Segregation of Duties (SoD) stands as a crucial imperative for IT managers committed to fostering a secure and efficient workplace. This practice, pivotal for bolstering security through task distribution among team members, brings forth diverse Segregation of Duties risks, including insider collusion and increased administrative workload.
Segregation of duties (SoD) has emerged as a crucial practice for organizations, especially those striving to maintain compliance with regulations like the Sarbanes-Oxley Act (SOX). This regulation made it necessary for companies to comply with SoD across various information security standards and regulations.
Failing to adhere to SoD rules can expose your organization to segregation of duties risks, leading to monetary fines and negative audit findings. As technology and financial reporting became more intertwined, audits now focus on limiting users' access to only what is necessary (known as "least privilege") and enforcing SoD policies to prevent conflicts of interest.
For instance, employees who can grant and modify system access permissions in an IT department should not have access to financial systems. Similarly, another IT team member ensures that the person responsible for setting up firewall controls cannot approve those changes. These measures help you maintain a secure and compliant environment in your organization.
Moreover, SoD also acts as a safeguard against errors and unintentional mistakes. When more than one person is involved in critical processes, the likelihood of catching errors increases significantly. A team-based approach ensures that one person's oversight can be compensated by another, leading to enhanced data handling and decision-making accuracy.
What is Segregation of Duties (SoD)?
Segregation of duties (SOD) is a principle in organizational management and internal control that involves dividing tasks and responsibilities among different individuals or departments to prevent conflicts of interest and reduce the risk of error or fraud. The key idea is to create a system of checks and balances by distributing critical functions across multiple people or teams.
The four main categories in which duties are typically segregated are:
- Authorization: The process of approving or granting permission for certain actions. This involves making decisions and setting policies.
- Custody: The physical control and handling of assets, such as cash, inventory, or sensitive information. This role involves safeguarding and protecting the assets.
- Record-keeping: The responsibility for documenting and maintaining accurate records of transactions, activities, or information. This helps ensure transparency and accountability.
- Reconciliation: The comparison and verification of different sets of records to ensure they are accurate and in agreement. This involves checking and balancing to identify discrepancies.
By separating these functions, an organization can create a system of internal controls that makes it more difficult for individuals to engage in unauthorized activities or make errors without detection. This helps safeguard the organization's assets, ensure accuracy in financial reporting, and maintain compliance with regulations.
Segregation of duties can prevent situations where a single individual could have too much influence or control over a particular process, reducing the risk of both intentional and unintentional errors. It is a fundamental component of a robust internal control framework and is often a compliance requirement with various regulations and standards.
Benefits of Segregation of Duties (SoD)
Segregation of Duties controls is crucial for effectively managing and protecting an organization's assets, particularly in the financial and accounting departments. Here are some benefits of implementing SoD:
- Enhanced Fraud Prevention
SoD mitigates the risk of fraud by ensuring that critical financial tasks are divided among different individuals. When one person oversees both the creation and approval of financial transactions, it creates an opportunity for fraudulent activities.
SoD establishes clear accountability, enabling the tracing of any discrepancies or fraudulent activities back to the person in charge or the responsible parties. This transparency is crucial for maintaining organizational integrity.
- Error Prevention and Accuracy
SoD's involvement of multiple individuals in financial processes enhances accuracy. Whether it's financial reporting or transaction recording, having two sets of eyes minimizes the likelihood of errors going unnoticed.
By reducing the chances of errors, SoD assists organizations in adhering to compliance standards, such as the Sarbanes-Oxley Act, avoiding costly violations.
- Effective Risk Mitigation
SoD protects organizational assets by distributing responsibilities. This ensures that no single individual has complete control over a process, minimizing the risk of misuse or mishandling of assets.
Beyond asset protection, SoD safeguards an organization's reputation. The public's trust in financial integrity is preserved through SoD's role in minimizing the risk of financial mismanagement.
- Conflict of Interest Avoidance
SoD aids in avoiding potential conflicts of interest by separating duties prone to compromise if handled by the same individual. For instance, preventing an employee from both hiring and determining compensation minimizes the risk of biased decision-making.
SoD promotes adherence to ethical standards, fostering transparency and integrity in decision-making processes.
- Compliance and Legal Safeguards
Adherence to SoD principles ensures organizations meet regulatory requirements and industry standards. This is particularly vital in highly regulated industries, where non-compliance can lead to severe legal consequences.
