Is your organization dealing with identity silos (fragmented directories) that make identity management a struggle? Or perhaps unauthorized users are able to bypass your implemented authentication mechanism? If you resonate with these issues, then identity fabric is your solution. What is identity fabric? In this article, we'll explore it in detail.
Before we discuss identity fabric, let me ask you an important question: 'Do you know what the prime target of malicious actors is?'
No, it's not an app or a network system – it is actually identity. Surprising right? But why identity?
Identities act as digital keys that help authorized users access the organization's app, system, and other resources. Since these keys provide a direct entryway, attackers look for ways to get hold of them.
This is precisely why most cybersecurity strategies are designed to safeguard identities (as in prioritizing meeting this need)—because protecting them means protecting everything at stake. Likewise, identity fabric is also built to serve the same purpose— 'to maintain identity security.' However, that's not all; there is more to explore, so let's dive deeper into the concept of identity fabric.
What Is Identity Fabric?
Identity fabric is a newly introduced concept in cybersecurity that focuses on empowering organizations to leverage solutions and strategies (such as using FIDOpasskeys instead of passwords, applying risk-based authentication methods, synchronizing directories, and more) to effectively manage identities and their data across all the systems, apps, and directories present in an organization's ecosystem (both on-prem and hybrid environment).
In simple words, identity fabric is a framework that provides guidelines for effectively managing and securing identities within your organization.
The main idea behind introducing this concept is to ensure that users' identities and data are kept out of malicious actors' reach (as attackers tend to target identities, exploit them, use them as a gateway to infiltrate apps or systems, and compromise sensitive data).
Note: Managing identities involves overseeing how identities are created, modified, or deleted and how they are authenticated before giving them entry. On the other hand, managing identities' data involves keeping track of where identities' data are stored (as in which all directories), whether the data is synchronized in all directories or not, and how third-party identity providers use the data of identities for authentication purposes. But don't confuse identity management with access management; they are both different concepts.
Also Read: Go through this blog post – Identity Management Vs Access Management: 5 Key Differences- to understand how they differ.
Now, you might probably question — 'What strategies and solution identity fabric recommend organizations to implement or adopt (other than the ones mentioned above)? How will these practices even help manage and secure identities?' Let's find out.
Strategies Outlined In Identity Fabric Framework
Below, we’ve mentioned the key practices outlined in the identity fabric framework and explained how each practice helps manage and secure identities.
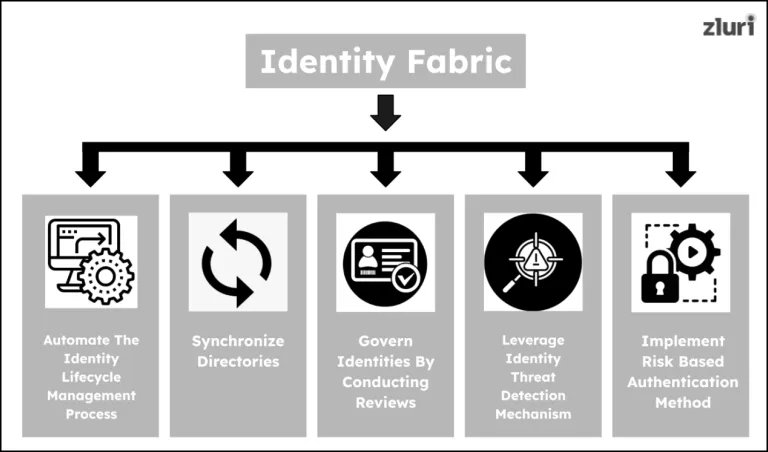
1: Automate The Identity Lifecycle Management Process — Simplifying Identity Creation, Modification, & Deletion
Managing the identity lifecycle manually has always been the go-to approach for organizations. Why? They think it is quite convenient! They also believe that practicing the manual approach will give them more control over how identities are managed.
But this is far from fact — what seems like control often turns into chaos while managing a growing pool of identities. What starts as ‘manageable’ quickly turns into tedious tasks, which consume significant time and open doors for mistakes to creep in. How? For that, you need to understand how IT teams manually create and delete identities. Here’s a breakdown of the process.
