IT Teams
• 12 min read
Top 11 Identity Server Alternatives & Competitors In 2024
22nd January, 2024
SHARE ON:
When it comes to streamlining access management, IT teams often turn to identity access management (IAM) solutions. One such solution is Identity Server offering a range of robust features to bolster access control.
However, it's crucial to explore other options within the IAM landscape. This helps you find the ideal solution for your organization's access control challenges.
Let’s explore some notable Identity Server alternatives and competitors, offering valuable choices for securing access management.
The plays a vital role in safeguarding data and minimizing the risks associated with identity management within the organization. It has earned the trust of its valued clients by providing a wide range of secure and reliable functions. However, its higher costs may prompt you to explore more cost-effective alternatives.
In this article, we will take an in-depth look at the Identity Server alternatives, including comparing their pros, cons, and customer ratings. However, before we proceed, let's look at the Identity Server and its limitations. This insight will assist you in choosing the most suitable tool to meet your needs.
Identity Server (IAM): An Overview
IdentityServer4 offers a comprehensive set of features designed to enhance the capabilities of your applications. From centralized authentication to single sign-on (SSO) and robust access control, IS4 provides a versatile toolkit for modern identity management. Let's explore the key additional features that make IdentityServer4 a valuable asset for your projects:
Authentication as a Service: IdentityServer4 serves as a centralized authentication service for all your applications, whether they are web-based, native, mobile, or services. It is an officially certified implementation of OpenID Connect, ensuring a secure and standardized authentication process.
Single Sign-On (SSO): Enjoy the convenience of single sign-on and sign-out across various application types. IdentityServer4 streamlines the user experience by allowing seamless access to multiple applications with a single login.
Access Control for APIs: IS4 issues access tokens for APIs, catering to a wide range of client types, including server-to-server communication, web applications, single-page applications (SPAs), and native/mobile applications. This ensures robust security and access control for your APIs.
Federation Gateway: IdentityServer4 supports external identity providers like Azure Active Directory, Google, and Facebook, enabling easy integration with trusted identity sources.
Customization: As a flexible framework, IdentityServer3 active directory offers extensive customization options. You can write code and adapt the system to meet your specific requirements, ensuring a tailored solution for your scenarios.
Open Source: IdentityServer4 is an open-source solution, backed by comprehensive documentation and a thriving community of developers and users. This open nature fosters innovation and collaborative support.
With IdentityServer4, you can elevate the security and usability of your applications while maintaining the flexibility to tailor the identity management process to your unique needs.
Drawbacks Of Identity Server
While Identity Server offers a robust solution for managing authentication and authorization in various applications, it's essential to be aware of its drawbacks, which may affect your decision when considering the IdentityServer4 alternatives. Some of the key drawbacks include:
Cost and Licensing: One significant drawback of the Identity Server is their cost. Depending on the scale and specific requirements of an organization, the licensing fees can be substantial. This can be a limiting factor, especially for small businesses or startups with tight budgets, making it less accessible for those looking for cost-effective solutions.
Complex Setup and Configuration: Setting up and configuring Identity Server can be complex and time-consuming, particularly for users who are not well-versed in identity and access management systems. The process requires a good understanding of the system's architecture, configuration options, and integration requirements, which can challenge less experienced administrators.
Resource Intensive: Identity Server can be resource-intensive, especially in terms of memory and processing power. This can impact the performance of other applications and services running on the same server. Efficient resource management and appropriate hardware provisioning are crucial to ensure smooth operation without performance degradation.
Steep Learning Curve: Implementing and utilizing an Identity Server open source effectively requires a certain level of expertise. The learning curve can be steep, especially for organizations new to identity and access management capabilities & solutions. Training and investment in acquiring the necessary skills and knowledge are often needed to optimize the use of the Identity Server.
Limited Customer Support: Some users have reported challenges with customer support for the Identity Server. Response times and issue resolution might not meet the expectations of all users. Insufficient customer support can be frustrating, especially during critical situations or when immediate assistance is needed.