SoD serves as a legal safeguard, demonstrating to regulatory bodies and stakeholders that an organization has proactively implemented internal controls to prevent fraudulent activities.
Despite the numerous benefits of SoD, there are some associated risks that IT managers must be aware of. This blog post will walk you through the various potential conflicts and segregation of duties risks.
Risks Associated with Segregation of Duties (SoD)
There are Segregation of Duties risks associated with the implementation and maintenance of a proper Segregation of Duties framework.
Here are some of the key segregation of duties risks:
1. Risks Due to Mergers and Acquisitions
In mergers and acquisitions (M&A), the convergence of distinct organizational structures often introduces a complex amalgamation of processes, systems, and access controls. This intricate interplay can result in a labyrinth of permissions and responsibilities.
The inherent risk surfaces when individuals are endowed with excessive or overlapping privileges, potentially enabling them to undertake conflicting tasks or gain access to sensitive information beyond the scope of their roles. A glaring example is a person's dual capability to approve and execute financial transactions, a situation fraught with inherent risks.
In the aftermath of a merger or acquisition, a meticulous examination and reevaluation of access controls and user permissions across all systems become imperative. Neglecting this critical step may expose the organization to potential vulnerabilities, ranging from data breaches and financial fraud to inadvertent errors carrying substantial repercussions. The crux of maintaining the Segregation of Duties principle lies in ensuring that each employee's access rights are judiciously limited to tasks pertinent to their role.
The challenge lies in harmonizing and consolidating access control policies from both entities, ensuring alignment with the newly established structure while upholding the core of SoD. This intricate process necessitates a comprehensive audit of user roles, permissions, and responsibilities to identify and rectify potential conflicts or violations.
2. Risk of Compromised Independence in Segregation of Duties
A significant segregation of duties risk in SoD implementation is the potential for collusion among individuals, especially when oversight is lacking. This collaborative effort to override segregation controls can compromise the independence integral to the SoD framework, exposing the organization to heightened concentrations of risk.
When oversight is inadequate, individuals might collude by sharing access credentials or manipulating workflows, undermining the established segregation controls. This compromises the independence intended by the SoD framework, eroding its effectiveness in preventing a single point of failure or misconduct.
Collusion weakens SoD, leading to increased fraud risks, errors, or unauthorized access. The organization becomes susceptible to potential damage like financial losses, reputational damage, and legal consequences as compromised independence hampers internal controls.
To address this risk, organizations should focus on robust oversight through regular monitoring, an internal audit trail, and strict adherence to SoD policies and procedures. Cultivating a culture of transparency and accountability acts as a deterrent, reinforcing the importance of maintaining the independence embedded in the SoD framework.
3. Risks Due to Organizational Inefficiency
Segregation of Duties is vital for risk of fraud prevention and internal control, but its implementation can inadvertently jeopardize business efficiency. SoD introduces extra steps and approvals in workflows, slowing down business processes. The need for constant coordination and communication can create bottlenecks, causing project delays and hindering overall productivity.
Strict SoD may limit employee flexibility and impede cross-departmental collaboration. Restricting individuals to specific tasks without a comprehensive understanding hampers creativity and adaptability, impacting innovation and organizational agility.
In some instances, SoD may lead to a shortage of skilled personnel in critical areas. Limited authorization for specific tasks poses challenges if key individuals are unavailable or overwhelmed, resulting in project slowdowns and missed deadlines.
To address efficiency risks associated with SoD, striking a balance between security and operational effectiveness is essential. Regularly review processes, identify bottlenecks and consider leveraging Identity Governance and Administration (IGA) technology to streamline workflows, reducing administrative burdens and ensuring prompt permissions. This proactive approach helps maintain the security benefits of SoD while optimizing operational efficiency.
4. Risks of Implementation Costs in Segregation of Duties
Implementing and maintaining an effective SoD controls program requires investments in technology, training, and ongoing monitoring. This segregation of duties risk arises from the potential struggle organizations may face in managing costs, leading to insufficient resources allocated to the SoD initiative.
For a robust SoD program, organizations must invest in advanced technology for role-based access control activities, comprehensive employee training, and continuous monitoring tools.
However, a significant risk lies in financial constraints that may hinder the allocation of adequate resources. Limited funding can compromise the effectiveness of the SoD initiative, leaving critical areas vulnerable to security breaches or errors.