- When a new user joins, IT teams review the user's registered data (which the user provides before joining and is generally stored in HRMS), such as their email address, the role they are hired for, and which department they joined. Based on this information, a digital identity (information that uniquely defines an individual) is created, and then these identities and the data are recorded/stored in the organization's central identity store (directories).
- Similarly, when it's time to delete an identity (generally, this action is taken when a user leaves the organization), IT teams first go through the HRMS database and check whose identity needs to be deleted. Then, they compile the information in a spreadsheet and use it as a source of information, based on which they delete users' identities and then remove the identity data from the directories.
Note: When IT teams practice manual methods, they overlook the identity modification part, as it becomes cumbersome to track and update changes in roles, departments, or permissions in real-time.
Now, you'll probably say – 'What's the problem here?' Well! This example demonstrates what IT teams need to do to manage one identity – Just One! You can calculate how long it will take to create or delete 100s and 1000s of identities.
This approach can still work for small organizations that don't hire or remove employees often (a rare occurrence). However, for mid-size organizations or enterprises that hire employees frequently and do mass layoffs, this approach is not at all reliable—the possibility of mistakes (human error) is quite high! In fact, it will also put identity security at risk.
Also Read: Learn How to Manage Offboarding During Mass Layoffs
For example, while creating identities for 20 new users, IT teams might accidentally skip mentioning critical details (like role) in identities. This will further leave app admins clueless about which permission to grant. Likewise, while deleting 50 user identities, IT teams might unintentionally miss out on deleting 5 user identities. These leftover 5 user identities will be the perfect bait for attackers to breach your critical system.
Ask yourself, 'Does this approach sound even remotely reliable?' No, right! This is why identity fabric frames guidelines that specifically mention automating identity management.
Also Read: How to Automate Identity Management?
Now, to automate the identity lifecycle process, you can opt for an access management solution like Zluri. It offers an automated access management solution that simplifies the process of identity creation, modification, and deletion. Here's how it works.
When new users join, Zluri’s access management solution automatically (you have to trigger this action) creates a unique digital identity for each of them. Where does it get the data from? It gathers the user’s information (like name, email address, role, or position) by seamlessly integrating with your human resource management systems (HRMS) or directories.
When users undergo — a role change, department switch, or any other midlife cycle shift, Zluri’s access management solution instantly updates the user’s digital identity profile with new details.
When a user is marked for offboarding, Zluri’s access management automatically deletes the user's digital identity from the organization's database.
How is it helping to secure digital identities?
Since Zluri assigns unique identities to every user, it becomes more difficult for attackers to impersonate as legitimate users (as they can’t crack the unique ID; simply put, they cannot figure out the specifics/identifiers of the digital identity) and gain access to sensitive apps, systems, and data. Plus, whenever changes occur (like role or department changes), Zluri instantly updates the identities’ details. Since it constantly does that, attackers are left with invalid or stale digital identities. When they use these stale identities, they find it impossible to breach the organization’s system.
Lastly, since Zluri immediately deletes user identities the moment a user is offboarded, it ensures that no unauthorized user or malicious actors can access offboarded user identities to infiltrate the organization’s system and application.
2: Synchronize Directories — Keeping Identity's Data Consistent Across All Database
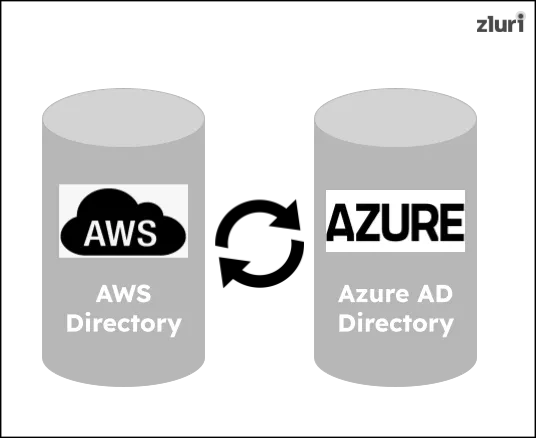
To align with this identity fabric guideline, you have to ensure that identity data remains consistent across all directories—whether on the cloud, on-prem, or spread across different providers like Azure, AWS, or Microsoft directories.
