An effective IGA tool is crucial for managing user identities, access rights, and permissions in an organization. However, with many IGA solutions on the market, IT managers must choose the right one. To make this choice easier, it's important to know the key features that make an IGA tool great.
Choosing the appropriate IGA tool is paramount if you’re seeking to optimize identity and access management strategies. A wrong choice can cause inefficiencies, security risks, and compliance breaches. Learn more about what IGA is here.
In contrast, a well-chosen IGA solution empowers your IT teams to ensure consistent access policies, automate user provisioning and deprovisioning, and minimize the risk of unauthorized access. Furthermore, it enables your team to maintain a comprehensive audit trail, facilitating compliance audits and reducing the burden on internal resources.
When evaluating IGA tools, it is crucial to consider their core features and functionalities. While the specific requirements may vary depending on the organization's industry and size, there are certain key features that IT managers should prioritize:
Essential Features of Identity Governance & Administration Tools
By considering the below key features and functionalities, you can make informed decisions when selecting an IGA tool that aligns with their specific needs and goals.
1. Comprehensive user access visibility: Gain insights into your SaaS landscape
In the realm of managing user access and permissions in your SaaS ecosystem, traditional methods like spreadsheets have proven to be challenging. These manual approaches often lead to errors, lack real-time updates, and fail to provide the holistic insights needed for well-informed decisions. This shortfall in accurate and timely data not only affects your ability to optimize costs and productivity but also exposes your organization to potential security risks.
Picture having a full grasp of every application and user access across your organization. Armed with this knowledge, you gain the potential to optimize costs, refine security measures, and boost overall productivity. The capacity to critically assess user access and permissions empower you to proactively tackle discrepancies and vulnerabilities.
Additionally, real-time data lets you spot redundant applications, consolidate licenses, and enhance vendor negotiations. The outcome? Remarkable cost savings that can be channeled into strategic initiatives, propelling business growth and innovation.
Now, envision a seamless solution that seamlessly aligns with your needs - An innovative identity governance and administration platform- Zluri.
It empowers your IT team to efficiently manage and safeguard user access. By leveraging Zluri's IGA, you unlock invaluable insights into your entire suite of SaaS applications through a centralized dashboard. This empowers you to ensure secure and authorized access to critical apps. With an array of robust features, Zluri enhances security and streamlines identity management for your organization.
But how does it help gain effortless access to the comprehensive insights you seek?
Discover the power of Zluri's data engine: Unleashing advanced discovery methods for enhanced identity governance
Zluri's data engine empowers your IT team with cutting-edge discovery methods, offering unparalleled insights into your SaaS app and user-related data. Your organization gains a holistic view of its application landscape through nine discovery methods, encompassingMDMs, IDPs & SSO, direct integration with apps, finance & expense management systems, CASBs, HRMS, directories, desktop agents (optional), and browser extension (optional).

