IT Teams
• 5 min read
Okta Vs. Duo Security: Which IAM Tool To Choose?
2nd August, 2023
SHARE ON:
Okta provides IAM features to help your IT admins address identity and security challenges. Meanwhile, Duo Security’s IAM feature provides security to users with complete device visibility, comprehensive coverage, and initiative authentication.
However, they also offer other key features that you can look into before choosing the suitable IAM tool for your IT admins.
To find the best one among the two, you as a CIO need to thoroughly look into each tool's capabilities and how it caters to your IT admin's needs.
Let's assume, a small business requires an IAM tool with advanced authentication features to secure sensitive SaaS app data. So which tool do you think will be more apt for this scenario, Okta or Duo Security?
Now in this scenario, Duo security can be a better choice as it caters to small-sized businesses and offers a wide range of authentication functionalities, helping them protect sensitive app data against security threats and cyberattacks. Whereas, Okta is a better fit for mid-market whose primary goal is to control user access and management.
This was just an overview of how features can bring a difference in your decision-making process. However, you cannot decide which tool to choose based solely on one functionality. You need to carefully consider each of their distinctive features to select the best one.
So, let's move on and compare both tools based on different parameters to help you decide which IAM platform will best meet the requirements of your IT team.
Comparison Based On Different Parameters: Which IAM Tool Is Better?
Listed below are a few key parameters based on which we have closely compared the two. This will help you decide which tool offers better functionalities and can help your team streamline the identity access management process.
1. Solution Categories
Okta is categorized as Cloud Directory Services, Identity and Access Management (IAM), and User Provisioning and Governance Tools. This tool is well-suited for both small and large-sized businesses.
Meanwhile, Duo Security is categorized as Cloud File Security, Cloud Data Security, Risk-Based Authentication (RBA), Multi-Factor Authentication (MFA), and Passwordless Authentication. This tool perfectly fits mid-sized businesses with 51 to 1000 employees
2. Identity access management
Okta verifies identity by allowing employees to self-verify it with document-based or knowledge-based proofs. Document-based proof includes any government-verified document, such as a driver's license, whereas knowledge-based proofs include employees answering specific questions to verify their identity.
Furthermore, Okta enables your IT admin to verify employees' identities through SSO security and integrations. This helps them allocate the right access level to authorized users, preventing potential security breaches.On the other hand, Duo Security performs two-factor authentication to verify identity, in which employees have to perform two methods to verify themselves. These elements of their zero-trust security model guard against security risks that target accounts and passwords.
To protect its users from security threats, including keylogging, stolen passwords, brute-force attacks, and phishing efforts, Okta allows your IT admins to implement its 2-factor authentication. Duo's 2FA platform combines the knowledge factor of identity verification with the possession factor of authentication, typically a hardware device like a security token or mobile device used in conjunction with a software token.
3. Zero Trust Strategy
Okta offers two zero-trust security solutions, i.e., workforce identity and customer identity. Workforce identity provides identity access for the work ecosystem that to help your IT admin protect crucial app data by granting authorized access to employees. Whereas customer identity offers seamless and secure access to your clients and helps create frictionless registration and login for your app.
Key Differentiators
Okta provides 7000 plus pre-built integrations, including Slack, Box, Workday, Zendesk, Amazon Web Services, DocuSign, Cerner, and Confluence
With the help of Okta's integration, your team can securely connect cloud-based SSO to cloud apps
Adaptive MFA enables your IT admin to protect SaaS apps and employee accounts from potential security risks like credential theft
With centralized access management, you can incorporate adaptive MFA and cloud-based SSO into on-premises apps
You can create seamless and secure consumer interactions with authentication as a service
Provisioning can be automated with lifecycle management features
Duo Security offers a zero-trust solution designed to secure apps, devices, and users. It is user-friendly and suitable for organizations that require sensitive data protection capabilities.
Key Differentiators
Credential threat risks can be minimized by permitting employees to securely access SaaS applications with SSO.
