Security & Compliance
• 7 min read
Ping Vs. SailPoint: Which IAM Tool To Opt For?
4th October, 2023
SHARE ON:
Ping enables your IT teams to grant the right level of access to authorized users to the right SaaS apps and data efficiently and securely. Meanwhile, SailPoint effectively manages employees' digital identities, access permissions, information security, and compliance.
However, both platforms offer other distinct capabilities. You, as an IT manager, can carefully examine before deciding which IAM tool to choose.
To find the best among Ping and SailPoint, you must thoroughly analyze each platform's key functionalities and determine how well it aligns with your IT team's needs. By doing so, you'll be able to make an optimal choice.
Let's take an example to help you understand better; an organization requires an IAM tool that helps with compliance control. So, which identity access management tool will be more suitable, Ping or SailPoint?
SailPoint can be a better choice in this scenario as its main emphasis is on compliance controls, managing and governing user identities, and access entitlements. Whereas Ping will be more suitable for organizations whose primary focus is on authenticating and authorizing user identities, granting secure access to SaaS apps and data, and enabling secure SSO capabilities.
This was just a gist of how your specific requirements can significantly affect your decision-making process. However, don't rely solely on one functionality to determine the ideal IAM solution. Instead, it is advisable to thoroughly evaluate each tool's capability before reaching a conclusion.
So, in this blog, we have differentiated both tools based on different parameters to help you decide which IAM platform will best meet the requirements of your IT team.
Comparison Based On Different Parameters: Which IAM Tool To Choose?
Below we've closely compared each parameter to help you determine which tool's functionalities are better for streamlining the identity access management process.
1. Solution Categories & Caters To Which Business Size
Ping Identity is categorized as customer identity and access management (CIAM), multi-factor authentication (MFA), passwordless authentication, privileged access management, risk-based authentication (RBA), and single sign on (SSO).
On the other hand, SailPoint is categorized as user provisioning and governance tools, sensitive data discovery, and self-service password reset (SSPR).
However, both Ping and SailPoint are well suited for the enterprise segment with 1000 plus employees.
2. Identity Access Management
Ping offers comprehensive identity verification and digital credential issuance solution. This enables your IT team to verify the authenticity of users' identities instantly.
It saves valuable time and reduces the costs associated with physical credential issuance, personal account management, eligibility management, and identity theft mitigation by swiftly validating the source and accuracy of credentials.
Also, in today's digital landscape, where people rely on their digital identity across various devices, Ping ensures no crucial identity-related information is leaked.
For instance, Ping streamlines the process by providing specific information required for a particular transaction, such as age confirmation rather than the complete date of birth.
Additionally, with this platform, your employee can seamlessly request access to required applications or data. Further, the IT team will verify their identity, ensuring that the person behind the credential is indeed who they claim to be.Meanwhile, SailPoint enhances your organization's security by safeguarding identities with access to SaaS apps and critical assets. It automates access management to reduce the risk of unauthorized access by former employees and unauthorized third parties. SailPoint promptly revokes access when employees leave, ensuring only authorized users can access your apps and data.
Furthermore, by using roles and policy logic, SailPoint enforces the least privilege, granting employees access only to necessary apps and data and minimizing security breaches. It aligns access with job roles to maintain a secure environment.
Also, it offers monitoring capabilities to detect unauthorized access attempts. Identifying incidents allows immediate preventive actions like account suspension or access revocation, mitigating security risks.
Through regular audits, SailPoint provides complete visibility and control over access risks. It ensures appropriate access levels during role changes or transitions, bolstering security and governance.
3. Securing Identity
How Ping Identifies Unauthorized Access Attempts?
Ping offers your IT team a comprehensive solution for managing and mitigating risks. It enables them to assign and collect an impact level from various risk signals, including suspicious device aspects, network information, and user behavior. Ping generates a risk score by analysing these signals, providing valuable insights into potential security threats.
Additionally, Ping assists your IT team in identifying critical users, allowing them to make informed decisions when granting or denying access to SaaS apps and data. This ensures that only the right level of access privileges are appropriately assigned to them.
Also, its multi-factor authentication (MFA) capabilities play a crucial role in preventing potential risks. It empowers your employees to authenticate themselves through multiple means, enhancing the verification of their identity and reducing the likelihood of unauthorized access.
Furthermore, Ping provides your IT team with centralized dashboards, offering deep insights into authentication patterns and highlighting common risk factors within the organization. This centralized view provides a comprehensive understanding of the organization's security landscape and facilitates effective risk management strategies.
How SailPoint Mitigates Unauthorized Access Attempts?
SailPoint allows your IT team to seamlessly handle access management throughout the employee lifecycle, granting, modifying, and revoking access as needed when employees join, change roles, or leave your organization. How does it do that?