Mitigation Strategies: To address the Segregation of Duties risks related to implementation costs:
- Budget Planning: Develop a clear budget that allocates sufficient resources for technology upgrades, training, and monitoring. This ensures financial constraints do not undermine the SoD program.
- Prioritization: Focus resources on high-impact areas within the SoD framework. Prioritize critical aspects to optimize resource allocation effectively.
- Cost-Benefit Analysis: Justify the SoD program investment through a thorough cost-benefit analysis, emphasizing the risks and consequences of inadequate controls.
- Continuous Evaluation: Regularly assess the financial landscape and adjust the SoD budget as needed. This flexibility enables organizations to adapt to changing circumstances.
Addressing these risks proactively enhances the resilience and effectiveness of SoD programs, safeguarding critical business processes and data.
5. Risks Arising from Increased Complexity and Collaboration
Implementing Segregation of Duties raises concerns about increased administrative overhead and potential miscommunications. In a collaborative environment, involving multiple individuals in tasks can slow down processes, especially when coordination is needed across different departments or time zones.
Misunderstandings become more likely, leading to errors, rework, and wasted time. To mitigate these segregation of duties risks, as an IT manager, facilitating seamless collaboration among teams is crucial. This involves employing robust monitoring mechanisms and regular status updates to ensure accountability and identify potential risks early on.
Consider investing in technologies such as a centralized project management system to streamline collaboration and communication. This can aid in task assignment, progress tracking, and efficient documentation, ensuring everyone has access to the most up-to-date information and contributing to the successful implementation of SoD.
6. Risks of Potential for Collusion
It is crucial to recognize that while the separation of duties serves as a valuable control mechanism, it may not completely eradicate the potential for collusion within your organization. Collusion occurs when individuals with distinct responsibilities collaborate to evade established controls and exploit vulnerabilities, posing a threat to your organization.
Despite their separate roles, individuals may devise schemes to manipulate the system and achieve shared objectives, causing serious harm. For example, two employees with different responsibilities might intentionally collaborate to carry out unauthorized activities. If one employee has access to social media accounts and another has the authority to create posts, they could team up to post inappropriate content, damaging the company's reputation.
External factors, such as personal relationships or shared interests, can also contribute to collusion risks. Close friendships or familial ties between employees may lead to a sense of loyalty that transcends professional roles, enabling collaboration in harmful actions.
To address the risk of collusion, organizations must implement additional security measures alongside SoD. Regularly reviewing access controls and permissions to align with the principle of least privilege is essential. Monitoring and auditing systems should be in place to detect suspicious behavior or collusion patterns.
Ongoing education and training for all employees on ethical behavior and the consequences of collusion can help foster a strong culture of integrity. Encouraging employees to report suspicious activities is a vital early warning system against potential collusion. By combining these measures, your organization can enhance its defenses against collusion risks and safeguard its integrity.
7. Risks due to resistance to change
SoD, a crucial strategy for distributing critical tasks to prevent conflicts of interest and potential fraud, fortifies your organization's internal controls. However, this approach can trigger uncertainty and resistance among your workforce, with employees hesitating to embrace changes in their roles and responsibilities, perceiving them as unnecessary or overly burdensome.
Resistance often stems from the fear of the unknown. Employees accustomed to existing tasks and routines may feel insecure and uncomfortable about altering their roles. Concerns about adapting to new responsibilities or fears of reduced job satisfaction due to increased complexity or workload may arise.
Addressing these concerns proactively is vital for an IT manager. Open communication is critical for overcoming resistance to change. Clearly explain the reasons behind SoD implementation, emphasizing its significance in enhancing security and safeguarding organizational assets.
Consider the impact on employee morale as well. Changes perceived as disruptive or unreasonable can lead to dissatisfaction and decreased motivation. Attending to emotional responses and facilitating a smoother transition is crucial. Providing training and support for new tasks builds confidence and competence, reducing the likelihood of resistance.
It is essential to encourage employees to share concerns and ideas and give them a voice in the process. Acknowledge and celebrate successes as your team adapts to the new SoD framework, fostering a positive attitude toward change.
Maintaining compliance with regulations and safeguarding sensitive information is paramount. Enter Identity Governance and Administration (IGA) solutions, such as Zluri.
Zluri's IGA solution allows you to define clear access policies enforcing SoD rules, automatically detecting and flagging any access combinations that could lead to conflicting activities. Let's delve into how Zluri achieves this.