Customization Complexity: While Identity Server offers a high degree of customization, tailoring it to specific organizational needs can be complex and requires in-depth system knowledge. Customizing features and functionalities may demand substantial development effort and expertise.
It's crucial for organizations to weigh these drawbacks against the benefits and their specific requirements when considering Identity Server alternatives. We will explore top Identity Server alternatives, empowering IT administrators to select robust Identity and Access Management (IAM) solutions for their organizations.
List Of 11 Best Identity Server Alternatives To Try In 2024
Below is a compilation of the top 11 Identity Server alternatives and competitors for identity and access management. Each of these alternatives comes with distinct features and capabilities, empowering you to select the IAM solution that aligns most effectively with your specific security and access management requirements.
1. Zluri
Zluri offers an extensive access management platform designed to effortlessly oversee user identities and access policies. It seamlessly integrates with a range of single sign-on (SSO) tools, excelling in enforcing stringent authentication and authorization controls while continuously monitoring user activities to ensure compliance.
This integrated approach grants you the ability to swiftly detect any suspicious activities, such as unauthorized access, in real-time. In case of such incidents, you can take immediate action to safeguard your invaluable application data.

Zluri's seamless integration with single sign-on (SSO) effortlessly merges new employees' data with their digital identity. This robust feature streamlines the onboarding process, enabling your IT administrators to promptly verify their identity and allocate precise access permissions for applications and data.
Beyond the convenience it offers, this additional layer of security acts as a bulwark against identity theft and safeguards your critical data, bolstering protection against potential security breaches.
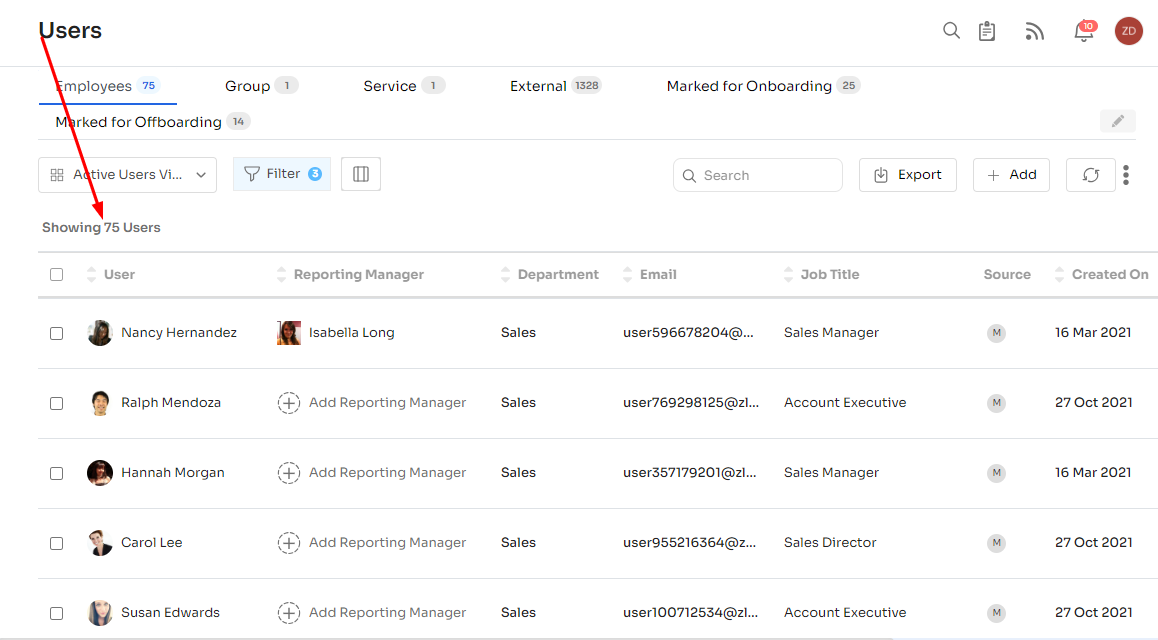
What truly sets Zluri apart is its ability to centralize every employee's access data within a unified platform. From this central hub, you gain comprehensive insights into your team's application access, log-in and logout activities, and permission levels. In short, Zluri ensures that the right employees have the appropriate access to the correct tools and resources.
