Security & Compliance
• 9 min read
DLP Policies: A Guide To Strengthening Data Security
29th September, 2022
SHARE ON:
As our reliance on data for daily operations deepens, organizations are consistently generating larger volumes of data daily. The repercussions of data loss can be catastrophic for a company, impacting both its reputation and financial stability. With the escalating prevalence of data threats, the importance of data security has never been more pronounced.
Therefore, it's crucial to understand and implement robust Data Loss Prevention or DLP policies and procedures to consistently safeguard your valuable data.
Data loss prevention (DLP) is a comprehensive concept covering various tools, techniques, and practices to prevent end-users from unintentionally transmitting critical or confidential data outside of an organization, reducing the risk of data loss. It acts as a safeguard against unauthorized access or theft of sensitive data by unauthorized users. Furthermore, it also aids network administrators in overseeing the movement of end-user data within the organization's network.
Data Loss Prevention or DLP Policies: An Overview
DLP policies include strategies, tools, and practices designed to prevent sensitive or confidential data from being unintentionally or maliciously leaked, lost, or exposed to unauthorized individuals or entities. The primary goal of DLP is to protect an organization's sensitive data, such as intellectual property, customer information, financial data, and other valuable information. For instance, in the event of a ransomware attack, where critical data may be at risk of loss, DLP measures play a crucial role.
DLP encompasses several key components and features:
Content Discovery: DLP systems scan an organization's data repositories to identify sensitive information, which may include credit card numbers, social security numbers, personal health information, trade secrets, and more. This is often done through keyword patterns, regular expressions, and other algorithms.
Data Classification: Once sensitive data is identified, it is typically classified based on its sensitivity level. Classification helps organizations prioritize protection efforts and determine who should have access to this data.
Policy Enforcement: DLP solutions use policies to define what actions can or cannot be taken with sensitive data. Policies may include restrictions on data sharing, copying, printing, or emailing. These policies are enforced through a combination of technologies and processes.
Monitoring and Alerts: DLP systems continuously monitor data flows and user activities. If they detect a violation of established policies, they generate alerts for administrators or security teams to take appropriate action.
Data Encryption: DLP often includes encryption capabilities to protect data at rest, in transit, and in use. Encryption can help safeguard data even if it falls into the wrong hands.
Endpoint Protection: DLP extends to endpoint devices like laptops and mobile phones, where data can be easily exposed or lost. Endpoint DLP solutions help control and monitor data on these devices.
Network-based DLP: This focuses on monitoring data as it moves across an organization's network, ensuring that sensitive information is not inadvertently exposed or leaked.
Cloud-based DLP: As organizations increasingly move data to the cloud, DLP solutions have adapted to protect data stored in cloud services and ensure it complies with data protection regulations.
User Education and Training: DLP efforts often involve educating employees about the importance of data protection and best practices for handling sensitive information.
DLP is crucial for maintaining data security, regulatory compliance, and protecting an organization's reputation. It is commonly used in industries with stringent data protection requirements, such as healthcare, finance, and government.
Implementing an effective DLP policy requires a thorough understanding of an organization's data, clear policies, and a combination of technology solutions and human vigilance.
Why are DLP Policies Needed Today?
Data Loss Prevention (DLP) serves a critical purpose by safeguarding sensitive data against unauthorized access, exploitation, or destruction. DLP software aligns with pertinent regulations, such as GDPR, HIPAA, or PCI DSS, to classify data into categories like regulated, confidential, or business-critical. In the event of a policy violation, DLP software takes proactive measures, often involving protective actions such as encryption and generating alerts.
DLP software and tools play a multifaceted role by filtering network data streams, overseeing endpoint operations, and monitoring cloud-based data. They ensure that data in use, data in motion, and data at rest remain shielded through a variety of DLP techniques. Additionally, DLP systems offer robust reporting capabilities, facilitating compliance with audits and routine requirements.
The increasing complexity of data security challenges drives the growing prominence of DLP technologies. With data residing in diverse environments, including databases, flash drives, file servers, mobile devices, personal computers, physical servers, and the cloud, the potential vectors for data exposure are numerous. DLP solutions address this by offering versatile means of addressing breaches and losses, considering the various ways data can traverse network access points, including VPNs and wireless networks.
