Security & Compliance
• 15 min read
Top 10 SailPoint IGA Alternatives To Consider In 2024
28th December, 2023
SHARE ON:
As organizations recognize the critical importance of Identity Governance and Administration (IGA), it is essential for IT managers to have the right IGA tool for proper access controls and fortified security.
SailPoint IGA has been widely adopted for its comprehensive IGA features in managing digital identities, roles, and access privileges. Nevertheless, there are several alternative options available.
Explore the top 10 SailPoint alternatives that give you a broader perspective and potentially uncover solutions that better suit your Identity and governance requirements.
The SailPoint identity platform offers a comprehensive solution centralizing identity management, providing full visibility and control over user access. It enables granular access controls through RBAC and ABAC, allowing you to define and enforce access policies based on roles, responsibilities, and contextual factors, thereby enhancing security, reducing unauthorized access risks, and ensuring compliance.
Although SailPoint identity security is a robust IGA tool, the solution does have some drawbacks that impede your team's effectiveness in managing user access. These limitations may differ depending on your individual needs and preferences, which may lead you to explore other alternative options.
Potential Limitations Of SailPoint Identity Security
Here are a few limitations of the SailPoint Identity platform:
The product requires extensive training and significant time from your team to understand and utilize it to its full potential. This may limit their ability and time to concentrate on other essential identity management tasks
This might not be ideal if you want a tool that offers extensive flexibility and customization. It has limitations in terms of customization, leading to inefficiencies in managing user access within your organization.
The tool's task-based architecture introduces delays in processing updates from authoritative sources. This can hinder real-time operations, especially in larger environments where multiple sources require frequent daily updates.
Considering the mentioned potential drawbacks, it is worth exploring the leading alternatives to SailPoint IGA. These alternatives provide advanced features and robust capabilities specifically designed to meet your IT teams' unique requirements.
List Of 10 SailPoint IGA Alternatives
Now, let's delve into the different alternative options to the SailPoint Identity platform:
1. Zluri
SaaS adoption is reaching new heights, and remote work arrangements are becoming increasingly widespread. However, these advancements come with challenges for IT teams, especially concerning manual management and user access review. The complexities of monitoring all user access privileges can create gaps that unauthorized users might exploit, putting the security of data stored in SaaS applications and systems at risk. As a result, data integrity and confidentiality have become primary concerns for IT teams striving to maintain a secure and efficient working environment.
Zluri presents an exceptional identity governance and administration platform that empowers your IT team to effectively manage and monitor user access. Unlike existing platforms tailored for on-premises environments, Zluri’s Identity Governance platform is specifically built for the SaaS and AI-driven world.
Zluri's IGA platform empowers you to take charge and strengthen security effortlessly. IT teams can benefit from features like user provisioning, automated access reviews, and self-service access requests to efficiently manage and enhance your organization's security.
Wondering how Zluri transforms identity governance & administration to empower your organization's access management?
Let's delve into what distinguishes Zluri from other IGA tools, showcasing its exceptional and distinctive capabilities.
Unveiling Zluri's Discovery Engine: Real-Time Visibility into User Access Data
Zluri's discovery engine comprises 5 unique methods: single sign-on (SSO), finance and expense management, API integrations, optional desktop agents, and browser extensions. These methods provide in-depth analysis and valuable user data, equipping your IT team with crucial insights into your SaaS applications.![zluri discovery method]()
With Zluri's integration, you can effortlessly determine user access, identify active users, assess permissions, and gain insights into various app-related aspects. Ensuring complete control and visibility, Zluri strengthens your defenses against potential breaches, enhancing security.
Seamless integration with popular identity systems and core applications achieves an impressive 50% scope coverage, streamlining authentication processes for a seamless user experience. With access to over 800 SaaS apps, Zluri delivers real-time data, insights, and AI-powered alerts, ensuring 100% visibility through API-based integration.
Zluri's extensive library of over 250,000 apps provides granular-level access data, offering comprehensive insights into user permissions within your SaaS ecosystem. Thus, you can harness the power of Zluri's robust integration capabilities for enhanced productivity and seamless data flow.Empowering Security & Efficiency: Zluri's Automation Engine
Zluri's automation engine seamlessly manages access workflows, ensuring efficient automation with meticulous reviews and strict adherence to defined rules and policies. It achieves this by establishing automation rules and triggers aligned with your identity governance policies, guaranteeing consistent adherence to predefined guidelines.
With Zluri, you can craft personalized access and review workflows that operate autonomously, efficiently managing access privileges and streamlining administrative processes, unlocking the full potential of your IT management capabilities.
Now, let's now delve into the core capabilities of Zluri's IGA:
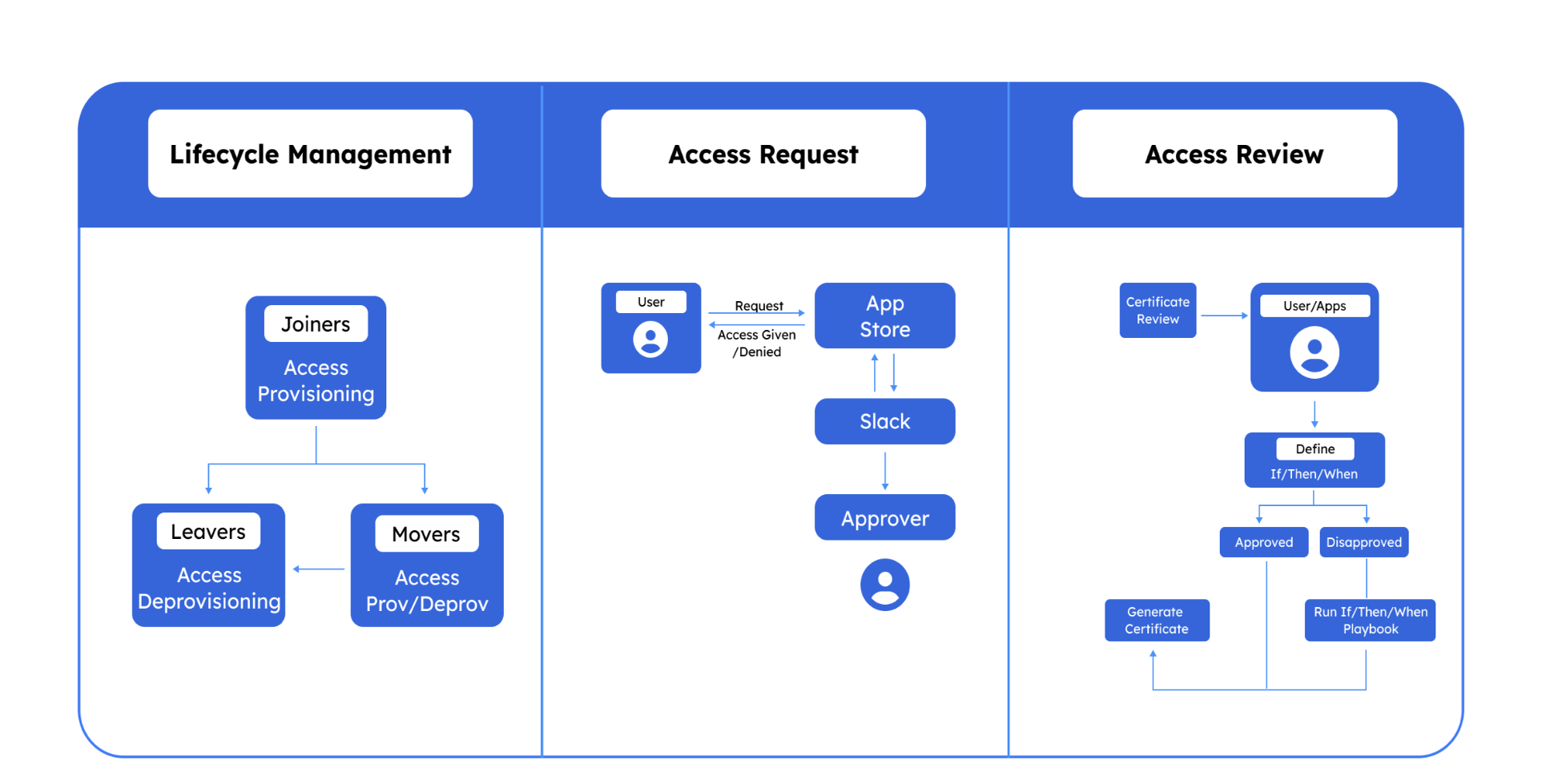
Lifecycle Management
Zluri offers an extensive access lifecycle management platform that covers the entire user access lifecycle, from provisioning to deprovisioning. This feature empowers your IT team to effectively manage user access rights throughout their tenure in the organization.