Key Highlights of Zluri's Advanced Features:
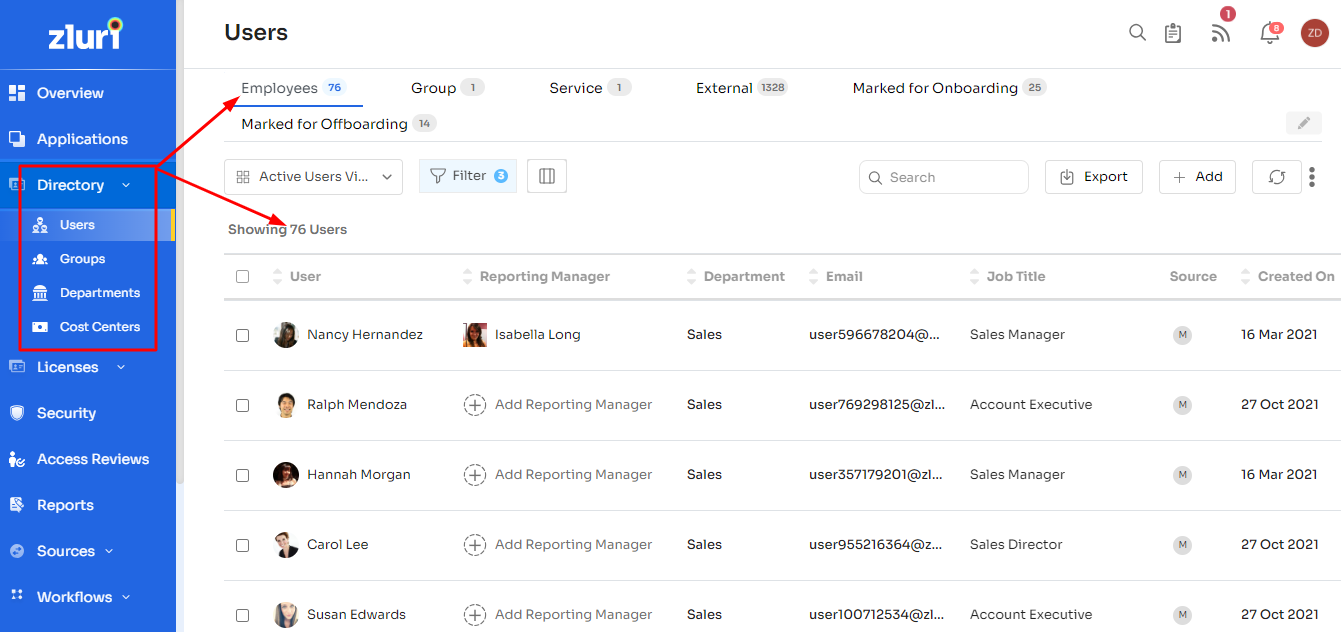
Centralized Access Control Management: Zluri's platform provides a unified, bird's-eye view of your organization's access control landscape. Effortlessly manage and govern team members' access to a variety of applications via a single, intuitive dashboard.
![Centralized Access Control Management]()
Seamless HR Integration: Zluri seamlessly integrates with your HR system, ensuring that employee information remains up-to-date. This integration plays a pivotal role in verifying employee identities during various phases, including onboarding, updates during employment, and user offboarding, thereby ensuring a continuous and secure Identity and Access Management (IAM) process.
