizations to implement either multi-factor or two-factor authentication methods (a combination of something you know, such as a password, something you have, such as a key fob, and something you are such as fingerprints also called as biometrics authentication). This practice basically adds an extra layer of security.
- For instance, even if a hacker somehow manages to steal a user’s password or any other credentials, they still have to bypass additional forms of verification, such as getting the unique code sent to the user’s device (which is nearly impossible to get), to finally enter a system. As a result, their attempt to breach your system will fail.
In a simple way, think of it as installing multiple locks on a door, each with its own unique key. Breaking through one lock is not enough; one needs to have a key to every lock. In short, this layered security approach creates a barrier between the unauthorized user or malicious actors and your organization’s critical assets.
Also Read: Types of Authentication Methods (Digital Authentication Methods)
2: Authorization Standard
Authorization identity access management standards are a set of guidelines that are designed to ensure only the required level of access permission (read-only, write-only, edit/delete, admin level permission) is granted to users and nothing beyond.
Note that authorization identity access management standards are only applicable after authentication. Basically, when a user successfully logs into an application (authentication completed), authorization identity access management standards come into play—they define what users can actually do within the application.
For instance, if a user only needs to read data stored in the app, that’s all they’ll be able to do. If they need to write or modify data, then that’s the level of permission they’ll be granted. For those in charge, they may have administrative rights to manage users and data, but even this is tightly controlled.
By enforcing strict permission rules, such identity access management standards help prevent unauthorized users from accessing and tampering with data (intentionally or unintentionally). In fact, even if an attacker gets hold of a user’s account, their ability to cause damage is restricted due to the limited permissions the user account holds.
Now let’s look at — ‘What specific guidelines are outlined in authorization standards?’
Guideline 1: Enforce Role Based Access Control (RBAC)
Previously, organizations used to grant their digital identities (users) full access rights (that means users can perform any action within the application). They generally preferred this approach because it seemed convenient. Their IT teams didn't have to constantly adjust access permissions every time a user’s role, department, or position changed. However, this convenience turned into a security blind spot, opening doors to multiple issues such as accidental data deletions, unauthorized data modifications, and frequent breaches.
Recognizing the risks of this approach, authorization identity access management standards included a rule mandating organizations to implement role-based access control across their applications. By implementing role-based access control, organizations can ensure that their users are only granted the right level of access to applications relevant to their role.
This way, users cannot access apps that are not required for their role and cannot perform actions that their role is not authorized to do, which further helps keep data secure from accidental modification, deletion, or security breaches.
Guideline 2: Enforce the Principle Of Least Privilege (PoLP)
To further impose more restrictions on what actions users can perform within an application, authorization identity access management standards established another rule, i.e., to enforce the principle of least privilege (PoLP). This access control helps ensure users are given the least level of access privileges — just enough permission to perform tasks without any issues. The idea behind restricting access rights to the bare minimum is to minimize the potential damage a user or attacker can cause (as they won’t be holding more access than needed, and eventually, they won’t be able to perform actions that can hamper data security).
Now, you will probably ask, ‘How will all these actually work? How will one apply these rules and when to apply them?’ To clear your confusion, below, we’ve explained the process step-by-step.
Also Read: 6 Ways To Implement Least Privilege with Identity Governance
Step 1: Before activating the authentication setup, you first have to implement the access controls, and to do so – you can follow one of the below methods:
- Method 1: You can use Access Control Lists (ACL), which are built-in features in applications. Most operating systems and database management systems also support ACLs. How does it work? You just have to specify the rule (e.g., if you want to grant access based on role, you can specify that) in the access control list, and the system or application will automatically follow the rule and perform the actions.
- Method 2: Or you can opt for an access management solution like Zluri. Zluri’s access management solution provides you with an automated rule workflow in which you can directly specify the rule/access control you want to enforce, and the system automatically implements it across all the applications. To provide you with more clarity about how it actually works, below we’ve given an example:
Note: With the help of Zluri’s access management solution, you can enforce multiple access controls (there are no restrictions), such as RBAC, PoLP, ABAC, JIT, CBAC, and a few others.
Suppose you’re setting up role-based access control and only want financial admins to access apps like Expensify and Spendesk. So, what you can do is – specify these rules in Zluri’s automated workflow as below:
Once the configuration is completed, whenever users request app access to these apps, Zluri’s access management solution will automatically check the conditions —against the rules you’ve defined.