Leverage Zluri’s IGA Solution to Mitigate the Segregation of Duties Risks
Navigating the complexities of setting up Separation of Duties policies can be challenging. Zluri's IGA platform simplifies this task, offering seamless user access management from initiation to conclusion.
How? Let's explore!
Unleashing the power of Zluri’s discovery engine
Zluri empowers your teams with cutting-edge discovery engine, simplifying the analysis and revelation of crucial data concerning your SaaS applications and user activitiesuses 9 discovery methods to gain complete visibility into your organization's SaaS landscape. These methods include browser agents, IDPs & SSO, direct integrations, desktop agents, active directories, HRMS platforms, MDM platforms, finance systems, and CASB platforms. This empowers your team to identify and manage SaaS applications effectively.
In fact, Zluri has been named in the Gartner® Report: Reduce Your IAM Attack Surface Using Visibility, Observability, and Remediation. Download now!
Gartner, Reduce Your IAM Attack Surface Using Visibility, Observability, and Remediation, Rebecca Archambault, 8 October 2025
Gartner is a trademark of Gartner, Inc. and/or its affiliates.
Gartner does not endorse any company, vendor, product or service depicted in its publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner publications consist of the opinions of Gartner’s business and technology insights organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this publication, including any warranties of merchantability or fitness for a particular purpose.
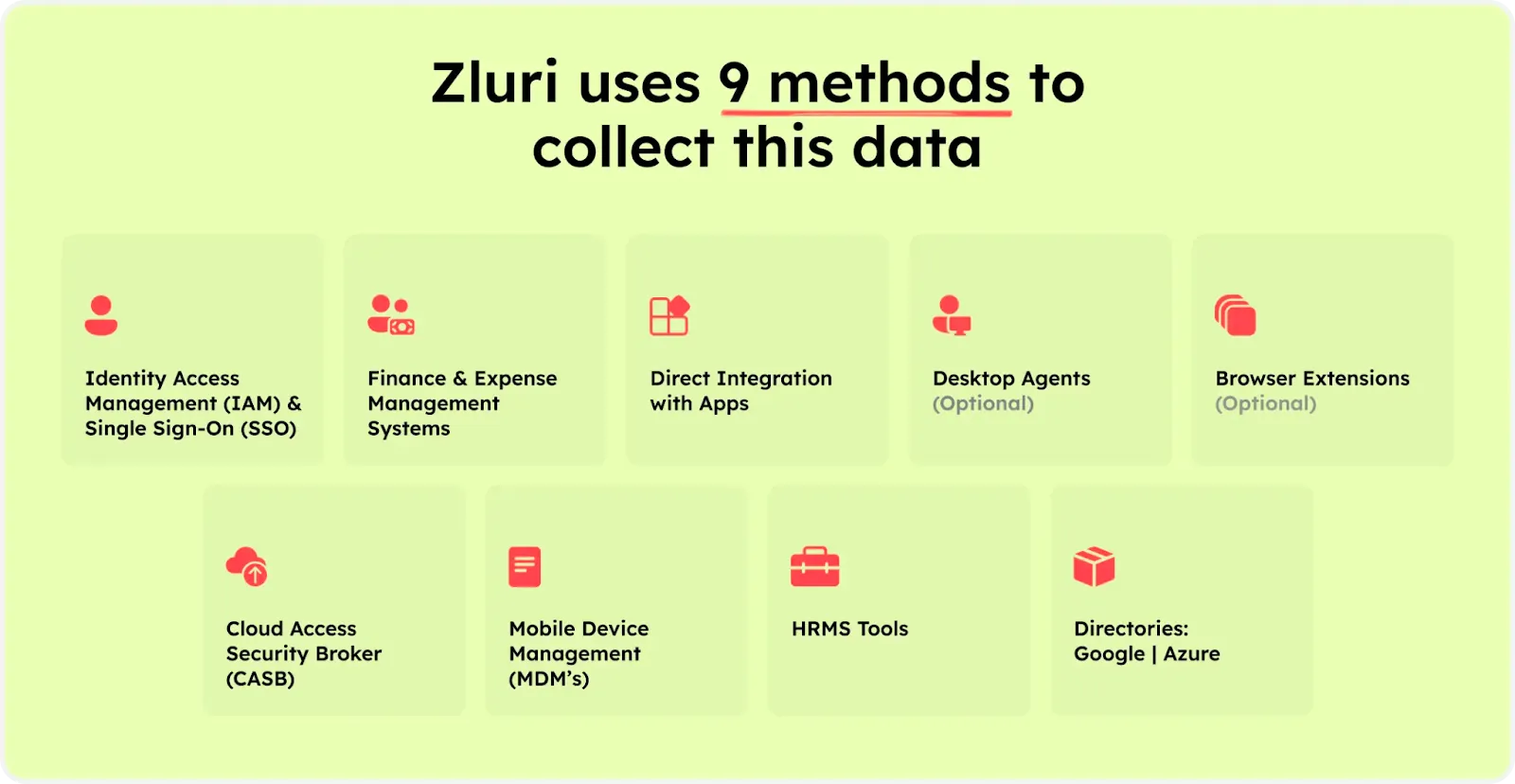
Beyond discovery, Zluri seamlessly integrates with over 300 SaaS applications, delivering real-time data, valuable insights, and AI-powered alerts to keep you consistently informed about SoD risks. With API-based integrations, Zluri guarantees thorough data discovery across all your SaaS applications, providing 100% visibility into your SaaS environment and robust SoD risk mitigation.