The Role of DLP Policies in Preserving Data Integrity
Preserving the integrity of your data is paramount in today's digital landscape. Custom DLP policies play a crucial role in safeguarding your organization's sensitive information. These policies are meticulously designed after a comprehensive risk assessment to mitigate the potential for accidental data loss. By adding this additional layer of protection, DLP policies act as a robust safeguard against data breaches and uphold the integrity of your critical data assets.
Data Loss Prevention Policy stands as an indispensable safeguard wherever data is stored. A fundamental pillar of the DLP approach revolves around the comprehensive protection of data in three key states:
Data in Use: DLP encompasses strategies to protect data in use, denoting information currently being processed by an endpoint or application at the moment of safeguarding. This often entails measures like user authentication and access control, ensuring that resources remain secure before granting access.
Data in Transit: DLP technology plays a pivotal role in guaranteeing that confidential data in transit across networks follows secure routes and remains within the organization's confines. Essential facets include safeguarding email communication, a cornerstone of modern business correspondence, and the implementation of encryption protocols to keep data shielded during transit.
Data at Rest: Even data at rest is not exempt from risk, and DLP solutions step in to secure files stored in diverse mediums, including cloud storage. These solutions exercise control over data storage and access, applying encryption to storage devices and vigilantly monitoring access to sensitive information.
An all-encompassing DLP solution excels in identifying and protecting various data types while identifying vulnerabilities. Its capabilities allow you to:
Recognize sensitive data that necessitates protection, whether through manual or automatic means, with the aid of metadata and predefined rules.
Regulate data transfers, whether between external users, internal users, or groups, through the deployment of endpoint-based agents.
Establish mechanisms to detect and alert against unauthorized activities or inadvertent policy violations, ensuring timely response and corrective action.
Safeguard data in motion by leveraging network edge technologies to scrutinize data traffic, pinpointing critical data breaches.
Employ encryption protocols to protect data at rest and enforce data retention policies effectively.
Detect data leaks by actively monitoring data transfers, identifying anomalies and unauthorized movements.
DLP policies serves as a comprehensive guardian of data integrity, ensuring data remains secure in every conceivable state and circumstance.
Key Benefits of Robust DLP Policies For Your Organization

DLP policies offer a proactive and comprehensive approach to fortify your data safeguards. Here are some key benefits:-
Comply with Regulations: Secure and comply with personal data, such as that which can be used to identify an individual, as defined by the GDPR, HIPPA, and CCPA. Data loss prevention tools identify, categorize, and tag sensitive data so that context, such as events and actions surrounding the data, may be monitored. Data loss protection tools also report in accordance with regulatory requirements, making compliance audits more manageable if they occur.
Protect your IP: On the internal network, protect the organization's important intellectual property (IP). Data loss prevention tools allow you to classify intellectual property in both organized and unstructured forms based on context. With the proper controls and policies, you can prevent unwanted exfiltration of sensitive data.
Have Data Visibility: Without understanding and the power to act, data is useless. If your company needs more visibility into data flow, a comprehensive enterprise data loss prevention solution can help you monitor and track your data on networks, endpoints, and the cloud. This gives you a better understanding of how individual users and data interact inside your business.
Secure BYOD: Secure environment in which users bring their own devices (BYOD). For personal mobile devices, malware is one of the most critical threats to endpoint security, according to the 2019 . Malicious exploits frequently use malware as a way to exploit.
Secure the Cloud: On cloud storage systems, ensure that data is protected and that unauthorized parties cannot access it. Data loss prevention techniques for the cloud are used to avoid data breaches and leaks and secure data.
Implementing robust DLP policies offers a wide array of advantages, from data security and privacy to compliance adherence and risk mitigation. These policies are a crucial component of any organization's overall cybersecurity strategy, ensuring the protection and integrity of valuable data assets.
Ways To Implement Effective DLP Policies & Procedures
To fortify your organization's defenses against data breaches and leaks, it is imperative to adopt and implement measures to ensure the effectiveness of your DLP framework. DLP policies and procedures serve as a critical framework for maintaining data security, privacy, and integrity.
By successfully implementing the DLP framework, organizations can secure sensitive data, safeguard their reputation, and meet compliance requirements, all while fostering a culture of data protection and integrity.
