Access Management
• 8 min read
Identity And Access Management Analyst Job Description
19th October, 2023
SHARE ON:
Identity and access management analysts are the ones who provide expertise and guidance to various business units. Their ultimate objective is to design and implement access controls across all systems effectively. However, there is more to the IAM analyst job role.
In this article, we'll shed light on the job description, responsibilities, qualifications, salary, and skills of an IAM analyst. So, whether you're an aspiring analyst or seeking to understand the role, this article will provide a clear overview.
Identity and access management analyst plays a pivotal role in managing the access rights and identities of both internal and external users within the organization. Their primary responsibility revolves around creating accounts, particularly supporting LEAP (Leading Enterprise Application Platform). This includes the management of accounts across a range of platforms, including Active Directory, CA Service Desk Management, Customer Service Portal, SAVE, CBMS, and Mainframe.
Also, they work closely with IT and cybersecurity teams to understand the necessary requirements for IAM. However, the roles and responsibilities are not restricted to this only; there is a lot more to uncover. So, in this article, we'll discuss in detail the identity and access management analyst job descriptions to provide you with a clear understanding of their duties.
Tasks Performed By Identity And Access Management Analyst
The IAM analyst plays a crucial role in supporting the organization's identity and access management program. They perform various IAM tasks effectively to ensure a secure access environment for both users and critical data.
Listed below are a few of the tasks that are included in an identity and access management analyst job description:
Manage user accounts and access permissions: IAM analysts are responsible for creating, modifying, and deactivating user accounts within the organization's identity management system. They also control what systems, applications, and data these users can access.
Collaborate for precise access control: IAM analysts work closely with the IAM team to ensure that individuals within the organization are granted the appropriate level of access to resources. This collaboration helps maintain the balance between security and operational efficiency.
Administer the IAM system daily: This involves the routine management of the identity and access management system, including tasks like user provisioning, deprovisioning, and more.
Troubleshoot and resolve IAM issues: When problems or issues related to identity and access management occur, IAM analysts step in. They troubleshoot and resolve these issues promptly to minimize disruption.
Contribute to IAM projects: IAM analysts actively participate in IAM-related projects and initiatives, such as implementing new security measures, integrating systems, or enhancing access control processes.
Maintain IAM program documentation up-to-date: IAM analysts maintain detailed documentation of the identity and access management program. This documentation helps in ensuring compliance, making audits more efficient.
Review access control reports for security: They regularly review access reports to identify potential risks or violations. This proactive approach helps maintain a secure access environment and minimizes the risk of unauthorized access.
Train new users on the IAM system: IAM analysts play a role in educating new users on how to use the identity and access management system effectively. This training ensures users understand how to request, access, and manage their permissions.
Adapt IAM to changing business needs: IAM analysts are responsible for adjusting the IAM system accordingly to the changing business needs. They need to align access controls with changing roles and requirements to ensure that access remains appropriate and secure.
Now that you are familiar with what all IT tasks are performed by IAM analysts, let's move forward and learn about their roles and responsibilities.
Duties Of Identity And Access Management Analyst
Here's a list of identity and access management analyst's duties:
Managing user groups: Creating and managing user groups within the identity & access management system, which streamlines access control and simplifies management.
Enforcing company policies: IAM analysts enforce company policies and procedures related to IAM, ensuring compliance and security are adhered to.
User activity monitoring: They actively monitor user activities within the identity & access management system to identify any unusual or suspicious behavior.
Reporting on IAM system activity: IAM analysts generate reports detailing the activities and usage of the identity & access management system. These reports are crucial for audits and security assessments.
Staying updated on best practices: IAM analysts maintain current knowledge of industry best practices in identity & access management to ensure the organization's approach remains cutting-edge and secure.
Now, let's proceed further and learn about what is the qualification criteria and salary range of identity & access management analysts.
IAM Analyst Qualification Criteria & Salary Range
Qualifications for an IAM analystcan vary among companies. But there are some common requirements asked by companies, which are: the IAM analyst candidates need to have a bachelor's degree. That, too, in the field of computer science, information technology, or related areas, is commonly sought by most companies.
Also, candidates are expected to have at least two years of experience in identity & access management or a related field. Here are some essential skills that candidates are expected to possess:
Proficiency in communication and project administration.
Strong analytical capabilities.
Exceptional organizational skills and attention to detail.
Familiarity with IAM principles and industry best practices.
Knowledge of IAM software
Proficiency in using spreadsheet and word processing software like Microsoft Excel and Microsoft Word.