Zluri’s nine discovery methods
By harnessing the potential of these discovery methods, your team can swiftly identify application access, pinpoint active users, scrutinize permissions granted, and even recognize critical users accessing the apps. The detailed granularity provided by Zluri's data engine offers invaluable insights, reinforcing your organization's security stance and enhancing compliance endeavors.
Bid farewell to laborious manual app categorization and user access tracking. Zluri's data engine elevates automation to new levels, seamlessly identifying managed, unmanaged, and shadow IT apps. This automation empowers your IT team to save time and resources, unveiling a more efficient approach to managing your app ecosystem.
Security is paramount, and Zluri makes it effortless for your IT team to uphold a secure access environment. With its intelligent IGA solution, you can ensure that the right employees have appropriate permissions for service accounts, effectively eliminating the risk of unauthorized access.
2.Automated access management: Streamline user access workflows for efficiency
Manually managing access rights for an ever-expanding array of users and resources is fraught with challenges. The risk of human error leading to security vulnerabilities or access inconsistencies is a persistent concern. As an IT manager, you understand that addressing access control manually can strain your team's resources and potentially hinder your organization's productivity.
Instead of grappling with individual access requests and provisioning user rights by hand, an automated IGA solution offers a streamlined, efficient approach.
Automated IGA solutions, like Zluri, are designed to manage access workflows with precision and speed. By automating access requests, approvals, and provisioning, your IT team can reallocate their efforts toward strategic initiatives that drive value. This shift not only increases productivity but also empowers your team to focus on projects that contribute directly to your organization's growth.
Enhance access & user lifecycle management with Zluri's streamlined automation engine
Through Zluri's user onboarding and lifecycle management, your IT teams can efficiently grant and revoke access rights as needed, enabling seamless onboarding and offboarding processes for employees and contractors. This saves valuable time and significantly reduces the risk of unauthorized access or lingering permissions.
Simplified User Access Provisioning with Zluri: Empowering IT Productivity and Enhanced Security
Efficient user access provisioning is critical to maintaining security and productivity. Zluri presents a groundbreaking solution that revolutionizes the onboarding process, streamlining it to perfection and liberating your IT team from repetitive and time-consuming tasks.
Zluri ensures that only authorized employees receive precisely the right level of access to essential SaaS applications and data, reducing the risk of human errors and over-provisioning that can lead to security vulnerabilities.
Empowering your IT team is at the core of Zluri's mission. With an intuitive interface, your IT professionals can effortlessly create and customize onboarding workflows, tailored to the specific job entitlements, roles, positions, and departments of each new employee. This newfound efficiency allows your team to grant secure access to multiple new hires simultaneously, efficiently and securely.
Gone are the days of complicated workflow design. Zluri's user-friendly interface allows your IT team to configure access privileges based on job roles and responsibilities with just a few clicks. Witness a remarkable increase in efficiency and enhanced employee productivity as the powerful workflow capabilities of Zluri come into play, ensuring the right access for the right users while maintaining the utmost security for your SaaS app data.
To streamline the onboarding process using Zluri, follow these straightforward steps:
Step 1: Access Zluri's workflow module and choose \"Onboarding\" from the dropdown menu. Click on \"New Workflow\" to begin creating your onboarding process.
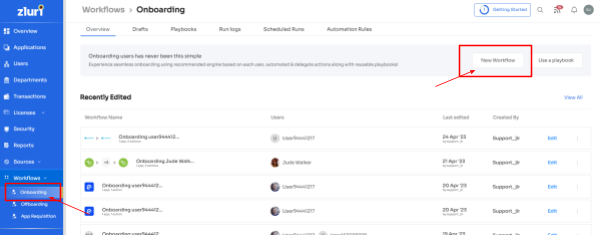
Step 2: Easily select the user(s) you want to onboard by using the search bar or manual selection. Click \"Continue\" to proceed.
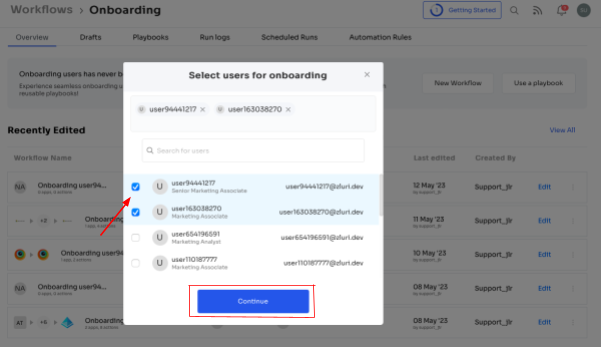
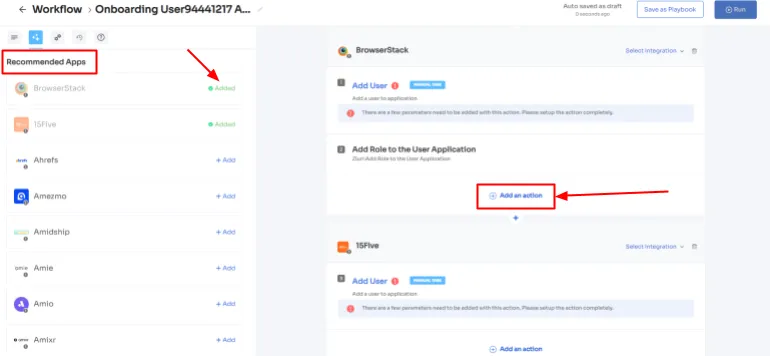
Step 3: On the left side, explore the recommended apps and select the necessary ones for the user. Tailor the onboarding process by defining desired actions for each application.