Here are some key steps:-
Determine Objectives: Defining your data protection objectives is the cornerstone of an effective DLP strategy. For instance, if your primary objective is regulatory compliance, your architecture might focus on encryption and access controls. Alternatively, if you prioritize increasing data visibility, monitoring and analytics tools become essential. Clarity on objectives guides your data protection path.
Data Classification: Structured and unstructured data must be recognized and classified to drive DLP. By categorizing data, you can identify sensitive information and apply appropriate safeguards. For example, financial records are structured data, while unstructured data might include email communication. Proper classification informs targeted protection.
Security Policy: A robust security policy strengthens your DLP program. Regular audits, incident tracking, and reporting ensure accountability and threat mitigation. Consider an incident where a security breach occurs. A strong security policy not only facilitates swift remediation but also minimizes damage by having a plan in place.
Roles and Responsibilities: Clearly defined roles in your DLP program promote accountability and alignment with objectives. For instance, designating a data protection officer ensures someone oversees the program. In practice, this clarity helps ensure everyone understands their part in maintaining data security.
Scope of Strategy: Determine whether your DLP strategy focuses on specific data categories or entails automatic identification and classification. For instance, a company might focus on securing only customer data, while another implements automatic classification for all sensitive data. Your scope decision guides your deployment architecture.
Documentation: Detailed documentation of DLP features is essential for consistent application. Consider an organization that experiences personnel changes. Clear documentation eases training for new team members, ensuring that DLP processes remain transparent and effective.
Key Performance Indicators (KPIs): Establishing KPIs, including those specific to DLP, contributes to ongoing strategy enhancement. For example, monitoring incident response times is a DLP-specific KPI. Regular assessment and evaluation of KPIs demonstrate the effectiveness and value of your DLP strategy over time. Establish key performance indicators, including those specific to DLP and other measures of success. Regularly assess and evaluate their performance. This continuous evaluation contributes to the ongoing enhancement of the DLP strategy and demonstrates its business value over time.
With these steps in mind, IT teams can significantly bolster their data loss prevention efforts, thereby safeguarding their sensitive information and ensuring data integrity. However, there exists a powerful tool, Zluri, that can seamlessly enforce DLP policies for the integration of data security. Let’s explore in detail!
Use Zluri For Effective Data loss prevention
With the increasing reliance on cloud-based applications and services, the need for effective Data Loss Prevention (DLP) measures has never been more critical. Zluri, an efficient SaaS Management Platform (SMP), steps in as a powerful ally in this endeavor, offering comprehensive features to prevent data loss and enhance data security.

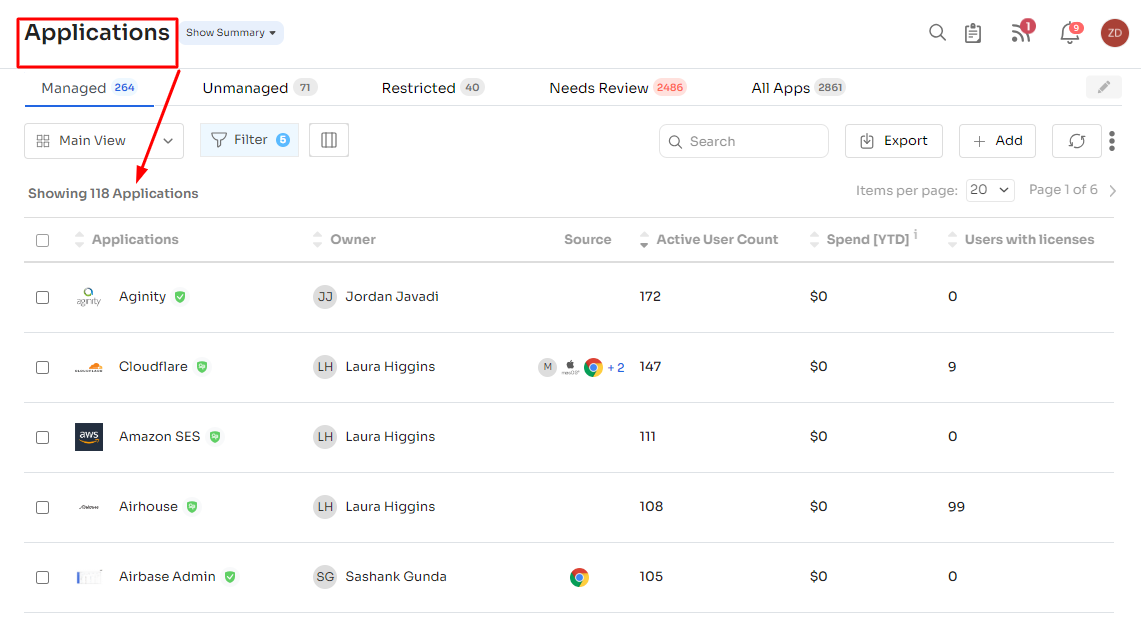
A 360-Degree View of Your SaaS Stack
Zluri empowers organizations with a centralized view of all the cloud-based applications in use. This invaluable capability provides insights into which SaaS applications are employed, who has access to them, and how they are utilized. Such visibility is instrumental in identifying data risks and vulnerabilities, facilitating proactive mitigation strategies.