![HR Integration]()
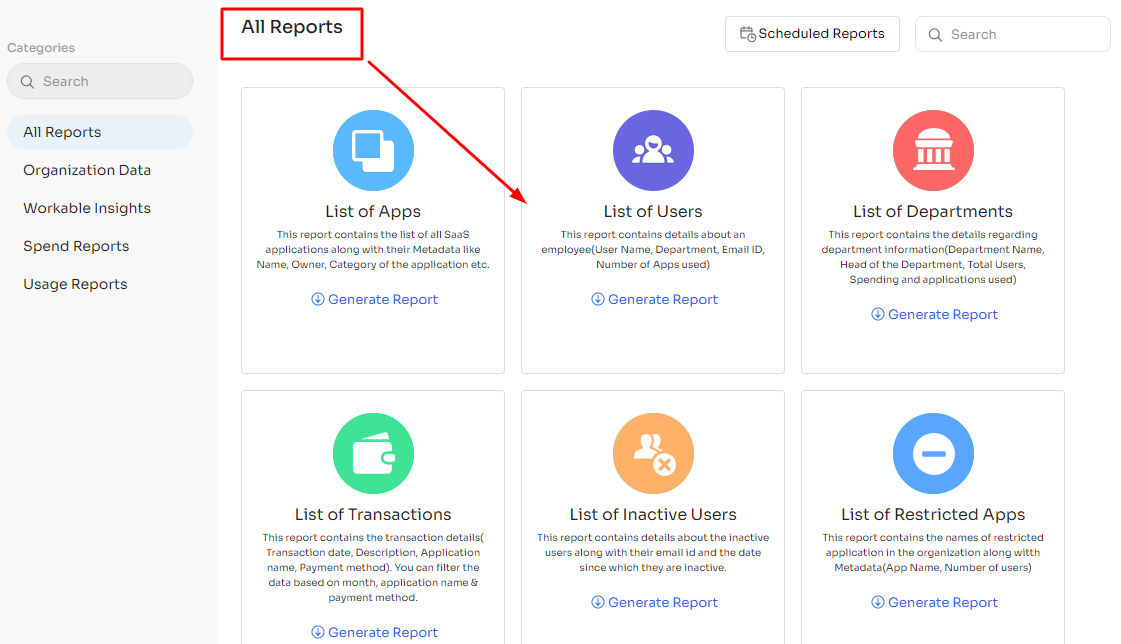
Regular Audits and Comprehensive Reporting: Zluri conducts routine audits and generates detailed reports. These reports provide invaluable insights into employee and application activities, covering events such as logins, logouts, group creation, department management, and user profile modifications.
![reports]()
Enhanced Security and Compliance Focus: Security and compliance are at the core of Zluri's mission. The platform implements robust security measures to safeguard sensitive data and simplify compliance with relevant laws and regulations. It ensures that all access controls and user identity management adhere to industry best practices, enabling your organization to meet regulatory compliance requirements while fortifying sensitive data against potential security threats.
Pros
Zluri provides a user-friendly and centralized platform for managing access to various applications and resources. This simplifies the process of granting and revoking access rights, reducing administrative overhead and improving security.
It helps organizations maintain compliance with data protection regulations and enhance overall security by ensuring that only authorized individuals have access to sensitive data and applications.
Cons
Zluri may not be the most suitable option for smaller organizations with fewer employees, as its features are primarily designed for large or mid-sized companies.