Zluri empowers your IT teams to craft tailored onboarding and offboarding workflows (playbooks) for seamless provisioning and deprovisioning. With just a few clicks, you can assign customized permissions based on roles, departments, and seniority levels, ensuring that every employee receives appropriate access to the necessary tools approved at the right level.
Automated user provisioning workflows:
Your team can easily provision access to the necessary applications and resources based on employees' job roles and responsibilities. This ensures that employees have the appropriate access to perform their tasks efficiently from day one.
To securely grant access to new employees using Zluri's user-friendly interface, follow these actionable steps:
Step 1: Access Zluri's platform and navigate to the workflow module. Select the onboarding option from the drop-down menu and click on "New Workflow" to proceed.
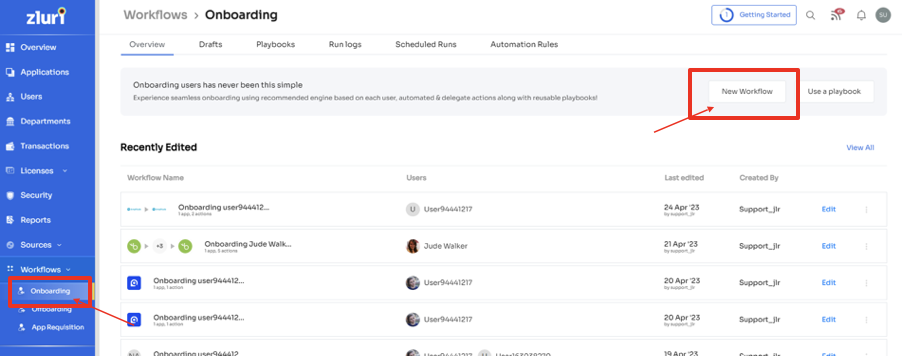
Step 2: Choose the employee(s) who need to be onboarded. Utilize the search bar or browse through the list to locate and select the relevant employee(s). Click on "Continue" to proceed.
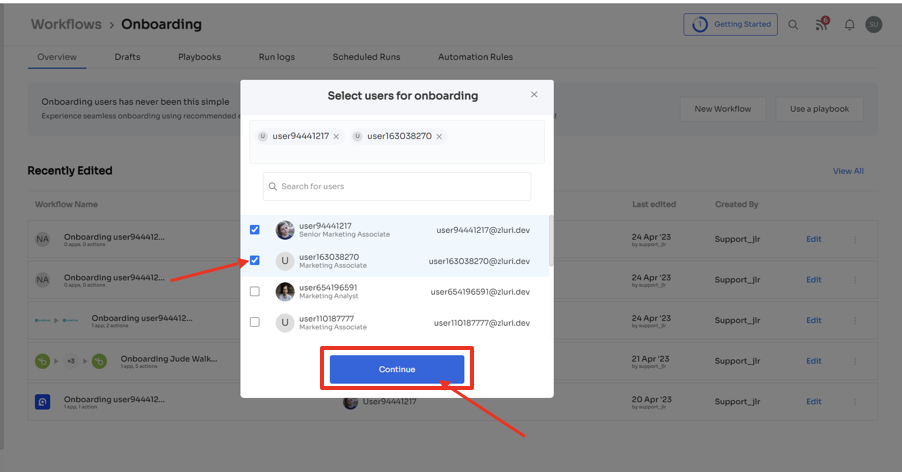
Step 3: Utilize Zluri's contextual-based app recommendations that consider factors like the user's role, department, and seniority level. This ensures a seamless onboarding experience, enhancing productivity and ensuring secure access.

Step 4: Further, you can use Zluri's in-app suggestions to automate additional tasks, like adding users to relevant channels or sending welcome messages through apps like Slack.
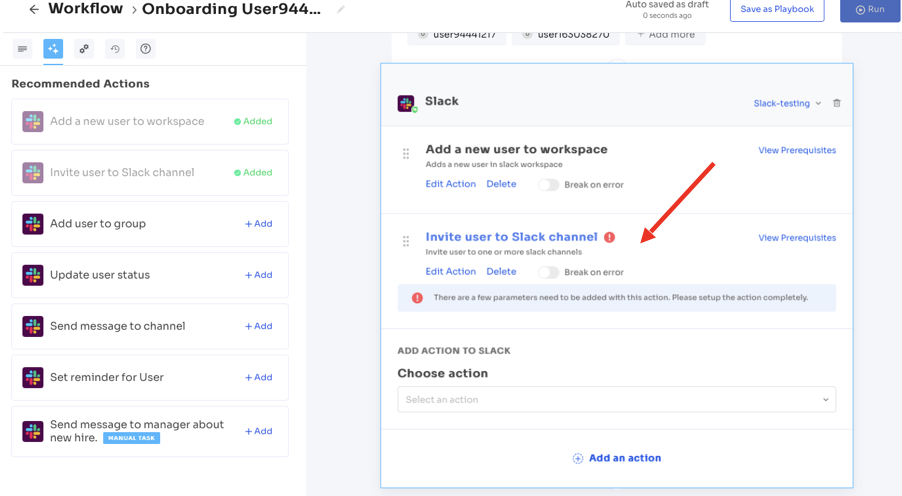
Step 5: Now save workflows as "playbooks" for future use within Zluri. This eliminates security risks when onboarding employees with similar designations, user roles, permission levels, and other common attributes.
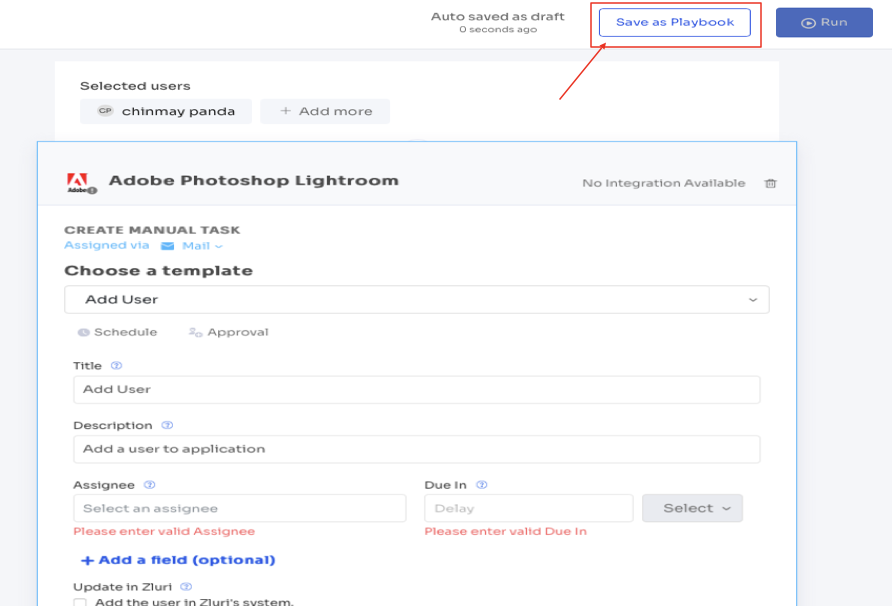
This automated workflow ensures a smooth onboarding journey while maintaining robust security measures.
Automated user deprovisioning workflows:
Additionally, Zluri simplifies the deprovisioning process when employees leave the organization or change roles. Your IT team can efficiently revoke access to all relevant applications and resources, reducing the risk of unauthorized access to sensitive data.
To make the most of Zluri's automated deprovisioning workflow, follow these steps:
Step 1: Access Zluri's main interface and navigate to the workflow module. Select " offboarding " From the drop-down menu and click "New Workflow" to initiate the process.