Automated De-Provisioning for Error-Free Access Management
One common challenge that organizations face, even with comprehensive visibility, is the potential for human errors in managing user access, especially during employee offboarding. For instance, manually revoking access for multiple departing employees can be error-prone, potentially leading to data exposure risks.
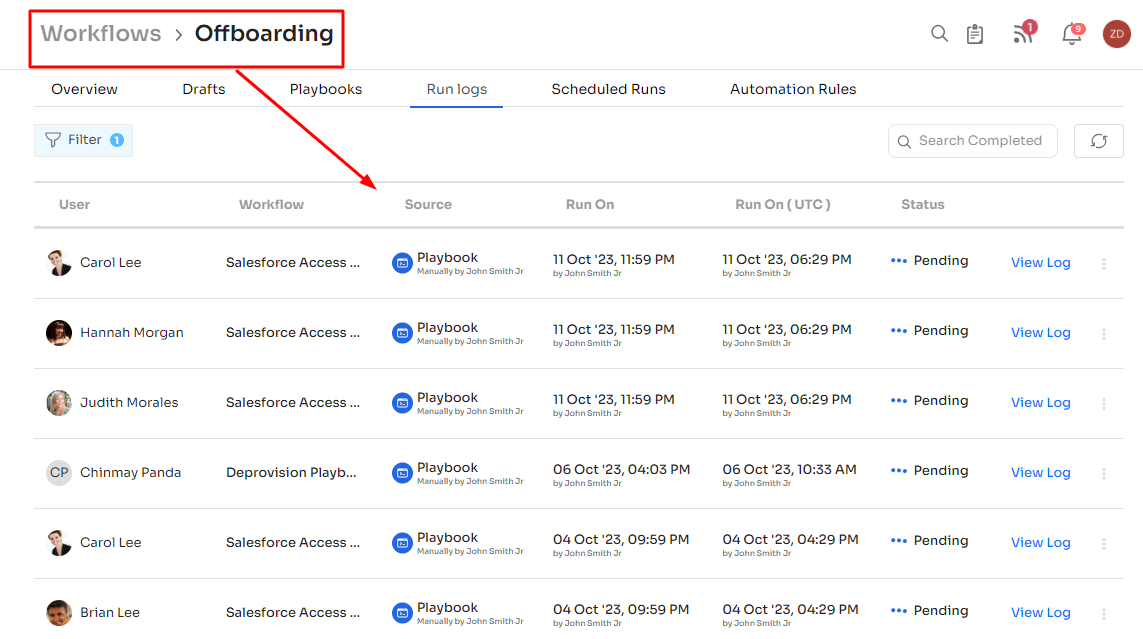
Zluri tackles this issue with its automated de-provisioning feature, allowing IT teams to swiftly and accurately revoke access with just a few clicks. Here's how it works:
User Access Removal: Zluri effectively removes a user's ability to sign in from all their devices, ensuring immediate cessation of access.
Data Transfer: Before removing access, Zluri carefully copies the user's data and transfers it to another designated user, preserving essential information.
Access Revocation: The user's access to the application is promptly revoked, leaving no room for data loss or unauthorized access.
With Zluri's automated de-provisioning, organizations can stay confident that every access point is adequately managed, reducing the risk of data loss during staff transitions.
