Security & Compliance
• 13 min read
Saviynt vs One Identity - Which is The Best IGA Tool?
8th September, 2023
SHARE ON:
Saviynt is recognized for its holistic approach to IGA, focusing on both identity governance and privileged access management (PAM). Its robust feature set includes identity lifecycle management, role-based access control (RBAC), policy enforcement, and compliance reporting.
OneIdentity, on the other hand, is acclaimed for its precision in identity and access management. Its IGA suite encompasses identity lifecycle management, access request and certification, and audit capabilities.
While both tools offer distinct functionalities, you, as an IT Manager, must evaluate before choosing the suitable IGA platform for your organization.
As an IT manager, choosing IGA solutions is paramount to ensuring data security, compliance, and efficient operations. Two prominent contenders in this space are Saviynt and One Identity. Let's delve into why thoroughly comparing these tools is essential for an IT manager to make an informed decision.
Comparing Saviynt and One Identity becomes essential because each tool brings unique strengths to the table. Your IT environment is distinctive, and what suits one organization might not necessarily suit yours. You can identify which features align better with your company's needs through a detailed comparison.
For instance, Saviynt boasts advanced role management capabilities, which can streamline the assignment of access rights based on job roles. This could be a game-changer for your e-commerce business, ensuring that employees in customer support are granted only the necessary permissions without compromising sensitive financial data.
On the other hand, One Identity offers robust integration options, which could be pivotal if your company relies on diverse software and systems. This integration prowess could facilitate a smoother access management process, enhancing user experience and overall productivity.
So, let's move ahead and compare both tools based on different parameters to help you decide which IGA solution will best meet the requirements of your IT team.
Saviynt vs One Identity - A Detailed Comparison Based on Different Parameters
1. Unique categories
Saviynt: This is an IGA and access management tool to manage privileged accounts and other IT entities with a zero-trust approach and protect them from insider breaches and security violations. Most organizations that use this application have 10k+ users, and it's mainly designed for large organizations.
One Identity: One Identity by Quest is a cloud-native IGA solution to enforce control over your digital assets and have a unified approach to managing every cloud asset of your organization without compromising on compliance requirements. Like Saviynt, One Identity is also used by organizations with over 10000 users and employees.
2. Integration capabilities
Saviynt: Saviynt supports out-of-the-box integrations with common cloud and hybrid applications for access and lifecycle management, connecting with ERP services, managing certificates, and much more. Some applications you can integrate with Saviynt are AWS, Databricks, Oracle EBS, Microsoft 365 Finance and Operations, Google Cloud Platform, Azure ID protection, etc.
Moreover, you can find integration options for any requirement or create your own. These integrations increase the efficiency of the overall identity management process as you allow all data to be synced frequently rather than manually transferring them.
Your IT admin can securely connect these applications like the active directory and enable secure dataflow for processes like provisioning and deprovisioning. For instance, any newly onboarded user is created first in the organization's active directory. This identity automatically appears in the IGA application, where the IT team can provide them access and entitlements.One Identity: Like Saviynt, One Identity also has integration facilities. This app integrates with cloud, native, on-prem, and hybrid applications, directories, and more. You can improve this IGA tool's functions by integrating it with necessary applications like ServiceNow, Ping Identity, One Login, AWS, Google Cloud Platform, Okta, Azure, etc. Together, you can aim for a holistic approach to identity governance and administration by selecting the right tools for integrations.
For example, you can integrate One Identity with Service Now, which can help you manage user requests, automate approvals, and process them through One Identity. That’s how a native integration helps with increasing the efficiency of your tasks and carrying them out with no errors and on time.
3. Lifecycle management
Saviynt and One Identity have automated lifecycle management that simplifies onboarding applications, assets, and users and manages them from when they join until they depart. Here is how lifecycle management works in Saviynt and One Identity.
Saviynt: This tool helps your IT teams to set up a smooth user onboarding and offboarding process with the help of automated workflows. Whether it’s a user, a third party, or a machine identity, you can onboard in a few steps and manage them centrally. For users and third parties, you can provision access, enforce controls and permissions required, and allow them to access mandatory digital applications with the least level of permissions.
You can automate both provisioning and deprovisioning so that users have access instantly when they join, and it’s revoked after they leave without delays. These automated workflows reduce the manual effort and remove any possible errors while providing and revoking access.
You can also remove approval workflows for low-level privileges and less sensitive applications. For instance, providing access to a company-wide communication application is mandatory for all users and requires no review from approvers. For other provisioning activities and access requests, automated approval can be enabled. Approvers can approve or deny through the mobile app or the desktop console in a single click to pass it to the next step.
Your IT administrator can create these workflows in the Saviynt application, create custom roles and policies, and apply group entitlements which get applied during provisioning when you select an appropriate role.One Identity: One Identity provides the capability to automate the manual and error-prone lifecycle management process. You can connect and sync one identity with your active directory or any other workforce directory to feed new user data into this system. One Identity captures user name, department, role, joining, etc, for efficient and fast automated onboarding. It also allows you to create entitlements for each user group to map them while onboarding a new user easily.