Familiarity with database concepts and experience with relational databases such as Microsoft SQL Server.
The ability to work effectively both as an individual contributor and within a team.
IAM Analyst Salary
IAM analyst salaries typically range between $60,000 and $85,000 annually, though this may vary among different companies. Additionally, many employers offer benefits like health insurance, dental insurance, and 401(k) plans. These benefits can contribute an extra $10,000 to $15,000 annually to the overall compensation package.
What All Is Expected From An IAM Analyst?
Below, you'll find the list of job expectations that an IAM analyst is required to fulfill:
The ability to deliver clear and accurate reports to senior management regarding the organization's IAM status.
Skilled in developing IAM metrics and Key Performance Indicators (KPIs) for tracking progress and measuring success.
Familiarity with diverse IAM tools and technologies, with the capability to recommend solutions aligned with the company's requirements.
Ability to lead IAM projects from start to finish, including planning, coordinating resources, and managing timelines.
A solid grasp of security concepts and their relevance to IAM.
That's not all; IAM analysts are expected to prepare specific types of reports and have a technical set of skills.
Types Of Reports Prepared By IAM Analyst
Here are the types of reports that an IAM analyst needs to prepare:
Access Request Report: This report details all the users who have requested access to the organization. It includes essential details like the access request date, the user's name and department, the type of access requested, and the approval status.
User Provisioning Report: This report offers insights into all user provisioning activities within the organization. It includes information such as the provisioning date, the user's name and department, the type of access provisioned, and the provisioning success status.
Audit Report: This report documents all audits related to IAM conducted within the organization. It encompasses the audit date, type, scope, and the findings resulting from the audit.
IAM Strategy Report: This report outlines the organization's IAM strategy, covering its goals, objectives, chosen tools and technologies, implementation timeline, and budget allocation.
User Authentication Report: This report details user authentication activities within the organization, including the authentication date, the user's name and department, the authentication method used, and the authentication's success status. It also tracks and investigates failed authentication attempts to preempt potential security breaches.
Password Reset Report: This report tracks all password reset activities within the organization, recording reset dates, user information, and the reset's success status.
Authorization Report: This report records all authorization activities within the organization, encompassing authorization date, user details, requested authorization type, and approval status.
IAM Analyst Technical Skills
The technical skills essential for the role of an IAM analyst include the following:
Need to be familiar with different operating systems (Linux, Windows, etc.)
Need to have a strong grasp of directory services (LDAP, Active Directory, etc.)
Have Profound knowledge of security protocols (SSH, TLS, etc.)
Proficiency in at least one scripting language (Python, Ruby, etc.)
Has hands-on experience with IAM tools (Okta, Ping Identity, etc.)
Now you know that an IAM analyst handles many critical tasks within the organization. From ensuring that only authorized users have access to the right resources to safeguarding the organization's digital assets. However, this responsibility can be complex and time-consuming to manage manually.
To assist IAM analysts in their work and streamline the IAM process, an effective solution like Zluri can be a game-changer. Why Zluri? What functionalities does it offer? Here's a quick guide.
Zluri: The Go-To Choice For An IAM Analyst
Zluri is an intelligent modern SaaS management platform that offers access management capabilities. It is designed to help your IT team automate and simplify several identity & access management processes. Including provisioning, access modification, and deprovisioning process, enforcement of access policy, and ensuring regulatory requirements are met.
Let's see what all benefits it offers in detail:
Zluri Enhances Data Security By Reducing Errors And Centralizing Access Control
Zluri automates the manual, repetitive access management tasks. This helps to significantly reduce the likelihood of errors in access management.
This reduction in errors is important for protecting data security. As such, inaccuracies or oversights in access control can pose substantial risks to an organization's sensitive data.
Additionally, Zluri centralizes access control, providing a unified platform to manage permissions for various SaaS apps. This simplifies access management, strengthens security, and makes it easier to grant and revoke access. Also, centralized control with Zluri improves IT efficiency and minimizes the risk of unauthorized access.
Enables You To Effortlessly Manage Employee Access To SaaS App And Other Digital Assets
Zluri seamlessly integrates with your organization's HR system, providing real-time employee data to you. Through this integration, Zluri automatically fetches and presents all employee information on a centralized dashboard.
This enhanced visibility allows your team to verify employee details without the need for manual intervention, enabling them to grant, modify, or revoke access as needed. Also, this helps ensure that each employee has the appropriate level of access to the correct applications at the right time.
