Security & Compliance
• 6 min read
Okta Vs. Cognito: Which IAM Tool To Choose?
25th September, 2023
SHARE ON:
Okta’s IAM is a secure, customizable, and drop-in solution to add authorization and authentication services to your apps. Meanwhile, Cognito’s IAM allows to add user sign-up and authentication to web apps and mobile.
However, both IAM tools have a few unique functionalities that you, as a CIO, can consider before deciding which IAM tool to opt for.
When deciding which of the two tools is better, you must thoroughly examine each platform's capabilities and how it caters to your IT team's needs.
Suppose a company requires an IAM tool offering a wide range of multi-factor authentication options. So which tool do you think will be more suitable for this scenario, Okta or Cognitio?
In this scenario, Okta will be an optimal choice to make as it offers a range of MFA options such as Okta Verify, SMS, voice, and more. While Cognito also supports MFA by allowing users to only verify their identity via SMS or a Time-based One-time Password (TOTP) generator, such as google authenticator.
This was just an example of how one feature can impact your decision-making process; it's important to note that choosing an IAM tool based solely on one functionality is not a comprehensive approach.
To make an informed decision, carefully considering each IAM tool's unique capabilities is crucial. By doing so, you can ensure that you select the IAM solution that is the most suitable for your IT team's specific requirements.
So, let's move on and compare Okta and Cognito based on different parameters to help you decide which IAM platform will be ideal.
Okta Vs. Cognito: Comparison Based On Different Parameters
Below are the parameters based on which we have closely compared the two IAM tools. By examining these parameters, you will be able to determine which tool offers the best functionalities to help your IT teams streamline the identity access management process.
1. Solution Categories
Okta is categorized as zero trust networking, cloud directory services, user provisioning and governance tools, single sign-on (SSO), and identity and access management (IAM). It is well suited for mid-market and large businesses where there are 51 and more employees.
On the other hand, Cognito is categorized as customer identity and access management (CIAM) and is a perfect fit for small businesses with 50 or fewer employees. 2
2. Identity Access Management
Okta’s IAM platform provides a universal directory, i.e., one directory for all your employees, devices, and SaaS apps. It offers a single view for multiple identity sources with AD (active directory) and LDAP (lightweight directory access protocol) directory integrations.
Furthermore, with Okta, your IT teams attain a flexible identity access management system that allows them to seamlessly manage employees' profiles and app access. Also, strengthen security by setting user access policies based on specific employee data such as employee's location, device, group member, IP, and more.
Connecting MFA factors with these policies will add to improving security. Also, your team can enforce LDAP and AD password policies and provide self-serve password resets for employees' ease, increasing efficiency.
Additionally, you can monitor all the access activities and obtain accurate reports, and if required, take action upon access by unauthorized users and secure the organization's crucial data.Whereas cognito’s IAM platform offers self-registration capabilities enabling your employees to sign-up themselves for the required application using their email address, phone number, or username. Also, they can view and update their profile information, including custom attributes, through the self-registration procedure.
It further reduces help desk calls with self-service solutions, such as password reset by SMS or email, allowing your IT teams to focus on core activities.
It doesn't stop here; Cognito offers a secure identity store (user pools), which helps securely store users' profile data, including federated users who sign in using external identity providers and users who join up directly.
This identity store is an API-based user repository that supports storage of up to 50 custom attributes per user, handles multiple data types, and enforces length and mutability restrictions. Further ensures that your employee selects the required attributes prior to completion of the sign-up process.
3. User Authentication
Okta’s IAM platform offers a multi-factor authentication solution that allows your team to secure employees' accounts from credential theft and fraud, keeping the right users in and unauthorized users out. This further helps protect sensitive data stored in customer-facing and enterprise apps.
Also, with Okta’s ThreatInsight, your IT team can automatically block suspicious IP addresses, allowing them to add an extra layer of security to protect your employee's identity and SaaS app data. It enables your team to create contextual access policies that examine risk factors, such as network, IP, device, and location, at every step of the authentication process.
Furthermore, Okta’s IAM offers single sign-on capabilities that allow your employees to authenticate themselves and access organizations' SaaS apps with a single set of credentials.