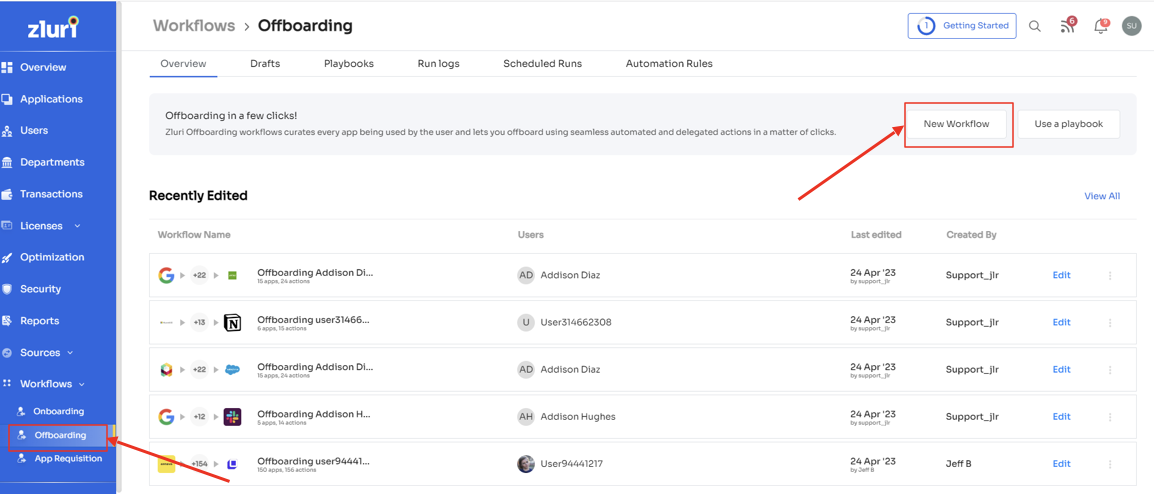
Step 2: Locate the dedicated offboarding user box. Your team can easily find and select the employee(s) you wish to offboard. Utilize the search bar or scroll through the list to identify the users. Once selected, click on "Continue" to proceed.
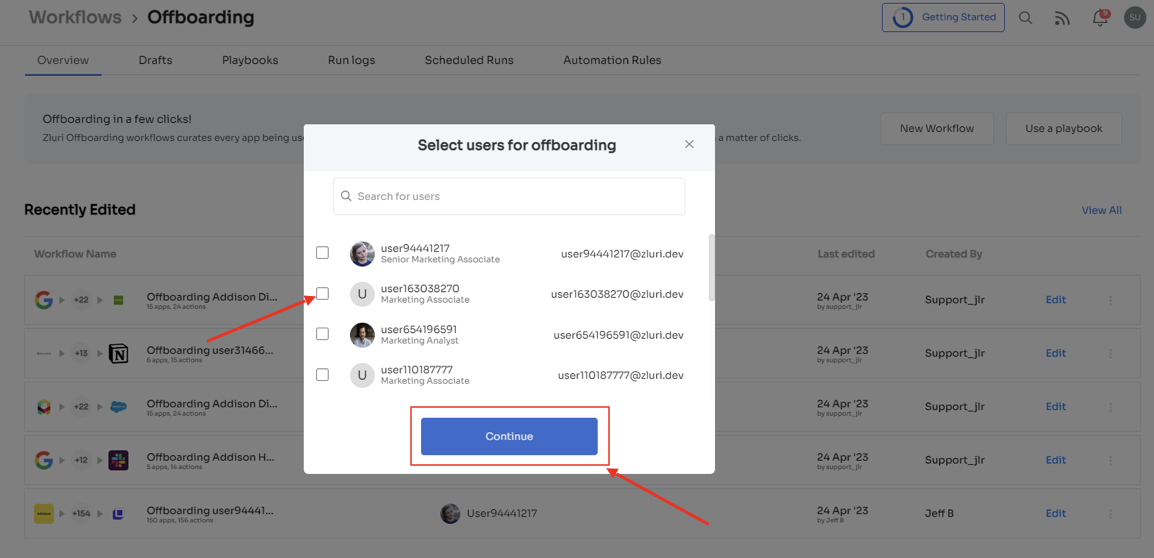
Step 3: Review all the applications that the offboarded employee had access to. Zluri provides suggested actions under "recommended actions" for each application. You can click on each application to view these recommendations. Choose and execute the necessary actions based on the provided recommendations to ensure appropriate access removal.
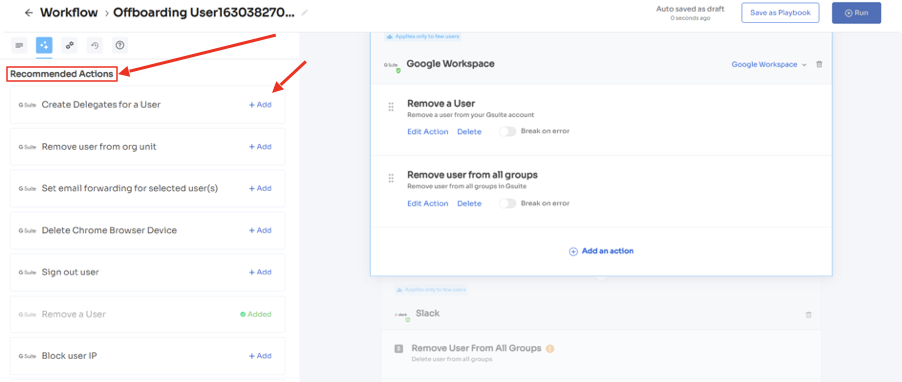
Step 4: Save the workflow as a "playbook" for future use. This enables your team to utilize the same playbook for deprovisioning users in subsequent instances.
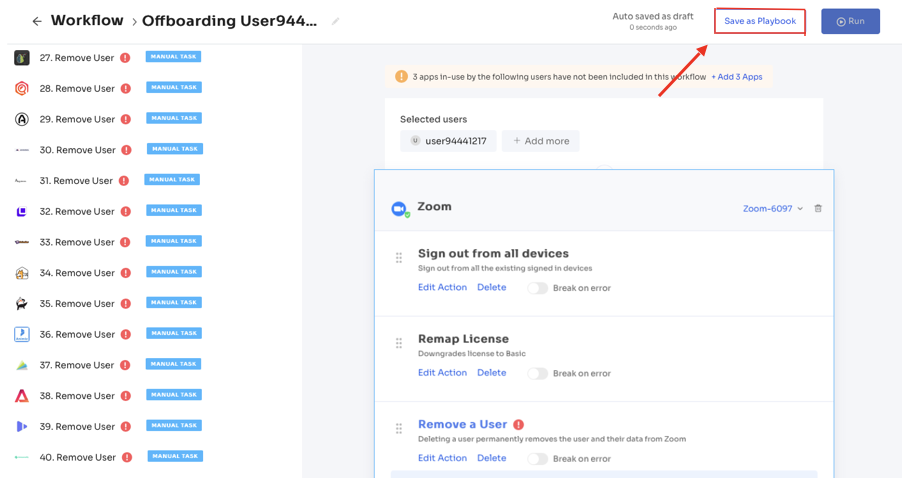
Following these steps, you can automate the user deprovisioning process, promote data security, and ensure compliance throughout the offboarding process.
Ad-hoc Requests management: Ticketless Solution
Zluri's self-serve model, known as the Employee App Store (EAS), simplifies the process of managing ad-hoc access requests when there are changes in their roles. With EAS, your IT team gains control over granting access to the necessary tools based on employees' job roles and permissions.

Using the EAS, your IT admin or designated approvers can review and approve access requests, ensuring that the requested permissions align with employees' job responsibilities. This governance mechanism helps prevent unauthorized access to sensitive information within your organization. Higher-level authorities have the command to override decisions made by lower-level admins or managers, enabling effective decision-making and access control.
Transparency is maintained throughout the access request process, as decision-makers can provide comments to explain why a request was rejected or even they can modify specific requests (can change the license tier if deemed more appropriate during the approval process).
