Security & Compliance
• 11 min read
10 Best Ping Identity Competitors & Alternatives in 2024
14th September, 2022
SHARE ON:
Are you an IT manager aiming to enhance your company's IT security? Look no further than Ping Identity, a cloud-based solution that enhances security in several ways. It simplifies your experience with single sign-on (SSO), strengthens security with multi-factor authentication (MFA), and streamlines directory management.
However, as an IT manager, it's crucial to remain flexible. Your organization's needs may evolve, and alternative solutions exist beyond Ping Identity. Take the opportunity to explore various Ping Identity alternatives and find the one that aligns best with your evolving requirements.
Ping Identity acts as your partner in achieving top-notch Zero Trust identity security. It offers a user-friendly experience while equipping your IT team with the scalability, flexibility, and resilience they need.
This solution covers your identity and access management needs and smoothly integrates with your hybrid IT setup. Plus, it can identify fraud in real-time on your web and mobile platforms.
However, it's worth noting that while Ping Identity is easy to use and set up, it comes with a higher price tag compared to many other identity and access management solutions available in the market. Let’s explore more details about the tool.
An Overview Of Ping Identity’s PingOne for Workforce
Your employees rely on their identities every day to do their jobs. PingOne for Workforce simplifies and strengthens identity protection, ensuring your employees work efficiently, and have seamless experiences.
PingOne simplifies the process of managing user identities by automating user provisioning and de-provisioning. Your team can easily onboard new employees, grant or revoke access rights, and maintain compliance with just a few clicks.
Further, PingOne is designed to adapt to your organization's needs, whether you're a small business or a large enterprise. Its scalability allows you to grow without worrying about outgrowing your identity management solution. You can add new applications and users seamlessly as your business expands.
Drawbacks of Ping Identity
Here are a few drawbacks of Ping Identity.
Ping Identity sometimes faces synchronization problems, causing it to malfunction intermittently. This inconsistency can frustrate you and your team, who rely on a reliable system.
Ping Identity cannot utilize extended properties for OIDC (OpenID Connect) connections. This limitation means you can't easily add custom attributes to tailor the system to your specific needs, which can be a significant drawback for you seeking flexibility.
Some Ping Identity solutions, like Ping One and Ping ID, are accessible only through the cloud. This can pose challenges for your team if the organization has strict security policies against cloud computing, potentially limiting their options for system access.
Understanding Ping Identity's documentation can be challenging. As a result, you and your team often rely on experienced integration partners to navigate the system's intricacies, which can add complexity and cost to the integration process.
But before discussing the various Ping Identity alternatives, we introduce Zluri here.
Opt Zluri for Your Identity & Access Management Capabilities
Managing user identities and ensuring secure access can sometimes be challenging for your organization. But guess what? Zluri is here to make your life easier.
Why should you choose Zluri, you ask? Zluri offers a SaaS management platform designed to handle all your SaaS applications and user access policies. It handles authentication, authorization, and monitors user activity and compliance.
Imagine a new team member joining your organization. With Zluri, their information seamlessly connects to their digital identity. This fantastic feature simplifies the process of setting up their access, allowing your IT admin to quickly confirm their identity and grant the right access to apps and data.
This added layer of security isn't just convenient; it also protects against identity theft and secures your crucial data from potential breaches.
Moreover, using Zluri, you can monitor everything from- which apps your team can access to when they log in and out and even the level of permissions they have. Zluri has got you covered.
This means you'll be able to spot any suspicious activities, like unauthorized access, and take action swiftly to safeguard your valuable app data.
But wait, there's more! Zluri also makes life easier for your IT team. It seamlessly integrates with your HR system, ensuring that all employee information is always up to date. Zluri uses this data to verify employee identities during onboarding, whenever changes happen, and even when someone leaves the company.
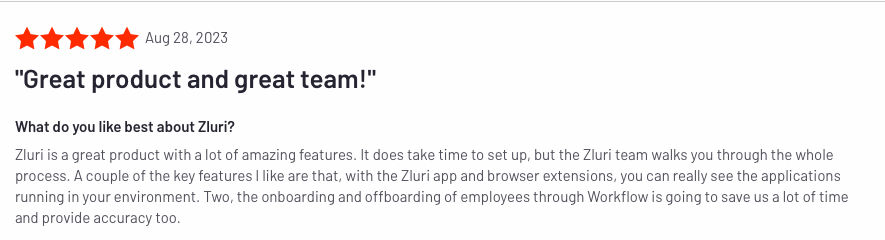
In addition, Zluri conducts regular audits and generates various reports that provide insights into your employees' and app activities, making it easy to meet your compliance requirements. You can track login and logout events, monitor group creation, manage departments, and monitor user profile changes.