For instance, you can create or import your organization’s roles and definitions, like administrators, regular users, special users, Analysts, etc., for every single cloud application you have, which gets applied per the functional role of the user you onboard. If a certain application has custom roles and attributes, you can also import it to One Identity and apply that to relevant users directly. With this custom entitlement option, you can be assured that users get the right level of privileges while being onboarded.
You don’t have to do anything to process the offboarding of the departing user. Rather, One Identity automatically removes the leaving user’s identity as it’s synced with the active directory.
In addition, One Identity can transfer how you process provisioning and deprovisioning with the help of workflows, construct them based on logic, and execute them automatically.
4. Access request management
An IGA application should have a smooth and easy-to-build access request feature because granting access to applications can also lead to security issues. The app should allow the user to request access to any application while giving the IT team full control over whether access is to be given or not.
Both Saviynt and One Identity have an access request feature through which users can request access to applications and track their status. Here is how this functionality works in both applications.
Saviynt: Users can request access to applications anytime through the desktop console or Saviynt’s mobile application. Or they can also request access if you have Saviynt integrated with Slack or Microsoft Teams. Saviynt offers intelligent suggestions to users on applications based on what they requested before and what their peers use for users to identify new applications to which they can safely get access.
Moreover, your IT admin can set up controls and policies to apply segregation of duties and prevent giving higher amounts of privileges while providing access. For this to happen, Saviynt shows the request details and possible risks and violations of granting access. So, approvers can make quick and informed decisions about who should receive access to what. To be more confident and specific about their decisions, they can use API Slack integration to gain expert consultation.
Your IT teams can also design custom approval workflows with the help of drag-and-drop options in the administrator console. You can create them without any code, save them, and reuse them for any application access request.
The team can also save time and provide quick access by assigning zero-approval workflows for less critical applications. This also helps users, as they can receive access in no time. They can also track their requests and see their status in the same place where they requested access. This is how the access request component of Saviynt works.One Identity: One Identity has an automated access request option, which is not elaborate like Saviynt or other IGA tools. One Identity allows you to manage complex access request approval workflows and create custom workflows for different applications. Users will be able to place their data or resource access request, which is processed based on the workflow.
Managers can decide whether access has to be granted or not. But there are no self-service platforms available with One Identity like Saviynt, or most common IGA tools, which is a drawback for One Identity users. Rather, One Identity has a shopping cart for users through which users can request access to privileged assets or any other privileges.
This works more like an access certification where users with the least privileges request access to elevated permissions, which approvers can review and attest or deny access for a given time.
5. Security and Compliance
Both Saviynt and One Identity take care of your identity management, security, and governance and have compliance checks and certifications. Here is how these applications secure your digital identities and ensure that it meets with compliance.
Saviynt: This application has multiple features to protect the digital identities of your organization and the overall IT network against cyber threats and breaches. It secures identities in three ways, allowing your IT team complete visibility over identity management, managing user access, providing only what’s required (through role-based and attribute-based access control), and enabling risk-based governance.
Regarding access management, you can adopt a zero-trust policy with Saviynt, where access levels are set to low and only required amounts by default. Any user who wants access to elevated entities has to require it through the access certification option (Just-in-Time Access).
At any point, your IT admin can ensure no standing privileges for any identity, which means the least chance of attack over your critical data. Even the allowed entitlements in privileged access management can be tweaked to avoid leaving with risky privilege combinations.
Saviynt also supports SoD (Segregation of Duties) as it automatically detects and prevents user access with policy conflicts where two different privileges are made available for the user. For instance, being able to update the user data as well as delete them or generate reports. Any potential risks or policy violations are brought to IT teams’ notice so that they can take action instantly, mitigate the issue, and isolate the affected identities and entities.
Through continuous monitoring, risk management, pre-built controls, and audit-friendly reporting, Saviynt manages compliance and regulatory standards. You can align these controls so that your entities perfectly meet standards like HIPAA, PCI, COBIT, CIS, etc.
In short, Saviynt lets your organization have an intelligent digital perimeter without even having a VPN that acts as a gateway for your network.One Identity: It helps you manage and monitor all of your users, including third-party vendors, and prevent any security violations they might commit with the help of user behavior analytics. One Identity also has features to track granular parts of users accessing privileged networks, like recording mouse movements, analyzing login patterns, and storing and playback recorded sessions.
There are many features that Saviynt has to ensure the security of your IT network. It allows you to adopt a least privilege policy where you limit the privileges to all users. If they require privileged access, they can request, and IT teams can manage these requests and review them by setting up Just-in-Time access which allows them to have higher permissions only for a limited time. Any other access privilege modifications can be applied centrally through Azure or AD.
In addition, One Identity has strong multi-factor authentication features that you can set up along with your regular username and password to permit only authorized users to access privileged identities. It has flexible authentication features like message, email, biometric, RSA SecurID, or even integrates with any third-party authenticator.