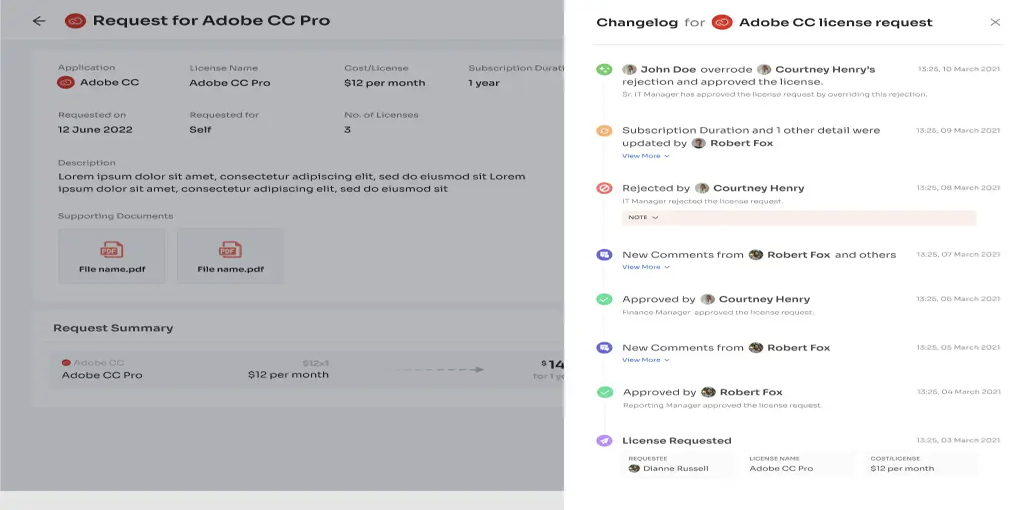
Users can conveniently track the status and updates of their requests through the "changelog" feature. This includes information on request approval or rejection, changes in license duration or tier, and any comments added by admins, providing visibility and accountability throughout the access management process.
Compliance Audit Excellence with Zluri's Access Certifications
Zluri understands the critical significance of compliance for all organizations. That's why it streamlines the access certification process, providing a well-organized and automated approach to review and authenticate user access and entitlements.
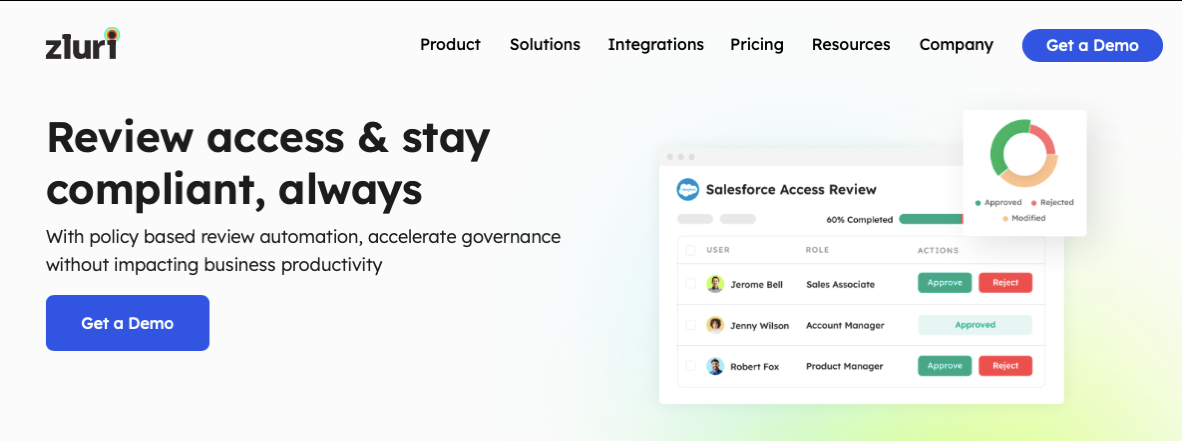
With a centralized platform, your IT teams and auditors can efficiently review and report on users' access. By conducting regular access certifications, you can validate and evaluate user access privileges, ensuring compliance with industry regulations and internal security policies.
Zluri's access review feature offers two key benefits for your IT teams:
Intelligent Automation: Effortlessly set review parameters, select reviewers, and schedule campaigns through intelligent automation.
Rule-Based Assessment: Evaluate user access rights based on predefined rules, saving time and reducing errors compared to manual spreadsheet reviews.
![get demo]()
Let's now explore these distinctive features step by step and uncover the full extent of what Zluri offers:
Full Access Oversight with Continuous Reviews:
Zluri stands out among other IGA tools with its innovative approach to access reviews. By adopting Zluri's IGA solution, you gain the power of continuous certifications, ensuring precise control over access privileges.
This proactive practice of regularly auditing and validating access permissions significantly reduces the risks of unauthorized entries and potential data breaches.
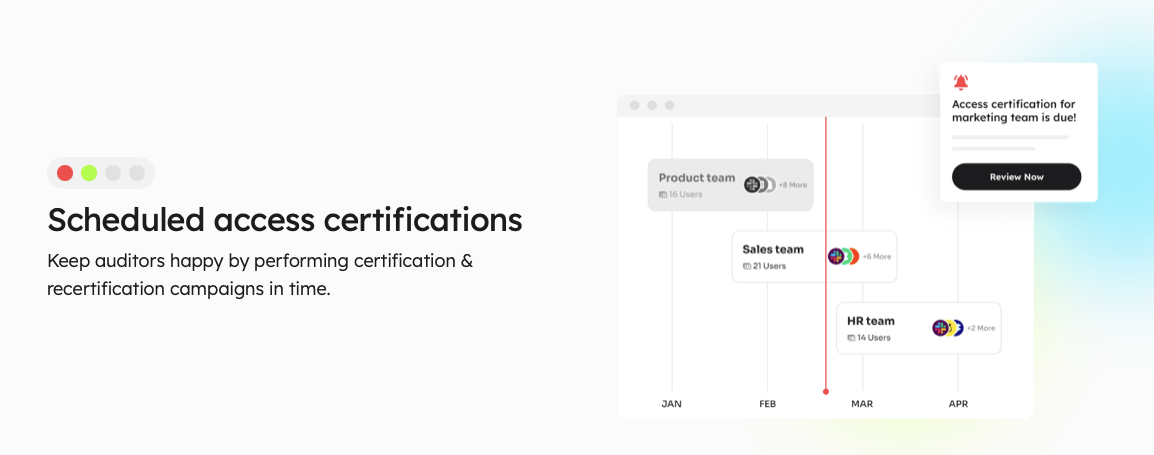
Access permissions undergo consistent scrutiny through recurring certifications, swiftly identifying and resolving any security vulnerabilities. This ongoing process assures robust access controls, ensuring your organization's sensitive information is safeguarded with unwavering vigilance.Strategic Access Reviews through Scheduled Certifications:
Zluri's scheduled certifications allow you to strategically plan and conduct access reviews at predetermined intervals. This ensures that access permissions undergo consistent and timely evaluation, reducing the risk of overlooking critical access issues.![scheduled access certifications]()
To streamline the certification process further, Zluri offers industry-standard certificate templates. These templates provide a standardized approach, simplifying the certification process for you and your team. Utilizing these templates ensures a comprehensive, accurate, and compliant certification process aligned with recognized guidelines.
