Granting users excessive privileges can create access gaps, while overly restrictive permissions can hinder their productivity or disrupt workflow. So, what to do? Strike a balance between maintaining security and meeting users’ requirements. Grant users access to what’s necessary for performing their responsibilities. How to achieve that? Implement user access controls. How? In this article, we’ll discuss the implementation procedure in detail.
Before we dive into the user access controls implementation procedure, let’s first address a couple of the most frequently asked questions: ' What are user access controls?’ ' How do they work?’ and ‘Why are they important?’
User access control is a security practice or technique that helps manage and control what users can view, use, or modify within an organization (regardless of whether the environment is on-prem or cloud computing). The main mission is to ensure apps, systems, data, networks, or any other resources are only accessed by authorized individuals with the right permissions.
How exactly do the user access controls work? They leverage authentication and authorization mechanisms to regulate user access rights. First, they verify user identity and then allow them to access resources based on pre-defined access rules.
- For instance, if an IT administrator attempts to access a particular application, the user access control system (you’ve got to set it up in your system beforehand) will validate whether the user is truly an IT admin (you’ve got to integrate your system with the identity provider (IdP) to authenticate the user's identity). Once validated, it will grant the IT admin access rights (as per pre-defined rules) and allow them to access the apps further.
Why is implementing user access controls so important? They act as a defense mechanism, helping prevent security incidents or breaches. Here’s how?
- When you apply user access controls, your users are only granted restricted access permissions – nothing more. How is it helping? Suppose a malicious actor somehow gets hold of your user’s account; now, their next move will be to use the permission that the account holds to access different resources and exploit them. However, by having user access controls in place, every user within your organization will have restricted access rights by default. This means even if the intruder manages to get their hands on any user account; they won’t be able to cause much damage due to limited access. As a result, your most critical resources will stay out of their reach, and the breach impact will also be less damaging.
- In fact, user access controls also protect your organization's resources from insider threats. Limiting users' access rights prevents accidental mishaps, such as users unintentionally deleting or omitting records or data (these incidents happen when users are granted excessive privileges).
- That’s not all; user access controls even help adhere to compliance regulations. Since user access controls are basically a security measure designed to prevent security breaches and protect critical data, implementing them fulfills one of the most mandated requirements set forth by compliance regulations (be it SOX, HIPAA, or GDPR): maintaining data security.
After becoming aware of the importance of user access controls, you’ll probably be eager to learn how to implement them. So, let’s dive in.
User Access Control Implementation Procedure
Below, we’ve provided a clear, step-by-step breakdown of the implementation procedure for user access controls.
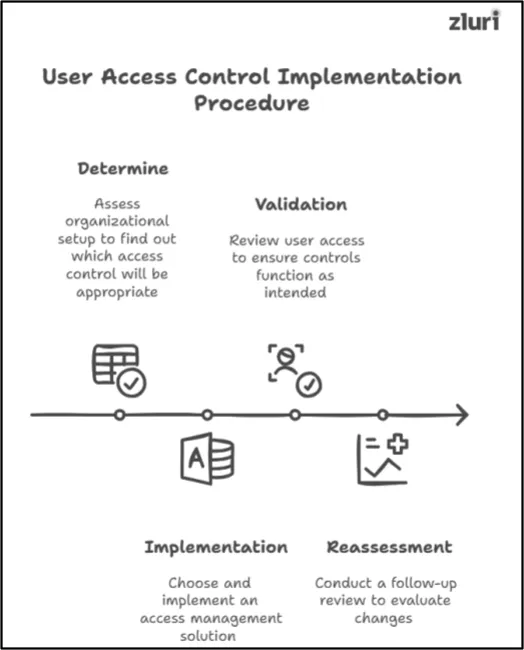
Step 1: Determine — Assess Your Organization’s Setup To Find Out Which User Access Control Will Be Appropriate
Blindly following trends or randomly choosing a user access control and applying it across your organizations is neither a viable practice nor will it work. Simply put, the user access controls you picked on a whim won't deliver the desired results.
So, instead of making decisions based on a fleeting notion, take a pause and start by assessing your organization's setup and requirements (such as what type of user base you have, large or small, whether your organization operates remotely, whether you engage with freelancers and seasonal contractors frequently, and a few other things). This practice will help you determine which user access controls suit your organization.