If the conditions are met, that means if the user requesting app access is a finance admin, access will instantly be granted (Zluri will notify the IdP that conditions are met). If the user doesn’t meet the conditions, Zluri’s access management solution will send this information to IdP (via integration), and the user’s access request will automatically be denied.
This way, you can ensure that only authorized users—those meeting your predefined access control rules—can access your critical applications, systems, and databases.
Step 2: Once you're done with the configuration part, the service provider (application) and identity provider (IdP) will take care of the rest.
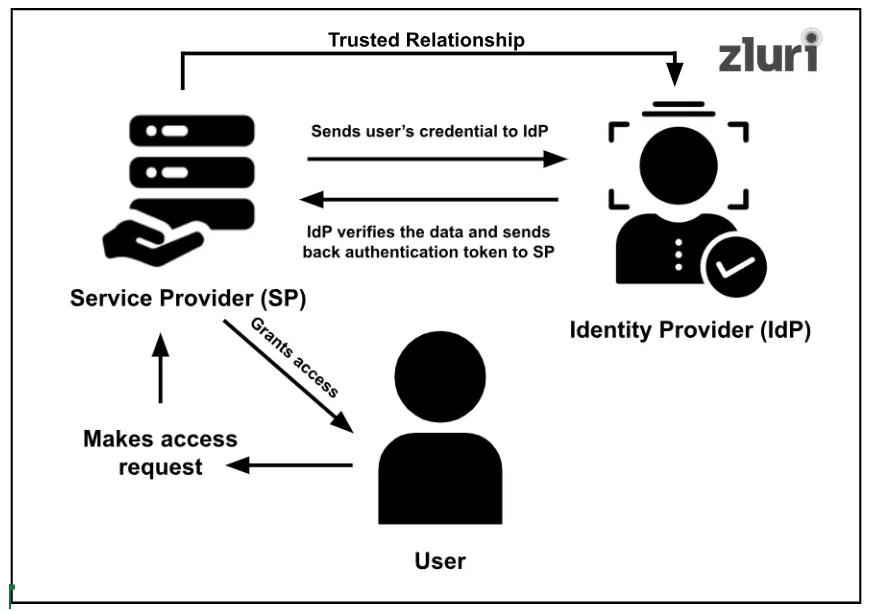
- When a user attempts to log in to an application using their credentials, the application (service provider) redirects the credentials to the identity provider for verification.
- Then, the IdP will validate the user's credentials (by integrating with the organization's directories and applications).
Note: we’ve assumed you have configured IdP to follow the access control rules
- Once successfully verified, the IdP will send a SAML assertion back to the application (service provider). This assertion contains the authentication token and the user's key details, such as user identity (e.g., username) and what access permission is suitable for them.
Note: If a user enters the wrong credentials, IdP will notify SP that the user is not a legitimate user (not an authorized personal), and the user's request to log in will immediately be denied.
- After that, the service provider will review the SAML assertion and will give the user entry along with the access permission (that you have configured in the above step).
Note: All of this happens within a fraction of a minute—basically, it happens quite fast. Therefore, the waiting period is completely eliminated, giving users secure access to apps right away.
Also Read: Authentication Vs Authorization: 5 Key Differences
3: Accounting Standard (Also Known As Auditing Standard)
Accounting or auditing identity access management standards are a set of guidelines designed to check whether an organization's digital identities hold the right level of access permissions. The main purpose of introducing such identity access management standards is to detect access misalignments or discrepancies that can lead to access gaps or, worse, data breaches.
How will this help? By identifying these anomalies early on, IT teams can take timely preventive measures (such as revoking or modifying access) and resolve them before they escalate and turn into a major issue.
Now, you might ask, 'Why do we need another set of identity access management standards? Wouldn't authentication and authorization identity access management standards be enough to protect us from threats and unauthorized access?'
It's a valid question, but you must understand that authentication and authorization identity access management standards act as a first-line defense. They establish rules regarding who can enter and what they can do. However, these measures, let alone won't suffice. Why?