Enhanced Data Security with real-time access reviews:
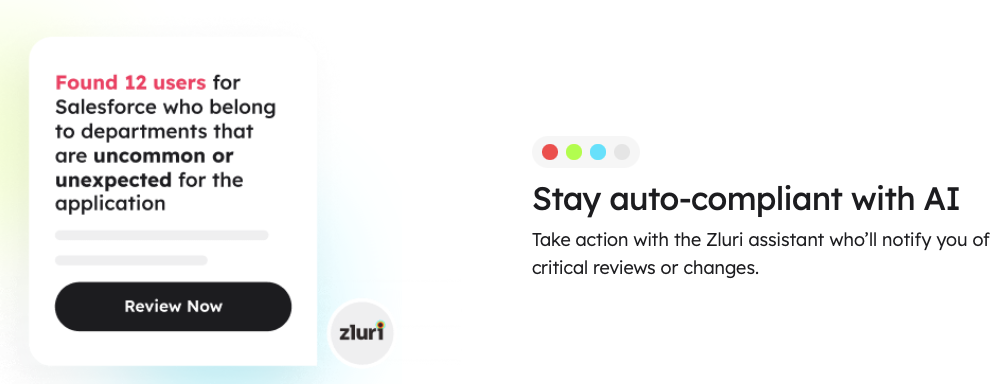
With AI-driven real-time access reviews, Zluri analyzes access patterns, user behavior, and system logs to swiftly identify unusual or potentially risky activities. This proactive approach enables prompt detection and alerts about anomalies, allowing you to mitigate security threats and safeguard your organization's sensitive data.![real time access sprawl detection]()
Zluri's access reviews also provide continuous monitoring, granting real-time visibility into access privileges. Stay updated on any changes or potential access-related issues, enabling you to swiftly address concerns and minimize the risk of unauthorized access or misuse.![stay auto compliant with AI]()
Moreover, Zluri's AI compliance capabilities offer intelligent insights and recommendations, aligning your access controls with industry regulations and standards, thus reducing the risk of compliance violations. Leveraging AI technology, Zluri simplifies the compliance process, making it easier for your organization to meet regulatory requirements effectively.
Zluri’s Auto-Remediation Capability
Beyond just reviews, Zluri goes the extra mile with its auto-remediation capabilities. Zluri takes swift corrective actions when access violations are detected, enhancing your organization's security and ensuring compliance.
By promptly revoking access for terminated employees or those with outdated privileges, Zluri helps mitigate the risk of unauthorized data breaches and ensures the security of sensitive information.
Follow these steps to automate the Access Review Process with Zluri:
Step 1: Access Zluri's main interface and navigate to the "Access Certification" module.
Step 2: Create a new certification by clicking "Create a New Certification." Assign a suitable certification name and responsive owner.
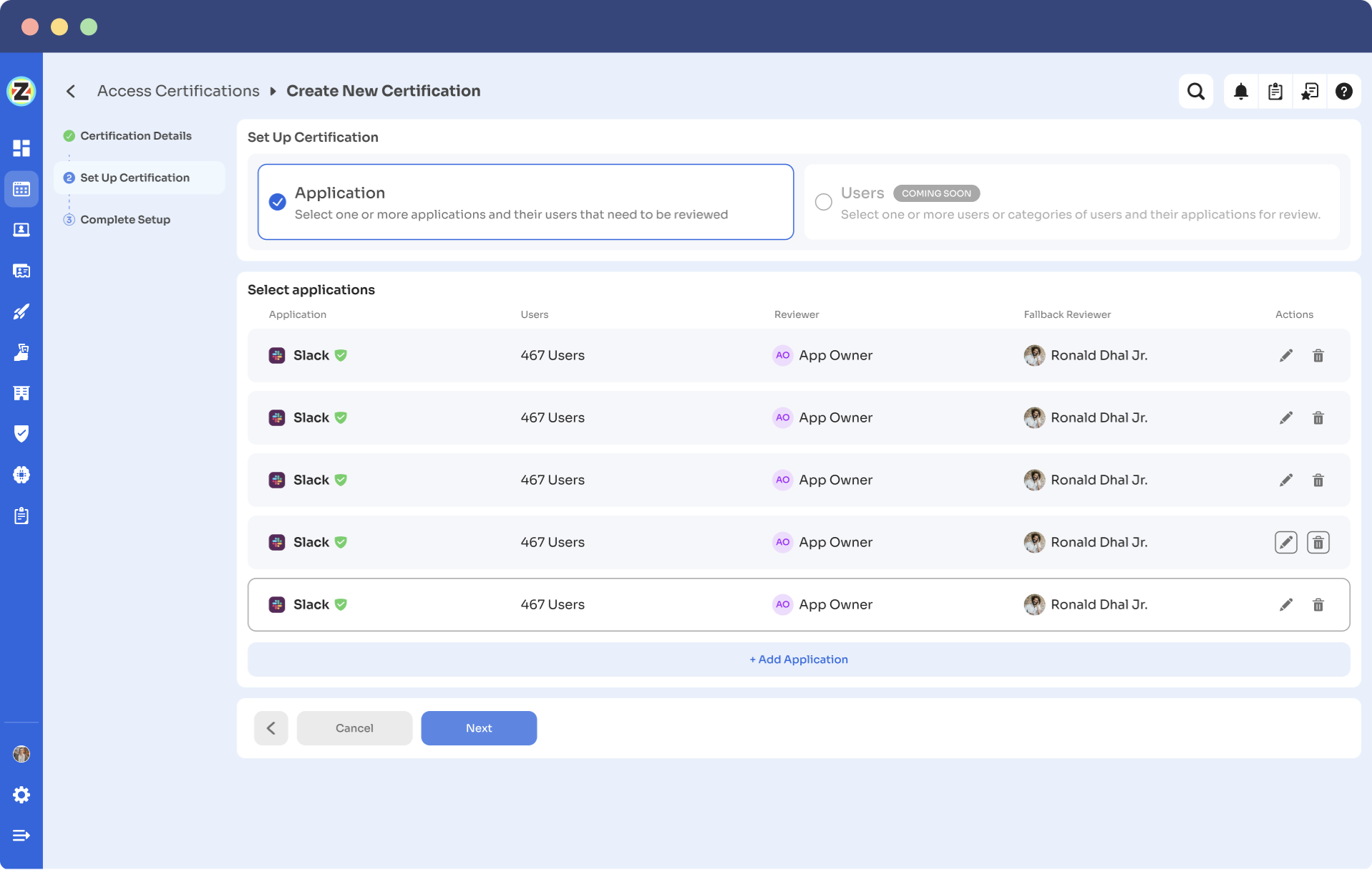
Step 3: Set up the certification by choosing the review method - either by Application or Users. For Application-based reviews, add the applications to audit users' access.
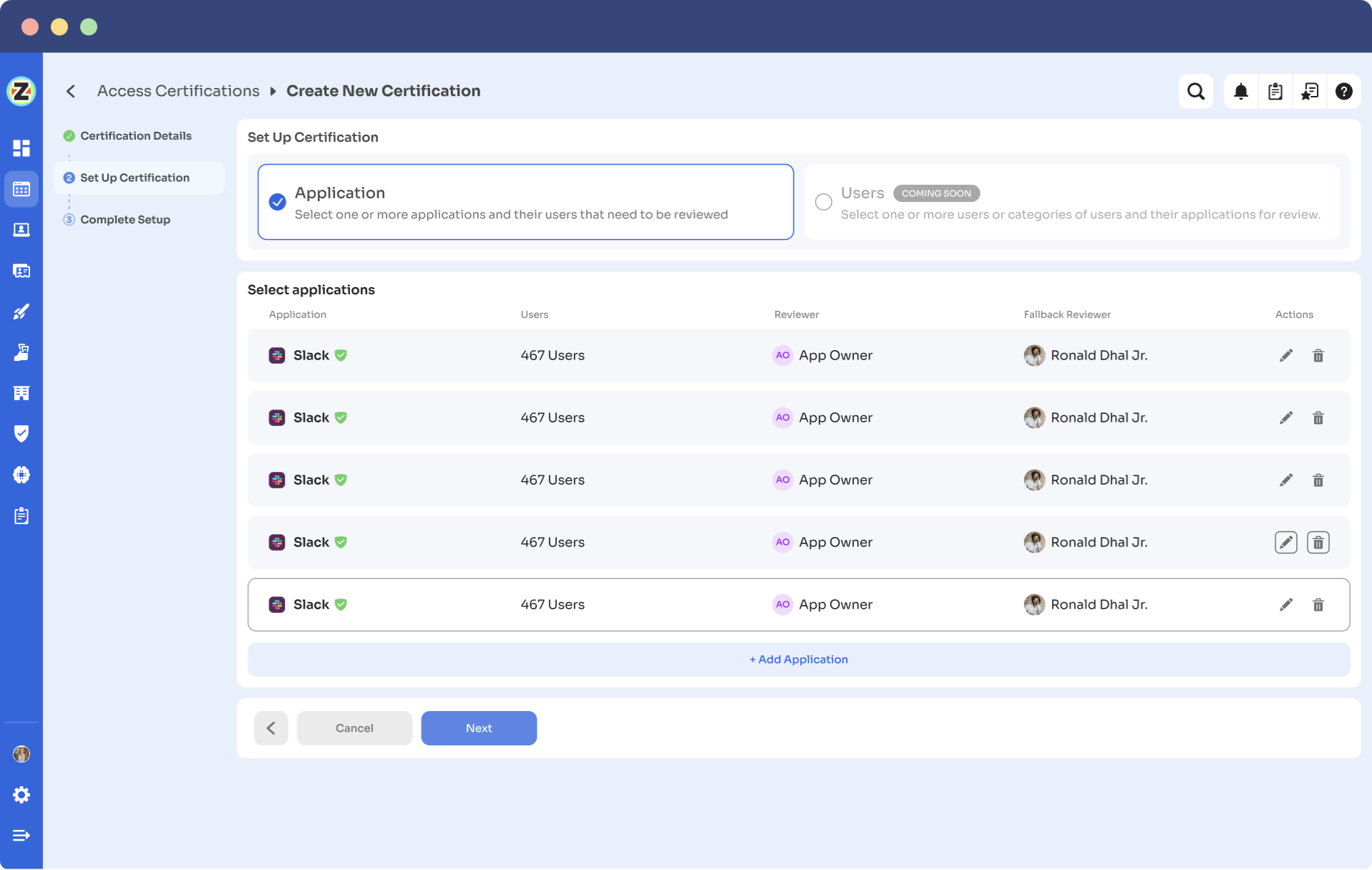
Step 4: Select primary and fallback reviewers from the drop-down menu. The primary reviewers are typically app owners. If primary reviewers are unavailable , fallback reviewer can carry forward the review process. So, choose the fallback reviewer thoughtfully for responsibility.