One Identity also plays a huge role in cloud governance. It helps business owners with data governance, where they want to classify and manage unstructured, sensitive data that they don’t want the IT team to handle. Business owners can decide to clean up this securely, manage its access requests, assign proper ownership, and create approval workflows.
Further, to protect you from compliance failure fines, One Identity supports compliance management through which you can track compliance requirements of every on-prem, cloud, and hybrid application your organizations use and maintain it effectively. You can access audit-friendly recordings and session data of privileged data and its access management anytime from the application that supports your compliance maintenance.
With these reporting facilities and session recording data, you don’t have to fear audits and have every proof required to prove compliance and policy adherence.
After thoroughly comparing Saviynt and One Identity, you might have better understood which tool will be an ideal solution for your IT team's specific needs. However, it's crucial to note that other platforms are also available and worth exploring. One such exceptional platform is Zluri, which offers remarkable features that help your IT team streamline the identity governance process.
So, let's have a quick look at how Zluri works.
Zluri - The Autonomous & Automated IGA Solution for Your IT Teams
Zluri presents a robust IGA platform for ensuring users have the right access to your SaaS applications. With Zluri's IGA platform, you can effortlessly control and bolster the security of your SaaS apps. You can set up users, review their access automatically, and let them request access independently. This puts you in charge of ensuring everyone has the right access.
Let's dive into what sets Zluri apart from other IGA tools with its distinct and exceptional capabilities.
Powerful Discovery Engine
Zluri simplifies the task for your IT team to gather important details about your SaaS apps and users. It offers five discovery ways to find this info: SSO, finance and expense management, direct integration with apps, desktop agents (optional), and browser extensions (optional).
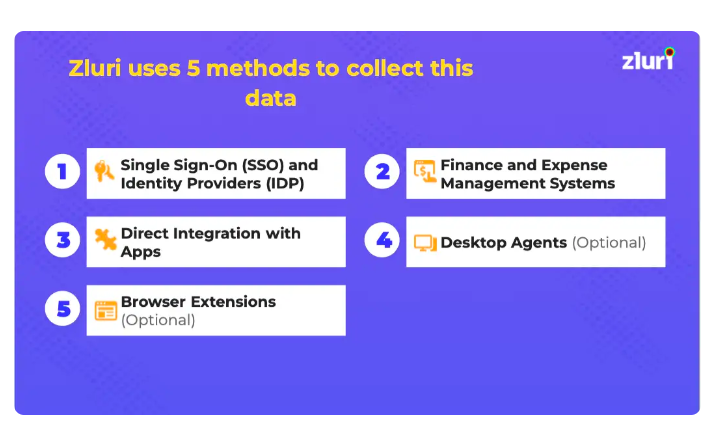
But Zluri does more than just find data. It connects with over 800 SaaS apps that help you to receive live information, useful insights, and AI alerts to stay updated. Through API connections, Zluri ensures you explore every corner of data in all your SaaS apps. You can be sure that Zluri shows you everything about your SaaS setup.
Streamline access management through Zluri’s Automation Engine
With Zluri's automation capabilities, your IT team can easily ensure employees have the correct access permissions. You can change access when an employee's needs change and remove access smoothly when needed. Wondering how Zluri achieves this? Let's take a quick look.
Lifecycle management
Zluri empowers your team to easily handle the user lifecycle by automating how they get access to and lose access to SaaS apps while working with your company.
With Zluri, ensuring your team members can use the right SaaS tools throughout their time at the company is a breeze. It makes setting up and removing access to these apps automatic, keeping your team's access secure while they're employed.
Automated onboarding
When a new user joins an organization, they have to be given access to the necessary tools for them to start working. This can be a pain-filled process for IT teams as they manually take care of the whole process, verify the user roles multiple times, and provide the right level of access after reviewing it through a line of approvals. This whole process is made shortened and seamless with Zluri with the help of automated provisioning.
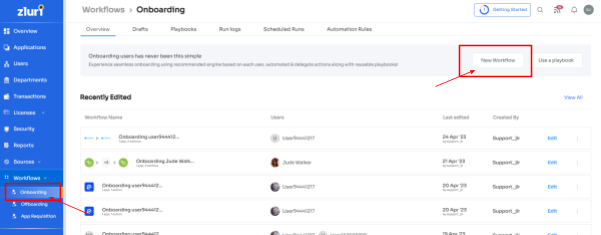
The workflows option of Zluri has a common interface for onboarding where you can view the most-used and recently-edited workflows, as in the picture below.

Here is the step-by-step procedure to create automated workflows for provisioning.
Under Zluri, go to workflows -> Onboarding, where you can create a New Workflow.