Customer Rating
G2: 4.9/5
Capterra: 4.9/5
2. Rippling
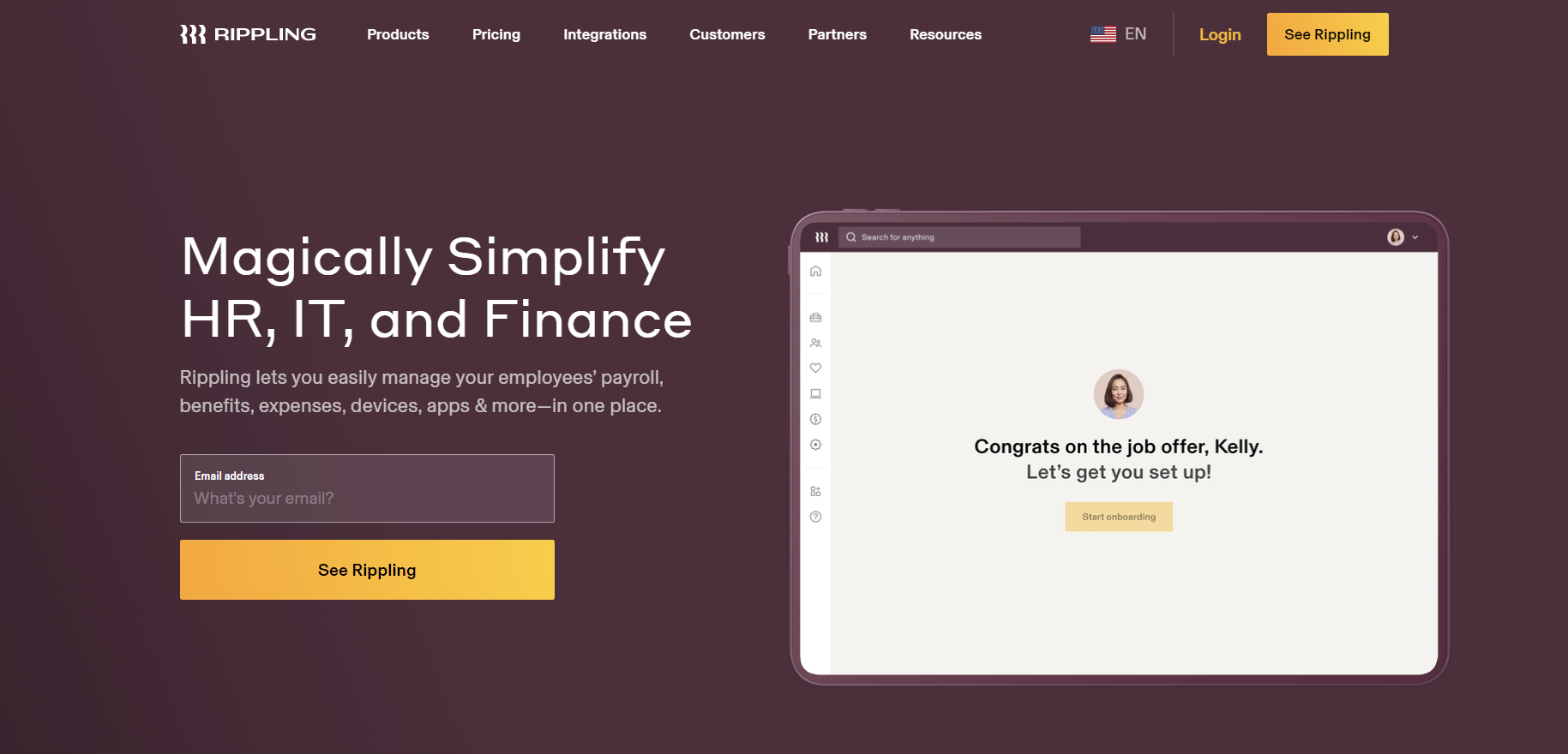
Rippling is built on the first Unified Workforce Platform, which has all the apps you need to run a global workforce without any trouble. Its cloud-based directory platform offers SSO capability, allowing employees to access all applications using a central dashboard.
It makes the IT department and its employees more productive and keeps applications safe from cyber threats. It puts all the information and systems about employees in one place and automates the tasks that used to be done by hand.
With Rippling's advanced authentication server, you have command over which application and data your team is authorized to manage.
Pros
The platform is accessible to a wide range of users, including those with varying levels of technical expertise. It minimizes technical jargon and complexities, ensuring that users can interact with it comfortably.
The platform provides clear, step-by-step instructions or a guided setup process. This simplifies the initial deployment, making it accessible to users who may not have advanced technical skills.
Some user-friendly platforms come with preconfigured settings or templates, reducing the need for extensive customization during setup. Users can choose from these options to get started quickly.