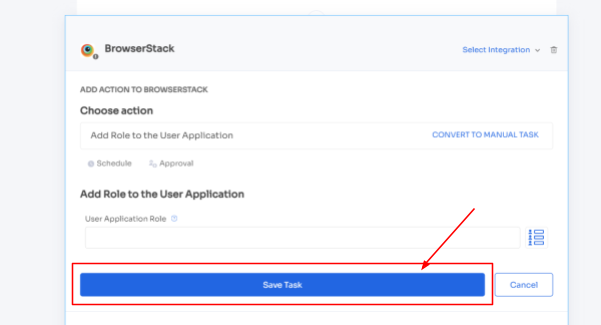
Step 4: Customize actions by selecting \"Edit Action\" and providing required details. You can even schedule these actions to be executed on the day of onboarding. Once finalized, save the actions by clicking \"Save Task.\"
Step 5: To ensure future efficiency, preserve the workflow by selecting \"Save as Playbook.\" Name your playbook in the prompted dialogue box and click \"Save Playbook.\" Your onboarding workflow is now ready to be utilized.
Note: Zluri's exceptional reusability and flexibility through playbooks empower you to create a streamlined onboarding process that fosters consistency across your entire organization. By harnessing Zluri's playbooks, you establish a strong foundation for effective onboarding, fostering a sense of belonging and engagement among new employees from day one.
Ultimately, this contributes to higher productivity, reduced turnover, and a more cohesive and successful work environment.
Effortless User Access deprovisioning with Zluri: Empowering IT Productivity and Enhanced Security
Deprovisioning employees when they leave an organization can be complex and time-consuming. However, Zluri offers a comprehensive solution through its onboarding playbook, streamlining the entire process and making it effortless and highly efficient. With Zluri's intelligent lifecycle management solution, you can save valuable time and effort while ensuring the security of your organization's data.
One of the key benefits of using Zluri is its automatic revocation of access to all devices, apps, and systems. When an employee departs, Zluri promptly disables their access, preventing any unauthorized entry to sensitive information. This ensures former employees cannot access company resources, reducing the risk of data breaches or security incidents.
Moreover, Zluri takes care of data backup and transfer to a new owner, mitigating the risk of losing essential data during deprovisioning. This feature ensures that critical information is securely handed over to the appropriate personnel, enabling a smooth transition even after an employee's departure.
In addition to data protection, Zluri simplifies employee license revocation and eliminates single sign-on (SSO) access. By doing so, the platform effectively blocks the ex-employee's usage of any organization's applications, further ensuring data security and preventing potential misuse of company resources.
By adopting Zluri's straightforward approach to employee offboarding, organizations can ensure consistent and secure deprovisioning for all departing employees. This level of efficiency and security allows HR and IT teams to handle departures easily and confidently, reducing the burden of administrative tasks and providing peace of mind during potentially sensitive situations.
Now, to streamline the offboarding process with Zluri, follow these straightforward steps:
Step 1: Access Zluri's user-friendly main interface and head to the workflow module. Simply choose the \"offboarding\" option from the drop-down list, and click on \"New Workflow\" to begin.
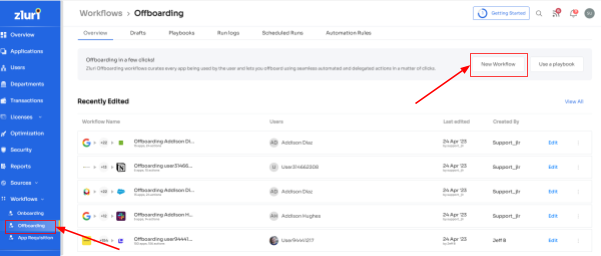
Step 2: Choose the user(s) you wish to offboard by selecting \"Select the user for offboarding.\" Once you've made your selection, click \"Continue.\"