![Onboarding]()
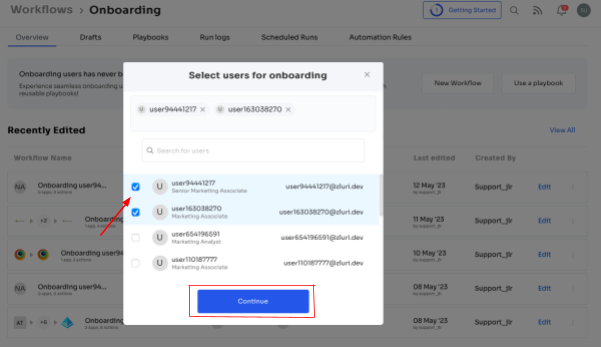
As you click on the New Workflow button, you will see a prompt where you can select users for onboarding or search from the given list. You can select users and press continue.
![Onboarding]()
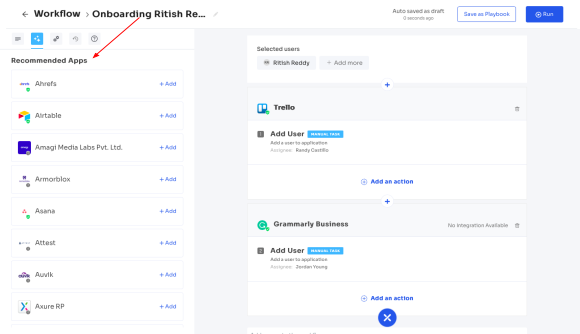
The next step is to provide access to the selected users. Zluri has intelligent app recommendations that you can use to select applications that users will need access to based on their roles, departments, and onboarding workflow history. |
For example, in the picture below, you can see the recommended apps for users where you can just click on add, select roles, and proceed to the next application.
4. Zluri also offers additional in-app suggestions to simplify provisioning tasks that you usually do away from the lifecycle management application. For example, adding users to the Slack channel so that the user can be added to relevant channels in the company-wide communication app.
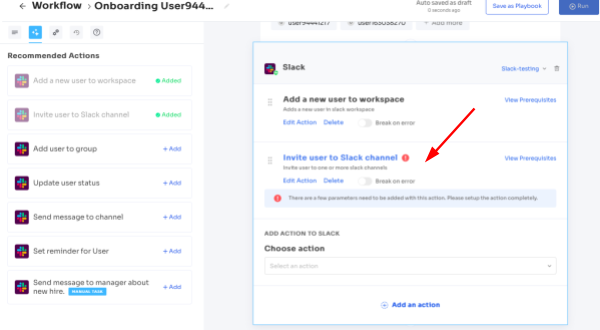
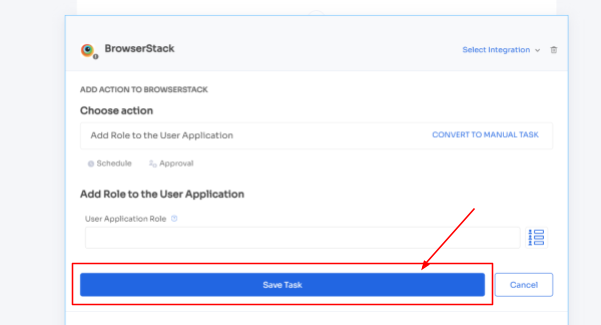
5. To execute certain actions, you need to Click on Edit Task and enter the required details. Your team can schedule the actions to execute the workflow on the day of onboarding. In order to save the actions, click on Save Task, and the actions will automatically be saved.
6. After this step, you can run the workflow to provide access to the new user. The whole onboarding process in Zluri will be finished in a few steps.
Note: You can also save this workflow as “playbook” for future use, where you can skip steps like adding applications, access levels, roles, channels, etc, and just proceed with adding users and finishing the provisioning process.
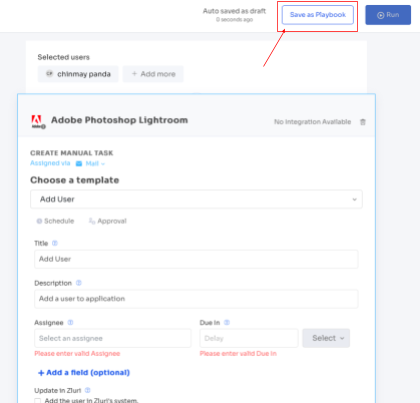
This is how automated provisioning works in Zluri.
Automated Offboarding
Like Onboarding, prompt offboarding is also crucial, as you can’t put your company’s data at risk by allowing users to access the organization’s applications even after leaving the company. Zluri has a simplified interface for offboarding to access the most-used workbooks from where you can start the offboarding process.
Here is how you can create an automated deprovisioning process and revoke the departing user's current access.