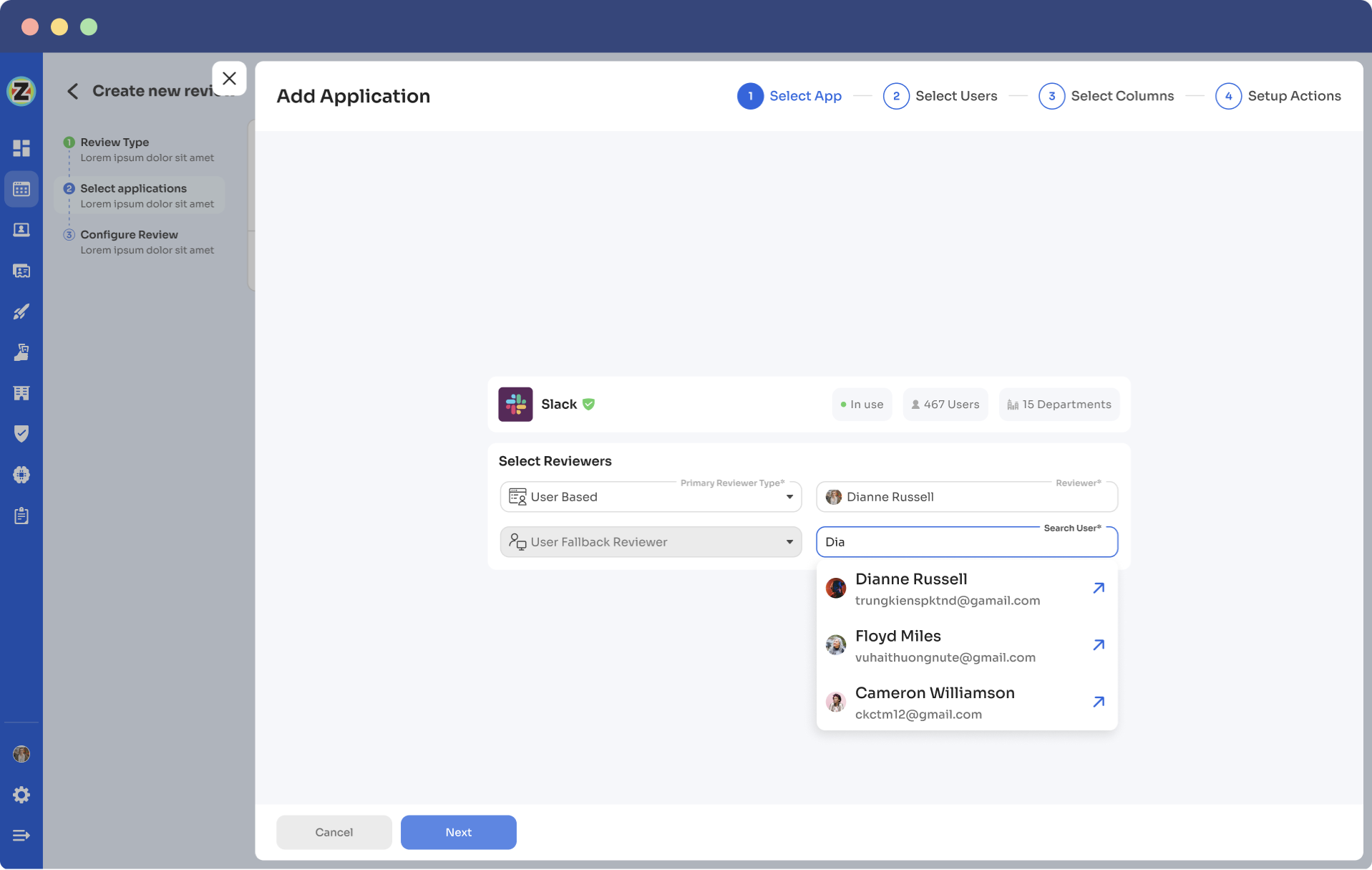
Step 5: Choose specific users to include in the certification process. Filter data points like user department, job title, usage, etc., as per your certification requirements for well-informed decisions by reviewers.
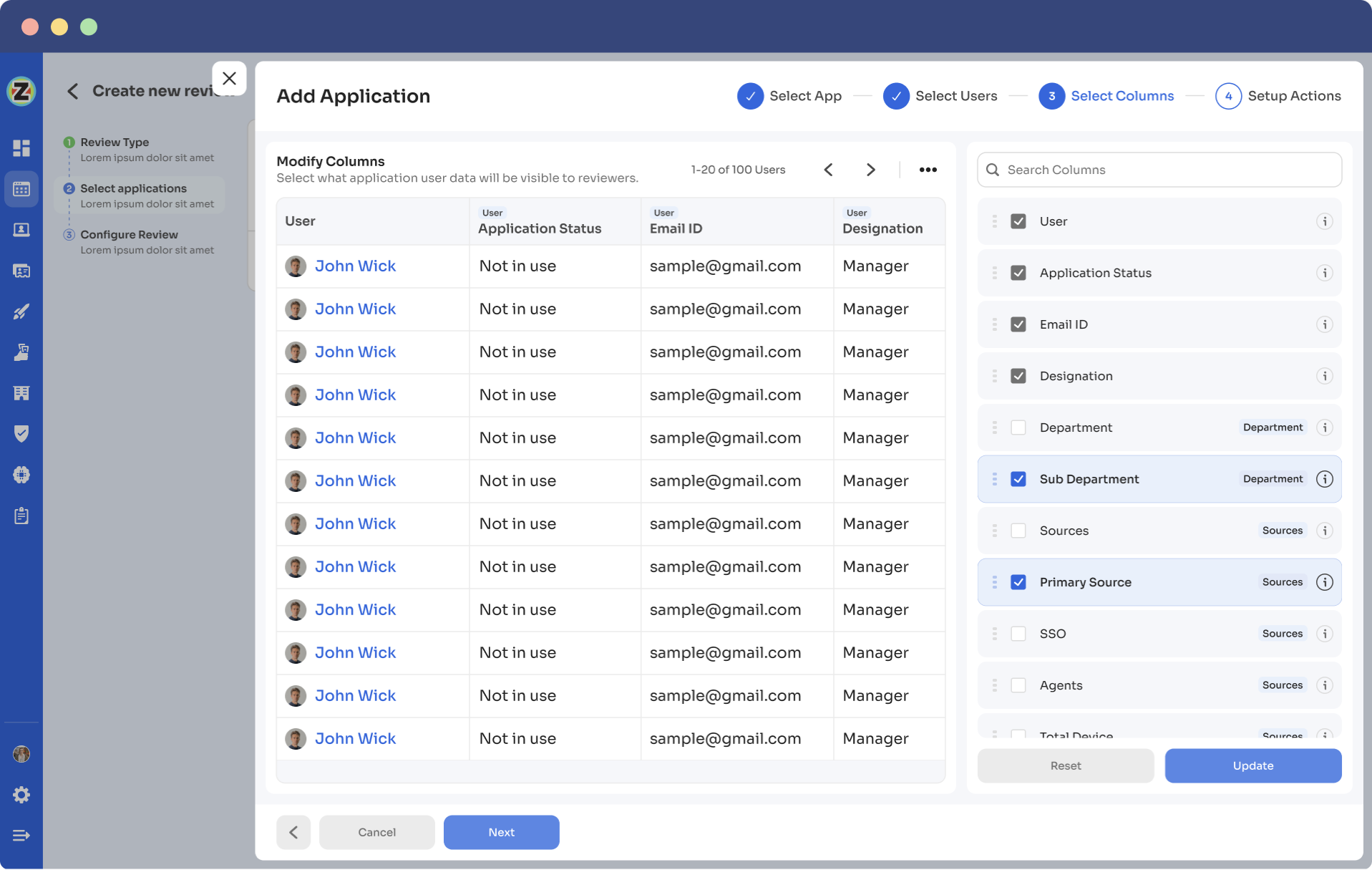
Step 6: Configure actions based on your needs, such as deprovisioning playbooks for rejection actions.Once you set up the action, click “add applications”.