Step 3: Zluri provides recommended actions tailored to specific apps. Effortlessly choose from a range of suggested actions and execute them across the selected applications.
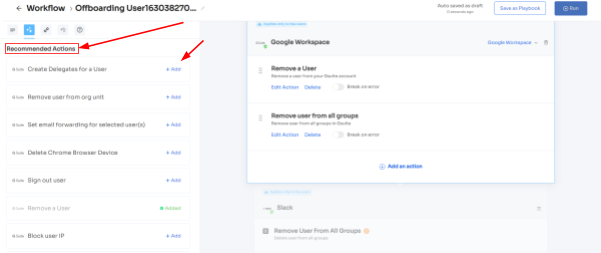
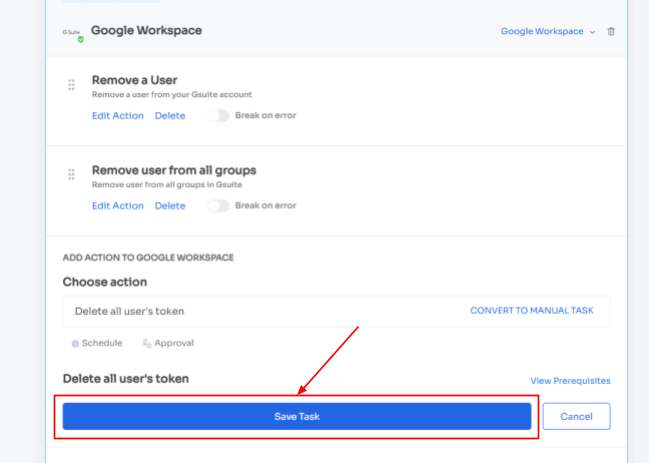
Step 4: To include additional actions, click \"Add an Action.\" Fill in the necessary details and save the task by clicking \"Save Task.\".
Step 5: Finalize the workflow by saving it as a playbook. Provide a name, click \"Save Playbook,\" your offboarding workflow is now set and ready to go.

Note: Unleash the full potential of Zluri's playbooks, empowering you to design
custom workflows with actions based on specific triggers and conditions. Tailor automation precisely to your organization's unique requirements and processes, with limitless possibilities.
Through this automation, your deprovisioning processes will be supercharged, guaranteeing swift and accurate access revoking for a seamless offboarding experience.
3. Self-service capabilities: Empower users with self-serve ad-hoc access requests
Access requests and approvals are integral to identity governance. An intuitive user portal provided by an IGA tool enables users to request access to various applications, systems, or resources based on their roles or job requirements. This self-service capability can empower users by allowing them to directly initiate access requests directly, eliminating the need for manual intervention.
The user-friendly portal can provide a clear and streamlined interface, making it easy for users to understand and navigate through the access request process. Simultaneously, the portal simplifies admins' approval workflow, ensuring quick and efficient access provisioning.
Ensuring effortless access request management with Zluri’s EAS:
One size does not fit all when it comes to access request management. Zluri offers a personalized user experience tailored to individual roles and attributes. This personalized approach simplifies the access request process, minimizing complexity and ensuring that users only have access to what's relevant to their roles. This not only enhances user efficiency but also reduces errors and fosters a greater sense of satisfaction with the identity governance solution.
Ensuring that employees have the right level of access to perform their new responsibilities while safeguarding sensitive data from unauthorized access is of utmost importance. Fortunately, Zluri's revolutionary self-serve model, the Employee App Store (EAS), is here to simplify access request management, making the process efficient and secure.

No more manual processes for managing permissions. With Zluri's EAS, both your team members and approvers can seamlessly review and approve access requests, tailored to the specific job roles of employees. This level of granularity ensures that employees have precisely the access they need to carry out their duties effectively while preventing unnecessary access to sensitive information.
Zluri empowers you with unparalleled control over access privileges, providing a secure environment within your organization's boundaries. With cutting-edge technology at your fingertips, you can effortlessly safeguard critical data, mitigating the risk of unauthorized access and maintaining full control over the tools and resources accessible to employees.