Users undergo mid-lifecycle changes (role, department, position changes), so they generally no longer require access to apps they once did. If those outdated permissions aren't revoked and remain with the user, they might pose a significant risk (these permissions could be misused, either intentionally by the user or by hackers who target the account to escalate access).
Therefore, there is a need for standards like auditing guidelines (because authentication and authorization standards don't cover this aspect) that can help detect these outdated permissions in a timely manner so that IT teams can fix them immediately.
Now let's look at — 'What specific guidelines are outlined in authorization standards?'
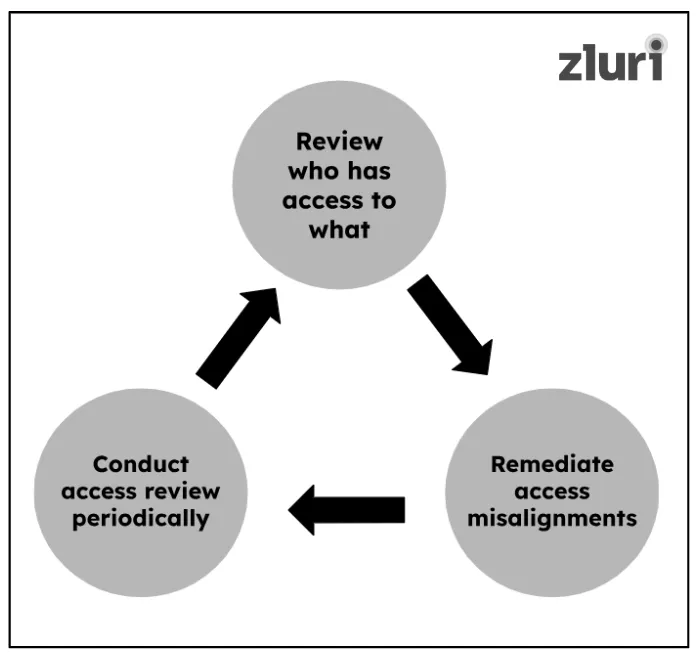
Guideline 1: Review The Access Permissions Users Currently Hold
To adhere to this guideline, your IT teams have to thoroughly review which users are currently holding access to which apps to determine whether those accesses align with their roles. Their focus should be on identifying access misalignments (users holding excessive or outdated permissions).
Guideline 2: Remediate Access Misalignments As Soon As They Are Detected
Another guideline that auditing identity access management standards includes is remediating access misalignments without delay. Whenever discrepancies are spotted, IT teams have to immediately take action. Either they can revoke unnecessary permissions or adjust access to match the user's current role. Basically, remediation action should be performed without any delay to ensure security is never compromised.
Guideline 3: Conduct User Access Review Regularly
To ensure user access permissions align with their roles and responsibilities throughout their tenure, you as an IT team must conduct user access reviews on a periodic basis (quarterly, bi-annually, or annually). This practice will help ensure that permissions stay up-to-date (align with users' current roles) and help close potential gaps that can jeopardize data security.
However, conducting access reviews manually can be externally time-intensive and prone to error. Why? IT teams first have to gather data regarding who has access to which apps and what permissions they hold, and then they have to create spreadsheets to record this data. After that, they have to go through multiple screens back and forth to review each user.
Rather than going through this hassle, opting for Zluri's access review solution will be more feasible. It conducts an in-depth review of your users' access and auto-remediates when any excessive privileges or unwanted access rights are detected (any sort of anomalies).
To trigger this action, your IT team simply needs to specify a few details regarding which SaaS apps and user types need to be reviewed and what actions you prefer to perform in case any anomalies are identified (like revoking or modifying the user access).
Based on the details you've defined, Zluri's access review automatically runs the access review and remediates access permissions when misalignments are detected without any manual intervention. What's more is, it even generates a detailed UAR report outlining its actions, so that you can check whether it has performed all the actions correctly or not.
To gain more clarity on how Zluri conducts reviews, check out its access review tour.
Role Of Triple-A Identity Access Management Standard In Meeting CIA Triad
There is an interesting fact about triple-A identity access management standards: These standards go beyond helping safeguard your app and data from intruders or unauthorized users. They even, in fact, help meet the CIA Triad – a framework that mandates adhering to three core principles: confidentiality, integrity, and availability.