Additionally, it gives your IT teams one central place to view, manage, and secure all your employee's access. Okta's SSO solution can quickly integrate with several identity stores, including AD, LDAP, HR systems, and other third-party identity providers.Meanwhile, Cognito’s IAM platform offers your team a built-in and customizable UI that helps them to streamline the sign-up and sign-in process for your employees. Also, you can use iOS, JavaScript SDKs, and Android to add user sign-up and sign-in pages to your applications.
Furthermore, you can add an extra layer of security for your employee's identity by enabling MFA in the Cognito user pool. Your employees can verify their identities using SMS or TOTP (time-based one-time password) generators, such as Google Authenticator.
Also, with adaptive authentication, it helps in protecting your employee's accounts and improving their sign-in experience. How does it do that? Cognito identifies unusual sign-in behavior, such as attempts from new locations and devices; it assigns the action a risk score and gives your team the option of either asking your employees for more verification or blocking the sign-in request.
4. Security
Okta’s IAM platform allows your team to seamlessly assign the right applications to the right users and revoke access based on triggers from HR systems, IT resources like AD and LDAP, and more with the help of its automation and provisioning integration capabilities.
Furthermore, it provides a centralized view of users and their accounts, making it easier for your IT team to conduct audits and generate reports on which app access your employee has, which employees were recently deprovisioned, and more. Your team can also use APIs to programmatically extract data from your auditing tools without any hassle.On the other hand, Cognito’s IAM platform provides advanced bot detection features that help your IT teams detect and prevent the reuse of compromised credentials in real-time. Further, it prompts your employees to update their passwords when Amazon Cognito notices they have submitted credentials that have already been hacked somewhere else.
Also, Cognito complies with a variety of security and compliance standards, including HIPAA, ISO 9001, PCI DSS, ISO/IEC 27001, ISO/IEC 27017, and ISO/IEC 27018 standards.
After comparing the two IAM tools, you might have better understood which tool will meet your IT team's requirements. However, you should not restrict yourself to two tools. That's because there are other efficient tools available in the market. One such platform is Zluri which offers excellent functionalities to streamline the identity access management process and can be a better alternative to Okta and Cognito.
So, What is Zluri? What unique features does it offer? Here's a quick brief.