The EAS operates on a robust approval system, involving three distinct levels: app owners, reporting managers, and IT admins. This multi-tiered approach allows higher authorities to override decisions made by lower-level admins or managers, facilitating swift and decisive action when required.
Approvals and rejections of access requests are accompanied by comprehensive explanations and comments, ensuring that employees understand the reasoning behind each decision. This fosters collaboration and clarity within the organization's access management process.
That's not all! Zluri's intelligent solutions enable approvers to modify specific access requests, tailoring permissions precisely to the organization's unique requirements. Keeping stakeholders informed is vital, which is why Zluri's IGA solutions offer a comprehensive \"changelog\" feature. This feature allows users to track updates, from approvals and rejections to license duration or tier changes.
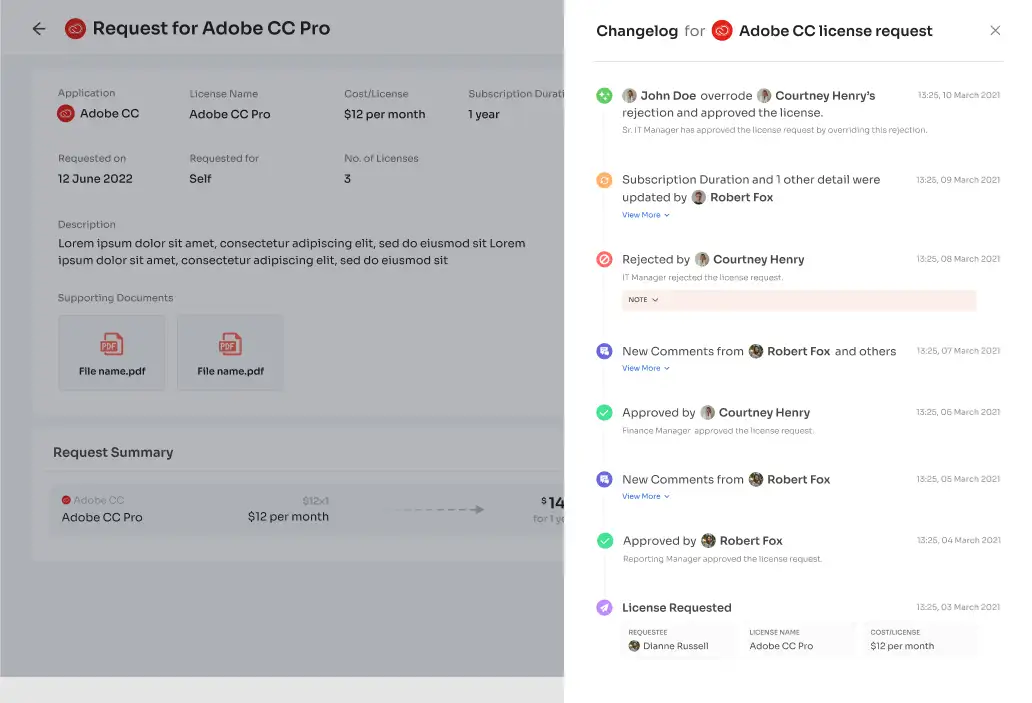
Furthermore, the changelog captures valuable insights, including comments added by any admin, promoting a collaborative and well-informed approach to access management. With Zluri's EAS, managing access requests has never been more efficient, transparent, and secure, allowing your team to navigate employee transitions with confidence.
4. Automated user access reviews: Proactive user access review for compliance
An IGA tool with access certification capabilities is vital for ensuring proper access management and security within an organization's IT infrastructure. Your IT teams can regularly review and verify user access rights across different systems and applications by implementing access certification. This process guarantees that users have the appropriate access privileges and identifies any excessive or inappropriate access that might have been granted over time.
The IGA tool must facilitate access review workflows involving relevant stakeholders, such as CIOs and data owners, in the certification process. This collaboration helps identify and mitigate instances of excessive or inappropriate access privileges, reducing the risk of unauthorized access and potential security breaches.
Moreover, the IGA tool should streamline the review process and ensure that user access aligns with the principle of least privilege. Following this principle, users are granted the minimum necessary access to perform their job roles effectively, thereby enhancing security and minimizing the attack surface.
How Zluri’s IGA revolutionizes access certifications:
Recognizing the value of time in the corporate landscape, Zluri's IGA solution takes a groundbreaking approach to access reviews by harnessing the power of automation. What was once a time-consuming and burdensome process is now streamlined, enabling admins to focus on mission-critical tasks.
With Zluri's IGA solution handling the bulk of the review process, you experience a remarkable tenfold increase in review efficiency, bidding farewell to tedious manual reviews and welcoming lightning-fast access assessments.
By leveraging Zluri's IGA, your team can experience a remarkable tenfold increase in review efficiency, bidding farewell to manual reviews and welcoming swift access assessments.
Unified Access: A Comprehensive View of Digital Identities
Zluri's IGA solution offers a unified access management approach, providing a complete view of an organization's access landscape. It consolidates user access-related information from various sources into an intuitive platform, eliminating the need for juggling multiple directories or identity repositories. Everything needed to understand access privileges and user activity is now easily accessible, promoting a seamless user experience.