No matter where the identity data is stored, it should stay perfectly in sync with the rest of the database.
Suppose your organization is using both Azure AD and AWS directories to store identity data. If any changes are made to the user's identity (let's say the role is updated) and recorded in the Azure AD directory, then the same data should also be reflected in the AWS directory.
How is this going to help? By performing this practice, you can ensure that when identity providers (like Okta or AuthO) pull data from any of these directories for authentication purposes, they access the most up-to-date, accurate, and consistent identity data without getting confused about which data to use.
Suppose a user's role has been updated in one directory but hasn't synced with others. In that case, the IdP might retrieve incomplete information (as there will be confusion about which data to fetch), further affecting the accuracy of identity validation. However, syncing directories will eliminate this confusion, and your identity authentication process will be free from any inaccuracies.
But how do you actually synchronize directories? You can use tools like AWS directory services, Microsoft Azure AD connect, or Okta universal directory.
3: Govern Identities By Conducting Reviews
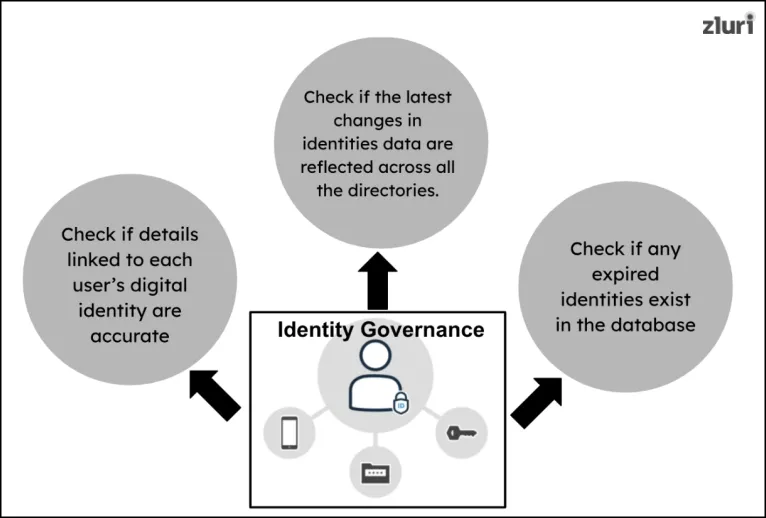
In this practice (outlined in the identity fabric framework), you need to thoroughly conduct a review (on a regular basis) to check whether the details linked to each user’s digital identity are accurate and up to date while ensuring no outdated or incorrect details slip through. You also need to cross-check whether the latest changes in identity data are reflected across all the directories.
That's not all; you need to perform an access review further to find expired digital identities that may linger around post-user departure. Now, to perform this type of review – you can opt for Zluri's access review solution. How will it help? It integrates with your directories and HRMs to list all inactive identities (you have to specify this action in the workflow) in a centralized dashboard. You can review the data, take bulk action, and remove them from your databases all at once.
Also read: 6 Best Approaches to Perform A User Access Review
This way, malicious actors won't be able to exploit them to gain unauthorized access and enter the organization's infrastructure. The best part is that Zluri generates a detailed user access review report that you can use as evidence to demonstrate to external certified auditors — that you implement practices that help maintain identity and data security. This way, you will be able to successfully obtain compliance certification.
4: Leverage Identity Threat Detection Mechanism
By using the identity threat detection (ITD) identity fabric method, you can track down hidden lurking cyber threats that can impact your identity security, such as — compromised credentials (e.g., of compromised endpoints), unusual login attempts from un-trusted location or device (these locations or devices won’t be mentioned in whitelist), unauthorized privilege escalation (sudden change in identities’ permission), abnormal accessing pattern (lateral movements across systems), and more.