Cons
Its primary limitation lies in the absence of integration with Okta Single Sign-On (SSO), potentially hindering users from accessing the platform seamlessly using their Okta credentials. Consequently, this could result in a fragmented login experience, necessitating users to manage additional sets of login information.
The quality of customer service can significantly impact the overall user experience. Users who encounter difficulties or receive subpar support may become dissatisfied with the platform, affecting their perception of its value.
Customer Rating
Capterra: 4.9/5
3. Okta
Okta Workforce Identity presents one of most powerful Identity Server alternatives: Single Sign-On (SSO) solution meticulously crafted to streamline user access and authentication across your organization's array of applications and services. Through Okta SSO, your team can relish a smooth and secure login experience, sparing them the ordeal of managing many user passwords.
Okta SSO further streamlines user lifecycle management by automating provisioning and deprovisioning user accounts. Whether employees are onboarded or offboarded, Okta takes care of aligning access to applications accordingly, significantly diminishing administrative burdens.
Pros
Okta SSO provides passwordless authentication methods, such as biometrics and one-time passcodes, eliminating the reliance on conventional password requirements and lowering the potential for password-related vulnerabilities.
Okta prioritizes user convenience by offering a centralized dashboard or portal where users can easily access and launch the needed applications. This dashboard simplifies navigation and saves time for employees, enhancing their overall productivity.
Cons
The system may not allow users or administrators to tailor it to specific organizational needs. This lack of customization options can hinder fine-tuning settings or features according to unique requirements.
Frequent session timeouts can lead to user frustration. Users may perceive it as an inconvenience, especially if they are frequently interrupted by sign-in prompts throughout the day.
Customer Rating
Capterra: 4.7/5
4. OneLogin
One Login is an access management software platform that manages identities and access that companies of any size can use. It offers a safe, one-click onboarding and offboarding procedure for users.
For instance, when a new user is added to OneLogin, access to the necessary apps may be provided to that user automatically, depending on the role they play and the responsibilities they have.
Multi-factor authentication is one of the ways in which One Login provides layered security to the individual and the organization.
Pros
One Login allows IT admins to manage user accounts, access permissions, and security policies across multiple platforms and systems from a single, unified interface. This streamlines the complex task of overseeing user access and permissions for different applications and services.
It provides organizations with the flexibility to customize access control policies to align with their specific needs and security requirements. Administrators can define access rules and permissions that suit the organization's unique workflow.
Cons
Frequent password resets can increase the workload for IT support and helpdesk teams. Users who struggle with password resets may require assistance, diverting IT resources away from other critical tasks and support requests.
Frequent session timeouts can interrupt users' work. When users are logged out unexpectedly, they must log back in and may lose unsaved work or disrupt their focus and productivity.
Customer Rating
Capterra: 4.7/5
5. JumpCloud Directory Platform
Jumpcloud is an open directory platform that allows users to access any resource from any device in any location safely and securely. JumpCloud's goal is to "Make Work Happen" by facilitating quick and safe access to the technological resources of businesses from any computer or mobile device, regardless of location.
The JumpCloud Directory Platform provides a single, cloud-based solution to IT, MSPs, VARs/Distributors, security operations, and DevOps to control and manage employee identities, as well as the devices used by those employees, and using Zero Trust principles.
Pros
JumpCloud provides various customization options, empowering organizations to personalize the tool according to their requirements and preferences. This adaptability greatly enhances its suitability for various unique use cases.
Furthermore, the platform delivers efficient group-based access control capabilities, streamlining the administration of user access permissions and simplifying the enforcement of security policies.
Cons
JumpCloud has one notable drawback: it lacks mobile device management (MDM) capabilities for smartphones and tablets, vital for maintaining control and security over mobile devices in an organizational setting.
However, one drawback with JumpCloud pertains to its reporting capabilities. The current set of reporting features within the admin portal is somewhat limited, hindering the efficient tracking and in-depth analysis of user access and security data.