To provide you with clarity, we've outlined a few scenarios below and mentioned which user access control applies to each one. Let's say:
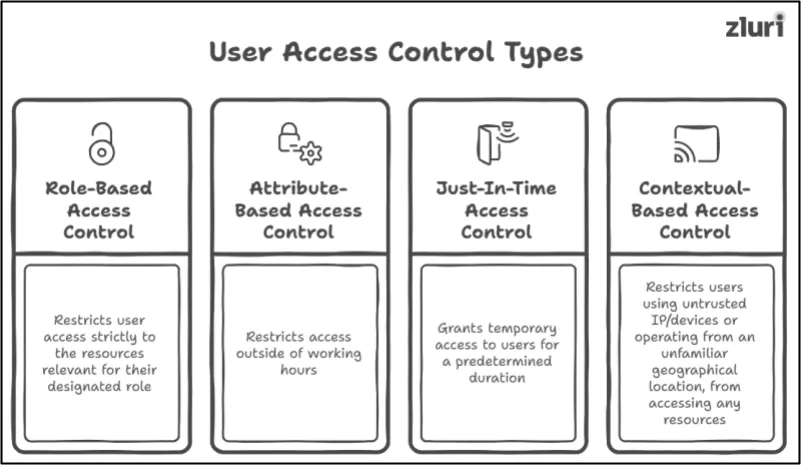
- Scenario 1# You're a large enterprise with multiple departments, such as HR, IT, sales, and finance, each with many users (employees). Now, you want to ensure that each user within these departments holds access to applications or other resources relevant to their role and nothing else. So, which type of user access control will be suitable?
User Access Control Type: Role-based access control (RBAC)
By applying role based access control, you can restrict a user’s access to only the resources that are relevant to their designated role. For instance, RBAC will grant users from the HR department access to tools like BambooHR, Workday, or HR cloud and will restrict their access to apps of other departments (as those apps are not relevant to their role).
- Scenario 2# Your organization operates remotely, and you have employees working from various locations around the globe. Now, you want to ensure that once your users clock out for the day, they no longer continue to access any of the critical datasets (this is typically done so that no users accidentally delete or alter sensitive data outside of working hours). So, which type of user access control would be a perfect fit for this scenario?
User Access Control Type: Attribute-Based Access Control (ABAC)
By applying attribute based access control, you can put time-based restrictions. For instance, the moment users log out (their work hours finish) from apps (that store critical data), the system will automatically revoke it (since you applied ABAC), protecting your critical data from accidental mishaps.
- Scenario 3# Your organization frequently engages with seasonal contractors and freelancers. Let's say you’re not comfortable with the idea of granting them standing privileges (i.e., always-on access rights). In that case, you just want to ensure these external users have access to your organization's apps or other resources necessary for performing their tasks for a predetermined period without exposing your resources to potential risks. So, which type of user access control would be ideal?
User Access Control Type: Just-In-Time Access Control (JIT)
By applying just-in-time access control, you can grant your seasonal contractors and freelancers access to your apps on an as-needed or temporary basis for a predetermined duration. Once these external users' contract terms end, the system will automatically revoke all the permissions granted to them (preventing lingering privileges).
Also Read: What Is Zero Standing Privilege?
- Scenario 4# Your organization has framed a whitelist specifying the trusted IP address, geolocations, and devices that are permitted to access the organization's resources. Now, you want to ensure that any access (login) attempts made by users using restricted IPs or unknown devices or operating from unauthorized locations (basically, which are not mentioned in the whitelist) are immediately restricted – no exceptions. So, which type of user access control would help achieve this?
User Access Control type: Contextual-Based Access Control (CBAC)
By applying contextual-based access control, you can restrict users – those using untrusted IP addresses or unauthorized devices or operating from an unfamiliar geographical location – from accessing any resources within the organization. For instance, if your user requests to access an app from a location (which is not specified in the whitelist), the system will automatically deny the access request (by default). It doesn’t matter if they’re authorized personnel or not; if they don’t meet the criteria, they will be locked out!
Note: You are not compelled to implement or adhere to just one user access control—you can strategically combine (mix and match) different user access controls to address your organization’s varied needs.
Step 2: Implementation — Opt For An Access Management Solution To Implement User Access Control
Once you've selected the appropriate user access controls, the next step — is to put them in, i.e., enforce them across your organization. How to do that? Typically, there are 2 ways to implement user access controls:
- Method 1: You can leverage access management solutions that will automatically apply the user access controls consistently (once triggers are specified) to access your organization with the least manual involvement.