Also Read: Top 8 Challenges of Cyber Security & How to Address Them
Once these vulnerabilities are discovered, you can generate an identity threat report (specifying all the detected cyber threats) and share it with security information and event management (SIEM) tools (like QRader or Splunk). These tools will then take corrective actions to close all the vulnerability points (by restricting the identity from access systems, updating the password, or replacing it with FIDOkeys).
Now you might ask – Doesn’t SIEM also help detect threats? It does, but not directly.
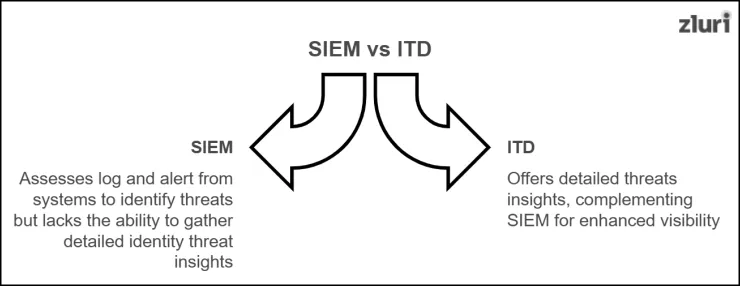
It gathers threat-related information by assessing logs and alerts from multiple systems or apps. Still, it does not have the algorithm to dive deep into and identify specific insights (like ITD). So, it is suggested that ITD be used with SIEM. This way, you will gain more visibility into threats lurking around and can effectively address them before they spiral out of control.
5: Implement a Risk-Based Authentication Method Rather Than Relying On MFA and 2FA
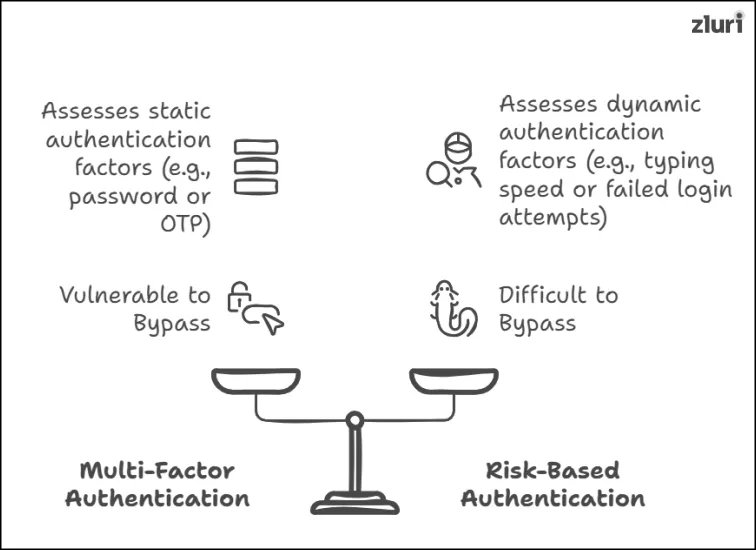
To ensure unauthorized users or attackers don’t even get a chance to enter systems or apps, identity providers use multi-factor or two-factor authentication [a combination of something that users know (password), something they have (OTP), and something they are (biometrics)] method to validate a user’s identity.
Also Read: Types of Authentication Methods
These are great adaptive authentication methods. However, the issue is that attackers (identity thieves) have evolved smarter. They leverage advanced technology to bypass these defenses (get hold of all these factors), fool the system, and enter your ecosystem.
Therefore, to outsmart the latest tech-savvy attackers, you have to level up your security game. How to do that? Configure your IdP to support a risk-based authentication method (a practice outlined in the identity fabric framework).
How is this helpful? Instead of just asking for passwords or OTPs, this authentication method focuses on validating user identity (whether they are who they claim to be) by assessing how the user interacts with the system, such as their typing speed, mouse movements, error rate (failed login attempts), devices they are using to enter, and activity history.