Real-Time Data Monitoring
Zluri enhances your data loss prevention strategy by providing real-time data monitoring capabilities. It continuously tracks data movements within your cloud-based applications, identifying unusual or suspicious activities. This proactive monitoring enables swift detection of potential data breaches and unauthorized access, allowing your organization to respond promptly to security threats.
Policy-Based Enforcement
Zluri offers policy-based enforcement, enabling organizations to define and enforce access policies and data protection rules. These policies can include access permissions, data sharing restrictions, and encryption requirements. By automating policy enforcement, Zluri reduces the reliance on manual interventions and minimizes the risk of policy violations that could lead to data loss.
Compliance Assurance
Zluri plays a crucial role in maintaining regulatory compliance. It assists organizations in aligning their DLP efforts with industry-specific and regional data protection regulations. By providing insights into compliance requirements, access controls, and data encryption, Zluri ensures that your data security practices meet the necessary legal and regulatory standards, mitigating potential compliance-related risks.
Risk Assessment and Data Loss Prevention
Zluri goes a step further by aiding in comprehensive risk assessment. It identifies data risks associated with each cloud-based application within an organization. This includes pinpointing high-risk applications, assessing data-sharing policies, and evaluating access permissions.
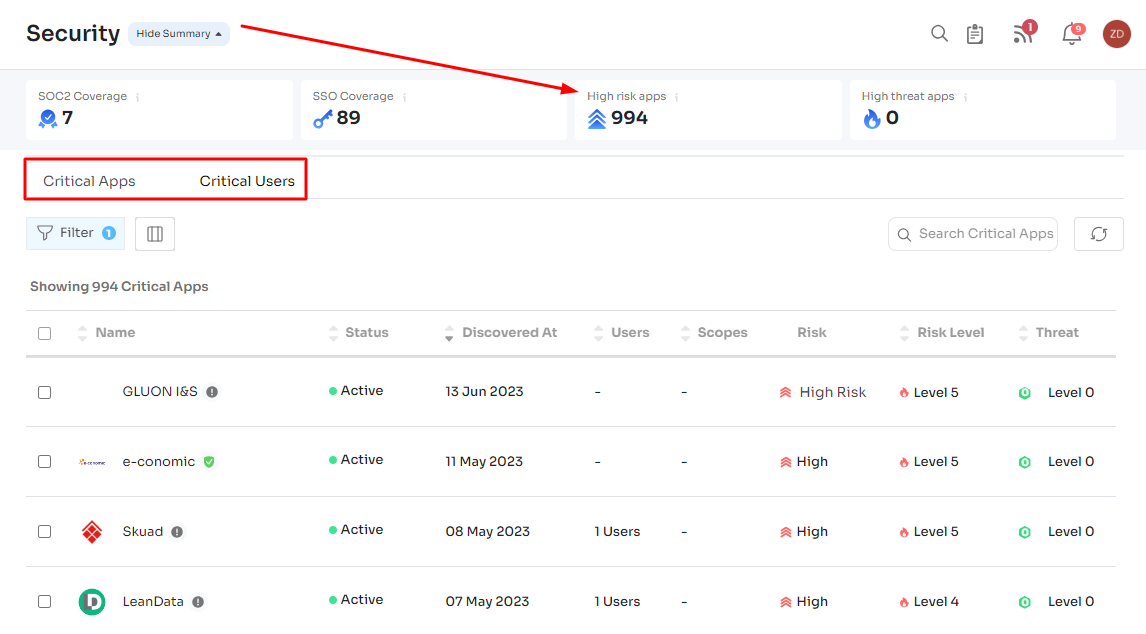
With this data-driven insight, administrators can take necessary actions to prevent data loss and unauthorized access, ensuring the security of critical information.
In an era where data security is non-negotiable, Zluri equips organizations with the features and capabilities they need to implement DLP effectively and proactively protect their data assets.
With Zluri, you can have peace of mind knowing that your organization's SaaS applications undergo assessment using strong security standards and industry best practices. This empowers you to make informed decisions and safeguard your invaluable data.
So, why hesitate? & Give it a try today!
Related Blogs
See More
Subscribe to our Newsletter
Get updates in your inbox