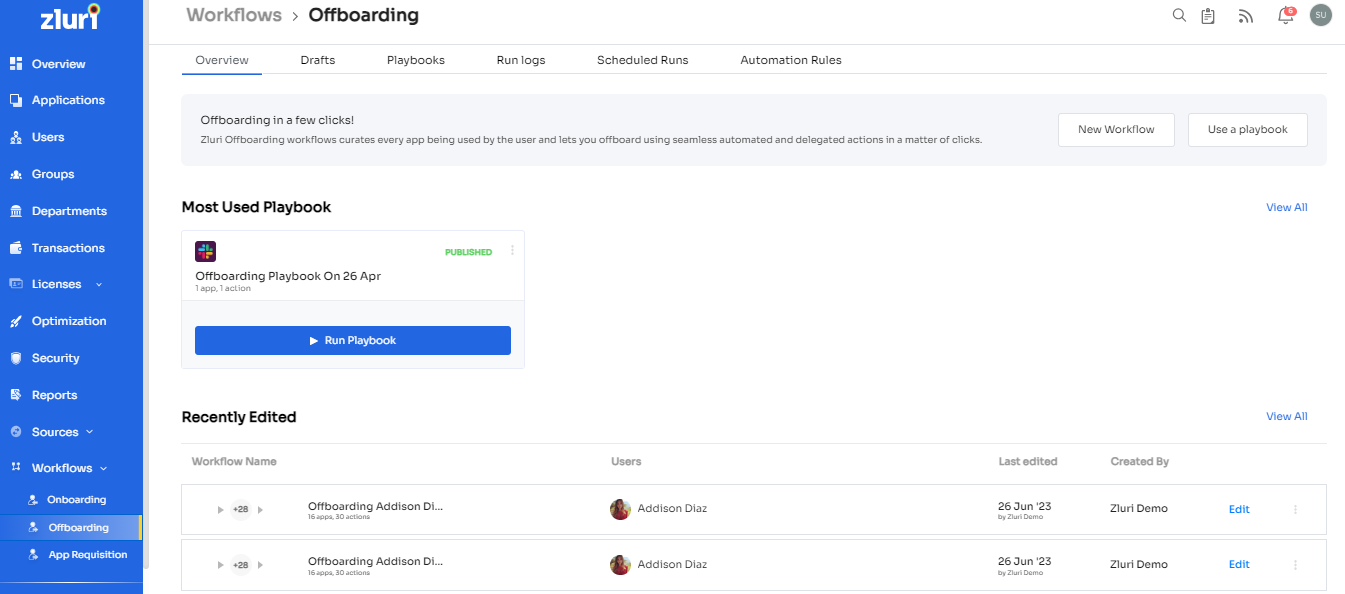
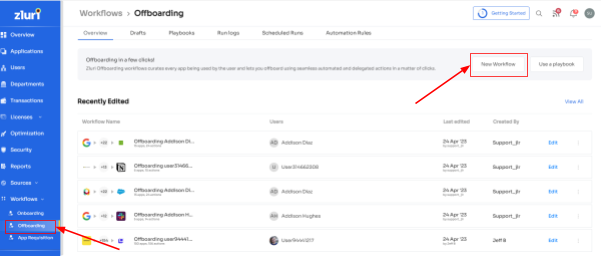
Start from Workflows -> Offboarding and click on Create a new workflow to start.
![Offboarding]()
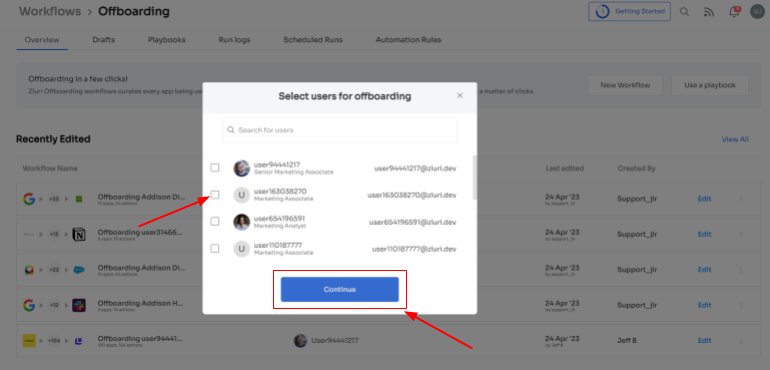
Create the workflow and start selecting users ready for offboarding, then press continue. You can select multiple users too.
![Offboarding]()
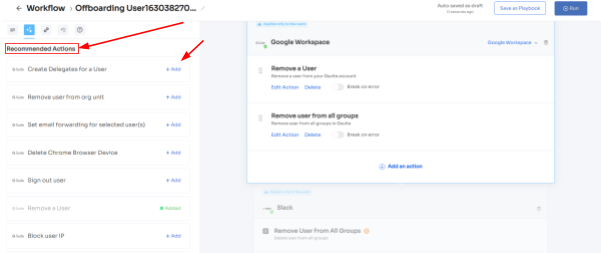
You can remove the access users have from here. Also, you can use recommendations and suggestions that Zluri provides for you on the left, which is to remove other privileges and to finally block the user from logging in.