Employees' identities can be verified at every access attempt and at regular intervals with the help of MFA.
Your team can gain a consolidated view of each device used to access apps, allowing them to track whether the devices pose any threat to data.
It enforces adaptive security policies to limit the exposure of crucial app data to as few devices and users as possible.
With Duo Security's remote access capabilities, your team can ensure that only required permission is granted to employees to access the organization's SaaS applications from anywhere.
This tool provides you with 24/7 customer support via call, email, and chat.
4. Security analytics and monitoring feature
Okta's security analytics will provide you with complete visibility into the organizations’ SaaS landscape. Further, its monitoring feature helps your team to identify suspicious activities, such as unauthorized access attempts, to take immediate action against security breaches.
Additionally, Okta's HealthInsight features audits help strengthen security posture by enforcing security policies, and the ThreatInsight functionality offers information about IP threats logged or blocked within the previous 7 days. Combining these features can help your IT admin generate reports on unauthorized activity. Also, Okta integrates with other security analytics applications helping contribute to security visibility.Meanwhile, Duo Security allows your IT team to use historical data to build a baseline of device behavior with the help of analysis and modeling. Based on baseline behavior, it scores deviations. This monitoring functionality will enable your teams to assess each component's risk effects and creates threat models to evaluate them.
5. Pricing Structure & Rating
Okta is available in three packages: "single sign on," which is for $2 per user per month, "single sign on plus," starting at $4/user per month; and "enterprise," at $8/user per month. You have to contact them for "enterprise plus" pricing details, and no free trial is available.
Whereas, Duo Security offers four packages: "Duo Free," which is free of cost with limited features, "Duo MFA," starting at $3 per user per month, "Duo Access," at $6/user/month, and "Duo Beyond," at $9/user per month. Unlike Okta, it offers a free trial of 30 days.
Customer Rating
Okta- G2: 4.5/5, Capterra: 4.7/5
Duo Security- G2: 4.5/5, Capterra: 4.7/5
After closely comparing the two, you might know which tool will be better for your IT team's requirements. Although, you shouldn't end your search for the IAM tool at this point. That’s because there are other efficient tools available in the market. One such platform is Zluri which offers excellent functionalities to streamline the identity access management process and can be a better alternative to Okta and Duo Security.