Zluri: The Best Stop For Simplifying Access Management
If you're looking to address the access management challenges your IT teams face, you can consider opting for an efficient platform like Zluri. But why Zluri? It ensures that your IT admin grants the right level of access to required applications to the authorized person at the right time. Zluri offers a centralized platform for managing user identities and access policies, controlling authentication and authorization processes, and keeping track of user behavior and compliance.
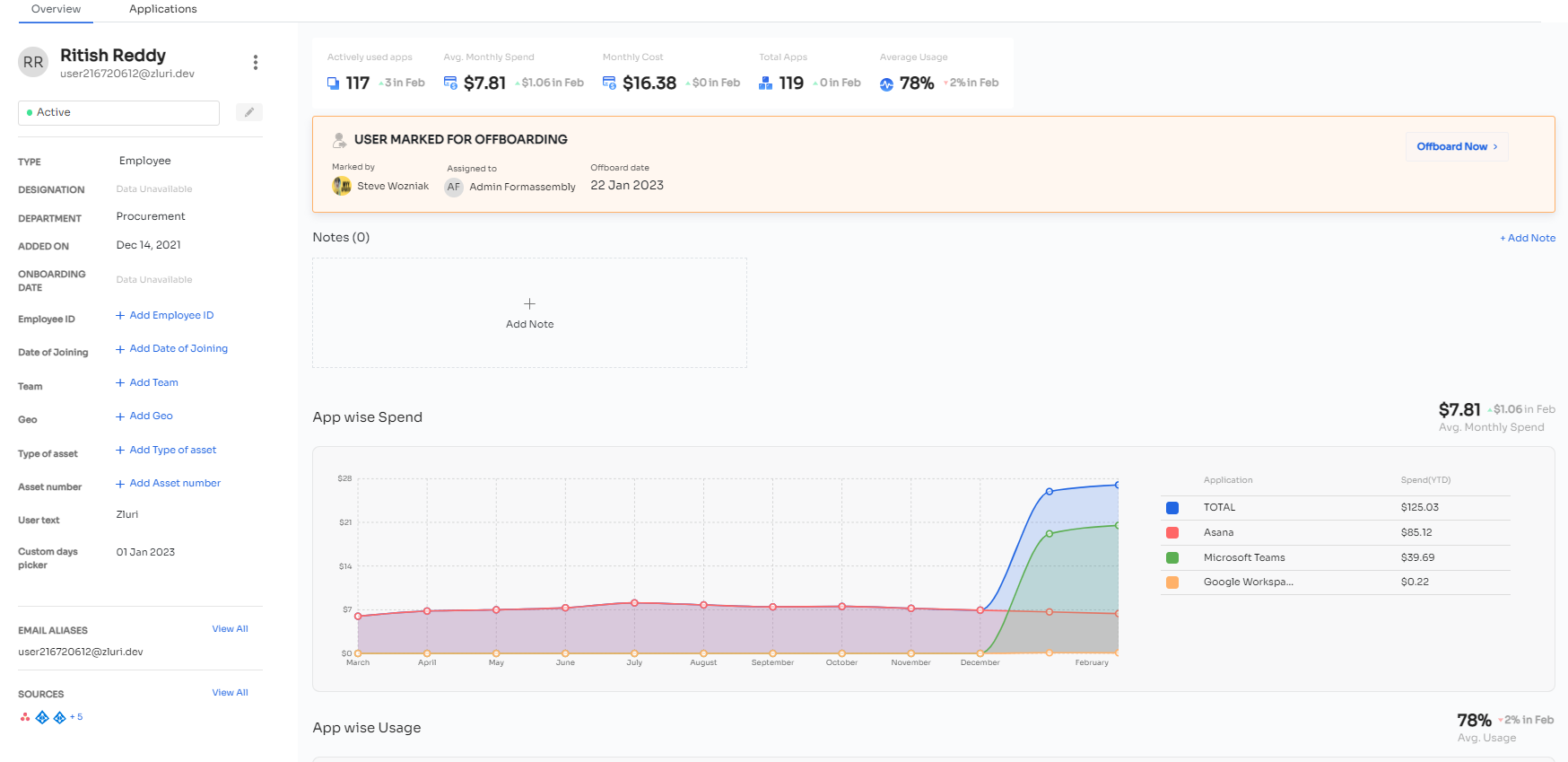
For instance, when a new hire joins the company, Zluri binds that employee's data to their digital identity so that, during provisioning, your IT admins can seamlessly confirm that employee's identification and grant them the right level of access to SaaS apps and data. Additionally, this aids in preventing identity theft and protecting important data from security breaches.
Apart from that, it offers single-sign-on and multi-factor authentication features, enabling your employees to authenticate themselves with a single set of credentials, and with a single click. This allows your employees to access the required app without any hassle and also reduces password fatigue.
However, it is a task to monitor the entire management process. But not with Zluri, your team can monitor each employee's access activities and level of permission they have from a single dashboard, including which applications they have access to, login & logout timings, level of permissions allocated to them, and more.
Further, this enables your IT team to identify suspicious activities such as unauthorized access attempts so that they can take immediate actions or security measures to protect sensitive app data from data breaches or cyberattacks.
It doesn't stop here; Zluri enables your IT admins to grant, modify, and revoke access securely and efficiently. Further, by integrating with the HR system, it fetches the employee data and updates in Zluri's dashboard. Your IT admins can utilize this data to verify employees' identities upon onboarding, mid-lifecycle change, and offboarding.
Additionally, it conducts audits on a timely basis and generates curated reports such as reports on employee and application activity, including group creation, login, and logout events, and changes to user profiles. Also, it generates security event reports such as failed login attempts, suspicious login attempts, and changes to security policies which helps your IT team prevent security breaches.
Now you know how Zluri can be a game changing solution for your team to manage identity access. So why wait? Book a demo now and see for yourself how it caters to your IT team's needs.
Related Blogs
See More
Subscribe to our Newsletter
Get updates in your inbox