You can add multiple applications for the same certification.
Step 7: Set start and end dates for the certification process to determine the review completion timeline. Optionally, save the template for future use.
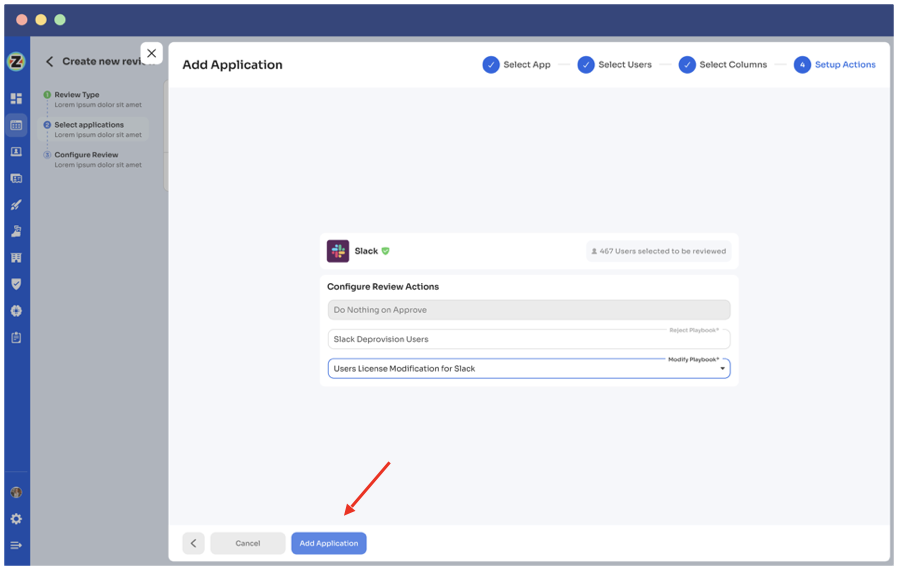
Step 8: Track the automated access review process by checking the 'Review Status.' Monitor pending, modified, declined, or approved reviews on a chart. Conclude the process by sending reports to reviewers via email after approval.
To explore Zluri's Identity Governance in-depth, schedule a demo today!
Pros
Zluri stands out from traditional IGA tools due to its seamless implementation process and user-friendly interface, making it incredibly easy for your IT teams to adopt and use.
It offers deep discovery capabilities and a unique SaaS data platform that sets it apart from existing solutions, ensuring optimal performance and security in your cloud-based environment.
Further, if you're looking for responsive customer support, this is the most ideal tool. Its support team is dedicated and readily available to address any concerns or issues that your team may have, ensuring a smooth and efficient experience with the tool.
Customer Rating
G2: 4.8/5
Capterra: 4.9/5
2. Saviynt Enterprise Identity Cloud
Saviynt IGA is a powerful tool that prioritizes seamless application and infrastructure access for users while maintaining compliance. It simplifies the identity governance and administration (IGA) process by enhancing organizational agility through automation and intuitive workflows.
With Saviynt IGA, users can enjoy smooth access to applications and infrastructure, ensuring their productivity is not compromised. The tool streamlines IGA operations by automating key processes and leveraging intuitive workflows, making identity management more efficient and user-friendly.
Moreover, Saviynt IGA ensures compliance by implementing robust controls and policies. It helps organizations meet regulatory requirements, enforce segregation of duties (SoD), and prevent unauthorized access, reducing the risk of compliance violations.
Pros
The tool offers your team a sleek and well-designed interface, making it convenient for them to navigate and use its features to its full potential.
If scalability is your priority, this tool is the ideal choice. It offers a high degree of scalability, allowing you to easily expand its capabilities to meet the evolving needs of your organization.
Cons
Certain features of the system may exhibit malfunctions, potentially causing capability issues for your team. For instance, when a user switches roles within the organization, their entitlements are supposed to change accordingly. However, if the entitlements do not update properly, Saviynt removes the existing entitlement but fails to re-issue the same entitlements, leaving the user without any entitlements. Further, this can lead to identity management complications.
Customer Rating
G2: 3.5/5
Capterra: 4.5/5
3. IBM Security Verify Governance
IBM Security Verify Governance is a comprehensive identity governance and administration solution that is specifically designed to retrieve and manage data from multiple sources. It accomplishes this through a combination of modules, a directory integrator, and a database. This appliance-based solution offers a range of capabilities to govern and administer identities within an organization effectively.
The platform provides robust capabilities for provisioning, auditing, and reporting on user access and activity throughout the entire lifecycle. With its comprehensive lifecycle management, compliance, and analytics features, this solution caters to both on-premises and cloud-based environments.
Pros
The platform offers extensive security measures facilitating user access management and conducting risk-based authentication analysis before granting system or application connectivity
This versatile tool offers your team the convenience of seamless operation, ensuring smooth functionality in both cloud environments and offline workstations.
The tool presents flexible deployment options and boasts effortless implementation into your systems, ensuring convenient adoption of IGA by your team.
Cons
If affordability is a key consideration for you, this might not be the most suitable choice. The pricing model of this solution is based on the number of features, which means that utilizing certain features may incur additional costs as they are add-ons.
Customer Rating
G2: 4.3/5
Capterra: no reviews
4. Okta Identity Governance
Okta's Identity Governance platform empowers your IT team to manage user access across systems and applications efficiently. Centralizing access controls simplifies the process of granting or revoking access, saving time and minimizing administrative burdens. This enhances productivity while reducing the risk of unauthorized access.
Okta's Identity Governance also prioritizes security by providing robust auditing and reporting capabilities. Your team gains visibility into user activities, enabling them to track and monitor actions, generate comprehensive reports, and ensure compliance with regulatory requirements during audits.
Pros
This tool offers an intuitive and user-friendly interface, making it convenient for your IT team to navigate through the tool and efficiently perform access management tasks.
The platform empowers your team to seamlessly integrate with various applications due to its robust integration capabilities. Whether direct integration or manual addition, the tool enables you to connect apps and monitor access for audit purposes effectively.
Cons
The tool may pose challenges during the setup process, requiring additional time and effort from your team. This complexity can result in delays in efficiently managing user access.
The process of configuring directories and synchronizing user data can be time-consuming and labor-intensive, posing a potential disadvantage in terms of the effort required for implementation.
Customer Rating
G2: 4.5/5
Capterra: 4.7/5
5. Symantec IGA
Symantec IGA offers a comprehensive suite of access governance and identity management capabilities. With this solution, you can effortlessly manage user access to both on-premise and cloud applications, automating the provisioning of new entitlements and removing unnecessary ones throughout the identity lifecycle.