So, What is Zluri? What unique features does it offer? Here's a quick brief.
Zluri: All-In-One Solution To Help Your IT Teams With Access Management
To mitigate all the access management challenges that your IT teams come across, you can consider opting for an efficient platform like Zluri. But why Zluri? Zluri provides a centralized platform for managing user identities and access policies, enforcing authentication and authorization controls, and monitoring user activity and compliance.
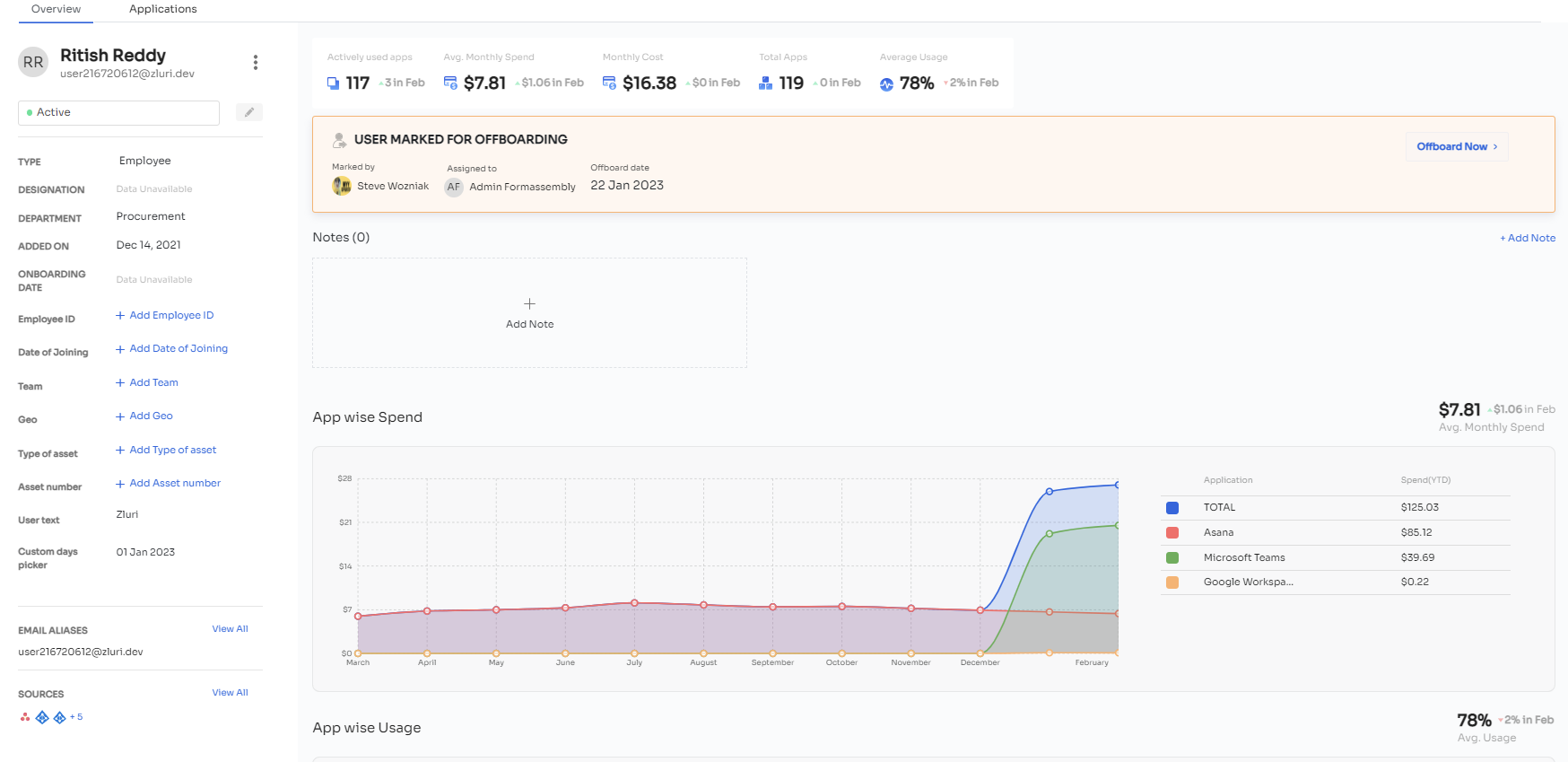
For example, whenever a new employee joins the organization, Zluri ties the employee's data with digital identity so that while provisioning, your IT admins can quickly verify their identity and grant them the required level of access to applications and data. Further, this also helps prevent identity theft and secure crucial data for security breaches.
Also, it provides SSO and MFA features, allowing employees to verify themselves with a single set of credentials, and with one click, employees can access required applications, reducing password fatigue.
The best part is you can monitor all the employee access activities and permissions from a single dashboard, including which applications they have access to, login & logout timings, level of permissions allocated to them, and more. Enabling you to identify suspicious activities such as unauthorized access attempts so that you can take immediate actions or security measures to secure crucial app data from the data breach.
Zluri doesn't stop here, it enables your IT admins to grant, modify, and revoke access efficiently and securely. It integrates with the HR system that helps update employee data in Zluri, and IT admins can utilize this data to verify employees' identities upon onboarding, mid-lifecycle change, and offboarding.
Additionally, it conducts periodic audits and generates curated reports such as reports on employee and application activity, including login and logout events, group creation, and changes to user profiles. Also, security event reports such as suspicious login attempts, failed login attempts, and changes to security policies. This enables your IT teams to streamline the identity access management process.
Zluri has other capabilities as well, such as ITAM, ITSM, ULM, etc. which you can look into by booking a demo now.
Related Blogs
See More
Subscribe to our Newsletter
Get updates in your inbox