It excels in providing detailed access data, offering a comprehensive understanding of user permissions and access levels within your SaaS ecosystem.
Empower Seamless Access Management Governance & Mitigate Segregation of Duties Risks
- Lifecycle Management
Zluri's user management solution makes handling employee access a breeze, ensuring your organization stays secure. Whether it's welcoming a new team member or saying goodbye, our IGA platform simplifies the process, maintaining tight security measures.
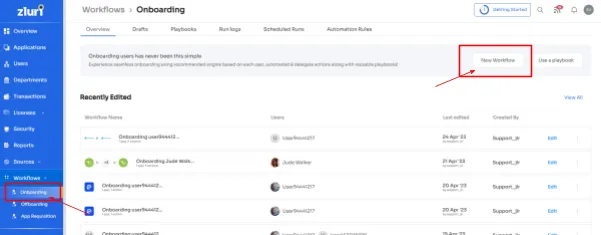
- Onboarding Made Easy:
When a new team member joins, Zluri's IGA ensures they quickly get access to the tools and resources they need. Automated onboarding steps and integration with HR systems mean less hassle. IT teams set up accounts centrally, reducing errors and making sure new hires have the right access from day one.
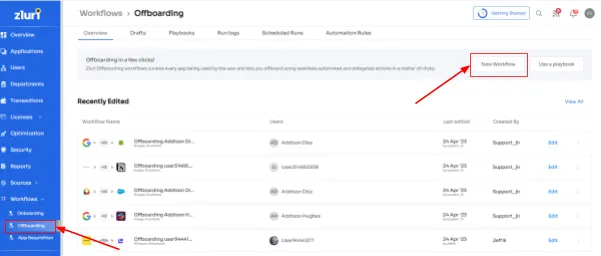
- Smooth Offboarding:
When someone leaves, Zluri's IGA helps IT teams take swift action. Automated deprovisoning processes revoke access across all tools, minimizing the risk of security issues. This proactive approach supports a strong security environment, making sure users only have access that fits their roles.
Innovative Features for Effective SoD Risk Mitigation: Zluri distinguishes itself with unique features that directly address SoD risk mitigation:
- Customizable Workflows: Tailor pre-defined workflows to your organization's distinct requirements, eliminating the need for manual access permission management. Zluri's intuitive interface allows customization based on user roles, departments, and seniority levels.
- Powerful Recommendations: Contextual app recommendations, based on user profiles, departments, and seniority, simplify the selection of appropriate apps for provisioning. In-app suggestions enhance user productivity by recommending efficient actions for task performance, all while maintaining SoD compliance posture.
- Reusable Playbooks: Save workflows as predefined "playbooks," eliminating the need to recreate processes for each user. This feature streamlines the entire process, boosting operational efficiency and contributing to a consistent SoD framework.
But what happens when a user’s role changes during the mid-lifecycle transitions?
- Access request management
Zluri makes managing user access during role changes super easy with its Employee App Store (EAS). This intelligent feature empowers your IT team to control employees' access to essential tools and applications.

The EAS allows swift review and approval of access requests based on job roles, ensuring precise access controls and safeguarding sensitive information.