SailPoint automates the onboarding and offboarding processes, significantly improving your IT team's efficiency and enhancing the overall experience for your employees. This automation not only streamlines IT operations but also safeguards against the potential risks associated with excessive access privileges or unauthorized entry by former employees.
To maintain the integrity of access permissions, SailPoint conducts regular audits and proactively monitors and manages all access points. This helps ensure the security of your organization's sensitive data by mitigating threats such as unauthorized access attempts.
Furthermore, it implements role-based provisioning policies, aligning employees' access permissions with their job descriptions. Doing so reduces the risk of unauthorized access by former employees and allows your IT team to restrict current employees' access to only what is necessary for their respective roles.
4. Authentication Process
Ping’s Passwordless Authentication Process
Ping offers a solution to mitigate security threats by embracing a passwordless approach. Passwords have long been prime targets in cyberattacks and a source of employee frustration. By eliminating passwords, Ping effectively reduces security risks while simultaneously enhancing employee engagement and productivity.
Ping’s passwordless authentication safeguards the most targeted asset of hackers: your users' identities. It offers quicker and more secure methods of logging in and gaining access, eliminating the vulnerabilities associated with traditional passwords. With single sign-on and centralized access features, Ping reduces the overall password footprint, enhancing security and convenience.
Moreover, Ping leverages multi-factor authentication capabilities, adding an extra layer of protection against password attacks. Ensuring that users are truly who they claim to be, prevents unauthorized access attempts.
Ping doesn't stop at passwordless authentication. It actively monitors the entire access process in real time, identifying various user risk signals. This proactive approach enables IT teams to promptly detect potential threats and take preventive measures, mitigating security risks effectively.
SailPoint’s Password Management Capabilities
On the other hand, SailPoint enhances security and boosts employee productivity while reducing the burden on your IT team. By streamlining access management, SailPoint ensures a seamless user experience while maximizing security measures.
SailPoint efficiently utilizes password policies to enforce strong password requirements. It enables your IT team to implement out-of-the-box configurations for password strength and complexity, ensuring that user passwords meet the highest security standards. Additionally, SailPoint leverages sync groups and a password dictionary to provide greater control over password management, minimizing access issues and reducing the risk of compromised credentials.
One of SailPoint's key strengths lies in its ability to support both on-premises and cloud applications. It securely synchronizes passwords across multiple applications, ensuring consistency and reducing the need for your employees to remember and manage different passwords. This synchronization capability not only enhances security but also improves the employee experience.
After thoroughly comparing Ping and SailPoint, you might have now understood which tool caters to your IT team's specific needs. However, it's crucial to note that other platforms are also worth considering. One such exceptional alternative is Zluri, which offers remarkable features that help your IT team streamline the identity access management process.
So, let's have a quick look at how Zluri is a better substitute for Azure AD and SailPoint.
Zluri: One-Stop-Solution For Managing Your User’s Access Permissions
If you're looking for the perfect solution to address your IT team's access management challenges, Zluri is the answer. What sets Zluri apart is its ability to securely and efficiently assign the right level of access permissions to the right employees for the required SaaS apps and data exactly when needed. With Zluri, your IT admins can easily modify and revoke access when employees change roles or leave the organization.
Zluri provides your IT admins with a centralized platform for managing user identities, access policies, and compliance. It effectively controls authorization and authentication processes while proactively tracking user behavior, such as access attempts, to ensure compliance and security.