- Access Directory: At the core of Zluri's IGA lies its robust capability to capture and organize user information from diverse sources. The platform ensures every user identity and associated access privileges are meticulously recorded and easily accessible for review, leaving no room for incomplete or inaccurate records.
- Access Privileges: With Zluri's unified access, administrators gain unparalleled visibility into managing user access privileges across the entire organization. This enhanced oversight enables swift identification of potential access discrepancies or suspicious permissions, bolstering the defense against cyber threats and ensuring constant alignment of access rights.
- Activity & Alerts: Zluri's IGA solution adopts a proactive approach to security by tracking user activity in real-time and triggering instant alerts for anomalous behavior or unauthorized access attempts. This vigilant alert system acts as an early warning mechanism, empowering you to respond promptly to security risks.
Automated Reviews: Unleashing the Power of Automation
Manual access review processes have long hindered productivity and security. However, with Zluri's IGA solution, a game-changing approach emerges, powered by cutting-edge automated review capabilities.
By seamlessly integrating automation into access management, Zluri's IGA empowers your organization to operate with greater efficiency, minimizing human errors, and fortifying security measures.
- Access Rules: With Zluri's IGA, you gain complete control over access rules and policies, tailoring them based on roles, responsibilities, and specific business requirements. Automation plays a crucial role here, enabling the platform to perform instant reviews and validations of user access against pre-established criteria.
This eliminates any ambiguity in the review process, ensuring that access is granted only to authorized personnel, bolstering security and reducing the risk of unauthorized access.
- Scheduled Certification: The forward-thinking scheduling feature introduced by Zluri's IGA automates system-generated reviews at regular intervals. This proactive approach ensures that access rights remain up-to-date, aligning with evolving security policies and best practices. By conducting periodic certifications, you can maintain a consistent and compliant access environment, reducing the potential for security gaps.
- Auto Remediation: In the face of security vulnerabilities, Zluri's IGA solution shines with its efficient automated remediation actions. Whether it's revoking access, notifying users and managers, or initiating access request workflows for approvals, the platform enables organizations to respond swiftly to security threats.
By automating these remediation actions, potential security risks are mitigated promptly, reinforcing the organization's security posture and maintaining a proactive defense against cyber threats.
The synergy of automation with access reviews significantly streamlines the entire process, freeing up valuable time and resources that can be redirected to more critical tasks. By reducing manual intervention, Zluri's IGA minimizes the likelihood of human errors, ensuring access reviews are conducted accurately and consistently.
Moreover, the automated approach empowers you to maintain a high level of security resilience. The proactive nature of scheduled certifications ensures that access permissions are continuously reviewed, helping organizations stay ahead of potential security risks and compliance issues.
- Here’s how you can automate user access reviews. Zluri’s ‘Access certification’ module has got you covered:
- Step 1: To automate access reviews, access Zluri's main interface and navigate to the \"Access certification\" module. Within the module, select the option to create a ‘new certification.’
- Step 2: Assign a name to the certification and designate an owner who will oversee the automated access reviews.