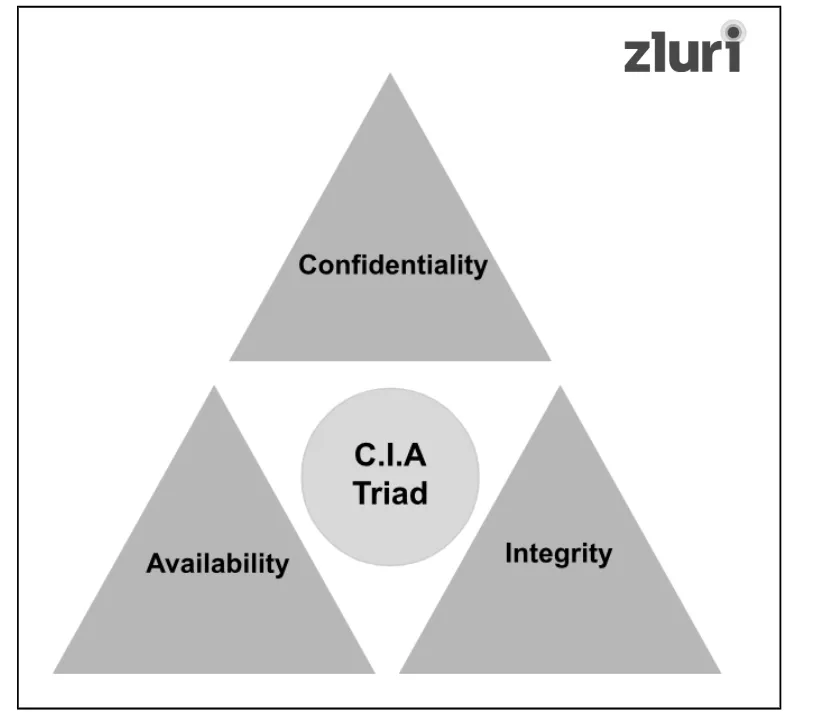
But how will triple A identity access management standards help meet them? Here’s how:
- Triple A Identity Access Management Standards Role In Meeting CIA Triad’s Confidentiality Principle
Triple A identity access management protects confidential data such as PHI, financial records, legal documents, and other critical datasets mentioned in non-disclosure agreements (NDAs) from accidental disclosure — by implementing strict access control.
This practice helps ensure that confidential data (stored in apps) access is restricted to only authorized users (along with that, these users will have only required permissions and nothing beyond) and no one else, which further prevents accidental data disclosure or data tampering.
- Triple A Identity Access Management Standards Role In Meeting CIA Triad’s Integrity Principle
Triple A identity access management standards help meet processing integrity — by ensuring the IdP you have chosen integrates with your SPs and directories. This seamless setup allows both parties to communicate and exchange user data without any interruption and carry out the authentication and authorization procedure properly (without any delay).
It also prevents data tampering or manipulation (like omission of data) during transit (while the data is in the processing line) by encrypting them (like IdP sends SAML assertion that only the SP can decrypt).
- Triple A Identity Access Management Standards Role In Meeting CIA Triad’s Availability Principle
Triple A identity access management standards meet the availability principle by ensuring the user’s data is always up-to-date and readily available for authentication and authorization purposes (when needed).
For example, these standards outline rules that mandate organizations to update their directories or identity repositories regularly. This means that if any change is made to user roles, permissions, or status, it should be directly reflected in the directories so that IdPs and SPs can use the latest user information during the authentication and authorization procedure.
In short, by implementing identity access management standards you are not only ticking off security requirements but also building a strong foundation to meet other necessary requirements like confidentiality, integrity, and availability principles. So, why wait? Implement these triple A identity access management standards and open doors to new possibilities.
Frequently Asked Questions (FAQs)
1. Which Principle Does Authentication Identity Access Management Standards Adheres To?
Authentication identity access management standards adhere to the zero—trust principle, i.e., ‘never trust, always verify.’
2. How do Triple A Identity Access Management Standards help comply with regulatory compliance?
Triple A identity access management standards help organizations implement strategies to secure sensitive data. This practice helps them meet data security regulatory requirements set forth by most compliance regulations, such as GDPR, HIPAA, SOX, and a few more. Simply put, organizations successfully comply with regulatory compliance by meeting the security requirements.









.svg)