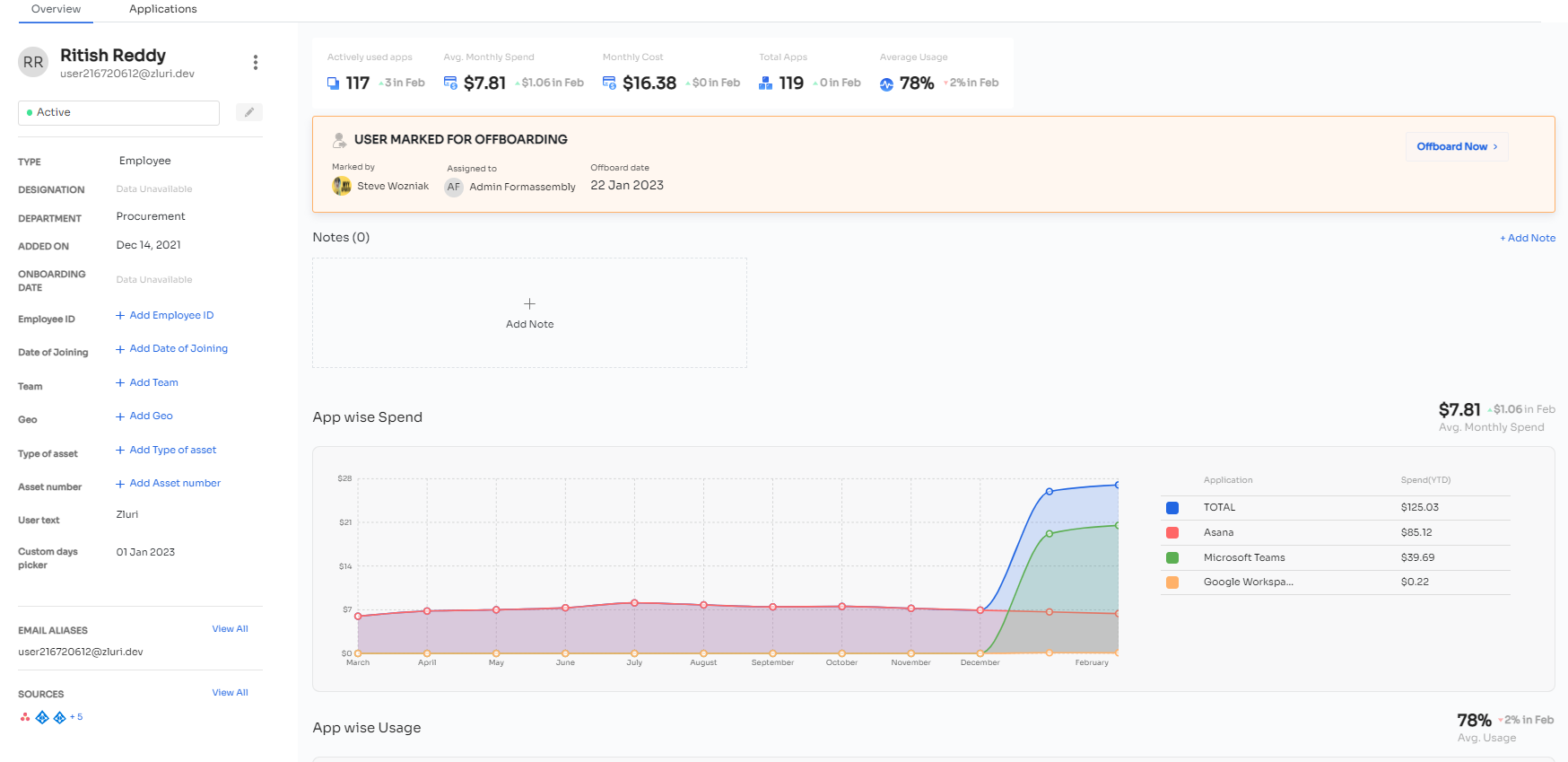
Let's dive into the benefits of Zluri with an example. a new employee joining your organization. Zluri securely associates the employee's data with their digital identity, enabling your IT admins to verify their identity during onboarding seamlessly. By doing so, your team can ensure that the employee is granted the right level of access permissions for SaaS apps and data, streamlining the onboarding experience and safeguarding against identity theft and security breaches.
Apart from these advantages, Zluri offers advanced functionalities like single sign-on (SSO) and multi-factor authentication (MFA). These functionalities help your employees to authenticate themselves using a single set of credentials and a few clicks. By eliminating the need to remember multiple passwords, Zluri minimizes password fatigue and improves the employee experience, making accessing the required SaaS applications seamless.
However, monitoring and governing the entire access management process can be daunting for your IT team, but Zluri has a solution for that as well. Your IT team can get a 360-degree view of employee access activities and permission levels through a centralized dashboard; with the help of this view, your team can seamlessly monitor every access step. This overview includes insights into the SaaS applications the employee has access to, login and logout attempts, and assigned permission levels.
Also, such visibility allows your IT team to detect suspicious user activities, such as unauthorized access attempts, and take immediate action or implement security measures to safeguard sensitive SaaS app data from breaches or cyberattacks.
But Zluri doesn't stop there. It also empowers your IT admins to securely and efficiently grant, modify, and revoke access. By integrating with the HR system, Zluri fetches employee data and updates it in its dashboard. This seamless integration gives admins the flexibility to verify employee identities during onboarding, changes in the employee lifecycle, and offboarding.
Additionally, Zluri conducts periodic audits and generates reports on employee and application activity, including login and logout events, group creation, and user profile changes. It also generates security event reports, such as failed and suspicious login attempts and changes to security policies. These reports assist your IT team in proactively preventing security breaches.
So why wait? Book a demo now and experience firsthand how Zluri enables your IT team to efficiently and securely streamline identity access management.
Related Blogs
See More
Subscribe to our Newsletter
Get updates in your inbox