Symantec IGA also includes self-service functionality, empowering end users to request new access, manage their profile attributes, and reset forgotten passwords. This self-service capability reduces the burden on your service desk, enhancing efficiency and user satisfaction.
Furthermore, the solution streamlines the access governance processes associated with reviewing and approving entitlements. By ensuring a least privileged access posture, Symantec IGA aids in maintaining a secure environment by granting only the necessary access to users.
Pros
It offers reporting and auditing capabilities, empowering your team to effectively track and analyze user activities, access permissions, and system events for enhanced security and compliance.
This option is worth considering if you seek a user-friendly interface for your team. It offers a convenient configuration process, allowing your team to integrate it with your existing systems efficiently.
Cons
The tool poses troubleshooting challenges which can lead to extended periods of system downtime and disruptions. It can hinder your team's ability to quickly and accurately address issues, resulting in time-consuming and inefficient troubleshooting processes.
If you require a tool with custom connectors for your team, then this may not be the ideal option. The process of creating custom connectors can be quite challenging with this tool.
Customer Rating
G2: 3.4/5
Capterra: 4/5
6. Microsoft Entra Identity Governance
Microsoft Entra Identity Governance offers robust identity governance and administration (IGA) capabilities that assist your IT team in meeting compliance requirements. With Azure AD, you can automate access request workflows, conduct access reviews and certifications. This solution streamlines user access management, conducts regular access reviews to ensure compliance, and maintains a detailed audit trail of user activities.
Microsoft Entra provides secure user access, empowering your team to extend access to external users while maintaining control and governance. You can grant external users access to specific resources and applications, define their access levels, and enforce security policies to safeguard your organization's data. By leveraging this platform, your team can effectively manage user access, ensure compliance, and enhance security within your organization.
Pros
This tool empowers your team to enforce stringent authentication policies, granting them control over access management while effectively mitigating insider threats and minimizing risks.
The platform seamlessly integrates with third-party applications, enabling efficient management of external identities (vendors, contractors, etc.). It allows granting limited permissions to external users, effectively safeguarding sensitive data from unauthorized access.
Cons
Troubleshooting technical difficulties with the Microsoft team can be time-consuming, and accessing the necessary technical support can be troublesome too.
The cost of Azure AD can be high, especially for organizations with large user bases and complex infrastructures. Its pricing is determined by factors like the number of users, data processing, and required services, resulting in potential significant expenses for such organizations.
Customer Rating
G2: 4.2/5
Capterra: 4.8/5
7. RSA Identity Governance & Lifecycle
RSA Governance & Lifecycle is a comprehensive IGA tool that empowers your organization with company-wide identity governance and administration capabilities. With this tool, your IT team gains clear visibility into user access, enabling them to identify who is accessing what resources within the environment precisely.
One of the key features is its ability to accelerate access certification processes. By automating access reviews and certifications, organizations can streamline the validation of user access rights, ensuring compliance with regulatory requirements and internal policies.
By considering relevant access control factors, such as roles, responsibilities, and job functions, the tool enables your team to make the right access decisions, granting appropriate access levels to users while minimizing the risk of unauthorized or overprovisioning.
Pros
The platform has a user-friendly design, offering dedicated versions for both iPhones and iPads. This ensures a seamless and intuitive user experience for your team members accessing the software on these devices.
It minimizes the need for extensive customization while also providing ample flexibility based on users' needs. This offers significant benefits as it reduces implementation time and costs, allowing your team to tailor the tool to their specific requirements and workflows.
Cons
The access provisioning and user account setup do not occur instantly or in real-time in this system. There are inherent delays and time intervals before the provisioning changes are implemented and effective. Consequently, this may introduce delays in the provisioning process within your organization
If affordability and the tool’s straightforwardness are priorities for you, this may not be the ideal solution. It is relatively expensive and requires a learning curve for new users to manage and govern access effectively.
Customer Rating
G2: 4.7/5
Capterra: 4.6/5
8. Oracle Identity Governance
Oracle Identity Governance simplifies user access management by automating access provisioning and deprovisioning processes, saving time and effort. The platform ensures compliance by adhering to predefined rules and guidelines, reducing the risk of penalties.
With Oracle Identity Governance, you gain access to advanced analytics and intelligent algorithms that enable the detection and mitigation of security risks. The platform can identify and respond to unusual activity in real-time by analyzing user behavior and access requests.
This proactive approach empowers your team to swiftly address security issues, minimizing the likelihood of data breaches and unauthorized access. Oracle Identity Governance strengthens your organization's security posture and effectively safeguards critical assets.
Pros
This tool efficiently handles access management for multiple users, making it a well-suited solution for large organizations. It remains effective even as your business expands and progresses over time.
The platform provides your team with complete flexibility to add groups, manage user access, user control, and more. It empowers your IT team to have control over access management and ensures a robust system for managing user permissions.
Cons
If ease of use is a priority for you, this might not be the ideal solution as the tool’s architecture is very complex, and it requires a substantial time investment from your team to grasp and utilize the tool's capabilities fully.
The tool presents a challenge with its intricate installation process, which can be demanding for users. Moreover, updating patches can be complex and arduous, amplifying the overall complexity of effectively managing the tool.
Customer Rating
G2: 3.7/5
Capterra: 4.4/5
9. ForgeRock Identity Governance
ForgeRock Identity Governance is a powerful solution that enhances identity and access management processes, prioritizing security, compliance, and efficiency for your organization. ForgeRock Identity Governance leverages the ForgeRock Identity Cloud, AI, and machine learning to ensure precise access control for every identity. It enables automation of account and entitlement provisioning, access request workflows, ongoing access certifications, and enforcement of segregation of duties policies.
The tool simplifies user onboarding, access changes, and offboarding procedures, ensuring that the appropriate individuals have timely access to the necessary resources. This streamlines administrative tasks and reduces the potential for unauthorized access or data breaches.
In addition, ForgeRock Identity Governance offers comprehensive compliance reporting and auditing features. Your team can generate detailed reports on user access, permissions, and activities. These reports are crucial for meeting regulatory requirements and successfully passing audits. They adhere to industry standards and regulations while identifying areas that require attention or improvement.
Pros
It provides your team with an intuitive platform to manage access and enhance security measures efficiently. Its simple design ensures convenience and ease of use, enabling seamless access management processes.
Setting up and configuring the tool is straightforward, allowing your team to get up and running quickly. This simplicity saves time and effort, ensuring a smooth implementation.
Cons
The tool has limitations when it comes to integrating with certain systems, particularly Unix-based systems. This limitation can restrict your team's ability to manage access to these systems effectively and may introduce potential security risks.
upgrading its IAM system demands a significant investment of time and effort from your team, thereby limiting their ability to concentrate on other crucial tasks such as risk prevention, compliance maintenance, etc.
Customer Rating
G2: 4.4/5
Capterra: 4.8/5
10. SAP Access Control
SAP Cloud Identity Access Governance offers a centralized platform for effectively managing user identities throughout your organization. It provides efficient user provisioning, deprovisioning, and lifecycle management capabilities.
The solution empowers your team to establish and enforce access controls based on roles, responsibilities, and business policies. It includes robust segregation of duties (SoD) functionalities, which prevent conflicts of interest and potential fraudulent activities by ensuring separation between incompatible duties.
Additionally, the platform automates access reviews and certification processes, enabling your GRC team to validate and confirm the appropriateness of user access efficiently. This automation saves time and effort by providing a systematic and streamlined approach to reviewing access privileges.
Pros
This tool offers an array of comprehensive features that assist your IT team in seamlessly detecting, managing, and preventing risk violations.
It provides robust control and monitoring capabilities for user authorizations, significantly aiding your team in identifying Segregation of Duties (SOD) conflicts.
Cons
The platform's initial implementation demands a higher level of effort from your team compared to other solutions. Thus, your team may require a significant amount of time to ensure a successful deployment.
Integrating the tool with other applications can be complex, involving compatibility issues, data mapping, and establishing secure connections. This may require additional time, resources, and technical expertise to ensure a successful integration.
Customer Rating
G2: 4.1/5
Capterra: 4.5/5
Related Blogs
See More
Subscribe to our Newsletter
Get updates in your inbox