- Method 2: Or else you can configure access control lists (ACLs) — it's a built-in feature available in most web applications that defines rules (you’ve to set up the user access control rules) about who can access what and applies them across the organization.
Now you’ll probably ask — ‘Which user access control implementation method should you choose?’
- If your organization has fewer resources (just a handful of applications or systems), you can consider opting for method 2, i.e., configuring the ACLs. You can directly configure each app and set up your preferred user access control rules without a hassle.
- However, if your organization has a large stack of resources, then you should definitely leverage an access management solution (i.e., method 1) — it’s a viable option. Why? Because configuring ACLs across 100s of web apps and systems can be quite challenging.
But how exactly does an access management solution help enforce user access controls?
To demonstrate how access management solutions enforce user access controls, below, we’ve taken Zluri’s access management solution as an example and explained how it serves the part.
Zluri’s access management solution offers an access control auto-engine that simplifies the user access controls implementation part. Here’s how it works: Zluri’s access control auto-engine provides an automated workflow in which your team needs to specify the user access control rules — and Zluri further applies those controls across the organization automatically.
Suppose, you want to enforce role-based access control, so all you need to do is specify — the trigger ‘when,’ conditions ‘who or what,’ and the action ‘then’ in the workflow as below:
Once the configuration is completed, whenever an IT admin requests to access an application, Zluri’s access management will first automatically validate whether they met the conditions or not. If conductions are met, such as if the user who is requesting app access is an IT admin, then access will instantly be granted. If the user doesn’t meet the conditions, Zluri will automatically deny access by default.
Step 3: Validation — Perform a User Access Review To Check Whether The Implemented User Access Controls Are Performing As Intended Or Not
Your journey doesn’t just end at implementing user access controls – you further need to thoroughly check whether they are functioning properly, meaning they can restrict access to authorized users only. To do so, you need to perform a user access review.
But the real question is, how do you perform this review? Well, you have two options: either opt for a manual approach (do it manually) or go for an automated approach (let an access review solution help you with the task).
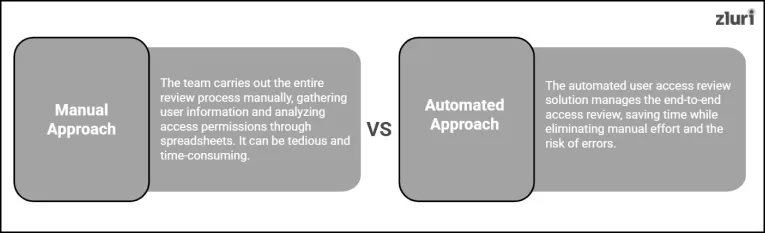
- Manual Approach: If you opt for this approach, your team will need to carry out the entire review process manually. This means that to review users' access, they'll first need to gather relevant user information by switching between multiple tabs and then have to carefully jot down those details in spreadsheets. Once the data is compiled, they have to analyze whether users hold the right access permissions (which will depict how your implemented user access controls are performing) – by going through those prepared spreadsheets. It can be tedious, time-consuming, and might leave room for human errors.
Nonetheless, if your organization is small and has a limited number of users and applications (roughly 10-20 users and apps), then this approach for reviewing user access rights might work fine. However, for mid-sized organizations or enterprises that have a complex infrastructure (with hundreds, even thousands, of users and a vast SaaS stack), this method simply won't suffice (review results won't be accurate).
Also Read: 6 Key Metrics for Reviewing User Access Rights
- Automated Approach: If you opt for this approach, you simply need to leverage an automated user access review solution to perform the access review (simply put, the solution will manage the task on your behalf), saving time and eliminating the risk of errors. How do they work?
To demonstrate how access review apps help evaluate implemented user access controls performance, below, we’ve taken Zluri’s access review solution as an example and explained how it functions.
Zluri’s access review solution offers two advanced features, a discovery engine, and auto-remediation capability, that simplify the process of reviewing user access rights and assessing the effectiveness of user access review controls.
Here’s how it works: It first integrates with your applications and automatically retrieves data regarding which users have access to the application. Then, it compiles a list of users alongside relevant details such as the user’s role, active status, designation, and a few other details and presents it in a centralized dashboard, making it easier for your reviewing team to evaluate that information.