- Step 3: Choose the preferred method of reviewing user access by exploring the options: Application, Users, and Groups.
- Step 4: Opt for the \"Application\" review method if desired and add the relevant application(s) to be audited for users' access.
- Step 5: Select a primary reviewer and a fallback reviewer from the dropdown menu for the automated access reviews.
- Step 6: Select the users to be included in the automated access reviews process and apply data filtering to refine the user selection based on certification requirements.

- Step 7: Proceed to the next step and configure the actions to be performed during the automated access reviews, choosing from the provided dropdown list of actions.|Note: If there are multiple applications to be included in the same certification, repeat the process of adding applications as needed.

- Step 8: Specify the start and end dates for the automated access certification process, ensuring they align with recurring or scheduled certifications.
- Step 9: Save the configuration as a template for future use by clicking on the \"Save Template\" option.
- Step 10: Monitor the progress and updates of the automated access review process for the specific certification by regularly checking the \"Review Stage\" section.
With the implementation of Zluri's IGA solution, the access review burden is significantly reduced through the power of automation. The platform streamlines the access review process, automating key tasks and simplifying the overall workflow. As a result, your team can experience a remarkable 70% reduction in manual efforts related to access reviews.
5. Robust reporting capabilities: Comprehensive audit reports & data insights
Picture this: A comprehensive suite of audit reports and data insights at your fingertips, empowering you with unparalleled visibility into user access across systems and data repositories. As you lead your IT security efforts, these reports act as your navigational compass, guiding you through the intricate waters of access management.
Consider the advantage of pinpointing who holds the keys to sensitive systems and crucial data. With this granular understanding, you are poised to swiftly detect anomalies and thwart unauthorized access attempts. Early intervention in the face of potential security risks becomes not just possible, but a tangible reality.
However, the value of these reports extends far beyond the confines of your IT department. Management and auditors find a goldmine of insights within these meticulously crafted documents. They are granted a panoramic view of your organization's access policies, which serves as a blueprint for understanding the intricacies of access control.
Data-driven decision-making takes center stage as these reports furnish quantifiable evidence of access control efficacy. Are your security objectives being met? Are compliance standards being upheld? The reports unravel the answers, allowing decision-makers to fine-tune access policies, optimize processes, and allocate resources judiciously.
Central to Zluri's capabilities is its ability to generate comprehensive audit reports that transcend mere documentation, evolving into a source of invaluable insights. These reports, meticulously curated, unfurl access patterns, vulnerabilities, and the very status of compliance within your organization. Imagine the power to visualize user access at its most granular level, a key that unlocks the door to preemptive action against security threats.
In the dynamic sphere of audits, where transparency is paramount, Zluri's reports prove to be your staunch allies. Demonstrating compliance to auditors becomes an exercise in ease, as these reports paint an accurate and compelling picture of your access management strategy. These are not just reports; they are the manifestation of your commitment to adherence and diligence.

However, Zluri goes beyond just providing insights. It smoothly turns insights into action with its unique access certification feature. Picture being able to start a review where assigned reviewers can approve, reject, or adjust access rights. Once the review is done and the reviewer agrees, a single click finishes the process.
And there you have it! Detailed audit reports are immediately sent by email, promoting transparency and responsibility throughout your organization.
Imagine the possibilities when your team is no longer bogged down by tedious, repetitive tasks. With Zluri's IGA taking care of the bulk of the review process, your workforce can redirect their valuable time and talents to more strategic initiatives. Freed from the administrative burden, they can focus on high-impact projects that drive your organization forward, contributing to growth, innovation, and enhanced customer experiences.
Book a demo now and experience it yourself!









.svg)



.svg)
.svg)
.svg)
.svg)

.svg)

.svg)

.svg)
















.webp)







.webp)
.webp)





.webp)