![Offboarding]()
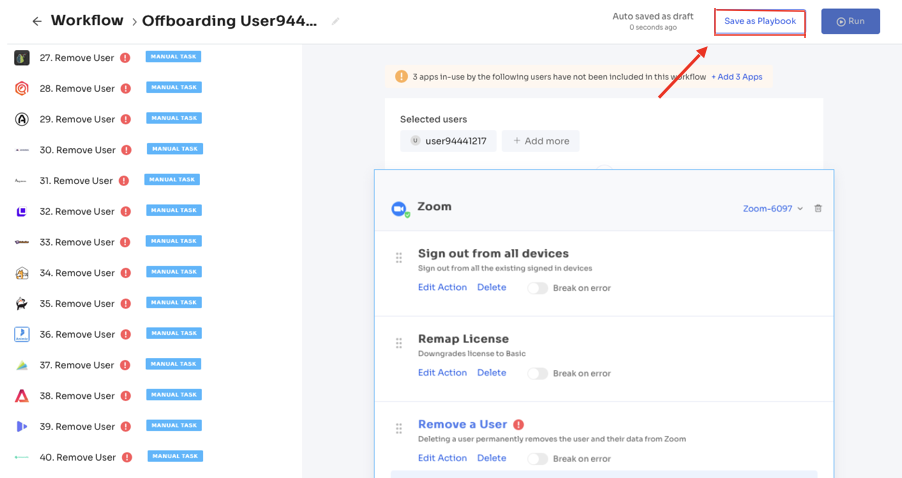
Once the previous step is done carefully, you can review the selection and proceed with running the workflow to revoke access instantly. Use the option, Save as Playbook to use this in the future.
![offboarding playbooks]()
This was how Zluri processes automated offboarding in a minute and secures your network and data from relieved users.
Ticketless access requests
Zluri goes beyond by making it even easier for your employees to ask for and get approval for access. It offers a self-serve model called an Employee App Store (EAS). This store has a collection of pre-approved SaaS apps and allows your employees to choose the apps that they need to simplify their tasks.

Even in this dashboard, your IT team can control what users should see, whether it’s only what they use or applications used by their peers and department as well. You can also block restricted, unapproved, and uncategorized applications for users and decide what information users should see about these applications.
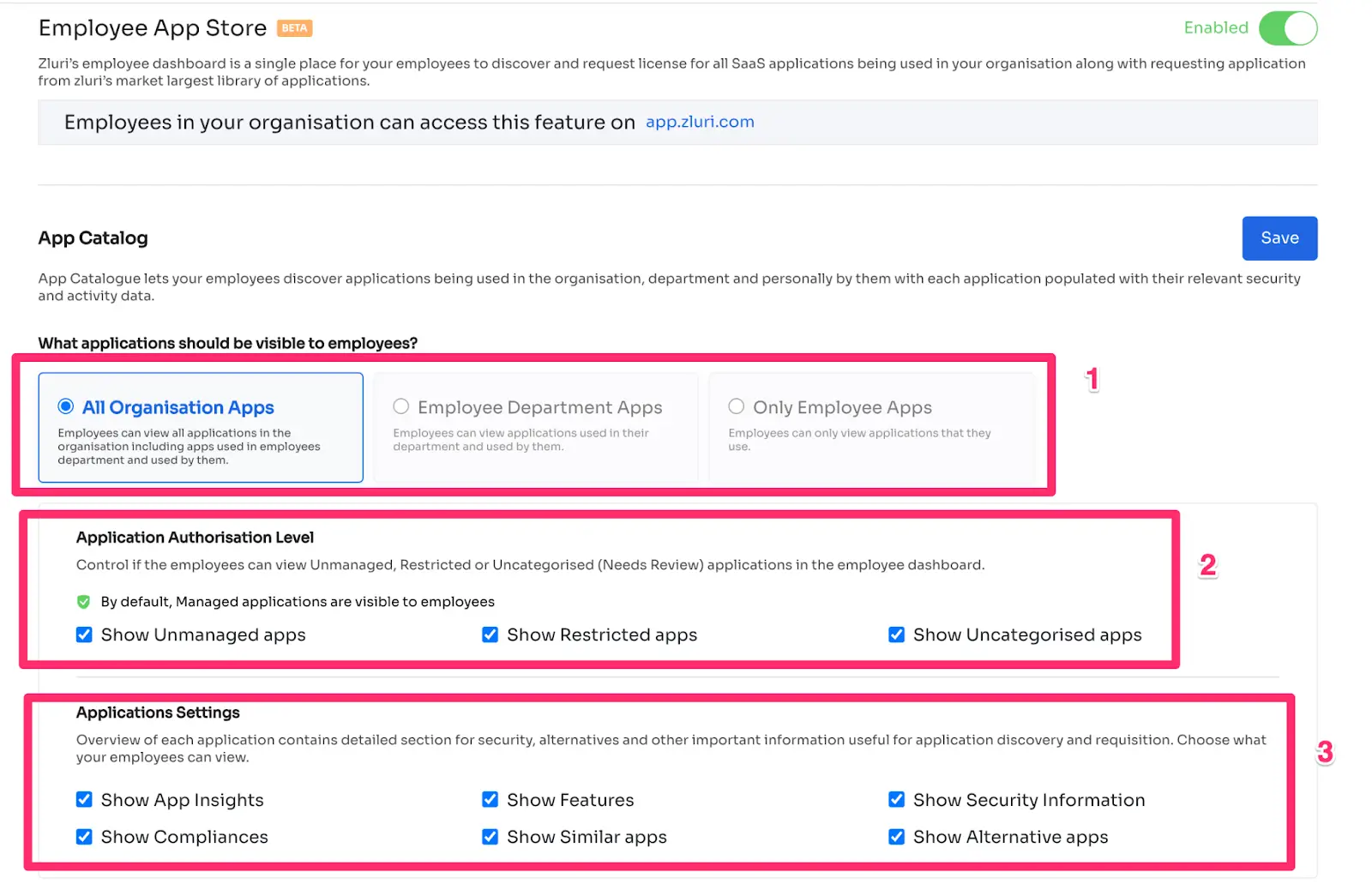
Users can also access the employee app store, requesting access to tools currently available in the organization’s stack and tools that can be procured. Any request they submit from here instantly reaches the IT team’s queue after the approval flow, if present. IT admins can review this and provide the least level of privileges possible.