Now, all your team needs to do is simply look for misalignments, such as users holding excessive privileges or departing user accounts that still have app access. In case any access anomalies are discovered that clearly depict your implemented user access controls not performing as expected, your team can directly request the IT team to re-configure the user access controls settings so that they function properly. But wait!
Here’s the best part: with Zluri, your team doesn't just have to stop reviewing user access privileges – they can take immediate remediation actions while they’re at it. This helps ensure that no access misalignments are left unresolved, preventing the creation of security loopholes that attackers can exploit.
Let’s say your team identified multiple inactive users holding access to one of your apps. With Zluri’s bulk remediation action feature, they can revoke all their access permissions in one go—right on the spot. No delays! No extra hassle!
That’s not all; after the review, Zluri even prepares a detailed user access review report (which works as audit logs) outlining all the actions performed during the process so that you can refer to it in the future or whenever needed.
Also Read: User Access Review Checklist
Step 4: Reassessment — Conduct A Follow-Up User Access Review To Evaluate The Implemented Change
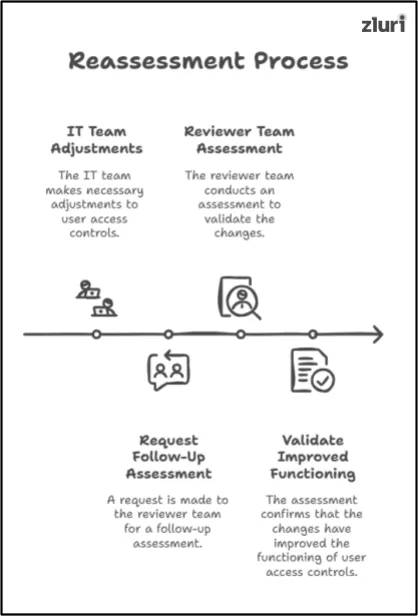
Note: This step only applies if any access misalignments were detected and the reviewing team requested to re-configure the implemented user access controls. If no changes are requested, this step can be skipped entirely.
Once the IT team has made the necessary adjustments to fix the functioning of the implemented user access controls, you can request that your reviewer team perform a follow-up assessment.
(Note – Make sure that your IT team isn’t the one responsible for reviewing the changes. The reason is that their involvement can introduce biases or create conflicts of interest, compromising the integrity of the review process).
This follow-up review will help validate that the changes made to user access controls have truly improved their functioning.
Create A Zero-Trust Security Setup By Implementing User Access Control
One thing is certain! You can no longer rely on the practice of blindly trusting your internal users and giving them the leverage to access ‘any’ application or resources they want – it’s not safe. Why? Malicious actors have evolved, and their tactics are more sophisticated than ever. They are not just targeting your apps and systems anymore; they are targeting your internal users – so they can impersonate and get into your systems.
This brings us to a terrifying truth: You might not even know that the user accessing your apps is really one of your trusted users or a malicious actor in disguise, putting your entire organization at risk.
This is why creating a zero-trust security setup is necessary. In this setup, no one, not even your internal users, is trusted by default. Everyone will be verified before they are given access to any apps or other resources. How to create this setup? It’s simple—you can implement user access controls (that act as defense mechanisms). These controls basically enforce strict conditions and allow users who meet the exact criteria access to organization resources.
For instance, users will only be granted access if they use trusted devices, connect from approved IP addresses, or try to access the system within business hours. If any of these conditions are not met, access is automatically denied—no exceptions.
With such rules in place, you regain control over who can access what within your organization. It’s a simple yet powerful practice ensuring only authorized users can enter your ecosystem at the right time and from the right place. In fact, you also get the peace of mind knowing that your critical resources are protected against unwanted intruders.
Also Read: What Is Access Control?
Frequently Asked Questions (FAQs)
1. What Is The Difference Between User Authentication & User Access Control?
User authentication involves verifying a user's identity, whereas user access control involves controlling what resources an authenticated user can access.
2. What Is The Difference Between Just-Enough-Access Control And Just-In-Time Access Control?
Just enough access control ensures users have minimal access necessary to perform their designated task (it's similar to PoLP user access control policy). Meanwhile, the just-in-time factor is taken into consideration. It ensures users are granted access for a limited duration when needed.





.svg)