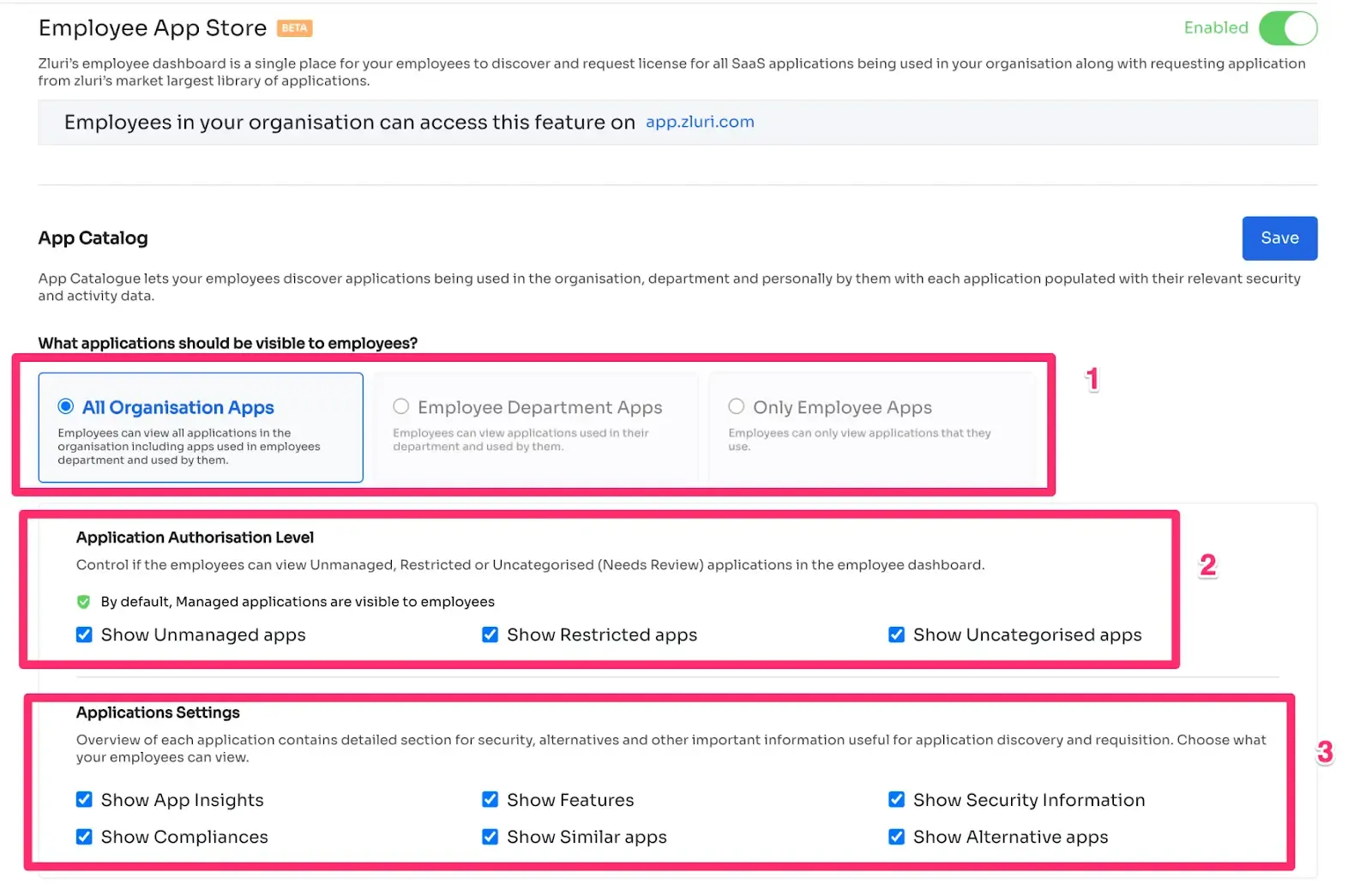
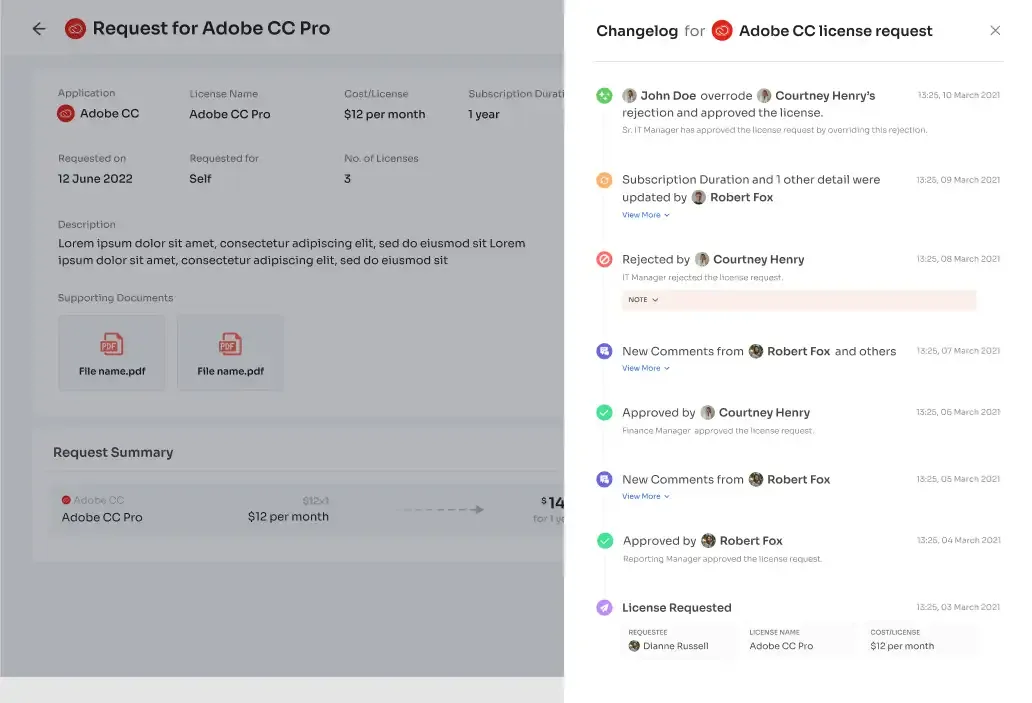
Zluri's transparent approval process operates on three levels: app owners, reporting managers, and IT admins. Higher-level authorities can override decisions by lower-level admins.
In case of rejection, decision-makers can provide clear comments. Approvers can modify requests as needed.
Zluri's "changelog" feature keeps users informed about access request updates, ensuring transparency and awareness.
Access certification
Say goodbye to manual complexities, as Zluri's intuitive platform simplifies setting up access review parameters, selecting reviewers, and scheduling campaigns. The intelligent automation feature evaluates user access rights using predefined rules, significantly reducing the time and potential errors compared to traditional methods.

Zluri's distinctive approach to access reviews aligns seamlessly with SoD risk mitigation:
- Continuous Access Reviews: Conduct periodic user access reviews with recurring assessments to systematically review access rights. This proactive approach helps identify and address potential Segregation of Duties risks swiftly.
- Scheduled Certifications: Plan and execute timely evaluations to reduce the risk of overlooking critical access issues. Zluri provides industry-standard certificate templates, ensuring an efficient, comprehensive, and accurate certification process tailored for SoD risk mitigation.
- Real-time Access Reviews: Leverage the power of artificial intelligence as Zluri continuously analyzes user activity, access patterns, and system logs in real-time. Detect unusual actions promptly, preventing SoD-related security threats and safeguarding sensitive information.
Leverage Zluri's AI compliance capabilities for intelligent insights and recommendations, ensuring your access controls align seamlessly with industry regulations and SoD standards. Simplify the compliance process effortlessly, making it easier for your organization to navigate and mitigate Segregation of Duties risks effectively.
FAQs
1. What is a Segregation of Duties Matrix template?
The SoD Matrix template is a visual representation or table that outlines and categorizes different job functions and responsibilities within an organization. It helps identify potential conflicts and ensures that critical tasks are appropriately divided among multiple individuals or roles.
2. How does Segregation of Duties work in the context of information systems?
In information systems, SoD involves defining and controlling user access to ensure that no single user has the ability to both create and approve transactions, which could lead to misuse or fraud.
3. Is SoD only applicable to large organizations?
No, SoD principles can be applied to organizations of all sizes. While the specific processes and risks may vary, the fundamental idea of separating duties to prevent conflicts and enhance security is applicable across different scales.







.png)

.svg)