So, if you're looking for a solution to simplify access management, enhance security, and boost your team's productivity, look no further – Zluri is the answer. Don't hesitate to schedule a demo today!
Customer Ratings
G2- 4.9/5
Capterra- 4.9/5
In this post, we will discuss 10 Ping Identity Alternatives & competitors available in the market.
10 Ping Identity Alternatives
When looking for Ping Identity alternatives, security is a crucial aspect that should be considered. Ping Identity has several alternatives and competitors, and we have compiled a list of solutions that readers can choose from.
1. Duo Security
Duo, a notable Ping Identity alternative, is a security suite hosted in the cloud and safeguards access to all applications for every user and device from anywhere in the world. It is designed to be simple to use as well as to implement while at the same time offering total visibility and control over the endpoint.
It provides strong authentication that does not require a password and multi-factor authentication that leads the market to its consumer, making it a suitable Ping Identity competitor.
Duo gives you the policies and control you need to block access based on the endpoints or user risk, and it does it in tandem with in-depth information regarding your users' devices. Users are provided with a standardized sign-in experience, which enables centralized access to on-premises and cloud-based applications.
Pros
Duo Security offers a seamless solution, especially when it comes to securing your network through multi-factor authentication (MFA). When you employ Duo's MFA for logging into critical security devices like firewalls, you can expect smooth and effective results.
Furthermore, Duo Security enhances your end-point security, providing an extra layer of protection. This added security measure bolsters your overall cybersecurity strategy, helping you safeguard your organization's digital assets effectively.
Cons
Sometimes, there's a delay in notification. This means that when there's an attempt to access a secure system, the user might not be informed promptly, restricting your ability to respond quickly to potential security threats
Reloading the app on a new device can be a cumbersome process. If the app reloading process is not smooth, it can lead to delays in setting up and configuring multiple devices for team members and impact productivity
The tool’s iOS push notifications may stop working without any clear error notice when the app becomes outdated. This can be frustrating for you who rely on these notifications to monitor and manage security events
Customer Ratings
G2- 4.5/5
Capterra- 4.7/5
2. LastPass
LastPass, Ping Identity competitor, is a passwordless identity management system that offers a variety of solutions that businesses of varying sizes may utilize. It gives employees the ability to generate, store, and share credentials in a frictionless manner. Additionally, it offers administrators vital visibility and control and ensures protection with LastPass' zero-knowledge security infrastructure.
With this identity management platform, you can gain access to additional access and authentication capabilities, such as single sign-on, which simplifies access to a maximum of three cloud applications, and multi-factor authentication (MFA), which secures the LastPass vault as well as single sign-on applications.
Pros
LastPass is your trusted vault for safeguarding all your essential business IT credentials. With LastPass, you can rest assured that your sensitive data is protected from unauthorized access or breaches.
LastPass is renowned for its user-friendliness, making it easy for your team to manage and access critical credentials.
Cons
LastPass does not offer a 4-hour auto-login feature. This means that your team needs quick access to their accounts and may find it inconvenient to log in manually whenever your team wants to use the tool.
If you're on the free plan, LastPass restricts the number of devices you can use without upgrading to a paid subscription and may require you to invest in a paid subscription to accommodate your needs.
Customer Ratings
G2- 4.4/5
Capterra- 4.7/5
3. JumpCloud
JumpCloud, a notable Ping Identity alternative, is an open directory platform that enables safe, hassle-free access to any resource, regardless of the operating system or physical location.
The JumpCloud Directory Platform provides IT, security operations, and DevOps with a unified cloud-based solution. This controls and manages employee identities and devices used by those employees and implements Zero Trust principles.
JumpCloud, being one of the major Ping Identity competitor, also offers identity & access management solutions for your team to manage identity, device, and access control requirements. Beyond this, JumpCloud also provides a passwordless identity management system.
Pros
JumpCloud offers a hassle-free implementation process, making it easy to get things up and running smoothly. With its user-friendly features, you can quickly set it up without the need for complex infrastructure.
JumpCloud operates in the cloud, eliminating the need for an on-premises AD/LDAP infrastructure. This means you can manage your authentication and directory needs without investing in costly hardware or maintenance.
With JumpCloud, you can utilize it for single sign-on (SSO), device management, and mobile device management (MDM). This versatility ensures that you get the most out of your IT management tools, making it a suitable Ping Identity alternative.
Cons
JumpCloud has a steep learning curve for users during the initial stages. While it offers powerful features, getting started with it might require a bit of time and effort to fully grasp.