For less sensitive applications, you can remove the approval workflow so that users receive instant access and no one has to waste their time.
Regarding the approvals, Zluri allows you to set up to three levels of approval, where you can set approvers like departmental leads, application owners, and IT managers.
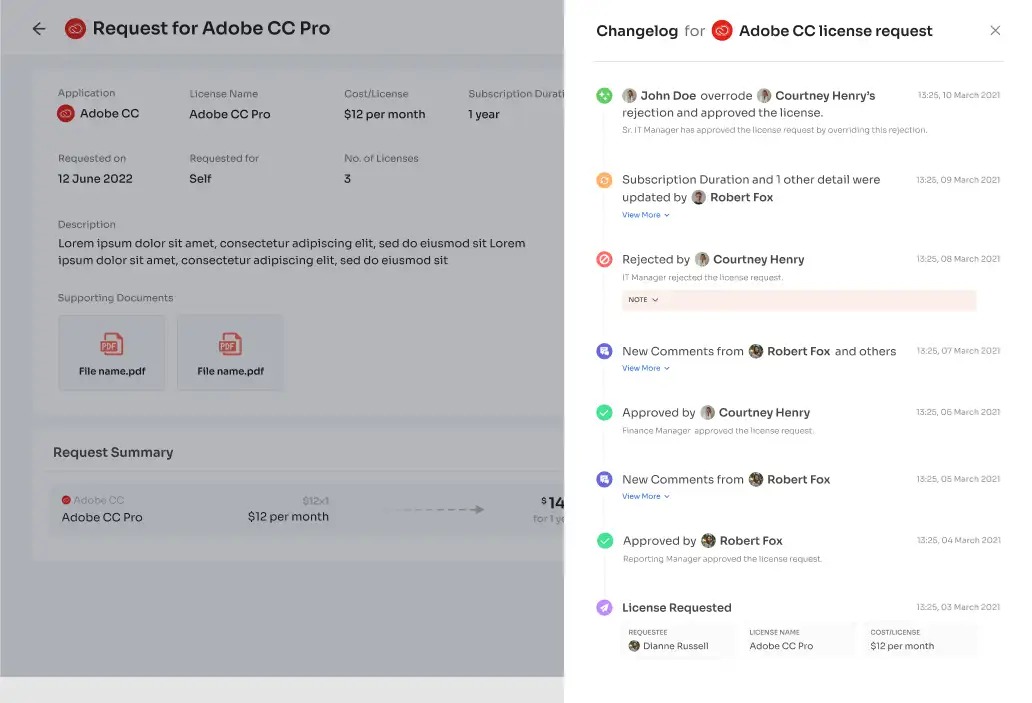
Users can also track the status of their applications from the option Changelog where the detailed flow of the request, as well as remarks from users, is mentioned.