Furthermore, it automatically revokes access when an employee departs, effectively preventing potential security breaches.
Enables You To Keep Track Of All The Access Activities
With Zluri, you can monitor all the access activities that are taking place in your organization, including:
Who among the users is granted access to specific applications?
How often do they utilize the SaaS applications?
What is their status, whether they are active or inactive (by evaluating the user's login and logout time)?
What level of permissions do they hold?
Which role, position, or department they are from, and all the other details that your team needs to know to effectively manage the user access?
By monitoring these access activities, you can easily understand the access patterns/user behavior. This will further help ensure that only the right user continues to access the organization's sensitive SaaS app data. Also, this allows you to maintain a well-governed and secure environment.
Enables You To Enforce Security Policies
Zluri enables your IT team to enforce segregation of duty policy (SoD), role-based access control (RBAC), the principle of least privilege (PoLP), and just-in-time access.
By enforcingthe segregation of duty policy Zluri enables you to ensure no two individuals are responsible for the completion of one task.
By implementing role-based access control, Zluri enables you to ensure the access permissions align with the user's roles and responsibilities.
By enforcing the principle of least privilege, Zluri enables you to ensure minimum access permissions should be granted to employees. This allows you to avoid over-provisioning or granting excessive privilege.
By enforcing just-in-time access, Zluri enables you to grant employees temporary or just-in-time access to required apps for a specific duration. This way, you can reduce the attack surface caused by standing privileges.
You Can Conduct Regular Access Audits And Generate Curated Reports With zluri
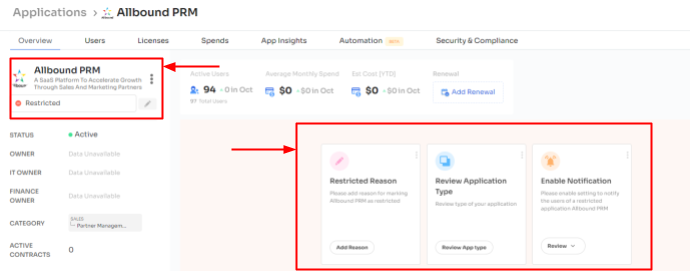
Access permissions sometimes remain unchanged even when they are no longer needed. This unchanging access presents a potential security threat. As unauthorized individuals could exploit these permissions to gain entry to sensitive information, potentially leading to a security breach.
With Zluri, you can routinely perform access audits to address this concern. These audits involve the review of existing access permissions. Additionally, Zluri generates reports that facilitate the identification of unauthorized users or those accessing critical applications with a high-risk profile. This further helps you to proactively implement measures to safeguard sensitive SaaS application data from potential security breaches.
Also, Zluri records the entire review process and generates access logs/audit trails to show as evidence to auditors. By doing so, you can meet stringent compliance regulations where data integrity is a crucial security requirement.
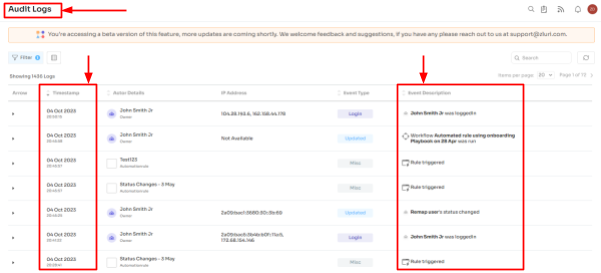
This proactive approach helps mitigate potential legal and financial penalties linked to non-compliance. Also, you can avoid getting into trouble and having to pay fines.
Allows You To Monitors And Analyses User Access
Zluri monitors access entitlements to evaluate if any users possess more access privileges than necessary. In the event of identifying issues or violations, your IT team can swiftly adjust the user's access permissions. This helps ensure that only the appropriate users maintain the correct level of access. This proactive measure helps prevent potential security that arises due to employees holding excessive permissions.
Also, Zluri also sends real-time notifications if any users attempt to access apps that are not authorized to access as per their role. These alerts help you take immediate actions, such as limiting or suspending user accounts as needed, to uphold a secure access environment.
So now that you know what all Zluri offers to streamline the identity access management process, why not book a demo now? And experience it firsthand. You'll discover that it might just be the ideal solution to kickstart your responsibilities as an IAM analyst.
Also Read: How to Choose an Identity Access Management Tool
Related Blogs
See More
Subscribe to our Newsletter
Get updates in your inbox