Suppose you have configured your IdP to support a risk-based authentication method. Now, if an attacker impersonates as a legitimate user and enters a password, IdP can spot the inconsistency in typing speed. This subtle detail – how quickly or slowly someone types – will help IdP spot the difference between real users and pretending ones. And once these attackers are detected, IdP will straightway deny their access or block them, preventing identity-based attacks.
This authentication method will make it far harder for attackers to bypass the defense.
Now that you are familiar with the strategies outlined in identity fabric, let’s proceed further and address one common misconception: Identity fabric and Converged identity are the same concept.
It’s understandable why this confusion occurred—after all, both identity fabric and converged identity aim to manage identities effectively. But while they do share a similar goal, they’re actually very different. Here’s how.
Identity Fabric vs Converged Identity: Clarifying The Confusion
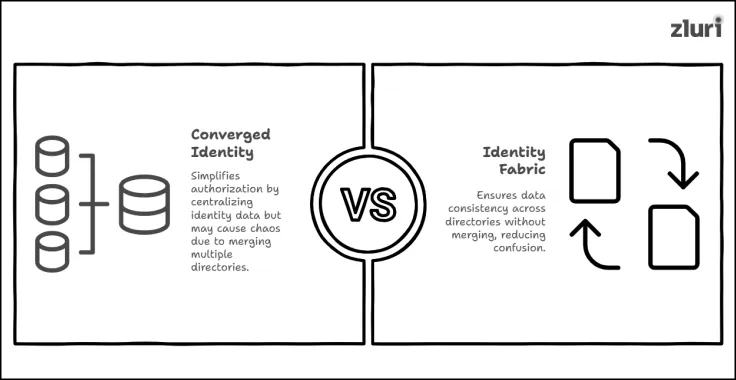
Converged identity focuses on combining/merging different identity stores/directories (where identity information is kept) into one central identity repository. The main idea behind this approach is to – simplify the process of authorizing (granting access rights) identities by eliminating the need to go through multiple directories to gather data. Plus, it provides IdP with a centralized identity responsibility (as a single source reference point) to authenticate users (so they don't get confused about which repository data to rely on).
But since most organizations have between 2-10 directories (more if it's an enterprise) that hold 1000s of identity data, merging them into one repository can create chaos and confusion. So, rather than forcing everything into one centralized location, identity fabric emphasizes synchronizing directories—ensuring identity data remains consistent across all the directories.
Never Trust, Always Verify: Implement Identity Fabric Guidelines To Create Zero-Trust Setup
Here's a fact—security risks (malware, zero-day exploits, data breaches, or insider threats; malicious actors will always be on a hunt to exploit vulnerability gaps) cannot be completely eradicated. They are inevitable.
Also Read: How IT Teams Can Prevent Insider Threats in Organization?
Although you can't eliminate them, but you can certainly outsmart them. You just need to follow the Never Trust, Always Verify (never trust any identity by default) principle (a preventive measure you cannot overlook).
Now, you might wonder,' How do you apply this principle?' The answer is simple: implement the strategies outlined in identity fabric guidelines. By incorporating identity fabric strategies such as using identity threat detection mechanisms, leveraging risk-based authentication methods, synchronizing directories, and others, you can lay a foundation for a zero-trust security setup.
For instance, by using the risk-based authentication method, you're not just verifying who someone says they are; you're checking how they act—analyzing their access behavioral patterns, typing rhythm, and even the devices they use (every finer detail), before granting the entry to the system. Don't worry; you are not trusting less; you are simply verifying more. Basically, you are creating a security checkpoint that does not allow attackers who impersonate a legitimate user (by stealing their identity) to enter the system and wreak havoc.
By performing such identity fabric practice, you thereby adhere to the never-trust, always-verify zero-trust principle and create a secure environment for your identities and data.
Now that you know how to build a zero-trust setup, it's time to create one for your organization. Do not delay! Breaches don't schedule their arrival—they can strike at any moment. So, create your defense system as soon as possible, and be prepared.
Also Read: Zero Trust Identity And Access Management








.svg)