When it comes to Mac installations, JumpCloud can be a bit finicky. You might encounter some temperamental issues during installation, which can be frustrating and time-consuming.
The mobile console of JumpCloud may not always be as responsive as desired. This lack of responsiveness could hinder your team’s ability to manage IT tasks on the go.
Customer Ratings
G2- 4.6/5
Capterra- 4.7/5
4. ForgeRock Identity Platform
The ForgeRock Identity platform enables global brands, companies, and government agencies to build secure, customer-facing partnerships across any app, device, or thing. Users may use online identities to increase revenue, expand their reach, and launch new business models.
ForgeRock stands out because it offers identity and access management, user authentication, and authorization in a seamless package.
Pros
ForgeRock Identity platform offers a smooth and hassle-free way to connect with your Java-based applications, making integration a simple task, and saving both time and effort for your IT team.
ForgeRock provides a private Maven repository that acts like a digital organizer for all your software pieces. It keeps tabs on dependencies, ensuring everything is in the right place.
Cons
One drawback of the ForgeRock Identity platform is that it may take some time to back up your data or restore it. This means that the process of safeguarding your important information or getting it back in case of an issue might not happen as quickly as you'd like.
Customer Ratings
G2- 4.4/5
Capterra- 5/5
5. Microsoft Azure Active Directory
Microsoft Azure Active Directory (Azure AD), a notable Ping Identity alternative, is a comprehensive identity and access management system with integrated security that connects individuals to the apps, devices, and relevant data while also assisting in preventing identity compromise.
It ensures the safety of adaptive access by using conditional access controls and multi-factor authentication.
Pros
With Azure AD, you gain a centralized user and resource management hub. This means that all user accounts, device configurations, and resource access controls can be conveniently administered through a unified online platform.
Another comprehensive feature of Azure AD lies in its hybrid functionality. This empowers you to seamlessly handle any pre-existing on-premise servers within your organization.
Cons
Moving your system from a traditional, on-premise Active Directory (AD) setup to Azure AD might be a steep learning curve, requiring you and your team to learn to adapt to a cloud-based approach.
When shifting from a local AD to Azure AD, some management options, such as group policy objects (GPOs), may not be available in the same way. As a result, you might need to reconfigure certain settings and policies to align with Azure AD's structure.
Customer Ratings
G2- 4.5/5
Capterra- 4.8/5
6. One Login
One Login is the market value leader in identity and access management. It streamlines identity management with safe, one-click access from all devices to enterprise cloud and on-premise apps.
OneLogin enforces your IT identity policies and removes employees from Active Directory to disable real-time app access. Take control of application access, onboard team members rapidly, and give end-users easy access to all their apps on every device.
Pros
OneLogin simplifies the task of integration with your various platforms. Whether it's your email, project management tools, or CRM, OneLogin ensures smooth integration, saving you valuable time and resources.
OneLogin offers a risk-free opportunity for your team to explore its capabilities. This allows you to assess if OneLogin fits your organization's needs without any financial investment upfront.
Managing directories, like those in G-suite and Workday, can be a cumbersome task. OneLogin simplifies this process by enabling effortless syncing. It reduces the risk of errors, enhances security, and ensures that your team can access the right resources when needed.
Cons
One drawback of using OneLogin is the need for frequent password changes. This can be quite a hassle for your team, often resulting in increased support tickets and user frustration.
OneLogin's process for adding new services or applications may not be very user-friendly. This can be challenging because your team may need additional training to understand and use the platform effectively.
Customer Rating
G2- 4.3/5
Capterra- 4.7/5
7. Auth0
Auth0 is a production unit of Okta identity cloud that takes a contemporary approach to identity in your hybrid environment. This enables businesses to grant users safe access to whatever application they choose, regardless of who they are.
Auth0 ensures the safety of login transactions every month, providing clients with simplicity, privacy, and security so they can concentrate on innovation instead. These unique capabilities make the tool a suitable Ping Identity alternative for your team.
Pros
With Auth0, you can efficiently manage passwords, establish security policies, control user privileges, and handle user accounts—all in one place. This minimizes the complexity of juggling multiple systems, making your job easier and more efficient.
AuthO takes care of a wide range of tasks on your behalf, including user management, security protocols, and account administration, freeing up your valuable time to focus on other important aspects of your IT responsibilities.
Cons
Auth0's integration capabilities may sometimes fall short, requiring additional workarounds or custom solutions. This limitation can increase your workload and create inefficiencies in managing user authentication and security.