Customer Rating
Capterra: 4.7/5
6. SailPoint
Sailpoint is a software program for managing identities and access that may either be installed locally, on the cloud, or in a physical data center. Through the use of identity governance and automated user provisioning, you are able to give employees access to various apps. It enables you to prevent access breaches, ensuring that the entire security is managed.
It offers you total insight into all access across your business and replaces manual procedures with automated workflows in order to distribute, manage, and protect access.
Pros
This software product excels in providing exceptionally responsive and supportive customer service, guaranteeing swift assistance and effective resolution of users' inquiries and concerns.
The platform acts as a unified gateway, allowing users to access multiple software applications from one central hub, streamlining access management. Users can easily navigate and launch various software tools from this centralized location, reducing the need for multiple login credentials and interfaces.
Cons
The documentation falls short in terms of comprehensiveness, as it does not provide a thorough and detailed coverage of the data, instructions, or guidance that users may require. Thus, it lacks the depth needed to fully address and support the user's needs, potentially leaving gaps in understanding and usability.
Customer Rating
Capterra: 4.2/5
7. Ping Identity
Ping Identity provides a robust platform for identity and access management aimed at fortifying security and simplifying access to networks, APIs, cloud-based applications, and on-premises software for businesses. Powered by advanced AI technology, this platform takes a proactive stance in detecting and addressing suspicious activities, all while upholding compliance with industry regulations.
This versatile tool empowers organizations to establish comprehensive access policies to protect valuable resources. It fosters smooth integration, synchronization, and data archival from various sources, unifying this data into a centralized repository for streamlined and effective management.
Pros
Ping Identity offers a user-friendly self-service portal with a streamlined interface, making registration and authentication requests effortless. This streamlines the onboarding process and enhances user productivity.
You can easily assign and update resource ownership information, thereby improving control and transparency in resource allocation throughout the organization.
Cons
The tool's limited adaptability in directly integrating custom attributes may pose challenges for organizations seeking personalized customizations.
Although Ping Identity provides robust deployment options, it falls slightly behind certain competitors when it comes to offering highly specialized deployment choices. Businesses with specific and advanced deployment requirements might discover more suitable alternatives elsewhere.
Customer ratings
G2: 4.4/5
8. Auth0
Auth0 stands as a strong IAM Solution, providing a powerful identity and access management service solution that prioritizes the security of organizations' application access while safeguarding user data privacy. This unwavering dedication empowers users to concentrate on their tasks, leading to improved productivity.
Auth0 streamlines authentication through a multitude of features, including unified login, single sign-on, multi-factor authentication, two-factor authentication, and more. These functionalities streamline access management and enhance the security of user interactions with applications, positioning Auth0 as a compelling option in the field of identity and access management.
Pros
Auth0 simplifies the process of searching, updating, and managing access data for diverse users, streamlining administrative tasks and improving operational efficiency.
Auth0 provides data source connectors that enable seamless connections with both on-premises and cloud-based IAM providers, ensuring IT team's flexibility in integrating and handling user data.
Cons
Your team may encounter challenges when attempting to change their email addresses if needed, potentially leading to user experience issues and support requests.
Auth0 primarily concentrates on cloud-based identity solutions, which may not align perfectly with organizations heavily dependent on on-premises applications and systems.
Customer ratings
G2: 4.3/5
9. CyberArk Identity
The CyberArk Workforce Identity platform represents an advanced solution tailored to simplify and fortify user access across an organization's comprehensive application ecosystem, encompassing cloud-based, mobile, and legacy platforms. It guarantees a seamless and exceptionally secure user sign-in and sign-out experience, with a particular focus on the critical phases of user onboarding and offboarding. The platform diligently considers multiple risk factors to enhance overall security.
To further elevate security measures, the CyberArk adaptive multi-factor authentication assumes a pivotal role in safeguarding your systems. By mandating that users provide a range of authentication methods before gaining access to applications, it stands as a robust defense mechanism against cyberattacks targeting compromised credentials.
Pros
CyberArk Workforce Identity provides a range of capabilities, such as server access management and role-based authentication, ensuring adaptability to meet various access management needs.