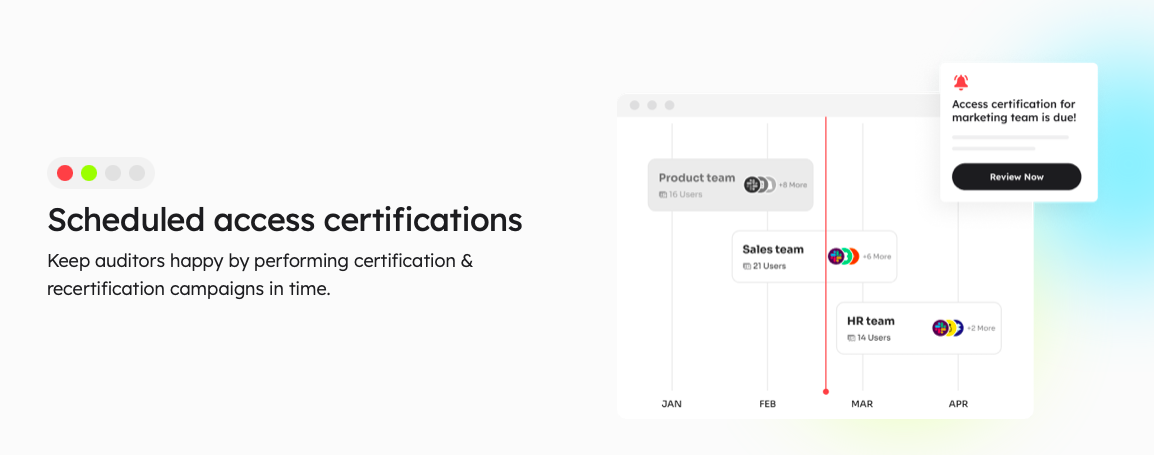
Access Certification
Discover the effortless way to handle user access reviews and permissions for your company with Zluri's IGA solution. Imagine a single, organized hub that streamlines your security, GRC, and auditing tasks. Zluri empowers you to easily define access review criteria, choose reviewers, and set up review schedules hassle-free.

By leveraging the power of intelligent automation, Zluri's predefined rules automatically validate user access rights, sparing you time and reducing mistakes that can happen with manual spreadsheet reviews. But Zluri goes beyond reviews. It takes swift action by fixing access issues if any violations are detected. This not only strengthens your organization's security but also ensures full compliance.
Zluri isn't just about reviews. It also assists you in removing access for departed employees or those who no longer require certain privileges. This vital feature thwarts potential breaches and safeguards your valuable data.
Additionally, Zluri generates comprehensive reports that offer insights into user access, vulnerabilities, and your adherence to compliance standards. These reports are your ace in the hole when demonstrating your meticulous approach to auditors and when making informed decisions about access management.
Zluri's unique approach to access reviews sets it apart from other IGA tools. Let’s see how.
Continuous Access Reviews: With Zluri's IGA solution, you're in charge of who gets access to what. You can closely monitor access rights by doing regular checks and planned reviews.
Regular access certifications make sure that access permissions are looked at and confirmed consistently. This helps find and fix security problems fast. And if you schedule reviews, you're less likely to miss important access issues.
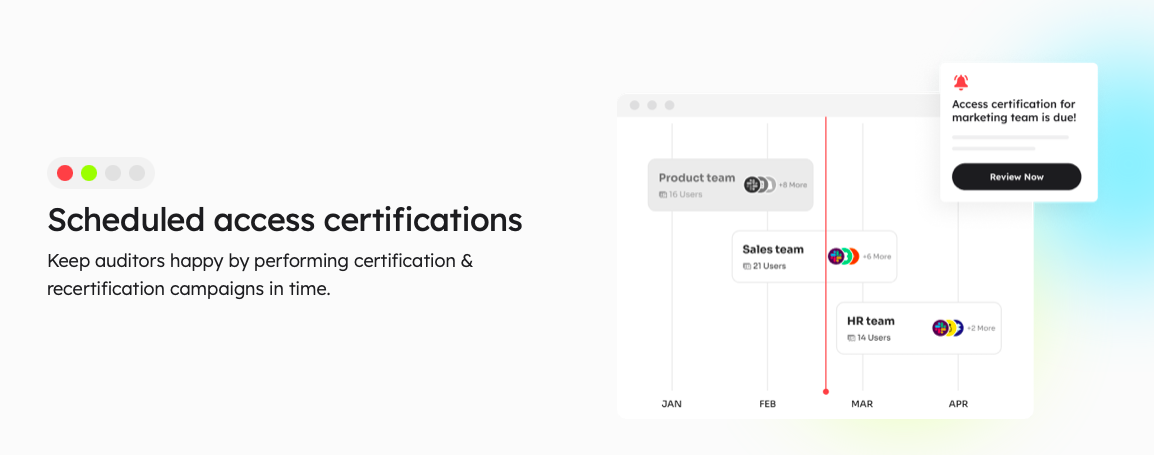
In addition, Zluri gives you templates that follow the rules everyone in the industry uses. These templates make it easy to do these checks and reviews the right way.
Real-time Access Reviews: Zluri uses the power of artificial intelligence (AI) to make your data safe and keep things compliant. It's like having a watchful eye that looks out for potential problems.
Zluri works in real-time, monitoring who's accessing your resources and how they're doing it. If anything looks unusual or risky, it promptly notifies you, enabling you to address issues before they harm your organization. This constant watch ensures the security of your vital information.
Moreover, Zluri's AI-driven compliance features provide smart insights and suggestions. It ensures that your access controls align with industry rules and standards, minimizing the chance of compliance breaches. By using AI to simplify compliance procedures, Zluri makes it effortless for your organization to meet regulatory demands.
For more information, Book a Demo today!
Related Blogs
See More
Subscribe to our Newsletter
Get updates in your inbox