Auth0 may impose certain constraints, such as character limits in the username field for users. These constraints can act as roadblocks for your team when they need to accommodate specific requirements or adapt the system to unique business needs.
Customer Ratings
G2- 4.3/5
Capterra- 4.6/5
8. Oracle Identity Management
Oracle Identity Management, a notable Ping Identity alternative, is a comprehensive cloud identity solution designed to handle the complexities of identity and access management within an organization. It offers a wide array of comprehensive features that cater to your IT needs.
One of its key features is its ability to seamlessly integrate with other Oracle products, creating a robust ecosystem for businesses heavily invested in Oracle technologies. This capability make Oracle identity management a powerful Ping identity competitor.
With Oracle Identity Management, you can expect robust user provisioning and de-provisioning capabilities, which streamline onboarding and offboarding processes. It also offers adaptive MFA and single sign-on (SSO) functionality, making accessing multiple applications securely with a single set of credentials easier.
Pros
Oracle Identity Management provides an extensive array of authentication policies it provides for integration and activation, making it easier for your team to safeguard sensitive data and systems.
The tool makes it very easy to add and manage groups, control user access, and maintain a high level of user control. This saves time and minimizes the chances of errors, ensuring that the right individuals have access to the right resources.
Cons
The tool is not very interface-friendly, and users often navigate through numerous apps to access the specific results they need. This can be time-consuming and can slow down your workflow.
With OIM, you may encounter the presence of bugs within the system. These bugs, while not insurmountable, can sometimes disrupt the smooth operation of Oracle's Identity Management.
Customer ratings
G2: 3.7/5
9. RSA SecurID

RSA SecurID provides a comprehensive suite that your company requires to tackle today's hybrid environment's unique issues in directory services, including authentication, access management, and identity governance. It achieves this while ensuring top-notch security and maintaining user-friendly convenience.
SecurID aids in spotting and reacting to advanced attacks, handling user access, and lowering the chances of risks, fraud, and cybercrimes.
Pros
One of the advanced capabilities of RSA SecurID is its user access management process. You can easily control who has access to what, and when necessary, they can swiftly revoke access, minimizing the risk of unauthorized access.
Whether it's on desktops or mobile devices, RSA SecurID takes the complexity out of implementation. This means that your team can quickly deploy the solution across the organization without the headaches of intricate installation processes.
Cons
With this tool, your users are restricted to having only a few RSA access tokens. This limitation can lead to user frustration, access delays, and increased support requests.
One notable drawback of RSA SecurID is the complexity it adds to remote access login. When trying to access systems remotely, users must merge their SecurID password with the SonicWall VPN password, making it less user-friendly compared to simpler login methods.
Customer Ratings
G2- 4.4/5
Capterra- 4.6/5
10. SecureAuth Identity Platform

SecureAuth Identity Platform, a notable Ping Identity alternative, is a comprehensive solution that seamlessly manages user identities and controls access to critical resources. You can centralize user authentication, authorization, and identity verification processes, ensuring that only authorized individuals gain access to sensitive data and systems.
SecureAuth, being a Ping Identity alternative, offers robust SSO capabilities, streamlining user access to various applications and services. Additionally, it supports a wide range of adaptive MFA methods, from biometrics to one-time passwords, providing flexibility in choosing the right level of security for each scenario.
Pros
With SecureAuth, the mobile app is a breeze for users to install. This means less time spent on troubleshooting and more time for your IT team to focus on critical tasks.
The platform offers best-in-class data security measures, protecting sensitive information. It minimizes the risk of breaches and data leaks, preserving the integrity and reputation of the organization.
Whether your IT environment changes due to scaling, technology upgrades, or other factors, this platform can seamlessly integrate, reducing the headaches associated with software compatibility issues.
Cons
SecureAuth Identity Platform has one potential challenge that some users might face: the need for specific skills to effectively use it, requiring a certain level of technical expertise or training to navigate its features and functionalities.
The tool may face network breakdowns that can result in inconveniences for your IT team. When relying on mobile devices for authentication, any network disruptions can hinder user access and workflow, leading to productivity losses.
Customer Ratings
G2- 4.4/5
Capterra- 4.5/5
About the author
Sreenidhe is a SaaS management expert and has a keen interest in ITAM and SAM practices. She is adept when it comes to SaaS Vendor Management and SaaS Spend management. Her knowledge of SaaS and SaaS management is self-thought and is based on a lot of reading. Before joining Zluri, Sreenidhe was working as a full-time journalist. She is also equally passionate about fashion and aspires to own a boutique someday.
Related Blogs
See More
Subscribe to our Newsletter
Get updates in your inbox