Its SSO-enabled identity services simplify credential management and enhance user convenience by allowing users to use one set of login credentials across various applications and services, making their experience more efficient and user-friendly.
Cons
While CyberArk Identity's smartphone permissions offer utility, they can give rise to privacy apprehensions. The absence of fine-grained authorization controls might pose limitations, potentially exposing sensitive data, which could be a concern for active users of the platform. This encompasses core identity management and its intricate facets.
The absence of support for SAML response encryption is a drawback, as it hinders the implementation of advanced capabilities needed for securing sensitive data during authentication processes and data exchanges. This encryption deficiency becomes particularly crucial when striving to ensure secure services.
Customer ratings
G2: 4.4/5
10. RSA SecurID
The RSA SecurID Suite provides a comprehensive identity and access management solution meticulously crafted to offer businesses the flexibility to customize access privileges for a diverse user base, including employees, associates, customers, and freelancers. This solution seamlessly spans both cloud and on-premise infrastructures, ensuring secure access to critical applications and sensitive data.
By harnessing cutting-edge machine learning capabilities, IT teams can implement multi - factor authentication using various methods, including push notifications, biometrics, one-time passwords (OTPs), and FIDO tokens.
Furthermore, this centralized platform simplifies administrative tasks, facilitating the automation of essential processes such as tracking, certification, notification, authorization, and compliance management.
Pros
The RSA SecurID Suite presents an assurance-level feature enabling organizations to deploy risk-based authentication methods. This elevates security by adapting authentication techniques according to the assessed risk level of each login attempt.
Additionally, the system automatically generates a new token upon expiration of the old one. This functionality eliminates the need for manual password re-entry to obtain a new token, enhancing both user convenience and security.
Cons
A potential drawback is that certain users may face challenges when resetting their passwords. It is crucial to offer sufficient support and resources to assist users who may need help with this process in order to ensure a seamless user experience.
While the tool boasts robust user provisioning capabilities, there is room for improvement in terms of user-friendliness. Simplifying the user provisioning process can lower the learning curve for administrators and enhance overall efficiency in user access management.
Customer ratings
G2: 4.8/5
11. Duo Security
Duo Security stands at the forefront of Identity Server alternatives, delivering a comprehensive suite of tools to bolster security and simplify access control for organizations.
Their prominent features encompass multi-factor authentication (MFA) and two-factor authentication (2FA) applications and access tools, which have become indispensable assets for organizations seeking to fortify their security measures. These user-friendly and intuitive solutions enhance your organization's security preparedness while streamlining the intricacies of access management, authentication reinforcement, and device oversight.
Duo's offering extends to include single sign-on functionality, easing user logins by providing access to multiple systems and applications. It seamlessly integrates with various systems, operates in the cloud to minimize on-premises setup, offers compliance support, and provides user self-service portal, making it a comprehensive solution for organizations looking to enhance both security and operational efficiency.
Pros
Duo Security places a significant emphasis on strengthening security without compromising user convenience, enabling organizations to reinforce their access security and fulfill compliance adherence.
Duo Security offers a straightforward setup process, enabling IT teams to enhance their security measures without the need for significant IT resources or specialized expertise.
Cons
Duo Security might pose difficulties for iOS users, especially concerning the reliable reception of push notifications. This could potentially disrupt the smooth verification process, resulting in delays or inconvenience during login attempts.
Additionally, for some users, the migration of their Duo Security authentication setup to a new device might prove challenging. This procedure can be cumbersome and may necessitate extra support or guidance, potentially leading to usability issues.
Customer ratings
G2: 4.5/5
About the author
Tathagata is a Technical Content Writer with 4+ of experience in the SaaS industry. He has a keen eye for research and understanding macro trends in the SaaS & AI-based technology space. He has worked across several marketing & strategy roles in various domains like banking, e-commerce, and education sectors. In his leisure time, Tathagata is a full-time PC gamer.
Related Blogs
See More
Subscribe to our Newsletter
Get updates in your inbox